Search form
A for and against essay about the internet.
Look at the essay and do the exercises to improve your writing skills.

Instructions
Do the preparation exercise first. Then read the text and do the other exercises.
Preparation

Check your writing: grouping - ideas
Check your writing: gap fill - useful phrases, worksheets and downloads.
What's your opinion? Do you think the internet is bad for young people?

Sign up to our newsletter for LearnEnglish Teens
We will process your data to send you our newsletter and updates based on your consent. You can unsubscribe at any time by clicking the "unsubscribe" link at the bottom of every email. Read our privacy policy for more information.
Threats of the Internet Essay
Introduction.
The Internet has become an indispensable part of our lives, gradually entering all the possible spheres and shaping the way we run our errands, communicate with people, and analyze the world around us. It changes our attitudes to work processes, leisure, and even interpersonal relations with the help of algorithms, simple solutions, and easy accessibility. Millions of services, goods, possibilities and infinite terabytes of all kinds of information have become available for a tap on the screen. In theory, all of these things seem to be convenient, progressive, and helpful, but the reality proves them to be also harmful to the well-being of people.
Some of the most relevant problems of today can already foreshadow the challenges we will most probably face in the not distant future. In the article “Our Machine Master” David Brooks predicts two ways for humanity equipped with artificial intelligence (AI). Contrary to many beliefs it will not give rise to humanoids, but it will be integrated into cars, headphones, watches, and other ordinary things that most people use on a daily basis. Such a close coexistence cannot but influence our habits and behavior, and in the end, such non-stop assistance and “external brain” might render people helpless and vulnerable in the face of all the dangers the real world holds.
Despite all the scientific and technical progress, our planet poses many dangers to humanity, some of them are still not thoroughly studied, some remain unknown. Moreover, even our bodies might become the victims of these technologies because less and less physical activities stay difficult enough to be performed by humans only. It is possible to suggest that we will have more free time and it will give a quality change to our lifestyle, but so far the experience of using technologies shows that they become addictive.
Another threat that lies in digital technologies is related to big data and control, which corporations acquire through online services. Such digital giants as Google and Amazon have access to all the personal and behavioral information that we share on the net, and though they claim to use for our benefit, the algorithms of the Internet also misuse in subtle and invisible ways. Searching tools can show us results they think should interest us judging by our previous clicks and views.
It is a powerful mechanism, but some people do not even notice that they are shown a distorted reality or only the part which the code deemed relevant for them. What started as endless freedoms and accessibility of all the information turns out to be pseudo equality and tyranny, in a way. I think that the article “Our Machine Master” by Brookes best argues with statistics and critical thinking, though all the rest also have relevant figures and examples, so none of them is weak.
Today digital media work according to similar principles of collecting big data, and showing the most interesting content for their users. YouTube and Instagram are among the most popular services that provide visual content; they both try to show as many relevant search results that should be interesting for users, based on their search history. Both are complex platforms with a variety of features, but at the same time, they are user-friendly, very appealing to large audiences, useful for sharing visual content and discussing it.
The wide popularity of these two services proves that people find them effective and relevant for their purposes because they succeed in holding the users’ attention and make them come back regularly. The main difference is that YouTube does not deal with photographs and mainly streams music videos and personal vlogs when Instagram also supports pictures, texting, and broadcasting. Instagram has a lower barrier of entry because photos require less preparation and work compared to video, they are easier to share, and do not take much time to be evaluated by other people.
In my personal experience, I use Instagram mostly to follow my friends and relatives and interact with them occasionally. As for YouTube, its audience seems impersonal to me, often there is too much happening in the comments section, and I usually do not contribute to discussions and only watch videos. Both services can steal a lot of my time because in a short period they have adapted to my choices and likes, and manage to provide interesting content I would not have found myself. This tendency is rather alarming, so I try to cut my time online and be mindful about things I come across on the net.
New media and technologies are developing so fast that it is hardly possible to keep up with their pace and stay sane, healthy, and socially acceptable. The biggest problem is that this endless succession of updates, notifications, and news demands all of our attention, and thus robs us of everything happening in the outer world. Attention has become one of the most valuable assets, and the more one spends online, the less connected they stay from their real-life troubles and joys. Apart from that, relying on technologies too much might weaken people and make it harder for them to adjust to the realities of the outer world.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 23). Threats of the Internet. https://ivypanda.com/essays/threats-of-the-internet/
"Threats of the Internet." IvyPanda , 23 Feb. 2024, ivypanda.com/essays/threats-of-the-internet/.
IvyPanda . (2024) 'Threats of the Internet'. 23 February.
IvyPanda . 2024. "Threats of the Internet." February 23, 2024. https://ivypanda.com/essays/threats-of-the-internet/.
1. IvyPanda . "Threats of the Internet." February 23, 2024. https://ivypanda.com/essays/threats-of-the-internet/.
Bibliography
IvyPanda . "Threats of the Internet." February 23, 2024. https://ivypanda.com/essays/threats-of-the-internet/.
- The Popularization of Instagram and Its Effects
- YouTube and Google Video
- YouTube: History, Advantages and Disadvantages
- Instagram in Our Life
- Outer Space and Its Impact on the Earth
- The YouTube Platform's Development and Influence
- YouTube Instructions: How to Upload a Video
- Instagram: Promotion of Loneliness
- How Instagram Claimed Its Users’ Most Intimate Moments
- Innovation: Instagram (App)
- The Children’s Online Privacy Protection Act (COPPA) and the Children’s Internet
- Wireless Local Area Network and Channel Fading
- The Internet of Things: Technical Description
- The Internet at Individual and Societal Levels
- Mobile Wireless Internet vs. Wi-Fi
- International edition
- Australia edition
- Europe edition

Five dangers the internet poses to a sustainable world
In recent months the world has been consumed by the tit for tat internet spying allegations between the US and China.
Then came the news that the NSA has worked with some of the internet's leading companies to not only spy on American citizens but those of Europe and Hong Kong as well.
Much of the ensuing debate has thus been about the erosion of privacy by the state and by large corporations increasingly using big data to "understand" customers and the behaviour of their staff.
But in the midst of this obsession with the privacy issue there has been little attention to other equally corrosive impacts of the internet revolution. Part of the problem is that until very recently, but hopefully no longer, the debate was framed in such a way as to cast any and all critics of the internet as either luddites or somehow anti-freedom.
There are four dangers, besides state surveillance, the internet poses which could make the world ungovernable and dangerous, destroy innocence and speed resource depletion.
First, it allows anyone to make their own guns and bombs, incite hatred and mobilise instant protests without regard to the consequences. Second, it creates unmanageable industrial espionage that will end the idea of businesses operating ethically. Third, it allows porn to reach every corner of the world, making access to the degradation of women only a click away. And fourth, it ramps up the speed of consumption and reduces its costs, hastening environmental destruction and resource depletion.
Dangers of pornography
The unrestricted access to porn by everyone from potential sexual predators to underage children is now making some headlines.
The United States has implemented an almost laughably limp system whereby adult websites can voluntarily list themselves under .XXX domain names. Iceland, Saudi Arabia and India are all considering bans on pornography, while the UK has plans to ban it on public wireless connections.
Yet at a time when a single porn site can account for almost 2% of total internet traffic, there is almost no reliable research into the effects that this explosion and instant access has on our societies, especially the young.
Whether any of the aforementioned bans will effectively restrict access to porn is one thing, but that such a major issue – and one that could have especially devastating impacts on children – has been all but ignored by policymakers until recently speaks volumes about the current unwillingness to challenge even the worst aspects of internet freedom.
Driving scale and speed of consumption
As for resource consumption, it's a truism that the internet has increased the pace of our lives. But while the benefits of this greater speed are shouted from the rooftops by the Silicon Valley crowd, its negative consequences have been left unexplored.
The omnipresence of the internet has made personal consumption both faster and easier than it has ever been before. And while the internet's role as a tool for enabling consumption is not novel – think product catalogues – its scale is.
It can be accessed from anywhere – on computers, laptops, phones and tablets and at work, at home and on the go. In the current frenzy to stimulate economic growth through promoting all forms of consumption, the internet is the medium with the greatest potential. Purchasing goods over the internet is both anonymous and guilt-free, and online retailers purposefully streamline the purchasing process to encouraging impulse buying, a growing addiction made easier as it doesn't even require leaving your chair.
The opportunity for billions now to desire anything from anywhere and buy it over the internet has given many "local" products a new found carbon footprint, at a time when we need the entire opposite. Then of course there's the whole question of jobs and tax losses.
The result is a massive, and growing, online marketplace that has changed attitudes, created a sense of entitlement and divorced customers from the reality of the resources that go into making consumer goods.
Impact on emerging economies
The greatest dangers are in the emerging economies, where internet penetration and purchasing power continue to skyrocket. China's internet retailing sector posted $210 billion in revenue in 2012, a growth rate of 60% from 2011. America's internet retailing market is only slightly larger and growing much more slowly. In India, 32% of smart phone users use their device for online shopping.
But the personal dimension is only half the story. The internet has also greatly increased the production speed of the goods themselves. In itself, this is not a bad thing. Internet-enabled supply chains have greatly increased efficiency, businesses which employ EDI (Electronic data interchange) can fulfill orders 30% more quickly.
Sourcing goods through Alibaba, China's largest e-commerce company, cuts the normal sourcing cycle by 75%. However, the increase in speed has only been in one direction. While we can cut down forests far faster than 100 years ago, we cannot grow them back any faster.
In other words, the internet has become a key tool in dramatically increasing the volume of consumption and the speed at which it is realised. This compression of the production cycle has put the institutions societies depend on – be they government bodies, private watchdogs or international agencies – to help negotiate between the need to consume and the need to conserve and protect, under unprecedented pressure.
Impact of an increase in speed
And even more than physical goods, the internet has sped up the creation and exchange of information with implications few are aware of. The incredible interconnectedness of global financial systems, for instance, allows for the practice of high-frequency trading and speculation of food commodities and resources, whereby stocks and other financial securities are bought and sold thousands of times a second.
It is the reason that financial firms are willing to pay millions of dollars for millisecond improvements in their connection speeds. These practices, which benefit no one save the traders themselves, create market instabilities which disproportionately affect those in the developing world.
The internet as it is today is a tool of enormous power that deserves most of the praise that has been heaped upon it. But the current cult of internet is unmistakably an ideological position quite removed from the reality of what the internet really is. And as with the worst kinds of ideology, it is afraid of being questioned.
Slaying sacred cows
The truth, however, is that the only way to really do service to the internet's potential is to ensure that our institutions are properly equipped to deal with its consequences, so that the laudable aspects of the internet don't have to be thrown out with the bad.
So what are the solutions? They are many but they require challenging a number of sacred cows. The key question surrounds the role of the state in controlling and using the internet. In America the NSA has apparently abused its mandate to protect American citizens by spying on them instead.
But the excesses of one government agency in one country should not cause us to reject the fundamental role of the government in protecting public good in the internet age. After all, the question remains, who will we trust to protect the nine-year old girl in Gansu province China, from pornography – Google or the Chinese government?
Chandran Nair is founder and CEO of the Global Institute for Tomorrow. He is the author of Consumptionomics: Asia's Role in Reshaping Capitalism and Saving the Planet.
Correction: This article was originally mistakenly published under the name of Doug Tompkins
- Guardian sustainable business
- Technology and innovation
- Pornography
Comments (…)
Most viewed.

John Brown University's Student Newspaper

Averting our eyes: The controversy of internet censorship
Pornography. Extremism. Fake News. Few words have as visceral an effect on a person as these. Together, these three items embody almost everything that is wrong in American society. And how has the government responded to their increase? By inviting them in as guests of honor through internet servers around the country.
Since its inception, the internet has been a nearly universal hub of information and activity. Everything from debates, auctions and photo albums is shared across the web in plain view of the public. Unfortunately, the internet contains much more sinister files than these. Pornography, drug deals and explicit content are all only a few clicks away from anyone with access to a computer. In this age, parents are forced to protect the eyes of their children from graphic content and sexual innuendos from the moment they touch their first device. Sexual addictions and crime rates across the country are on the rise and the vulgarity of the internet bears the brunt of the blame.
For years there has been an ongoing argument regarding the subject of internet censorship. Many groups claim that any content that someone desires to put on the web should be allowed to be posted. Others staunchly believe that the internet has become too explicit and harmful to be allowed to continue unchecked.
I believe that there is a difference between the restriction of useful information that can be applied and evaluated freely by consumers and the restriction of material that has little to no positive application. To be clear, I don’t believe that the internet needs to be dismantled. It is a wonderful tool with limitless potential for the improvement of mankind. But, I also believe that it is a tool that can easily be misused. Evil was not born on the day the internet was created, but it was given a new foster home. In the days of newspapers and encyclopedias, evil things were still captured and mass-produced but not on the scale that the internet allows them to be.
Much of the content on the internet including pornographic websites fall within that category of harmful material. These are things that have no potential to improve society and serve as a stumbling block to many who are exposed to them. We are becoming a culture that is more addicted, sexualized and uncaring than we ever have been before, and it is happening at a younger age than we have previously seen. Left unchecked, this exposure could lead to a dramatic shift in the moral values of American youth. When exposure to explicit content becomes normalized, other more socially unacceptable acts become more acceptable. Several scholars and studies have made the connection between rape acceptance and pornography exposure. Pornography is not simply images or videos; it is the breeding place of complacency and acceptance of heinous acts.
Another more controversial item needing censorship from the internet is websites and forums that foster extreme or criminal opinions. The United Nations Office of Drugs and Crime published a document that records multiple examples of how the internet has been used to foster terrorism across the globe. One of the main ways these groups use the internet to reach people is through propaganda, including messages, videos or games that intended to sway people to a more extreme mindset.
This topic becomes startling when we realize that none of this is actually prohibited. The UNODC states that “the dissemination of propaganda is generally not, in and of itself, a prohibited activity.” How is this not illegal? Criminal groups are embedding dangerous messages into the internet, and there is nothing the law can do to stop them.
The final commonality on the internet that needs to be regulated is fake news. As internet users, we are practically drowned in a flood of news. I understand that storylines will differ based on the perspective from which they are told, but an issue arises when two stories become irreconcilable. We are correct to assume that a narrative contains multiple storylines, but those lines should not contradict each other.
Somehow, individuals and news outlets manage to transform a single-threaded story into a web of self-contradiction and fallacy. Often, only a select few of those accounts are reasonably factual, leaving the rest as pure fiction, written to incite an emotional response in undiscerning people. It has become increasingly difficult to find cultural common ground with people around us because of the sheer quantity of fallacies we are fed. Humanity requires a standard to be set for news on the internet if groups are to begin to fix bridges and restore broken relationships.
But my viewpoint is uncommon. As a whole, the general American consensus is that freedom of speech should not be infringed. They cry that the First Amendment protects our freedom and keeps the government from influencing our lives. The American Constitution makes it clear that information should be free for all, and that it cannot be restricted by the government.
There is certainly justification in their fears. Governments should not be allowed to abuse their power to subjugate their citizens by scrubbing the internet. Many people fear what may happen to America if internet censorship is allowed. They fear that their freedom of speech will be infringed upon, and they will not be able to express their doubts and concerns to the public. In the opinion of many, internet censorship is the first step down the road leading to the eventual loss of freedom for Americans. Without freedom, innovation and progress will come to a standstill, leading to the undoing of American society.
The discussion regarding internet censorship is just one example of a larger ongoing debate. The core of this issue lies the question of man’s moral compass. If a man is born good, then there is no need to regulate content on the internet or anywhere else. But if man is inherently evil, regulation is imperative. Without guidance, humanity will slowly fall away from moral rightness, and we will begin to suffer the consequences of our arrogance.
The question also remains, who exists that is good enough to regulate us? Certainly not the government. They are human as well and have shown that they fall victim to the same errors as the public. The regulator would have to be a group with objective goals and moral uprightness. I am not sure if such a group exists. But if humanity has proven anything, it is that we are a people sorely in need of regulation if we are to remain on a path to improvement.
Comments are closed.
Contact The Threefold
Join our team, latest articles.
- Liberty University Fined by Department of Education over Campus Safety Issues and Title IX cases
- “The 96th Academy Awards ceremony” kept things entertaining
- “Jesus Did Not Save Me In A Church, He Saved Me In JBU:” Meet Juan Carlos Rodriguez
- Dune: Part Two; The Cinematic Experience We’ve Been Waiting For
- A Statement for Women
Follow us on Twitter
Essays About The Internet: Top 5 Examples and Prompts
Are you writing essays about the internet? Then, read our guide, including interesting essay examples and writing prompts to get you started.
The internet is a vast network of billions of computers connecting people virtually worldwide. When you connect to the internet or go online, you can access loads of information and communicate with people from millions of miles away.
The internet has presented groundbreaking benefits to society, such as global, real-time communication, more accessible access to information, and more source of leisure. However, when in the wrong hands, the internet can be a dangerous neighborhood that bustles with criminal opportunities for thieves, stalkers, and murderers.
For inspiration in writing an article about the internet, read our round-up of thought-provoking essay examples and prompts.
1. Forty Years Of The Internet: How The World Changed Forever by Oliver Burkeman
2. who owns the internet by elizabeth kolbert, 3. a nation of echo chambers: how the internet closed off the world by will leitch, 4. the rise of memes in the internet world by lennlee keep, 5. how to fight lies, tricks and chaos online by adi robertson, 10 writing prompts on essays about the internet, 1. the internet’s benefits to students, 2. dangers of the internet on the youth, 3. how the internet changed how we date, 4. how the internet revolutionized business, 5. safeguarding your privacy online, 6. effects of internet slang on literacy, 7. are bloggers replacing journalists, 8. the internet of things, 9. metaverse: the future of the internet, 10. creating communities online.
“It’s impossible to say for certain when the internet began, mainly because nobody can agree on what, precisely, the internet is. (This is only partly a philosophical question: it is also a matter of egos since several of the people who made key contributions are anxious to claim the credit.”
Burkeman treads the history of the internet through the lens of those who claim to have contributed to its development and arrival on the tech scene. His nostalgic journey interestingly shows how the internet emerged glacially slow, heading toward the dotcom boom not until decades after a successful computer communication experiment initially intended to establish US defense. You might also be interested in these essays about computers .
“The Internet revolution has, indeed, sent heads rolling, as legions of bookstore owners, music critics, and cirrhotic editors can attest. Instead of becoming more egalitarian, the country has become less so: the gap between America’s rich and poor grows ever wider.”
Once envisioned to democratize power to the people, the Internet disappoints as it continues to concentrate power on a few, deepening inequality with graver concerns, such as piracy and fake news.
“We now only have to interact with people who agree with us; if I use Twitter as my primary news source, as so many people do, I can carefully curate my feed to exclude anyone who disagrees with me about anything. (And if someone who slips in there who does, I can call them a horrible person.).”
The essay laments how the internet has isolated us into our echo chambers, leaving our beliefs unchallenged and stripped of world-proven facts on matters as evident as vaccination. Furthermore, because we addictively feed into the positive validation of people who share our opinions, it becomes easy to demonize those who don’t. As such, our society deals with more conspiracy theory believers and spreaders.
“The internet is still in some ways the Wild West, and putting your meme and your art out in the world requires a certain amount of faith in humanity, diligence and maybe a good rights attorney on retainer.”
An integral part of social media, memes may not mean what we know them to be in the internet age. Instead, evolutionary biologist Richard Dawkins contends that memes are cultural ideas and customs passed on if worthy of being “meme”-icked. If we go by this definition, memes could date back to early civilizations and even be found in the animal kingdom.
“This kind of viral half-truth is part of the fabric of today’s internet, and the kind of anger it inspired has been turned into a dangerous commodity. It’s cynically exploited by businesses for ad-supported “fake news,” by scammers raising money online, and by authoritarian governments to spread hate and fear.”
The widespread falsehoods being peddled over the internet requires netizens’ heightened vigilance. But Robertson recognizes the struggle always to be vigilant, drawing up a list of practical techniques everyone can use to combat fake news.

Share your insights and experience on how the internet has expanded your knowledge in a subject matter and helped you complete your academic papers. In addition, you can compare these perks against the difficulties students and researchers had to endure before the birth of the internet.
Anyone can be a victim on the internet, but kids are most vulnerable to cyberattacks and offenses. So first, cite the most common concerns kids can encounter while surfing online. A few examples you can include are cyberbullying, phishing, predators, and scams. Next, offer kids and parents some helpful safety tips to avoid falling prey to these online traps.
Critics hate the internet for making dating among the youth an easy game that heavily emphasizes sexual and physical attractions. Do you agree with them? Discuss your feelings on this point. You can also look into how the internet has strengthened relationships, especially long-distance ones, through communication.
In your essay, take a deep dive into how e-commerce has forever changed how we do business, from how we market our products to the skills of employees now sought. Then, lay down the risks and opportunities in e-commerce. Finally, provide expert tips on how businesses, especially small and medium enterprises, can be competitive by conquering the risks online while optimizing profits through the opportunities of a digitally borderless world.
Privacy is a contentious issue over the internet. Laws on privacy have turned more complex and become doubly challenging to enforce. In this prompt, hammer down the essence of maintaining privacy on the internet. Then, taking off from privacy experts’ recommendations, offer your audience critical steps to ensure they protect their private space and their data when online.
Internet slang is an evolving language created for people to communicate online easily. It has drawn extensive debates on its effects on the future of language and literacy. In your essay, write your insights on internet slang’s negative and positive effects on shaping students’ linguistic views and skills. If you’re a linguistics geek, you might also be interested in discovering how different languages created their internet lingos.
Can blogging meet journalistic standards and be a reliable source of truth? Journalists do not think so, but some contend that blogging is a form of citizen journalism that can legitimately put light on different angles of an event or situation. Answer this question yourself through your essay and dig deeper into the pros and cons of blogs as a source of news.
The Internet of Things (IoT) — the interconnectivity of devices made possible by the internet — is poised to be the next most significant technological advancement. When writing this essay, explain what part IOT can play in redefining the future. Then, cite its potential real-world applications and how it can revolutionize industries.
Write about the metaverse and its promises of raising the online experience to the next level. Talk about what your readers can expect and what activities they can do once they enter the metaverse. Then, consider tackling the technologies making the metaverse a reality and the cost of “living” in this virtual space. You may also go so far as to mull over the potential problems the metaverse poses, such as promoting an improved alternate world to escape from reality.
One of the most significant social benefits of the internet is finding new friends who share the same interests. We can engage with them directly or through forum discussions that strengthen our knowledge of our interests. For this essay, write about online groups and communities you are part of and share how these are helping you learn more while also challenging you to think more deeply to develop your insights and analysis. Want your essay to leave a good, lasting impression on your readers? Check this guide on how to write an argumentative essay . If you’re still choosing an essay topic, read our essay guides on social media and technology .

Yna Lim is a communications specialist currently focused on policy advocacy. In her eight years of writing, she has been exposed to a variety of topics, including cryptocurrency, web hosting, agriculture, marketing, intellectual property, data privacy and international trade. A former journalist in one of the top business papers in the Philippines, Yna is currently pursuing her master's degree in economics and business.
View all posts

- Get started with computers
- Learn Microsoft Office
- Apply for a job
- Improve my work skills
- Design nice-looking docs
- Getting Started
- Smartphones & Tablets
- Typing Tutorial
- Online Learning
- Basic Internet Skills
- Online Safety
- Social Media
- Zoom Basics
- Google Docs
- Google Sheets
- Career Planning
- Resume Writing
- Cover Letters
- Job Search and Networking
- Business Communication
- Entrepreneurship 101
- Careers without College
- Job Hunt for Today
- 3D Printing
- Freelancing 101
- Personal Finance
- Sharing Economy
- Decision-Making
- Graphic Design
- Photography
- Image Editing
- Learning WordPress
- Language Learning
- Critical Thinking
- For Educators
- Translations
- Staff Picks
- English expand_more expand_less
Internet Safety - Introduction to Internet Safety
Internet safety -, introduction to internet safety, internet safety introduction to internet safety.

Internet Safety: Introduction to Internet Safety
Lesson 1: introduction to internet safety, introduction to internet safety.
There's almost no limit to what you can do online. The Internet makes it possible to access information quickly, communicate around the world, and much more. Unfortunately, the Internet is also home to certain risks , such as malware , spam , and phishing . If you want to stay safe online, you'll need to understand these risks and learn how to avoid them.
Adopting a safer mindset
Computers can often give us a false sense of security . After all, no one can physically harm you through a computer screen. But to stay safe online, you'll want to take a more cautious approach. Here's one way to think about it: Treat the Internet as you would a shopping mall .
Most people don't consider a mall to be an especially dangerous place. You can go there to shop and meet up with friends. But there are also small things you may do to stay safe, even if you don't think about them very often. For example, you probably wouldn't leave your car unlocked or give your credit card number to a stranger.
Apply this same mindset whenever you're online. You shouldn't be afraid to use the Internet, but remember that it comes with many of the same risks you'd face in the real world. Throughout this tutorial, we'll show you how to prepare for these risks so you can be online without putting yourself in danger.
So what are you waiting for? Let's get started!
/en/internetsafety/creating-strong-passwords/content/
The Dangers of the Internet Beyond Cyberbullying

When the topic of kids and the internet arise in just about any conversation, the subject of cyberbullying is rarely far behind. It’s one of the most prominent issues children and teens are facing today. Unfortunately, it’s not the only thing parents should be concerned about when it comes to their children using the internet.
Online predators, posting private information and hackers phishing for information are just a few more of the problems we have to watch out for as our kids learn how to be responsible digital citizens. Here are just a few issues adults can keep an eye out for when it comes to the internet and our children.
The Safety of Social Media Apps
It seems like every month there’s a new social media app that all of the kids are clamoring to use. First it was Facebook, then Instagram, then Snapchat, and most recently it’s TikTok. TikTok allows users to post short videos, usually of choreographed dances (although short comedic sketches have been inching their way up the ranks as of late), for their friends and followers to see. The app incorporates hashtags for easier searching, has the latest musical hits and in general, comes across as a really fun mobile application aimed at children and teens.
However, many of these applications make it difficult to determine what the companies are doing with the information needed to set up an account. Just recently TikTok was hit with major cybersecurity concerns about the information stored from each user ranging from location to information about the device the app is being used on.
So far, nothing particularly dangerous has been done with the information but it’s still important for parents to be aware and it presents a great opportunity to discuss with your children what you should and should not post online . The good news is that features like GPS tracking can be turned off, but the problem is that many don’t know it was tracking location to begin with. Before you let your kids download any social media apps, take some time to do some research on the features of the app and decide from there if it’s something you deem safe for your children.
The Presence of Online Predators
There are a number of online games specifically marketed to kids, but parents should be aware it’s not always other kids your children are playing with . Little ones are taught from an early age the importance of knowing about stranger danger, but strangers seem a lot less scary if they’re posing as a friendly opponent in a seemingly innocent online game. Sex trafficking continues to be on the rise and, unfortunately, many predators use online personas to lure kids into situations where they can be kidnapped and sold into sex trafficking rings.
In 2018, the National Human Trafficking Hotline received over 7,000 reports of sex trafficking in the United States alone. Many times sex traffickers pose as friends or someone interested in pursuing a romantic relationship as it’s easier to then manipulate the younger population with that level of control. While all of this might seem like it’s taken directly from a Hollywood movie script, it’s crucial that parents are aware of the potential dangers relating to online predators. The better-informed parents are about sex trafficking, the easier it is for them to know the potential signs of a dangerous interaction unfolding online.
The Internet and Mental Health
In 1998, the term “internet addiction” was officially coined and as of now, the DSM-5 recognizes the problem as an official mental disorder . As the use of smartphones and mobile devices has become more and more prevalent, it should come as no shock that the number of those suffering from internet addiction has increased as well . It’s especially prevalent in the younger population with stats showing that children between the ages of eight to ten spend 11 hours a day in front of a screen on average .
Teens and children who suffer from internet addiction typically have poor planning skills, have issues with control and spend an excessive amount of time on the internet, and these things set them up to have more mental health issues down the line. Just like cyberbullying has lasting effects like depression, internet addiction can disrupt their school life with poor grades and shorter attention spans. Plus, as noted previously, these things have a domino effect later on in life as poor planning and impaired control can have an effect on finding a successful career.
While cyberbullying is a major problem among teens and children, it’s important that adults are aware of other potential issues as well. We all want the best for our children, but if we don’t know the potential risks, it makes it hard for us to educate them on our reasoning behind our decisions. As long as we continue to stay educated on the evolving trends surrounding the internet and social media, we’ll be in a better position to help our children make smarter decisions now and in the future as well.
View the discussion thread.
Related Stories

Guards of Calm: helping teenagers to cope with stress

My advocacy journey, from Iraq to the United States

A Letter for Girls Who Struggle
The Power of Thinking
C 2019 Voices of Youth. All Rights Reserved.

Essay on Misuse of Internet
Students are often asked to write an essay on Misuse of Internet in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Misuse of Internet
Introduction.
The internet is a helpful tool for information and communication. But, misuse of the internet has become a significant concern.
Misuse of Internet
Misuse of the internet includes cyberbullying, online scams, and addiction. Cyberbullying involves harming others online, causing emotional distress. Online scams trick people into giving away personal information or money. Internet addiction can lead to neglect of physical health and relationships.
While the internet has many benefits, its misuse can cause harm. It’s important to use the internet responsibly to avoid these issues.
250 Words Essay on Misuse of Internet
The advent of the internet.
The internet, a revolutionary technology, has transformed the world into a global village. It has brought about significant advancements in communication, education, and business. However, the misuse of the internet has also become a growing concern.
Internet Misuse: A Double-Edged Sword
The internet, while being a powerful tool, can also be a dangerous weapon when misused. Cyberbullying, identity theft, and invasion of privacy are some of the significant issues arising from its misuse.
Cyberbullying, a form of harassment using electronic means, has severe psychological effects on victims, leading to depression, anxiety, and even suicide in extreme cases. Identity theft, another misuse, involves stealing personal information for fraudulent activities, leaving victims financially and emotionally distressed. Invasion of privacy, facilitated by the internet, involves unauthorized access to personal data, leading to a loss of personal freedom and security.
Combating Internet Misuse
Addressing internet misuse requires a multi-faceted approach. Firstly, stringent laws need to be enforced to deter potential offenders. Secondly, internet users must be educated about potential threats and how to protect themselves online. Lastly, technology companies must take responsibility for creating safer online environments.
In conclusion, while the internet has brought about unprecedented advancements, its misuse poses serious threats. Therefore, it is crucial to address these issues to ensure the internet remains a tool for progress, not a weapon for destruction.
500 Words Essay on Misuse of Internet
The Internet, an invention of the late 20th century, has become an integral part of our daily life. It has revolutionized communication, education, business, and entertainment. However, with its widespread usage, misuse of the Internet has also increased significantly, posing serious ethical, social, and psychological challenges.
The Dark Side of Connectivity
The Internet, designed to promote connectivity, has also become a tool for cybercrime. Identity theft, phishing, and fraud have become commonplace. Cybercriminals exploit the anonymity provided by the Internet to commit crimes without fear of immediate reprisal. This misuse not only threatens individual privacy but also poses a significant risk to national security.
Internet and Social Disintegration
While the Internet connects people globally, it also contributes to social disintegration. The excessive use of social media can lead to addiction, causing people to become more engrossed in their virtual lives than their real ones. This can lead to strained relationships, reduced productivity, and even mental health issues.
Spread of Misinformation
The Internet’s ability to disseminate information quickly and widely is a double-edged sword. It has been misused to spread misinformation and fake news, often leading to panic, confusion, and mistrust among the public. This can have serious implications, particularly during crises, where accurate information is crucial.
The Dark Web and Illegal Activities
The dark web, a part of the Internet not indexed by search engines, is a hotbed for illegal activities. From drug trafficking to illegal arms sales, the dark web provides a platform for such activities to take place anonymously. This misuse of the Internet has serious societal implications, contributing to crime rates and undermining law enforcement efforts.
In conclusion, while the Internet has undeniably brought about significant benefits, its misuse poses serious challenges that need to be addressed. It is crucial to promote digital literacy and cyber ethics among users. Moreover, robust cyber laws and their effective enforcement are needed to curb the misuse of the Internet. The challenge lies in achieving a balance between leveraging the benefits of the Internet and mitigating its potential misuse. It is a collective responsibility that requires the cooperation of individuals, communities, and governments alike.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Internet of Things
- Essay on Internet Bullying
- Essay on Internet and Modern Life
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Front Psychol

Terrorism and the internet: How dangerous is online radicalization?
Jens f. binder.
1 Department of Psychology, Nottingham Trent University, Nottingham, United Kingdom
Jonathan Kenyon
2 His Majesty’s Prison and Probation Service (HMPPS), Counter Terrorism – Assessment and Rehabilitation Centre (CT-ARC), London, United Kingdom
This work is concerned with the extent and magnitude of threat related to online radicalization in the context of terrorist acts and related offending. Online influences have been depicted as major drivers for the propagation and adoption of extremist ideologies, which often contain an element of collective grievance, and subsequent acts of violence. This is most pronounced in the discussion of so-called lone actor terrorism, but extends to all forms of extremist offending, and beyond. The present work situates online radicalization leading to terrorist acts within the wider context of grievance-based beliefs and attitudes. Further, it addresses current positions and debates surrounding the relevance and mechanisms of online radicalization in terrorist offending. Recent evidence from quantitative studies is reviewed to estimate prevalence of online radicalization and the level of threat that results from it. This is followed by a discussion of plausible, but opposing, interpretations of the estimates presented. While online radicalization does occur, with and without reference to offline processes, the resulting threat is not overly high. This assessment, however, refers to the present only and is unlikely to hold for the future, given the general growth and acceleration of online activity among terrorist actors.
Online radicalization as a cause for common concern
This work is concerned with the extent and magnitude of threat related to online radicalization in the context of terrorist acts and related offending. Online radicalization is here understood as a process during which individuals get exposed to, imitate and internalize extremist beliefs and attitudes, by means of the Internet, in particular social media, and other forms of online communication. This definition is adopted for entirely pragmatic reasons and should not mask the fact that almost none of its terms has gone uncontested ( Neumann, 2013 ; Gill et al., 2015 ; Macdonald and Whittaker, 2019 ; Evans and Williams, 2022 ; Rothut et al., 2022 ). From a forensic perspective, such radicalized individuals are seen as at an increased risk of committing offenses which may take the form of violence, causing harm and death to many, as in violent acts of terrorism ( Kenyon et al., 2021a ; Evans and Williams, 2022 ; Hamid and Ariza, 2022 ).
The present work will, first, situate online radicalization leading to terrorist acts within the wider context of grievance-based beliefs and attitudes. This will allow for an outline of the extent to which the specifics of terrorism studies are generalizable and can contribute to a wider integrative perspective on grievance and violence. Second, we will address current positions and debates surrounding the relevance and mechanisms of online radicalization in terrorist offending. Third, we will review recent evidence that is available on the prevalence of online radicalization and the resulting level of threat. For this, our emphasis is on recent, quantitative studies, less so on qualitative and theory-driven work, although we acknowledge the wealth of important contributions from such work in the wider thematic area. This allows us to arrive, fourth, at a quantification of threat levels, which, we believe, is crucial to current debate.
Online radicalization processes have been of major concern, not only in the area of terrorism, but in the wider field of grievance-based violence. In fact, recent work has introduced a comparative approach that builds on the commonalities between perpetrators of, for example, high school shootings, hate crimes, and terrorist attacks ( Brooks and Shaw, 2022 ; Clemmow et al., 2022 ; Ebbrecht, 2022 ). In particular for offenders deemed to be lone actors, the boundaries between terrorism and other forms of offending are blurred ( Capellan, 2015 ; Kenyon et al., 2021a ; Clemmow et al., 2022 ). Capellan (2015) sees both ideological and non-ideological mass shootings as belonging to one broader type of homicide defined as lone actor grievance-fueled violence. Similarly, Clemmow et al. (2022) propose a general Lone Actor Grievance-Based Violence framework that accommodates both lone actor terrorists and mass murderers, based on a detailed cluster analysis on several dimensions (propensity, situation, preparatory, leakage, and network indicators).
Over the past decade, the way in which the Internet presents, selects, connects and curates information, by virtue of its architecture as much as through user activity, has been identified as particularly concerning in the context of extremist ideologies. Broad concepts that have emerged address the dangerous normalization and acceptance of extremist messages that result from such information management. For example, Von Behr et al. (2013) reviewed evidence that pointed to the formation of echo chambers online, structures in which individuals can surround themselves with likeminded others and help reinforce each other’s views, thus contributing to an amplification of opinions. Related to echo chambers, filter bubbles ( Pariser, 2011 ) have received sustained attention. For these, automated algorithmic selection of content is the main driver. Individuals are exposed to more and more content of the same type, at the expense of alternative viewpoints. Although a solid understanding of the actual effects of such broad mechanisms on radicalization has not been reached yet ( Reed et al., 2019 ), their potentially sweeping generality and relevance is without question. Studies have documented problematic Internet uses for specific platforms across a spectrum of different forms of extremism, ranging from clearly political ideologies (e.g., right wing; O’Callaghan et al., 2014 ) to those that can be associated with religion (e.g., jihadi-inspired; Clifford and Powell, 2019 ; Macdonald et al., 2019 ) and those that are more difficult to categorize such as entrenched misogynistic world views ( Speckhard et al., 2021 ). In the following, we will focus on a more detailed review of the role and specific mechanisms of online radicalization in the context of terrorism.
Online radicalization and terrorism
The specific context of terrorism.
Although there is some indication of a common basis for grievance-based forms of offending, there are a number of specific factors that surround acts of terrorism. These are important to highlight for a further investigation of online radicalization. All definitions of extremism and terrorism are contentious, but there is general agreement that a frame is provided by some ideology supportive of violent changes to societal and/or political order (see, for example the perspective adopted by the United Kingdom government in its most recent counter-terrorism strategy: UK Government, 2018 ). This also means that there are pre-existing structures and organizations that represent, shape and use such ideologies and exert influence on individuals as members and followers. These organizations are concerned with recruitment or member management and the channeling of activity. At their most powerful stage, they assume para-military and quasi-governmental forms (as in the example of Al Qaeda; see Gunaratna and Oreg, 2010 ).
But next to these organizational forms, a wider gray area can be identified, in which individuals are inspired to commit acts of violence. This is captured by the label of the lone actor terrorist ( Gill, 2015 ; Kenyon et al., 2021a ). Online radicalization in the context of terrorism can therefore occur in direct exchange with networks and groups with a high interest in recruitment and a readiness to invest resources in communication and outreach activities; online radicalization can also occur in a less systematic way, driven by the individual. This duality is further reflected in theoretical explanations of radicalization that focus either on bottom-up (i.e., through emerging group dynamics; Sageman, 2004 , 2008 ) or top-down dynamics (i.e., through hierarchies that channel influence from an organization to those to be radicalized; Hoffman, 2008 ), or, indeed, a synthesis of both ( Conway and McInerney, 2008 ).
It should also be considered that a wide range of content generated by organizations classed as terrorist or extremist is deemed illegal in many countries, as is the formal or informal organizational membership. This poses a dilemma for terrorist organizations operating online: high levels of secrecy can be achieved through encryption, thereby minimizing the risk of detection, but this limits outreach to recruits and sympathizers severely. Further, the accessibility of extremist materials online can be very high, but digital files leave traces on individuals’ devices, and the mere downloading of certain materials can lead to detection and prosecution. As a result, terrorist groups have shown substantial adaptability and flexibility in their use of online services and platforms ( UK Home Office, 2019 ). A common strategy established over the last few years consists of using entry points on mainstream sites that can be used to guide those interested to other digital locations such as encrypted services or dedicated web sites ( Clifford and Powell, 2019 ; Macdonald et al., 2019 ).
Recent work on online influences in terrorist offending has provided evidence both for and against a perspective on Internet activities as a specific risk factor. Separate lines of research suggest that offenders radicalized online pose the least threat to society when compared with those who have more, and more face-to-face, social exchanges ( Kenyon et al., 2021b , 2022a ; Hamid and Ariza, 2022 ). In addition, online radicalization has been criticized as an overly simplistic, artificial construct that neglects the realities of today’s seamless transitioning between online and offline spheres ( Gill et al., 2015 ; see also Conway, 2016 ). At the same time, the evidence base also indicates that online radicalization can and does occur, with potentially violent consequences, as in the case of some lone actor cases ( Kenyon et al., 2021a ).
There is no doubt that online activities play an important role in most forms of terrorism. Research has documented how terrorist organizations and terrorist actors have kept pace with technological development. To the extent that the Internet permeates all aspects of our daily lives, it is also an integral part of the propagation of extremist ideologies and resulting actions and operations. From the start of more wide-spread Internet use, research has documented how novel forms of online engagement have led to novel aspects of terrorist activity (e.g., Weimann, 2006 , 2014 ). A recent overview by Evans and Williams (2022) , based on a synthesis of earlier studies, groups online activity into five broad domains: Financing, networking and coordination, recruitment and radicalization, knowledge transfer, and mobilization to action. The main conclusions by Evans and Williams (2022) indicate that all extremist movements engage in online activities, in ways and with platforms that are no different from normal everyday uses of the Internet. In relation to radicalization, the Internet plays an integral role in the generation, consumption and spread of extremist propaganda.
Other work has focused on the facilitating role of the Internet during the radicalization process itself, often emphasizing that online and offline influences are intertwined and reinforce each other ( Von Behr et al., 2013 ; Gill, 2015 ; Valentini et al., 2020 ). Jensen et al. (2018) assign an accelerating role to social media, in particular for the radicalization of foreign fighters, but see radicalization as a process which is not exclusively online or offline. Likewise, Herath and Whittaker (2021) , similar to Gill’s (2015) earlier work, take issue with a clear-cut dichotomy of either online or offline and provide evidence for several radicalization pathways that combine both types of influence in different measure. Indeed, Whittaker (2022) argues that any separation of online and offline radicalization is meaningless since both domains are part of the same information environment and cannot give rise to different processes of radicalization.
Next, to any conceptual debate, however, it remains a fact that any individual on a pathway toward increasing radicalization may obtain relevant information from the online world, in large quantities and at comparatively low levels of environmental restrictions and control. This poses a challenge to policy makers and regulators. Regulating and monitoring the online world requires measures, resources and, often, legislation different from those needed in an offline public sphere. Simply declaring the Internet to be an integral and inseparable part of our lives will not resolve this challenge and does not offer nuanced responses. Where authors have considered radicalization to happen (nearly) exclusively through online means, opinions on resulting threat are mixed. Hamid and Ariza (2022) concede that online radicalization exists and poses a problem, however, they conclude that it constitutes a lower threat than other forms of radicalization and is of lesser pertinence to security. Other work also indicates that threat levels differ depending on the online and offline means of radicalization ( Gill et al., 2017 ; Jensen et al., 2018 ; Kenyon et al., 2021b , 2022a ).
Mechanisms of online radicalization
Before the estimation of prevalence and threat are addressed in the next section, the frame of the debate is best shaped by addressing an a priori question, namely whether Internet technologies are suitable and have the actual power to lead to radicalization “on their own.” In this section, the focus is on studies that have outlined how Internet technologies can support and facilitate radicalization processes, potentially independent of any offline exchanges. Core questions that emerge from these studies concern the role of active and passive uses of the Internet and how these can further extremist attitudes and beliefs. Such mechanisms provide a more solid basis to consider online radicalization as a persistent problem.
Echo chambers and filter bubbles, as outlined above, have been identified as possible mechanisms almost a decade ago ( Von Behr et al., 2013 ; Reed et al., 2019 ). Some research findings tentatively affirm that such mechanisms have also been effective in recent years when it comes to radicalization. Further, there are now studies that have followed individuals and their online activities much more closely and allow for a more detailed understanding of the mechanisms at play. It should also be noted that the general consensus sees the role of the Internet as that of a facilitator or catalyst, far less as a driving causal factor (see Meleagrou-Hitchens and Kaderbhai, 2017 ). As such, the question here is not so much how the Internet would cause radicalization, but how precisely it can support such a process in those individuals who are particularly vulnerable.
Gill (2015) focused on a behavioral analysis of lone actor terrorism, i.e., cases characterized by an absence or scarcity of social interaction. The Internet main roles concerned the reinforcement of the individual’s radical mind set, the dissemination of propaganda and information leakage prior to an attack. Of those functions, reinforcement is most likely to be of relevance during the radicalization process. The comprehensive analyses by Hamm and Spaaij (2017) , covering more than 60 years of lone actor terrorism in the U.S., may contribute to a wider understanding of the reinforcement that can be obtained online. The authors found that lone actors were more likely to maintain some affinity with an extremist organization in the time period before the 9/11 attacks compare to after. Hamm and Spaaij explained this shift with increased online activity and a change in audience and social influence. Lone actors are thought to obtain ideological direction not through organizations, but networks of anonymous online activists, a crucial transformation that has made lone actor terrorism more decentralized and leaderless.
There is some suggestion that exposure on its own has some substantial effects. Hassan et al. (2018) conducted a systematic review on the link between exposure to extremist online content and violent radicalization. Having identified a set of 11 empirical studies, using a range of methods and focusing on several extremist ideologies, the review concludes that there is tentative evidence that exposure leads to radicalization, although it is not clear which level of involvement is needed on the user’s side to become more radicalized. Similarly, Wolfowicz et al. (2022) reviewed and integrated experimental and observational evidence in a comprehensive meta-analysis. Based on four experimental studies, the authors obtained a small effect for mere exposure to media content, i.e., with passive study participants, on radicalization outcomes (Hedges’ g = 0.08), which was slightly increased in case of high trait aggression ( g = 0.13).
Focusing in detail on the Twitter activity by 110 self-proclaimed Daesh supporters, Smith et al. (2020) were able to show how conformity to the linguistic and stylistic aspects of an extremist group environment increased over time and was positively related to engaging in group mobilizing interaction. While these findings demonstrate how radicalization processes can be detected online, and are expressed in social media activity, the focus is clearly on users who are neither passive nor in social isolation. A similar level of activity is described in the study by Speckhard et al. (2021) on self-defined involuntary celibates (“incels”) online. The authors provided an account of how a subset of those identifying as “incels” are further radicalized in online forums that support the immersion in a grievance-based perspective and lead to an increased endorsement of violence. Within active and extended online networks, there is also the possibility that radicalizing messages are controlled by feeder accounts, thus channeling influence in a more organized manner, as in the study on the Twitter networks surrounding foreign fighters in Syria by Klausen (2015) .
Using a large (44 k) sample of Twitter users, Magdy et al. (2016) compared interactions online (use of hashtags, retweets, replies, and mentions) prior to and after the 2015 terrorist attacks in Paris. Negative attitudes toward Muslims and endorsement of extremist hashtags after the event could be predicted to a substantial extent from previous Twitter activity (e.g., consumption of anti-Muslim tweets), even in the absence of prior references to Islam by the user. These findings point to the possible effects of more passive social media consumption, or social media activity that is not focused on a particular target, which increases the readiness for developing more specific extremist views.
Next, to the question of how much activity or engagement is necessary online to support radicalization, other work has focused on the type of format and content that is most effective. Wolfowicz et al. (2022) , in their meta-analysis, attempted to separate online exposure from other forms of media consumption. Pooling outcomes from 49 observational studies, they conclude that TV consumption carries no effect while active and passive online exposure to radical content are related to risk of radicalization ( r = 0.22 for active, and r = 0.24 for passive online consumption). Among active information seeking online, accessing jihadist magazines showed the strongest association with radicalization (up to r = 0.29), in contrast to beheading videos ( r = 0.16), possibly because these are more indicative of violence and aggression more generally. This finding coincides with the study by Frissen (2021) on a large sample (>1,800) of Belgian young adults: self-reported cognitive radicalization was most pronounced.
The empirical evidence to date has been integrated in several theoretical analyses and frameworks. For example, Mølmen and Ravndal (2021) derive a total if six factors of theoretical importance to the process of radicalization from a review of the literature, three of which carry particular relevance in an online context. These are facilitation, acceleration, and echoing. Facilitation encompasses any intensification in the exposure to extremist content, acceleration refers to the shorter timeframe that is assumed for online radicalization as compared to offline processes, and echoing implies a further reinforcement, and normalization, of an extremist mind set due to the like-mindedness of the sources of influence encountered online. Likewise, Neo (2019) has proposed a model of internet-mediated radicalization that outlines the supportive functions of Internet technologies during five phases of the radicalization process: reflection, exploration, connection, resolution, operation. It is worth noting that while the connection seems to suggest actual communication with others, this phase can also be dominated by unidirectional online influences, without interaction.
In sum, the Internet provides several functions and mechanisms that allow for online radicalization, and likely so in the absence of actual social interaction. It seems that development of a grievance-based perspective, and the deeper immersion therein, are most effectively achieved by combining both asocial and social engagement online. It should be added, however, that there is general agreement that a combination of online and offline processes is seen as most effective in the furthering of the radicalization process.
Evidence on threat levels
In this section, recent studies are reviewed to, firstly, establish our understanding of the prevalence of online radicalization and, secondly, to arrive at some informed estimate of the actual threat level that results from such radicalization. To this end, the focus is on quantitative studies that are based on some clearly defined population of terrorist actors and allow for statistical interpretation and generalization, to a certain extent. As will become clear, all such studies differ from each other in terms of the underlying data sources, the type of terrorist actor under investigation and the precise set of variables and operationalizations used. Following a review of prevalence and threat, a wider discussion is initiated of the divergent interpretations that can be derived from the current state of knowledge. By alternating between conflicting critical narratives, the aim is to get closer to an answer of a core question of the present work: How dangerous is online radicalization?
Evidence on prevalence of online radicalization and associated threat
In their landmark study from 2015, Gill et al. provided a detailed account of online activities of 227 United Kingdom-based terrorist actors, covering the period from 1998 to 2013. Overall, there was evidence for some online activity related to an attack or relevant terrorist offense in 61% of all cases. Looking at specific activities, 54% of all cases used the Internet for learning, 44% for the spread of extremist online media, 32% for attack preparation. Some of these figures, unsurprisingly, were markedly increased toward the end of the time period covered. In a follow-up study, using a modified data set with 223 entries, Gill et al. (2017) further differentiated online activity based on several offender characteristics. So-called lone actors were substantially more likely (2.64 times) than group-based terrorists to learn online. The type of attack was likewise correlated with online activity, with those concerned with using Improvised Explosive Devices (IEDs) being more likely to engage in online learning compared to other attackers.
The figures from Gill et al. (2015) are roughly confirmed by Whittaker (2021) who used a data set on 231 U.S. based Daesh (IS) terrorists, all that were recorded during the period 2010 to 2020, and their online activities. Some online activity was found to be present in 92% of all cases; more than 80% interacted online with co-ideologues, 80% used social media platforms for at least some of their activities, 36% had disseminated propaganda online. The somewhat increased percentages are not surprising given the extended time period up to 2020 and the fact that the peak activity of Daesh/IS falls into the years 2015 and 2016, after what the study by Gill et al. (2015) was able to consider.
These findings indicate the overall importance of Internet technologies for terrorist actors, and they provide important detail on the type of activity, for the United States and the United Kingdom. They stop short, however, of assigning a specific role of such activities to the radicalization process proper. While Gill et al. (2017) link lone actor terrorism to both online activities and to the severity of the chosen plot and attack method, it would be premature to conclude that lone actors define all relevant cases of online radicalization. It can be assumed that radicalization is an ongoing development and continues while actors are fully operational. Under this assumption, all online activity would also be relevant to radicalization, by definition. Other studies, in contrast, have placed a direct emphasis on the role of online activity within the radicalization history of individuals, as far as this can be reconstructed from sources. The focus here is, again, on quantitative studies that allow for some estimate of overall prevalence and threat level.
Bastug et al. (2020) investigated the role of social media for 51 Canadian Islamist extremists from 2012 onwards. Information on radicalization was available for 32 individuals. Of these, online activities were underpinning the radicalization process in 21 cases. This puts the prevalence rate at in between 41% and 66%, for an overall group size of 51 or 32, respectively. In this study, however, online activities could occur alongside other radicalization mechanisms. The prevalence rate therefore refers to mixed modes of radicalization as much as to more exclusive online influences.
Similarly, Jensen et al. (2018) , using the comprehensive PRIUS data base of U.S.-based extremists, noted that radicalization involving social media rose substantially over time. In the period from 2011 to 2016, social media were assigned a primary role in radicalization for 17% of all cases ( n = 295), across a spectrum of causes including jihadist, far-left, far-right and single issue ideologies. A primary role of social media was assumed if exposure to extremist ideologies and more than half of the socialization took place online. This provides a more restrictive criterion for online influences, but again assumes a mixed-model of radicalization. The study also provided an opportunity to discuss the acceleration potential of the Internet for the process of radicalization. By focusing on a sub-set of jihadist foreign fighters, Jensen and colleagues were able to define a meaningful start and end point to radicalization (i.e., from the first time contact with extremist ideologies to the first attempt to take up the role of foreign fighter), and they found that as social media engagement increased the duration of the process decreased.
Returning to the challenge of interpreting reported prevalence, using mutually exclusive categories for online and offline radicalization pathways allows for more insightful estimates. In a study on individuals arrested in Spain for activities related to jihadi terrorism, Reinares et al. (2017) collected information on 178 cases. The time period covered reaches from 2013 to 2016. For 119 cases in the sample, information on the radicalization environment was available and a classification according to Internet activity could be established. An environment that was exclusively online was found in 35% of cases, offline only was the case for 24%, and for 40%, a mix of online and offline influences was found. Of note, radicalization was defined here as development prior to involvement in terrorist activities.
The comprehensive study by Hamid and Ariza (2022) provides a rare opportunity to relate the radicalization pathway to the severity of the terrorist act. This allows for a direct, quantified estimate of the level of threat that follows from different radicalization modes. Focusing on attack behaviors, the authors created a database containing 439 jihadist attackers active in eight Western countries in between 2014 and 2020. Of these, 54% were radicalized mostly offline, 18% online, and for 9%, a mix of online and offline influences could be established. Online radicalization typically came with social interaction. Only 2% of the sample conformed to a pathway labeled asocial online radicalization. A radicalization pathway could not be established for 17% of all cases.
When it comes to threat levels, those radicalized offline showed a three times higher likelihood of successful attack completion when compared to those radicalized online ( Hamid and Ariza, 2022 ). The only exception were the few cases of asocial online radicalization; for these, successful attack completion was 2.5 times more likely than for the offline group. The severity of outcomes was likewise related to radicalization and showed more severe outcomes when offline processes were involved. Online radicalization, both social and asocial, did not play a role for attacks with more than 20 people injured or more than 5 attack casualties, in contrast to offline or hybrid radicalization.
So far, the findings discussed are based on publicly available data, often involving carefully maintained open data bases, but also integrating media reports, court proceedings, and other documentation. In contrast, our own work on extremist offenders in the United Kingdom, England and Wales specifically, is based on closed-source data generated within the Prison and Probation Service (HMPPS; Kenyon et al., 2021b , 2022a , b ). A data set was generated by coding Extremism Risk Guidance Reports (ERG22+; Lloyd and Dean, 2015 ; National Offender Management Service, 2017 ), together with two Structured Risk Guidance Reports, an earlier version of the ERG22+ report, covering cases across a range of causes and ideologies. These reports constitute detailed accounts of an offender’s background and radicalization journey prior to the offense. In the majority of cases, offender interviews form part of the basis for the ERG22+ reports although a range of other restricted and more freely accessible sources get consulted, e.g., court reports, police reports, sentencing remarks, prison intelligence reports, among others.
Importantly, the detailed accounts are supplemented by formalized risk assessments on a total of 22 variables. These are aggregated to represent three different dimensions of the risk, or threat, that an offender poses: engagement, intent and capability. Reports and assessments are generated by HMPPS professionals who have undergone a specialized training program. Thus, the ERG22+ reports constitute one of the few standardized sources that allow for a triangulation of radicalization pathway, offense characteristics and current levels of risk and threat.
Within a total of 269 case reports, all related to the Terrorism Act, 235 cases of radicalized extremists could be identified. These conformed to the definition by Silke (2014) : there was evidence they had held extremist views prior to coming into custody and that they had engaged in extremist activity outside prison. Of those, 12% had been radicalized primarily online, 40% primarily offline, and 48% through a mix of influences. Online radicalization coincided with a greater likelihood of mental illness or personality disorder being present as well as a lower degree of social connection with other extremists offline (63% were classed as lone) when compared to the other two categories. Further, online radicalization was characterized by a lower likelihood of being in an attacker role compared to radicalization offline.
In terms of risk assessments, online radicalization came with the lowest level of risk on all three dimensions. Engagement, as defined in the ERG22+, refers to a growing interest or identification with an extremist ideology or any group in support of such an ideology. Only 32% of the online group were classed as highly engaged, in comparison to 67% in the mixed group and 50% in the offline group. Intent refers to future readiness to overcome inhibitions and take action by committing offenses on behalf of the group or cause. Here, 15% of the online group were classed as high, with 48% in the mixed group and 36% in the offline group. Finally, capability encompasses knowledge, skills, networks and the general training necessary for carrying out terrorist acts. The online group showed significant (i.e., highest) levels in only 5% of all cases while for the offline group this figure was 41% and for the mixed group 22%.
In sum, the prevalence rate of online radicalization, in particular in the decade from 2010 and 2020, stands roughly at 12%–35% within a wider population of terrorists. This range is derived by looking across Western countries and somewhat differently defined populations. While Reinares et al. (2017) and Hamid and Ariza (2022) focus on jihadist terrorists, the former with a focus on individuals actually apprehended, the latter with a focus on terrorist attacks on record, Kenyon et al. (2022a , b) work with information on incarcerated offenders covering a wider spectrum of ideological backgrounds. It should be noted that the label “online” here refers to instances where the clear dominance or near exclusivity of online processes could be established with sufficient confidence. If mixed forms of radicalization were included, prevalence figures would be higher (as, for example, in Bastug et al., 2020 ) although it would then no longer be warranted to assign a driving force to Internet technologies.
Individuals radicalized online do not typically pose the highest level of threat. Considering the few successful attacks identified by Hamid and Ariza (2022) and the few individuals attributed high levels of threat, in particular any significant levels of capability, in Kenyon et al. (2022a , b) , it seems that substantially dangerous individuals constitute no more than 2% in populations of Western-based terrorist actors. These figures need to be taken with great caution, given the scarcity of quantifiable findings. They do resonate, however, with the low threat levels found previously for lone actors (e.g., Gill et al., 2017 ), although findings also show clearly that the overlap between lone actors and those radicalized online is far from complete.
Opposing narratives compatible with the evidence
The review in the preceding section exemplifies, first and foremost, the substantial challenges that come with any attempt at quantifying the extent and outcomes of online radicalization. Equally challenging, however, is an appraisal and interpretation of the outcomes of quantification. In this section, this point will be developed through the presentation of two opposing narratives. In contrast to section Evidence on prevalence of online radicalization and associated threat, the purpose here is to outline a more holistic perspective rather than to reference again relevant literature.
In the first narrative, online radicalization is seen as posing a low threat by itself. While Internet activity has increased over time in all studies reviewed, this often seems to be attributable to the wider spread of Internet technologies and Internet use in society. In particular, the rise of social media among terrorist actors is closely mirrored by the global development these platforms have seen. Mixed modes of online and offline radicalization emerge as a standard model, and most studies have assigned a reinforcing, facilitating, possibly accelerating role to the Internet in there ( Gill et al., 2015 ; Jensen et al., 2018 ). When considering mutually exclusive radicalization pathways, captured as solely online, solely offline, or combined, the Internet emerges still much more as an enabler, rather than a driver on its own.
When viewing online radicalization as a specific radicalization pathway, threat levels appear even lower. In our work to date ( Kenyon et al., 2022a ), online radicalization does coincide with an offender type that is socially isolated, more prone to mental illness and associated conditions, and less likely to commit acts of violence. This type is assessed as low in engagement with extremist ideologies, or groups representing such ideologies, and further shows lowest levels of intent and low capability compared to other radicalization pathways. Other work has also highlighted a tendency for information leakage online, and where this is prior to an offense, it can help to thwart attacks ( Gill et al., 2017 ; Kenyon et al., 2021a ; Hamid and Ariza, 2022 ). This has led to the view that those radicalized online are comparatively powerless, in particular when it comes to translating online activity into offline violence ( Conway, 2016 ). As far as the evidence goes, successful attackers who have radicalized primarily online are very rare when compared to any wider extremist offender population. As far as convicted individuals within the Western world are concerned, online radicalization and violence do not share a strong or direct link.
The second narrative assigns a much higher threat level to online radicalization. A few individuals on this radicalization pathway manage to commit acts of violence, and these may be particularly difficult to detect when leakage does not occur, fails to trigger a security response or is intentional and helps to enhance the effectiveness of an attack [see Hamm and Spaaij (2017) on the distinction between intentional and unintentional information disclosure online]. There is also the possibility that many online-only offenders are simply at an earlier stage in their pathway toward violence-endorsing extremism (in comparison to those who have already forged stronger social connections). In our work, 32% were highly engaged with extremist causes and groups while 15% showed high levels of intent regarding future offending. It is therefore hard to conclude that online radicalization results in, more or less, harmless offenders.
In terms of overall prevalence, the studies that offer a breakdown over time ( Jensen et al., 2018 ; Hamid and Ariza, 2022 ; Kenyon et al., 2022b ) indicate that exclusive or predominant online radicalization has been on the rise until recently, and most likely still is. Although the percentages are comparatively low, they are markedly above zero. Indeed, most of the discussion surrounding online radicalization follows a particular logic whereby risks and threats are described as comparatively low, not negligible. In this context, it also needs to be considered that mixed forms of radicalization, involving some form of online activity, are becoming the norm. For these offenders, our previous work ( Kenyon et al., 2022a ) has shown some of the highest levels of risk: 67% on this radicalization pathway showed high levels of engagement and 48% high levels of intent.
Finally, online radicalization and non-violent (online) offending are still likely to encourage and endorse violence and contribute to the perpetuation of an online culture of extremist beliefs, stabilizing a grievance-based climate that carries the ongoing potential of encouraging acts of violence in others. Given the inherently global outreach of the Internet, this may be one of the strongest arguments to take online influences seriously. The prevalence of hate speech and related materials online can be deemed high, and recent studies in this area have shown that occasional encounters with such online content are experienced by 40% to 50% of younger individuals ( Saha et al., 2019 ; Costello et al., 2020 ). As such there are constant opportunities for the initiation of further radicalization processes within large populations, and no suggestion of any downward trend.
When considering again the empirical evidence for these opposing narratives, it is noteworthy that the few studies that allow for some quantification differ markedly on a range of important dimensions, yet converge, by and large, in their findings. The underlying data sources are mostly openly accessible, with the exception of our work on reports held by HMPPS, the United Kingdom penal system. Looking at a prison-based population comes with several restrictions. Only terrorist actors that are both apprehended and sentenced will undergo this risk assessment. This is in contrast to comprehensive databases of all known terrorist acts. These are incident-based and therefore likely to register more actors. Another variation concerns the way studies can address radicalization as a process and estimate threat. This ranges from assessing the effectiveness and severity of the offense to prospective risk assessments of the individual. Some studies have focused exclusively on jihadi-inspired actors whereas others have covered the whole spectrum of what falls under some definition of extremist ideology. All studies, however, focus on actors based in the Western World, i.e., the United States, Western Europe, and Australia.
The two opposing narratives outlined so far can also be linked to different courses of action regarding prevention and counter-terrorism measures. When focusing on relative risk, any allocation of resources for prevention needs to consider that online radicalization does, at present, not constitute a main source of threat. When focusing on absolute risk, it is crucial to note that exclusive online radicalization does occur, for a non-trivial proportion of all terrorist actors and incidents, and constitutes one established and growing pathway for terrorist activities.
Current limitations and outlook
Online radicalization seems to pose a manageable risk. This evidence is based, however, chiefly on data that falls in the decade from 2010 to 2020. When assessing the present state of affairs and attempting to forecast future developments, a number of unknowns need to be taken into account. The first concerns any effects due to the global COVID-19 pandemic, which since 2020 has altered the modes of work and socializing for large parts of the world population and has increased online activities in many domains of life ( Feldmann et al., 2020 ). Concerns over the effects of the pandemic on extremism are high, and first evidence shows that online extremism may have increased in particular for grievance-based ideologies ( Davies et al., 2021 ). It remains to be seen whether the pandemic has changed and steepened the growth trajectory for online radicalization, but there is at the very least a substantial risk of acceleration.
Another unknown factor concerns, by necessity, the ongoing evolution of the Internet. This concerns both the functionality and accessibility of technologies and their relevance to terrorist activity. For example, adding a virtual reality component to training units could increase the capability of online actors once the technology has become more of a standard for wider populations of users. Further, developments such as the Internet of Things could provide novel forms of both radicalization and attacks ( Henschke, 2021 ; Sullivan and Montasari, 2022 ). These developments also extend to easily accessible attack equipment such as weaponry generated through 3D-printing and promoted on social media ( The Guardian, June, 2022 ).
A final unknown noted here concerns the uncertainty over effect sizes for any indirect harm caused by the perpetuation of extremist online networks and extremist online culture. As noted above, the Internet provides the mechanisms for radicalization and the opportunities for encountering relevant content ( Magdy et al., 2016 ; Hassan et al., 2018 ; Costello et al., 2020 ; Smith et al., 2020 ; Saha et al., 2019 ). Those radicalized online can therefore have effects on others by the endorsement and spreading of propaganda and similar content. A quantification of such indirect harm, however, seems exceedingly difficult at present.
Lastly, the question of generalizability of terrorism-related findings to other forms of grievance-based violence needs revisiting. Many of the considerations in the present work are not confined to terrorism, but can be extended to other forms of grievance-based offending. Evidence on the online radicalization process does not, generally speaking, presuppose any specifics in the domain of terrorism, and findings on information leakage and general offender characteristics are, as pointed out in the beginning, very similar across different forms of grievance-fueled violence ( Capellan, 2015 ; Kenyon et al., 2021a ; Clemmow et al., 2022 ). There is still, however, careful scrutiny required since terrorist offending can comprise much more than immediate acts of violence.
The data bases used to establish prevalence and threat related to online radicalization contain not only violent attackers, but a multitude of roles including supporters, facilitators, recruiters, propagandists and so forth. While upper threat estimates derived from the data are related, by definition, to violent attackers, other roles can still pose a substantial danger to society. In addition, the links to grievance may not be as strong in the context of terrorism as they are for related forms of violence. The most pertinent example concerns the engagement dimension in the ERG22+ reports analyzed in our research ( Kenyon et al., 2022a ). Engagement, within this framework of risk assessment, can refer to immersion in an extremist ideology as much as it can refer to group identification and attachment. While the first type of engagement would imply a strongly held grievance-based belief set, the second may be more a matter of social influence, peer pressure and a need for belonging. Again, this means that terrorism is, on a practical level, treated as a more broadly defined category and shows only partial overlap to the category of grievance-fueled violence.
To return to our initial question, within the domain of terrorism, online radicalization, as a process dominated or entirely guided by Internet-related activity, does occur and poses a discernible threat, although both prevalence and threat level have so far been lower in comparison to other forms of radicalization.
Author contributions
All authors listed have made a substantial, direct, and intellectual contribution to the work and approved it for publication.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
- Bastug M. F., Douai A., Akca D. (2020). Exploring the “demand side” of online radicalization: evidence from the Canadian context . Stud. Conflict Terror. 43 , 616–637. doi: 10.1080/1057610X.2018.1494409 [ CrossRef ] [ Google Scholar ]
- Brooks N., Shaw R. (2022). Fixated and grievance-fuelled persons: Considerations on the dangers of gaps, silos and disconnects . Psychiatry Psychol. Law , 1–17. doi: 10.1080/13218719.2021.1995518 [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Capellan J. A. (2015). Lone wolf terrorist or deranged shooter? A study of ideological active shooter events in the United States, 1970–2014 . Stud. Conflict Terror. 38 , 395–413. doi: 10.1080/1057610X.2015.1008341 [ CrossRef ] [ Google Scholar ]
- Clemmow C., Gill P., Bouhana N., Silver J., Horgan J. (2022). Disaggregating lone-actor grievance-fuelled violence: comparing lone-actor terrorists and mass murderers . Terror. Polit. Viol. 34 , 558–584. doi: 10.1080/09546553.2020.1718661 [ CrossRef ] [ Google Scholar ]
- Clifford B., Powell H. (2019). Encrypted extremism: Inside the English-speaking Islamic state ecosystem on telegram . Washington DC: George Washington University. [ Google Scholar ]
- Conway M. (2016). Determining the role of the internet in violent extremism and terrorism: six suggestions for progressing research . Stud. Conflict Terror. 40 , 77–98. doi: 10.1080/1057610X.2016.1157408 [ CrossRef ] [ Google Scholar ]
- Conway M., McInerney L. (2008). Jihadi video and auto-radicalization: Evidence from an exploratory YouTube study. In European Conference on Intelligence and Security Informatics (pp. 108–118). Heidelberg: Springer.
- Costello M., Barrett-Fox R., Bernatzky C., Hawdon J., Mendes K. (2020). Predictors of viewing online extremism among America’s youth . Youth Soc. 52 , 710–727. doi: 10.1177/0044118X18768115 [ CrossRef ] [ Google Scholar ]
- Davies G., Wu E., Frank R. (2021). A witch’s brew of grievances: the potential effects of COVID-19 on radicalization to violent extremism . Stud. Conflict Terror. , 1–24. doi: 10.1080/1057610X.2021.1923188 [ CrossRef ] [ Google Scholar ]
- Ebbrecht C. K. (2022). Systematic review: risk factors and mechanisms of radicalization in lone-actor grievance-fueled violence . Nordic Psychol. , 1–35. doi: 10.1080/19012276.2022.2074524 [ CrossRef ] [ Google Scholar ]
- Evans A. T., Williams H. J. (2022). How extremism operates online. RAND Corporation. Available at: https://www.rand.org/pubs/perspectives/PEA1458-2.html
- Feldmann A., Gasser O., Lichtblau F., Pujol E., Poese I., Dietzel C., et al.. (2020). The lockdown effect: Implications of the COVID-19 pandemic on internet traffic. In Proceedings of the ACM Internet Measurement Conference (pp. 1–18). ACM.
- Frissen T. (2021). Internet, the great radicalizer? Exploring relationships between seeking for online extremist materials and cognitive radicalization in young adults . Comput. Hum. Behav. 114 :106549. doi: 10.1016/j.chb.2020.106549 [ CrossRef ] [ Google Scholar ]
- Gill P. (2015). Lone actor terrorists: A behavioural analysis . Oxon: Routledge. [ Google Scholar ]
- Gill P., Corner E., Conway M., Thornton A., Bloom M., Horgan J. (2017). Terrorist use of the internet by the numbers: quantifying behaviors, patterns, and processes . Criminol. Public Policy 16 , 99–117. doi: 10.1111/1745-9133.12249 [ CrossRef ] [ Google Scholar ]
- Gill P., Corner E., Thornton A., Conway M. (2015). What are the roles of the internet in terrorism? Measuring online behaviours of convicted UK terrorists. EU FP7 VOX-Pol report. Available at: http://voxpol.eu/what-are-the-roles-of-the-internet-interrorism .
- Gunaratna R., Oreg A. (2010). Al Qaeda’s organizational structure and its evolution . Stud. Conflict Terror. 33 , 1043–1078. doi: 10.1080/1057610X.2010.523860 [ CrossRef ] [ Google Scholar ]
- Hamid N., Ariza C. (2022). Offline versus online radicalization: which is the bigger threat? Tracing outcomes of 439 jihadist terrorists between 2014–2021 in 8 Western countries. GNET report. Available at: https://gnet-research.org/wp-content/uploads/2022/02/GNET-Report-Offline-Versus-Online-Radicalization.pdf
- Hamm M. S., Spaaij R. (2017). The age of lone wolf terrorism . New York: Columbia University Press. [ Google Scholar ]
- Hassan G., Brouillette-Alarie S., Alava S., Frau-Meigs D., Lavoie L., Fetiu A., et al.. (2018). Exposure to extremist online content could lead to violent radicalization: a systematic review of empirical evidence . Int. J. Dev. Sci. 12 , 71–88. doi: 10.3233/DEV-170233 [ CrossRef ] [ Google Scholar ]
- Henschke A. (2021). “ Terrorism and the internet of things: cyber-terrorism as an emergent threat ,” in Counter-terrorism, ethics and technology . eds. Henschke A., Reed A., Robbins S., Miller S. (Cham: Springer; ), 71–87. [ Google Scholar ]
- Herath C., Whittaker J. (2021). Online radicalization: moving beyond a simple dichotomy . Terror. Polit. Viol. , 1–22. doi: 10.1080/09546553.2021.1998008 [ CrossRef ] [ Google Scholar ]
- Hoffman B. (2008). The myth of grass-roots terrorism-why Osama bin Laden still matters . Foreign Aff. 87 , 133–138. [ Google Scholar ]
- Jensen M., James P., LaFree G., Safer-Lichtenstein A., Yates E. (2018). The use of social media by United States extremists. National Consortium for the Study of Terrorism and Responses to Terrorism (START).
- Kenyon J., Baker-Beall C., Binder J. (2021a). Lone-actor terrorism: a systematic literature review . Stud. Conflict Terror. 1–24. doi: 10.1080/1057610X.2021.1892635 [ CrossRef ] [ Google Scholar ]
- Kenyon J., Binder J., Baker-Beall C. (2021b). Exploring the role of the internet in radicalization and offending of convicted extremists. Available at: https://www.gov.uk/government/publications/exploring-the-role-of-the-internet-in-radicalization-and-offending-of-convicted-extremists
- Kenyon J., Binder J. F., Baker-Beall C. (2022a). Online radicalization: Profile and risk analysis of individuals convicted of extremist offences . Legal Criminol. Psychol. 1–17. doi: 10.1111/lcrp.12218 [ CrossRef ] [ Google Scholar ]
- Kenyon J., Binder J. F., Baker-Beall C. (2022b). Understanding the role of the internet in the process of radicalization: an analysis of convicted extremists in England and Wales . Stud. Conflict Terror. , 1–25. doi: 10.1080/1057610X.2022.2065902 [ CrossRef ] [ Google Scholar ]
- Klausen J. (2015). Tweeting the Jihad: social media networks of Western foreign fighters in Syria and Iraq . Stud. Conflict Terror. 38 , 1–22. doi: 10.1080/1057610X.2014.974948 [ CrossRef ] [ Google Scholar ]
- Lloyd M., Dean C. (2015). The development of structured guidelines for assessing risk in extremist offenders . J. Threat Assess. Manag. 2 , 40–52. doi: 10.1037/tam0000035 [ CrossRef ] [ Google Scholar ]
- Macdonald S., Grinnell D., Kinzel A., Lorenzo-Dus N. (2019). Daesh, twitter and the social media ecosystem: a study of outlinks contained in tweets mentioning Rumiyah . RUSI J. 164 , 60–72. doi: 10.1080/03071847.2019.1644775 [ CrossRef ] [ Google Scholar ]
- Macdonald S., Whittaker J. (2019). “Online Radicalization: Contested Terms and Conceptual Clarity”, in Online Terrorist Propaganda, Recruitment, and Radicalization . ed. J. R. Vacca (Boca Raton: CRC Press; ). [ Google Scholar ]
- Magdy W., Darwish K., Abokhodair N., Rahimi A., Baldwin T. (2016). #isisisnotislam or #deportallmuslims? Predicting unspoken views. In Proceedings of the 8th ACM Conference on Web Science (pp. 95–106). ACM.
- Meleagrou-Hitchens A., Kaderbhai N. (2017). Research perspectives on online radicalization: a literature review, 2006–2016 , vol. 19. Dublin: International Centre for the Study of Radicalization, 1–98. [ Google Scholar ]
- Mølmen G. N., Ravndal J. A. (2021). Mechanisms of online radicalization: how the internet affects the radicalization of extreme-right lone actor terrorists . Behav. Sci. Terror. Polit. Aggress. , 1–25. doi: 10.1080/19434472.2021.1993302 [ CrossRef ] [ Google Scholar ]
- National Offender Management Service (2017). ERG22+ & extremism risk screen: Summary and overview . London: Ministry of Justice. [ Google Scholar ]
- Neo L. S. (2019). “ An internet-mediated pathway for online radicalization: RECRO ,” in Combating violent extremism and radicalization in the digital era . eds. Khader M., Neo L. S., Ong G., Tan E., Chin J. (Hershey, PA: IGI Global; ), 197–224. [ Google Scholar ]
- Neumann P. R. (2013). Options and strategies for countering online radicalization in the United States . Stud. Confl. Terror. 36 , 431–459. doi: 10.1080/1057610X.2013.784568 [ CrossRef ] [ Google Scholar ]
- O’Callaghan D., Greene D., Conway M., Carthy J., Cunningham P. (2014). Down the (white) rabbit hole: the extreme right and online recommender systems . Soc. Sci. Comput. Rev. 33 , 459–478. doi: 10.1177/0894439314555329 [ CrossRef ] [ Google Scholar ]
- Pariser E. (2011). The filter bubble: What the internet is hiding from you . London: Penguin Books. [ Google Scholar ]
- Reed A., Whittaker J., Votta F., Looney S. (2019). Radical filter bubbles: Social media personalization algorithms and extremist content . London: Global Research Network on Terrorism and Technology. [ Google Scholar ]
- Reinares F., Garcia-Calvo C., Vicente Á. (2017). Differential association explaining jihadi radicalization in Spain: a quantitative study . CTC Sentinel 10 , 29–34. [ Google Scholar ]
- Rothut S., Schulze H., Hohner J., Greipl S., Rieger D. (2022). Radikalisierung im Internet: Ein systematischer Überblick über Forschungsstand, Wirkungsebenen sowie Implikationen für Wissenschaft und Praxis. Bonn: Core-NRW. [ Google Scholar ]
- Sageman M. (2004). Understanding terror networks . Philadelphia, PA: Pennsylvania University Press. [ Google Scholar ]
- Sageman M. (2008). Leaderless jihad: Terror networks in the 21st century . Philadelphia, PA: University of Pennsylvania Press. [ Google Scholar ]
- Saha K., Chandrasekharan E., De Choudhury M. (2019). Prevalence and psychological effects of hateful speech in online college communities. In Proceedings of the 10th ACM conference on web science (pp. 255–264). [ PMC free article ] [ PubMed ]
- Silke A. (2014). “ Risk assessment of terrorist and extremist prisoners ,” in Prisons, terrorism and extremism: Critical issues in management, radicalization and reform . ed. Silke A. (London: Routledge; ), 108–121. [ Google Scholar ]
- Smith L. G., Wakeford L., Cribbin T. F., Barnett J., Hou W. K. (2020). Detecting psychological change through mobilizing interactions and changes in extremist linguistic style . Comput. Hum. Behav. 108 :106298. doi: 10.1016/j.chb.2020.106298 [ CrossRef ] [ Google Scholar ]
- Speckhard A., Ellenberg M., Morton J., Ash A. (2021). Involuntary celibates’ experiences of and grievance over sexual exclusion and the potential threat of violence among those active in an online incel forum . J. Strat. Secur. 14 , 89–121. doi: 10.5038/1944-0472.14.2.1910 [ CrossRef ] [ Google Scholar ]
- Sullivan A., Montasari R. (2022). “ The use of the internet and the internet of things in modern terrorism and violent extremism ,” in Privacy, security and forensics in the internet of things (IoT) . eds. Montasari R., Carroll F., Mitchell I., Hara S., Bolton-King R. (Cham: Springer; ), 151–165. [ Google Scholar ]
- The Guardian (2022). Meta banned firearms sales. Why are they still available on Facebook and Instagram? Available at: https://www.theguardian.com/technology/2022/jun/15/meta-firearms-sales-facebook-instagram-ghost-guns
- UK Government (2018). CONTEST: The United Kingdom’s strategy for countering terrorism (Revised June 2018). Available at: https://www.gov.uk/government/publications/counter-terrorism-strategy-contest-2018
- UK Home Office (2019). Online harms white paper. Available at: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/793360/Online_Harms_White_Paper.pdf
- Valentini D., Lorusso A. M., Stephan A. (2020). Onlife extremism: dynamic integration of digital and physical spaces in radicalization . Front. Psychol. 11 :524. doi: 10.3389/fpsyg.2020.00524, PMID: [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Von Behr I., Reding A., Edwards C., Gribbon L. (2013). Radicalization in the digital era: the use of the internet in 15 cases of terrorism and extremism. RAND Corporation. Available at: https://www.rand.org/pubs/research_reports/RR453.html
- Weimann G. (2006). Terror on the internet: The new arena, the new challenges . Washington, D.C.: US Institute of Peace Press. [ Google Scholar ]
- Weimann G. (2014). New terrorism and new media (Vol. 2) . Washington, D.C.: Commons Lab of the Woodrow Wilson International Center for Scholars. [ Google Scholar ]
- Whittaker J. (2021). The online behaviors of Islamic state terrorists in the United States . Criminol. Public Policy 20 , 177–203. doi: 10.1111/1745-9133.12537 [ CrossRef ] [ Google Scholar ]
- Whittaker J. (2022). Rethinking online radicalization. Perspectives on . Terrorism 16 , 27–40. [ Google Scholar ]
- Wolfowicz M., Hasisi B., Weisburd D. (2022). What are the effects of different elements of media on radicalization outcomes? A systematic review . Campbell Syst. Rev. 18 :e1244. doi: 10.1002/cl2.1244 [ CrossRef ] [ Google Scholar ]
Skip to content
Read the latest news stories about Mailman faculty, research, and events.
Departments
We integrate an innovative skills-based curriculum, research collaborations, and hands-on field experience to prepare students.
Learn more about our research centers, which focus on critical issues in public health.
Our Faculty
Meet the faculty of the Mailman School of Public Health.
Become a Student
Life and community, how to apply.
Learn how to apply to the Mailman School of Public Health.
Just How Harmful Is Social Media? Our Experts Weigh-In.
A recent investigation by the Wall Street Journal revealed that Facebook was aware of mental health risks linked to the use of its Instagram app but kept those findings secret. Internal research by the social media giant found that Instagram worsened body image issues for one in three teenage girls, and all teenage users of the app linked it to experiences of anxiety and depression. It isn’t the first evidence of social media’s harms. Watchdog groups have identified Facebook and Instagram as avenues for cyberbullying , and reports have linked TikTok to dangerous and antisocial behavior, including a recent spate of school vandalism .
As social media has proliferated worldwide—Facebook has 2.85 billion users—so too have concerns over how the platforms are affecting individual and collective wellbeing. Social media is criticized for being addictive by design and for its role in the spread of misinformation on critical issues from vaccine safety to election integrity, as well as the rise of right-wing extremism. Social media companies, and many users, defend the platforms as avenues for promoting creativity and community-building. And some research has pushed back against the idea that social media raises the risk for depression in teens . So just how healthy or unhealthy is social media?
Two experts from Columbia University Mailman School of Public Health and Columbia Psychiatry share their insights into one crucial aspect of social media’s influence—its effect on the mental health of young people and adults. Deborah Glasofer , associate professor of psychology in psychiatry, conducts psychotherapy development research for adults with eating disorders and teaches about cognitive behavioral therapy. She is the co-author of the book Eating Disorders: What Everyone Needs to Know. Claude Mellins , Professor of medical psychology in the Departments of Psychiatry and Sociomedical Sciences, studies wellbeing among college and graduate students, among other topics, and serves as program director of CopeColumbia, a peer support program for Columbia faculty and staff whose mental health has been affected by the COVID-19 pandemic. She co-led the SHIFT research study to reduce sexual violence among undergraduates. Both use social media.
What do we know about the mental health risks of social media use?
Mellins : Facebook and Instagram and other social media platforms are important sources of socialization and relationship-building for many young people. Although there are important benefits, social media can also provide platforms for bullying and exclusion, unrealistic expectations about body image and sources of popularity, normalization of risk-taking behaviors, and can be detrimental to mental health. Girls and young people who identify as sexual and gender minorities can be especially vulnerable as targets. Young people’s brains are still developing, and as individuals, young people are developing their own identities. What they see on social media can define what is expected in ways that is not accurate and that can be destructive to identity development and self-image. Adolescence is a time of risk-taking, which is both a strength and a vulnerability. Social media can exacerbate risks, as we have seen played out in the news.
Although there are important benefits, social media can also provide platforms for bullying and exclusion, unrealistic expectations about body image and sources of popularity, normalization of risk-taking behaviors, and can be detrimental to mental health. – Claude Mellins
Glasofer : For those vulnerable to developing an eating disorder, social media may be especially unhelpful because it allows people to easily compare their appearance to their friends, to celebrities, even older images of themselves. Research tells us that how much someone engages with photo-related activities like posting and sharing photos on Facebook or Instagram is associated with less body acceptance and more obsessing about appearance. For adolescent girls in particular, the more time they spend on social media directly relates to how much they absorb the idea that being thin is ideal, are driven to try to become thin, and/or overly scrutinize their own bodies. Also, if someone is vulnerable to an eating disorder, they may be especially attracted to seeking out unhelpful information—which is all too easy to find on social media.
Are there any upsides to social media?
Mellins : For young people, social media provides a platform to help them figure out who they are. For very shy or introverted young people, it can be a way to meet others with similar interests. During the pandemic, social media made it possible for people to connect in ways when in-person socialization was not possible. Social support and socializing are critical influences on coping and resilience. Friends we couldn’t see in person were available online and allowed us important points of connection. On the other hand, fewer opportunities for in-person interactions with friends and family meant less of a real-world check on some of the negative influences of social media.
Whether it’s social media or in person, a good peer group makes the difference. A group of friends that connects over shared interests like art or music, and is balanced in their outlook on eating and appearance, is a positive. – Deborah Glasofer
Glasofer : Whether it’s social media or in person, a good peer group makes the difference. A group of friends that connects over shared interests like art or music, and is balanced in their outlook on eating and appearance, is a positive. In fact, a good peer group online may be protective against negative in-person influences. For those with a history of eating disorders, there are body-positive and recovery groups on social media. Some people find these groups to be supportive; for others, it’s more beneficial to move on and pursue other interests.
Is there a healthy way to be on social media?
Mellins : If you feel social media is a negative experience, you might need a break. Disengaging with social media permanently is more difficult—especially for young people. These platforms are powerful tools for connecting and staying up-to-date with friends and family. Social events, too. If you’re not on social media then you’re reliant on your friends to reach out to you personally, which doesn’t always happen. It’s complicated.
Glasofer : When you find yourself feeling badly about yourself in relation to what other people are posting about themselves, then social media is not doing you any favors. If there is anything on social media that is negatively affecting your actions or your choices—for example, if you’re starting to eat restrictively or exercise excessively—then it’s time to reassess. Parents should check-in with their kids about their lives on social media. In general, I recommend limiting social media— creating boundaries that are reasonable and work for you—so you can be present with people in your life. I also recommend social media vacations. It’s good to take the time to notice the difference between the virtual world and the real world.
Internet is dangerous .Do you agree or disagree to this.
Unauthorized use and/or duplication of this material without express and written permission from this site’s author and/or owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Writing9 with appropriate and specific direction to the original content.
Fully explain your ideas
To get an excellent score in the IELTS Task 2 writing section, one of the easiest and most effective tips is structuring your writing in the most solid format. A great argument essay structure may be divided to four paragraphs, in which comprises of four sentences (excluding the conclusion paragraph, which comprises of three sentences).
For we to consider an essay structure a great one, it should be looking like this:
- Paragraph 1 - Introduction
- Sentence 1 - Background statement
- Sentence 2 - Detailed background statement
- Sentence 3 - Thesis
- Sentence 4 - Outline sentence
- Paragraph 2 - First supporting paragraph
- Sentence 1 - Topic sentence
- Sentence 2 - Example
- Sentence 3 - Discussion
- Sentence 4 - Conclusion
- Paragraph 3 - Second supporting paragraph
- Paragraph 4 - Conclusion
- Sentence 1 - Summary
- Sentence 2 - Restatement of thesis
- Sentence 3 - Prediction or recommendation
Our recommended essay structure above comprises of fifteen (15) sentences, which will make your essay approximately 250 to 275 words.
Discover more tips in The Ultimate Guide to Get a Target Band Score of 7+ » — a book that's free for 🚀 Premium users.
- Check your IELTS essay »
- Find essays with the same topic
- View collections of IELTS Writing Samples
- Show IELTS Writing Task 2 Topics
1.Please share your motivation for undertaking this programme?1.Please share your motivation for undertaking this programme?
Climate change is a big environmental problem that has become critical in the last couple of decades. some people claim that humans should stop burning fossil fuels and use only alternative energy resources, such as wind and solar power. others say that oil, gas and coal are essential for many industries, and not using them will lead to economic collapse. what is your opinion support your point of view with relevant examples., at the present time, the population of some countries includes relatively large number of young adults, compared with the number of older people. do the advantages of this situation outweigh the disadvantages, your manager has asked you to arrange a party for a colleague leaving the company. write a letter to your manager. in your letter suggest a suitable date and time for the party recommend a venue propose the food and entertainment options that should be available., the given graph shows the nitrogen oxide emissions produced by four vehicles. summarise the information by selecting and reporting the main features, and make comparisons where relevant..
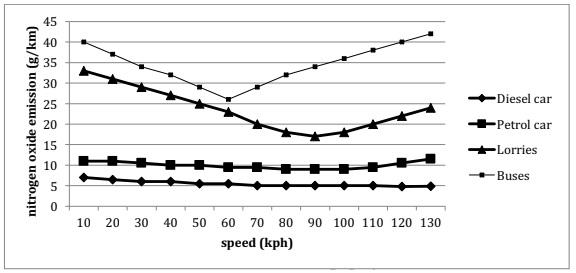

A Latina Harvard grad advised women to marry older men. The internet had thoughts.
W hen she was 20 years old and a junior at Harvard College, Grazie Sophia Christie had an epiphany. She could study hard and diligently pursue her “ideal existence” though years of work and effort.
Or she “could just marry it early.”
Christie chose the latter.
In a column for New York magazine’s The Cut, the Cuban American editor and writer extolled the value of marrying an older, wealthier man as a shortcut to the life she desired. Christie’s March 27 story went viral, topping the magazine’s “most popular” list and inspiring hundreds of overwhelmingly negative comments online and on social media. As Miami New Times described it , “The essay hit the internet with a virtual thud heard round the world.”
Readers were taken aback by myriad aspects of Christie’s florid essay, which runs nearly 4,000 words. Though she was an undergraduate, Christie lugged “a heavy suitcase of books each Saturday to the Harvard Business School,” which she felt offered the best options for a suitable mate. “I had high breasts, most of my eggs, plausible deniability when it came to purity, a flush ponytail, a pep in my step that had yet to run out," she wrote. "Older men still desired those things.”
She crashed an event at the Harvard Business School and met her future husband when she was 20, and they married four years later.
Many readers were struck by the fact that Christie had the benefit of an elite education — she also completed a fellowship at Oxford University — yet chose to enter into an unequal marriage. “My husband isn’t my partner. He’s my mentor, my lover, and, only in certain contexts, my friend,” she writes. “I’ll never forget it, how he showed me around our first place like he was introducing me to myself. This is the wine you’ll drink, where you’ll keep your clothes, we vacation here; this is the other language we’ll speak, you’ll learn it and I did.”
Christie, now 27, writes that she enjoys time “to read, to walk central London and Miami and think in delicious circles.”
There is, Christie writes, a downside to her monied existence: “I live in an apartment whose rent he pays and that shapes the freedom with which I can ever be angry with him. He doesn’t have to hold it over my head, it just floats there, complicating usual shorthands to explain dissatisfaction.”
By marrying so young — although as many social media users pointed out, her husband is only 10 years older — Christie was able to leave a “lucrative but deadening spreadsheet job to write full-time, without having to live like a writer.”
A recurring theme in the viral response to Christie’s article, ostensibly about age-gap relationships, is that it should have been titled “The Case for Marrying a Rich Man.”
Christie’s transactional approach to marriage and relationships resonated — negatively — with readers. An online parody of her original piece has already been posted by the literary magazine McSweeney’s. Her words have been dissected by a columnist at Slate, who called it “bad advice for most human beings, at least if what most human beings seek are meaningful and happy lives.”
Online, people who commented on Christie’s essay called it “an insult to women of any age,” “a sad piece of writing,” and “pitiful in so many ways.” Some readers wondered if the article was a satire or a joke. One of the kinder comments on New York magazine’s website said: “This is one of the most embarrassing things I have ever read. I am truly mortified for the writer.”
Christie has so far not responded to media requests for interviews, and several attempts by NBC News to contact her were unsuccessful. Her Instagram account was recently switched from public to private.
According to her personal website , Christie is editor-in-chief of a new publication, The Miami Native, “a serious magazine about an unserious city.” Her website’s bio page, which appears to have been disabled, previously stated that she was “writing a novel between Miami, London, sometimes France.”
Christie grew up in Miami. Her parents, Miami New Times has reported , are prominent in Florida’s conservative Catholic community. Her mother was appointed to the state Board of Education in March 2022. A senior fellow for The Catholic Association, she hosts a radio show , “Conversations with Consequences,” on the Eternal Word Television Network. Her father is a physician and an anti-abortion activist who, according to his website , lectures regularly on Catholic social issues, particularly marriage, family, and the dignity of life.”
For more from NBC Latino, sign up for our weekly newsletter .
This article was originally published on NBCNews.com

Is a robot writing your kids’ essays? We asked educators to weigh in on the growing role of AI in classrooms.
Educators weigh in on the growing role of ai and chatgpt in classrooms..

Remember writing essays in high school? Chances are you had to look up stuff in an encyclopedia — an actual one, not Wikipedia — or else connect to AOL via a modem bigger than your parents’ Taurus station wagon.
Now, of course, there’s artificial intelligence. According to new research from Pew, about 1 in 5 US teens who’ve heard of ChatGPT have used it for schoolwork. Kids in upper grades are more apt to have used the chatbot: About a quarter of 11th- and 12th-graders who know about ChatGPT have tried it.
For the uninitiated, ChatGPT arrived on the scene in late 2022, and educators continue to grapple with the ethics surrounding its growing popularity. Essentially, it generates free, human-like responses based on commands. (I’m sure this sentence will look antiquated in about six months, like when people described the internet as the “information superhighway.”)
Advertisement
I used ChatGPT to plug in this prompt: “Write an essay on ‘The Scarlet Letter.’” Within moments, ChatGPT created an essay as thorough as anything I’d labored over in AP English.
Is this cheating? Is it just part of our strange new world? I talked to several educators about what they’re seeing in classrooms and how they’re monitoring it. Before you berate your child over how you wrote essays with a No. 2 pencil, here are some things to consider.
Adapting to new technology isn’t immoral. “We have to recalibrate our sense of what’s acceptable. There was a time when every teacher said: ‘Oh, it’s cheating to use Wikipedia.’ And guess what? We got used to it, we decided it’s reputable enough, and we cite Wikipedia all the time,” says Noah Giansiracusa, an associate math professor at Bentley University who hosts the podcast “ AI in Academia: Navigating the Future .”
“There’s a calibration period where a technology is new and untested. It’s good to be cautious and to treat it with trepidation. Then, over time, the norms kind of adapt,” he says — just like new-fangled graphing calculators or the internet in days of yore.
“I think the current conversation around AI should not be centered on an issue with plagiarism. It should be centered on how AI will alter methods for learning and expressing oneself. ‘Catching’ students who use fully AI-generated products ... implies a ‘gotcha’ atmosphere,” says Jim Nagle, a history teacher at Bedford High School. “Since AI is already a huge part of our day-to-day lives, it’s no surprise our students are making it a part of their academic tool kit. Teachers and students should be at the forefront of discussions about responsible and ethical use.”

Teachers and parents could use AI to think about education at a higher level. Really, learning is about more than regurgitating information — or it should be, anyway. But regurgitation is what AI does best.
“If our system is just for students to write a bunch of essays and then grade the results? Something’s missing. We need to really talk about their purpose and what they’re getting out of this, and maybe think about different forms of assignments and grading,” Giansiracusa says.
After all, while AI aggregates and organizes ideas, the quality of its responses depends on the users’ prompts. Instead of recoiling from it, use it as a conversation-starter.
“What parents and teachers can do is to start the conversation with kids: ‘What are we trying to learn here? Is it even something that ChatGPT could answer? Why did your assignment not convince you that you need to do this thinking on your own when a tool can do it for you?’” says Houman Harouni , a lecturer on education at the Harvard Graduate School of Education.
Harouni urges parents to read an essay written by ChatGPT alongside their student. Was it good? What could be done better? Did it feel like a short cut?
“What they’re going to remember is that you had that conversation with them; that someone thought, at some point in their lives, that taking a shortcut is not the best way ... especially if you do it with the tool right in front of you, because you have something real to talk about,” he says.
Harouni hopes teachers think about its implications, too. Consider math: So much grunt work has been eliminated by calculators and computers. Yet kids are still tested as in days of old, when perhaps they could expand their learning to be assessed in ways that are more personal and human-centric, leaving the rote stuff to AI.
“We could take this moment of confusion and loss of certainty seriously, at least in some small pockets, and start thinking about what a different kind of school would look like. Five years from now, we might have the beginnings of some very interesting exploration. Five years from now, you and I might be talking about schools wherein teaching and learning is happening in a very self-directed way, in a way that’s more based on … igniting the kid’s interest and seeing where they go and supporting them to go deeper and to go wider,” Harouni says.
Teachers have the chance to offer assignments with more intentionality.
“Really think about the purpose of the assignments. Don’t just think of the outcome and the deliverable: ‘I need a student to produce a document.’ Why are we getting students to write? Why are we doing all these things in the first place? If teachers are more mindful, and maybe parents can also be more mindful, I think it pushes us away from this dangerous trap of thinking about in terms of ‘cheating,’ which, to me, is a really slippery path,” Giansiracusa says.
AI can boost confidence and reduce procrastination. Sometimes, a robot can do something better than a human, such as writing a dreaded resume and cover letter. And that’s OK; it’s useful, even.
“Often, students avoid applying to internships because they’re just overwhelmed at the thought of writing a cover letter, or they’re afraid their resume isn’t good enough. I think that tools like this can help them feel more confident. They may be more likely to do it sooner and have more organized and better applications,” says Kristin Casasanto, director of post-graduate planning at Olin College of Engineering.
Casasanto says that AI is also useful for de-stressing during interview prep.
“Students can use generative AI to plug in a job description and say, ‘Come up with a list of interview questions based on the job description,’ which will give them an idea of what may be asked, and they can even then say, ‘Here’s my resume. Give me answers to these questions based on my skills and experience.’ They’re going to really build their confidence around that,” Casasanto says.
Plus, when students use AI for basics, it frees up more time to meet with career counselors about substantive issues.
“It will help us as far as scalability. … Career services staff can then utilize our personal time in much more meaningful ways with students,” Casasanto says.
We need to remember: These kids grew up during a pandemic. We can’t expect kids to resist technology when they’ve been forced to learn in new ways since COVID hit.
“Now we’re seeing pandemic-era high school students come into college. They’ve been channeled through Google Classroom their whole career,” says Katherine Jewell, a history professor at Fitchburg State University.
“They need to have technology management and information literacy built into the curriculum,” Jewell says.
Jewell recently graded a paper on the history of college sports. It was obvious which papers were written by AI: They didn’t address the question. In her syllabus, Jewell defines plagiarism as “any attempt by a student to represent the work of another, including computers, as their own.”
This means that AI qualifies, but she also has an open mind, given students’ circumstances.
“My students want to do the right thing, for the most part. They don’t want to get away with stuff. I understand why they turned to these tools; I really do. I try to reassure them that I’m here to help them learn systems. I’m focusing much more on the learning process. I incentivize them to improve, and I acknowledge: ‘You don’t know how to do this the first time out of the gate,’” Jewell says. “I try to incentivize them so that they’re improving their confidence in their abilities, so they don’t feel the need to turn to these tools.”
Understand the forces that make kids resort to AI in the first place . Clubs, sports, homework: Kids are busy and under pressure. Why not do what’s easy?
“Kids are so overscheduled in their day-to-day lives. I think there’s so much enormous pressure on these kids, whether it’s self-inflicted, parent-inflicted, or school-culture inflicted. It’s on them to maximize their schedule. They’ve learned that AI can be a way to take an assignment that would take five hours and cut it down to one,” says a teacher at a competitive high school outside Boston who asked to remain anonymous.
Recently, this teacher says, “I got papers back that were just so robotic and so cold. I had to tell [students]: ‘I understand that you tried to use a tool to help you. I’m not going to penalize you, but what I am going to penalize you for is that you didn’t actually answer the prompt.”
Afterward, more students felt safe to come forward to say they’d used AI. This teacher hopes that age restrictions become implemented for these programs, similar to apps such as Snapchat. Educationally and developmentally, they say, high-schoolers are still finding their voice — a voice that could be easily thwarted by a robot.
“Part of high school writing is to figure out who you are, and what is your voice as a writer. And I think, developmentally, that takes all of high school to figure out,” they say.
And AI can’t replicate voice and personality — for now, at least.
Kara Baskin can be reached at [email protected] . Follow her @kcbaskin .
- Share full article
Advertisement
Supported by
Jane Coaston
What the TikTok Bill Is Really About, According to a Leading Republican

By Jane Coaston
Ms. Coaston is a contributing Opinion writer.
Last month, the House passed a bill that would require TikTok’s parent company to sell its U.S. business to a company without ties to the Chinese government, or face a ban of the TikTok app in the United States.
In Washington, which has become increasingly hawkish toward the Chinese government, worries and fears about the Chinese Communist Party’s role in ByteDance are widespread. But outside Capitol Hill, millions of people — especially younger Americans — use TikTok everyday for entertainment and increasingly for search. Even beyond the potential speech or other legal issues, if this bill becomes law and a divestiture doesn’t work, those people might be pretty surprised if they were no longer able to download or update the TikTok app.
Representative Mike Gallagher, the Wisconsin Republican, is a co-sponsor of the legislation — he’s about to leave Congress but if this becomes law, it will have an effect on social media and U.S.-China relations long after his departure. Many lawmakers in both parties are concerned about the effects of social media on teens. Mr. Gallagher’s much more concerned about the Chinese government, and we spoke about speech concerns, the message to authoritarian governments from a bill like this and how Donald Trump’s fluctuating support affects the chances the bill will actually become reality.
This interview has been edited for length and clarity and is part of an Opinion Q. and A. series exploring modern conservatism today, its influence in society and politics and how and why it differs (and doesn’t) from the conservative movement that most Americans thought they knew.
Jane Coaston: So what’s the scenario with TikTok that you fear the most? Data theft, misinformation, tracking generations of Americans, and then using their information and attention against ‘em — or something duller than what I’m imagining.
Representative Mike Gallagher: There are two threats. One is what you could call the espionage threat. It’s data security — using the app to find Americans, exfiltrate data, track the location of journalists, etc. We have incidences of this happening already that are in the public domain. That’s a serious threat, but I actually think the greater concern is the propaganda threat. If TikTok continues to establish itself as the dominant news platform in America, and if the algorithm remains a black box and subject to the control of ByteDance and by extension the Chinese Communist Party, you’re placing the control of information — like what information America’s youth gets — in the hands of America’s foremost adversary. And that’s a risk I don’t think we can afford to take. Obviously, there’s well-established precedent when it comes to traditional media for foreign ownership, which is why we think a divestiture is the most prudent way to guard against both of those threats.
[ In 2022, Forbes reported that TikTok employees pulled the IP addresses and user information of three reporters to monitor their whereabouts after the reporters published a critical article about ByteDance; TikTok said the employees were no longer employed by the company. ]
Coaston: Let’s say I’m 19 years old, I’m in college. I use TikTok for normal stuff. Make the case to me that there’s a security risk.
Gallagher: We have already examples of TikTok, as I mentioned before, spying on journalists. TikTok has not been truthful about where its data was housed in the past, and using TikTok’s own metrics when it comes to comparing content on that platform versus Instagram — recognizing it’s not an apple-to-apples comparison based on the different way the apps work — there are disparities that don’t make any sense. It can’t be explained away by sounding variables such as the fact that TikTok doesn’t operate in India. And the closer you get to the topics that are sensitive to the Chinese Communist Party — whether it’s Covid origins, whether it’s the Uyghur genocide, whether it’s Hong Kong, etc. — the disparities get more and more severe. Again, this gets back to the black box nature of the algorithm. But the other thing I would say to that 19-year-old who wants to continue to use TikTok, that’s fine. In the scenario that our bill envisions, once the ownership structure changes, the national security concerns are substantially alleviated. I see no reason the user experience can not only continue but also improve.
[ Earlier this year, TikTok limited access to a tool that researchers used to track trending topics on the platform. In the past, groups like the Network Contagion Research Institute at Rutgers University have found that based on tags, certain topics, like protests about increasing anti-democratic measures in Hong Kong and reports of the confinement and forced labor of Uyghur Muslims in China, are underrepresented on TikTok compared with Instagram. TikTok has said that the Chinese government has no influence over the app. ]
Coaston: How much have you used TikTok? Do you have a burner phone with TikTok on it by any chance?
Gallagher: I do not. I don’t really use social media at all. I have a staff account — but I made that decision about six years ago, I think, to remove myself personally from it. I don’t have it on my phone. And that was more to me a matter of wanting to be effective, and I found myself not having the time I wanted to do deep thinking and writing and researching, and the minute I got off it, the more my productivity improved. Now that’s just me personally; I just don’t find it useful. There are occasions when I would use Twitter to sort of monitor various Chinese Communist Party propaganda accounts during the pandemic. I became fascinated with what they were doing to spread kind of dangerous anti-American rhetoric on our platforms.
People will send me TikTok videos sometimes as examples, but I don’t have the app even on a burner phone. I do think when we’re talking about all this stuff — social media companies in America and China — a principle underlying all of it has to be reciprocity. As we have this debate about how and whether to regulate a foreign adversary-controlled social media application in the United States, it’s worth remembering that our social media applications are not allowed in China. There’s just a basic lack of reciprocity and your Chinese citizens don’t have access to them. And yet we allow Chinese government officials to go all over YouTube, Facebook and X spreading lies about America. I think this is a microcosm with a broader lack of reciprocity in the entire U.S.-China relationship. And I do think as a matter of principle, it puts us on firm ground to address this issue.
Coaston: Jameel Jaffer at the Knight First Amendment Institute recently said on X, “a U.S. TikTok ban would be a gift to authoritarian regimes around the world.” There’s also an argument that banning an app in the same way that the Chinese communists do, as you just mentioned, is basically a propaganda win for China. How should conservative China hawks be thinking about the messages that this ban might send worldwide?
Gallagher: Which is why it’s not structured as a ban and why TikTok lies about it being an outright ban. That argument backfired — and I think the push notification they forced on millions of users actually sort of proved our point about the concerns with how the tool could be weaponized to inject disinformation into the American legislative process and the democratic process. The outcome we’re trying to navigate toward is a divestiture or a sale or a separation. I actually think that’s an outcome that American investors in ByteDance should want. We’re not talking about an outright ban; we’re trying to force a sale. Now you need a mechanism to force the sale, to be sure. I also would disagree that the bill addresses content or speech; it’s about conduct, specifically foreign adversary control of social media.
[ TikTok has sent messages to users to call their representatives, which resulted in widespread calls to congressional offices. ]
Coaston: So there are some Republican lawmakers who seem most concerned with the mental health of young people rather than something specific to Chinese ownership. In states like Utah, where I live, there are efforts to restrict teen social media usage more broadly. Are you in favor of that more expansive, less libertarian approach to social media and big tech for younger people? For adults?
Gallagher: Well, I think I need to caveat this: I share the concerns, but it’s a separate issue than what this bill is trying to address. What I’m narrowly trying to address with this bill is foreign adversary control of a dominant social media platform and news platform in the United States. Now, once we address that issue, then we can have a bigger debate about the effect of social media more broadly to include American social media companies. I’ve been persuaded by Jonathan Haidt’s work, both in the previous book he wrote with Greg Lukianoff, “The Coddling of the American Mind,” and then Haidt’s book that just came out, “The Anxious Generation,” that it is strongly correlated with the skyrocketing rate of anxiety and depression that we’re seeing among Gen Z. I think it’s worthy of government attention. There’s not an obvious government solution that I’ve been able to address. In fact, right now, my instinct is that it is my responsibility as a parent to set guardrails and not rely on the government to do it for me.
You could, however, and I think this is where Haidt’s analysis has been very persuasive, entertain raising the internet age of adulthood. And that is something that I haven’t seen a piece of legislation yet that I’m ready to co-sponsor, but the idea makes sense to me and I think there would be government authority to do that if we decided to do that. But again, that is not what this bill is about.
The other idea, which I think is sensible but doesn’t lend itself to federal legislation — though there might be state and local efforts at the school-district level — is finding a way to incentivize, if not mandate phone-free schools. Haidt’s analysis is very good at highlighting the benefits of doing that. But again, that’s not something I would legislate as a member of Congress, if that makes sense. As a parent, I’m terrified about the corrosive impact of social media — I even see it among my colleagues and I referenced my own experience and how social media I think really sapped my own productivity. I think there’s a way in which it precludes us from having a serious debate on certain policy issues because there’s no shared epistemological framework. We’re debating what is true and what isn’t, and we spend all our time on that and we never get to the actual debate over policy. But again, that’s just a broader issue and it’s not addressed by our bill right now.
Coaston: So Donald Trump supported banning TikTok and now he doesn’t. How much harder does that make it for Republicans to vote for this legislation?
Gallagher: So in many ways I was surprised by his statement because a lot of this started with Trump. I mean, he was ahead of the curve when he tried to address the national security problems posed by ByteDance ownership of TikTok. And our bill is an extension of that effort. Obviously his effort ran into a legal buzz saw. We tried to learn from that and draft the bill in a way where it would survive a legal challenge and was on the strongest constitutional grounds. The bill is not trying to shut TikTok down and then force all its users onto Facebook. So if that’s the former president’s concern, then this bill should not worry him because that is not the intent and that I don’t think is what would practically happen. And then we had the vote after he made the statement, and we still got 352 votes. I think that just shows that there’s serious bipartisan concerns about ByteDance’s ownership of TikTok, excuse me, and either this administration or the next administration, which could be the Trump administration, is going to have to address it.
After the interview, I followed up with Mr. Gallagher in email on a few points. These have also been edited for length and clarity.
Coaston: Conservatives also used to be pretty leery of government control and intervention. The approach of many conservatives to TikTok feels to me like “government knows best” and “government will call the shots.” Did conservatives change their way of thinking, or is China just scaring the hell out of them?
Gallagher: There’s a clear precedent of the government protecting Americans from national security threats posed by foreign-adversary-controlled applications and preventing our foreign adversaries from influencing the American airwaves. For a century, the Federal Communications Commission has blocked concentrated foreign ownership of radio and television assets on national security grounds, and in 2020, CFIUS (the Committee on Foreign Investment in the United States) forced a divestment of the app Grindr, citing national security concerns stemming from its Chinese ownership.
Coaston: Clearly, there are a lot of younger people who would be upset if a divestment didn’t work and TikTok no longer operated in the United States. How do you think about the politics of that?
Gallagher: Fortunately for the kids, this bill presents a great opportunity for ByteDance to divest of TikTok and continue operating in the United States. This decision is squarely in TikTok’s hands.
The Times is committed to publishing a diversity of letters to the editor. We’d like to hear what you think about this or any of our articles. Here are some tips . And here’s our email: [email protected] .
Follow the New York Times Opinion section on Facebook , Instagram , TikTok , WhatsApp , X and Threads .
Jane Coaston was the host of Opinion’s podcast “ The Argument .” Previously, she reported on conservative politics, the G.O.P. and the rise of the right. She also co-hosted the podcast “The Weeds.” @ janecoaston
Exhausted, hungry and sleep-deprived: UCLA student super-commuters search for relief

- Show more sharing options
- Copy Link URL Copied!
Sofia Gevorgian’s life as a college student revolves around her nearly one-hour commute to and from UCLA’s campus in Westwood and her family home in the San Fernando Valley.
During her first year, she would race home after the last class of the day around noon, forgoing clubs and social events typically hosted in the evening so she could beat traffic and get home in 30 minutes rather than an hour or more. This year, she’s trying a different strategy: stay at school until 7:30 p.m. to attend office hours and club meetings, and sometimes even later to participate in intramural soccer games.
But the 10-hour-plus school day takes its toll on her, she said.
“I’m just sacrificing so much energy,” she said. “Making the drive home at night when you’re tired is in of itself exhausting, coupled in with being on campus all day to attend classes and clubs. It’s all a lot.”
To alleviate stresses on student commuters who — unlike campus resident students — have no place to settle down and can feel isolated, UCLA is creating “BruinHubs” where they can rest and study before and after class. The hubs are complete with napping pods, study tables, charging stations, snacks, a microwave and a refrigerator to store meals for their long day on campus.

“Naturally disadvantaged academically by their commute, they don’t have enough time in their days to sleep, study or get together with their study groups,” Dana Cuff, a professor of architecture and urban design at UCLA, said at a recent UC Regents meeting.
The need is great. Nearly half of UCLA’s undergraduate students and the majority of its graduate students live off campus — and 43% of those students commute more than an hour each way, Cuff said.
The push to expand commuter hubs comes as UCLA students, staff and faculty face a lack of affordable housing near campus, said Monroe Gorden, vice chancellor of student affairs.

UC stirs furious debate over what high school math skills are needed to succeed in college
The University of California is weighing what kind of data science classes could count as math for admission, sparking debate over equity and access.
March 19, 2024
Fourth-year student Darlene Luna Barahona lives in Santa Clarita. She hits the freeways around 7 a.m. to brave her hour-and-a-half commute to campus. The 21-year-old transferred from College of the Canyons, a community college in Santa Clarita, last school year with a financial aid package that she would rather go toward her tuition than university-affiliated housing — which can cost more than $1,800 per month.
Before starting her part-time job at UCLA’s Transfer Student Center this year, the BruinHub in the John Wooden Center, also home to UCLA’s main gym, was Barahona’s go-to spot after classes to wait out traffic.
“This is my pod,” she laughed, pointing to the pink resting pod in the corner. “I would come here a lot and sit and work on homework and prepare for midterms and finals.”
The resting pods are carved wooden capsules with a small curtain for privacy. Inside the pod, a reading light and outlet allow students to work lying down or sitting up. The colorful furniture and polka dots painted on the tall white walls under fluorescent lighting give a playful feel to the hub.

This BruinHub opened in fall 2021, re-purposed from an under-used racquetball court. It is open from 5:15 a.m. for early commuters to 1 a.m. A second BruinHub was re-purposed inside a conference room and opened this winter quarter in the Strathmore Building, which also houses UCLA’s Basic Needs Center that provides emergency housing and food for students in need.
A shortage of campus study spaces, particularly during finals, and a lack of places where students could prepare food made it difficult for student commuters to get work done, eat, lie down and recharge phones and laptops.
“There’s a time I didn’t bring food at all, because I didn’t want to spend money on campus, so I would just bring snacks because I knew I needed to eat and I didn’t want to carry my lunch with me the whole day,” Barahona said of her time before she discovered the BruinHubs.
Dominique Peñate, program coordinator for commuter support and programs, knows the struggles of student commuters all too well, having commuted from South Gate before graduating from UCLA in 2022
“Some students stack their classes and try to only come in twice a week to save on gas and parking, and I used to do the same,” she said.
Gevorgian said the BruinHubs are a good start toward addressing student commuter needs. But she called on the university to offer more online class availability for commuter students and more lenient in-person attendance policies, particularly when bad weather makes driving dangerous. She also advocates for student commuters to have priority to register for UCLA’s limited online course offerings.
“We had the atmospheric rain, really heavy floods last month and professors were still requiring students to come in person and that is a danger to the students themselves,” Gervorgian said. “And if they do choose to stay home, then they would be missing out on class, so that leaves a negative educational impact on the students.”
“I feel like UCLA underestimates how essential it is to have online classes as an option,” Barahona said. “For commuters, it’s just easier to have that option for Zoom.”

UC applications rise for fall 2024, with gains in diversity and transfer applicants
University of California applications rose to 250,000 for fall, driven by a rebound in transfer applicants and gains in racial, ethnic and socioeconomic diversity.
March 6, 2024
UCLA is in discussions to build more BruinHubs in its libraries, in its new 11-story Trust Building in downtown L.A. and at its satellite campus at the former Marymount California University site in Rancho Palos Verdes , Peñate said.
The BruinHubs are not intended to be a substitute for students in need of housing, but to allow the university to tap into underused spaces and re-create them into a space that can help student commuters, Gorden said.
“The BruinHub allows us to think about those niche areas where sometimes students make conscious decisions of where they are living,” he said. “But we do have a need to think about the longer-term housing needs of our students.”
More to Read

How student housing around USC is transforming a historic Black and Latino neighborhood
March 20, 2024

Inside UCLA gymnast Emma Malabuyo’s push to juggle classes and qualify for the Olympics
Feb. 16, 2024

SoCal housing crisis makes commute times worse. But the rich get a traffic break
Dec. 13, 2023
Start your day right
Sign up for Essential California for news, features and recommendations from the L.A. Times and beyond in your inbox six days a week.
You may occasionally receive promotional content from the Los Angeles Times.

Ashley Ahn is a 2023-24 reporting fellow at the Los Angeles Times. She has previously interned at CNN, USA Today, NPR and Foreign Policy Magazine. Ahn is from Georgia and a graduate of the University of Pennsylvania.
More From the Los Angeles Times

Powerful unions allege schools are misusing arts education money, demand state intervention
April 1, 2024

Former official pleads guilty to embezzling nearly $16 million from O.C. school district
March 29, 2024

Is your child struggling to master the potty? These 5 takeaways from our panel can help
March 28, 2024

World & Nation
Should college essays touch on race? Some say affirmative action ruling leaves them no choice
March 27, 2024
Find anything you save across the site in your account
How Chinese Students Experience America
By Peter Hessler

In my composition class at Sichuan University, in the southwestern Chinese city of Chengdu, the first assignment was a personal essay. I gave some prompts in case students had trouble coming up with topics. One suggestion was to describe an incident in which the writer had felt excluded from a group. Another was to tell how he or she had responded when some endeavor went unexpectedly wrong. For the third prompt, I wrote:
Have you ever been involved in a situation that was extremely threatening, or dangerous, or somehow dramatic? Tell the story, along with what you learned.
It was September, 2019, and the class consisted of engineering majors who were in their first month at university. Like virtually all Chinese undergraduates, they had been admitted solely on the basis of scores on the gaokao , the national college-entrance examination. The gaokao is notorious for pressure, and most of my students chose to write about some aspect of their high-school experience. One girl described a cruel math instructor: “He is the person whose office you enter happily and exit with pain and inferiority.” Edith, a student from northern Sichuan Province, wrote about feeling excluded from her graduation banquet, because her father and his male work colleagues hijacked the event by giving long-winded speeches that praised one another. “That’s what I hate, being hypocritical as some adults,” she wrote.
Few students chose the third prompt. Some remarked that nothing dangerous or dramatic had ever happened, because they had spent so much of their short lives studying. But one boy, whom I’ll call Vincent, submitted an essay titled “A Day Trip to the Police Station.”
The story began with a policeman calling Vincent’s mother. The officer said that the police needed to see her son, but he wouldn’t explain why. After the call, Vincent tried to figure out if he had committed some crime. He was the only student who wrote his essay in the third person, as if this distance made it easier to describe his mind-set:
He was tracing the memory from birth to now, including but not limited to [the time] he broke a kid’s head in kindergarten, he used V.P.N. to browse YouTube to see some videos, and talked with his friends abroad in Facebook and so on. Suddenly he thought of the most possible thing that happened two years ago. In the summer vacation in 2017, he bought an airsoft gun in the Internet, which is illegal in mainland China but legal in most countries or regions. Although it had been two years since then, he left his private information such as the address and his phone number. In modern society, it is possible to trace every information in the Internet and [especially] easy for police.
Vincent’s parents both worked tizhinei , within the government system. The boy approached his father for advice, and the older man didn’t lecture his son about following the rules. Vincent described their exchange:
“If you are asked about this matter,” dad said, “you just tell him that the seller mailed a toy gun and you were cheated. And then you felt unhappy and threw it away.” Sure enough, two policemen came to his home the next day.
Vincent stood about six feet tall, a handsome boy with close-cropped hair. He always sat in the front of the class, and he enjoyed speaking up, unlike many of the other engineers, who tended to be shy. On the first day of the term, I asked students to list their favorite authors, and Vincent chose Wang Xiaobo, a Beijing novelist who wrote irreverent, sexually explicit fiction.
As with many of his classmates, Vincent hoped to complete his undergraduate degree in the United States. I was teaching at the Sichuan University–Pittsburgh Institute, or SCUPI . All SCUPI classes were in English, and after two or three years at Sichuan University students could transfer to the University of Pittsburgh or another foreign institution. SCUPI was one of many programs and exchanges designed to direct more Chinese students to the U.S. In the 2019-20 academic year, Chinese enrollment at American institutions reached an all-time high of 372,532.
Nobody in Vincent’s section had previously studied in the U.S. Almost all of them were middle class, and they often said that their goal was to complete their bachelor’s degree in America, stay on for a master’s or a Ph.D., and then come back to work in China. A generation earlier, the vast majority of Chinese students at American universities had stayed in the country, but the pattern changed dramatically with China’s new prosperity. In 2022, the Chinese Ministry of Education reported that, in the past decade, more than eighty per cent of Chinese students returned after completing their studies abroad.
Vincent also intended to make a career in China, but he had specific plans for his time in the U.S. Once, during a class discussion, he remarked that someday he would purchase both a car and a real firearm. The illegal airsoft pistol that he had acquired in high school shot only plastic pellets. In 2017, when Vincent ordered the gun, it had been delivered to his home at the bottom of a rice cooker, as camouflage. At the time, such subterfuges were still possible, but the government had since cracked down, as part of a general tightening under Xi Jinping.
In Vincent’s essay, he was surprised that the two policemen who arrived at his home didn’t mention the forbidden gun. Instead, they accused him of a much more shocking crime: spreading terrorist messages.
“That’s ridiculous,” Vincent said. “I have never browsed such videos, not to mention posted them in the Internet. You must be joking.” “Maybe you didn’t post it by yourself,” the policeman said. “But the app may back up the video automatically.”
Vincent admitted that once, in a WeChat group, he had come across a terrorist video. The police instructed him to get his I.D. card and accompany them to the station. After they arrived, they entered a room labelled “Cybersecurity Police,” where Vincent was impressed by the officers’ politeness. (“It’s not scary at all, no handcuffs and no cage.”) The police informed him that they had found a host of sensitive and banned material on his cloud storage:
“But how interesting it is!” the policeman said. “They sent pornographic videos, traffic accident videos, [breaking news] videos, and funny videos.” “Yes,” he said helplessly, “so I am innocent.” “Yes, we believe you,” the policeman said. “But you have to [sign] the record because it is the fact that you posted the terrorism video in the Internet, which is illegal.”
On one level, the essay was terrifying—Chinese can be imprisoned for such crimes. But the calm tone created a strange sense of normalcy. The basic narrative was universal: a teen-ager makes a mistake, finds himself gently corrected, and gains new maturity. Along the way, he connects with the elders who love him. Part of this connection comes from what they share: the parents, rather than representing authority, are also powerless in the face of the larger system. The essay ended with the father giving advice that could be viewed as cynical, or heartwarming, or defeatist, or wise, or all these things at once:
“That’s why I always like to browse news [but] never comment on the Internet,” father said. “Because the Internet police really exist. And we have no private information, we can be easily investigated however you try to disguise yourself. So take care whatever you send on the Internet, my boy!” From this matter, Vincent really gained some experience. First, take care about your account in the Internet, and focus on some basic setting like automatic backup. Besides, don’t send some words, videos, or photos freely. In China, there is Internet police focus on WeChat, QQ, Weibo, and other software. As it is said in 1984 , “Big Brother is watching you.”
More than twenty years earlier, I had taught English at a small teachers’ college in a city called Fuling, less than three hundred miles east of Chengdu. The Fuling college was relatively low in the hierarchy of Chinese universities, but even such a place was highly selective. In 1996, the year that I started, only one out of twelve college-age Chinese was able to enter a tertiary educational institution. Almost all my students had grown up on farms, like the vast majority of citizens at that time.
In two years, I taught more than two hundred people, not one of whom went on to live abroad or attend a foreign graduate school. Most of them accepted government-assigned jobs in public middle schools or high schools, where they taught English, as part of China’s effort to improve education and engage with the outside world. Meanwhile, the government was expanding universities with remarkable speed. In less than ten years, the Fuling college grew from two thousand undergraduates to more than twenty thousand, a rate of increase that wasn’t unusual for Chinese institutions at that time. By 2019, the year that I returned, China’s enrollment rate of college-age citizens had risen, in the span of a single generation, from eight per cent to 51.6 per cent.

Link copied
When I had first arrived, in the nineties, I believed that improved education was bound to result in a more open society and political system. But in Fuling I began to understand that college in China might work differently than it did in the West. Students were indoctrinated by mandatory political classes, and Communist Party officials strictly controlled teaching materials. They were also skilled at identifying talent. In “River Town,” a book that I wrote about teaching in Fuling, I described my realization that the kind of young people I once imagined would become dissidents were in fact the most likely to be co-opted by the system: “The ones who were charismatic, intelligent, farsighted, and brave—those were the ones who had been recruited long ago as Party Members.”
This strategy long predated the Communists. China’s imperial examination system, the ancestor of the gaokao , was instituted in the seventh century and lasted for about thirteen hundred years. Through these centuries, education was closely aligned with political authority, because virtually all schooling was intended to prepare men for government service. That emphasis stood in sharp contrast with the West, where higher learning in pre-modern times often came out of religious institutions. Elizabeth J. Perry, a historian at Harvard, has described the ancient Chinese system as being effective at producing “educated acquiescence.” Perry used this phrase as the title for a 2019 paper that explores how today’s Party has built on the ancient tradition. “One might have expected,” she writes, “that opening China’s ivory tower to an infusion of scholars and dollars from around the world would work to liberalize the intellectual climate on Chinese campuses. Yet Chinese universities remain oases of political compliance.”
At Sichuan University, which is among the country’s top forty or so institutions, I recognized some tools of indoctrination that I remembered from the nineties. Political courses now included the ideas of Xi Jinping along with Marxism, and an elaborate system of Party-controlled fudaoyuan , or counsellors, advised and monitored students. But today’s undergraduates were much more skilled at getting their own information, and it seemed that most young people in my classes used V.P.N.s. They also impressed me as less inclined to join the Party. In 2017, a nationwide survey of university students showed decreased interest in Party membership. I noticed that many of my most talented and charismatic students, like Vincent, had no interest in joining.
But they weren’t necessarily progressive. In class, students debated the death penalty after reading George Orwell’s essay “A Hanging,” and Vincent was among the majority, which supported capital punishment. He described it as a human right—in his opinion, if a murderer is not properly punished, other citizens lose their right to a safe society. Another day, when I asked if political leaders should be directly elected, Vincent and most of his classmates said no. Once, I asked two questions: Does the Chinese education system do a good job of preparing people for life? Should the education system be significantly changed? Vincent and several others had the same answer to both: no.
The students rarely exhibited the kind of idealism that a Westerner associates with youth. They seemed to accept that the world is a flawed place, and they were prepared to make compromises. Even when Vincent wrote about his encounter with the Internet police, he never criticized the monitoring; instead, his point was that a Chinese citizen needs to be careful. In another essay, Vincent described learning to control himself after a rebellious phase in middle school and high school. “Now, I seem to know more about the world,” he wrote. “It’s too impractical to change a lot of things like the education system, the government policies.”
Vincent took another class with me the following fall, in 2020. That year, China had a series of vastly different responses to COVID . Early on, Party officials in Wuhan covered up reports of the virus, which spread unchecked in the city, killing thousands. By February, the national leadership had started to implement policies—strict quarantines, extensive testing, and abundant contact tracing—that proved highly effective in the pre-vaccination era. There wasn’t a single reported case at Sichuan University that year, and we conducted our fall classes without masks or social distancing. Our final session was on December 31st, and I asked students to write about how they characterized 2020. Vincent, like more than seventy per cent of his peers, wrote that it had been a good year. He described how his thinking had evolved after observing the initial mistakes in Wuhan:
Most people held negative attitudes to the government’s reaction, including me. Meanwhile, our freedom of expression was not protected and the supervision department did a lot to delete negative news, critical comments, and so on. I felt so sad about the Party and the country at that time. But after things got better and seeing other countries’ worse behaviors, I feel so fortunate now and change my idea [about] China and the Party. Although I know there are still too many existing problems in China, I am convinced that the socialist system is more advanced especially in emergency cases.
In 2021, after suspending visa services for Chinese students during the pandemic, the U.S. resumed them. Throughout the spring, I fielded anxious questions from undergraduates who were thinking about going to America. One engineer itemized his concerns in an e-mail:
1. How to feel or deal with the discrimination when the two countries’ relationship [is] very nervous? 2. What are the root causes [in] America to cause today’s situation (drugs; distrust of the government, unemployment, and the most important, racial problem)?
They generally worried most about COVID , although guns, anti-Asian violence, and U.S.-China tensions were all prominent issues. One student who eventually went to America told me that in his home town, in northeastern China, ideas about the U.S. had changed dramatically since his childhood. “When people in the community went to America, the family was proud of them,” he said. “But this time, before I went, some family members came and they said, ‘You are going to the U.S.—it’s so dangerous!’ ”
Vincent’s mother was on a WeChat group for SCUPI parents, and that spring somebody posted an advisory from the Chinese Embassy in Washington, D.C.:
Since the COVID pandemic, there have been successive incidents of discrimination and violent crimes against Asians in some cities in the United States. . . . On March 16, three shooting incidents occurred in Atlanta and surrounding areas, killing 8 people, of whom 6 were Asian women, including 1 Chinese and 1 Chinese citizen. . . . When encountering such a situation, you must remain calm, deal with it properly, try to avoid quarrels and physical conflicts, and ensure your own safety.
That month, Vincent told me that he planned to buy a .38 revolver after arriving in Pittsburgh. He had already researched how to acquire a hunting license and a firearm-safety certificate. In July, a month before he was scheduled to leave, I had dinner with his mother. She said that she worried about gun violence and racial prejudice. “Lots of people say that now in America you can’t rise to the highest level if you are Chinese,” she said.
Vincent’s mother was born in 1974, the same year as many of the people I had taught in Fuling. Like them, she had benefitted from a stable government job during the era of China’s economic boom. She and her husband weren’t rich, but they were prepared to direct virtually all their resources toward Vincent’s education, a common pattern. Edith, the girl who wrote about her graduation banquet, told me that her parents were selling their downtown apartment and moving to the suburbs in order to pay her tuition at Pittsburgh—more than forty thousand dollars a year. Like Vincent, and like nearly ninety per cent of the people I taught, Edith was an only child. Her mother had majored in English in the nineties, when it was still hard to go overseas. After reading “Gone with the Wind” in college, she had dreamed of going abroad, and now she wanted her daughter to have the opportunity.
At dinner with Vincent’s mother, I asked how his generation was different from hers.
“They have more thoughts of their own,” she said. “They’re more creative. But they don’t have our experience of chiku , eating bitterness.”
Even so, she described Vincent as hardworking and unafraid of challenges. I saw these qualities in many students, which in some ways seemed counterintuitive. As only children from comfortable backgrounds who had spent high school in a bubble of gaokao preparation, they could have come across as sheltered or spoiled. But the exam is so difficult, and a modern Chinese childhood is so pressured, that even prosperous young people have experienced their own form of chiku .
They often seemed eager for a change of environment. In my classes, I required off-campus reporting projects, which aren’t common at Chinese universities. Some students clearly relished the opportunity to visit places that otherwise may have seemed illicit or inappropriate: Christian churches, gay bars, tattoo parlors. Occasionally, they travelled far afield. One boy in Vincent’s year who called himself Bruce, after Bruce Lee, rode a motorcycle several hundred miles into the Hengduan Mountains, at the edge of the Tibetan Plateau, to research a road that had been constructed as part of China’s supply chain during the Second World War.
Vincent liked interacting with people from different backgrounds, and he researched a massage parlor, a seedy pool hall, and an outdoor marriage market in Chengdu’s People’s Park. At the marriage market, singles tried to find partners, often with the help of parents and various middlemen. In Vincent’s opinion, Chinese parents were too controlling, and young people had spent so much time studying that they had no dating experience. He wrote:
Because of one-child policy and traditional ideology, many parents consider their children as their treasure which belongs to the parents instead of the children themselves. . . . I hope the future Chinese children can have genuine liberty.
Vincent’s mother told me that she and her husband had made a point of allowing their son to decide for himself whether to go to America. But many parents were nervous, including Bruce’s father, who didn’t want his son to go to the U.S. because of the political tensions with China. In the end, Bruce decided to take a gap year before leaving. The delay was probably fortunate, because while researching the highway in the mountains he drove his motorcycle around a blind curve and was hit by a thirteen-ton dump truck. Bruce and the motorcycle slid beneath the truck; by some miracle, the vehicle came to a halt before killing the boy. I didn’t hear about the accident from the police, or the hospital, or anybody at the university. It was characteristic of these hardworking students that the news arrived in the form of an e-mailed request for an extension:
Dear Prof. Hessler, I had an accident on my way to the Lexi Highway. I was turning a corner when I was hit by a truck. Now I have a fracture in my left hand and a piece of flesh has been grinded off my left hand. Then the ligaments and nerves were damaged, and the whole left hand was immobile. My left foot was also injured. It was badly bruised. The whole foot was swollen and couldn’t move. I’m in hospital now. I’ll have to stay in the hospital for a while before I can come back. So I may not be able to write the article about the Lexi Highway. I don’t know what to do now. Can I write the article at a later date? Because I can’t do my research right now. And it’s really hard for me to type with one hand. Best wishes, Bruce
The first time I saw Vincent in Pittsburgh, in October, 2021, he had lived in America for only eighty-two days, but already he had acquired a used Lexus sedan, a twelve-gauge Winchester shotgun, a Savage Axis XP 6.5 Creedmoor bolt-action rifle, and a Glock 19 handgun. “It’s the Toyota Camry of guns,” he said, explaining that the Glock was simple and reliable.
Vincent had studied the gun laws in Pennsylvania, learning that an applicant for a concealed-carry permit must be at least twenty-one, so he applied on his birthday. The permit cost twenty dollars and featured a photograph of Vincent standing in front of an American flag. He had also researched issues of jurisdiction. “I can use it in Ohio,” he said. “But not in California. I don’t like California.” One reason he disliked California was that state law follows the Castle Doctrine, which, in Vincent’s opinion, provides inadequate protection for gun owners. “Pennsylvania has Stand Your Ground,” he said, referring to a law that allows people to defend themselves with deadly force in public spaces. “They made some adjustments to the Castle Doctrine.”
Vincent was thriving in his engineering classes, and he said that some of the math was easier than what he had studied in high school in China. His views about his home country were changing, in part because of the pandemic. Vaccines were now widespread, but the Party hadn’t adjusted its “zero COVID ” strategy. “Their policy overreacts,” Vincent told me. “You should not require the government to do too many things and restrict our liberties. We should be responsible for ourselves. We should not require the government to be like our parents.”

A couple of times, he had attended Sunday services at the Pittsburgh Chinese Church Oakland, an evangelical congregation that offered meals and various forms of support for students. In China, Vincent had never gone to church, but now he was exploring different denominations. He had his own way of classifying faiths. “For example, a church with all white Americans,” he said, referring to his options. “One of my classmates joined that. I think he likes it. He goes every week. He can earn so many profits. Even the Chinese church, they can pick you up from the airport, free. They can help you deliver furniture from some store, no charge. They do all kinds of things!”
In 2021, there were more than fifteen hundred Chinese at the University of Pittsburgh, and around three thousand at Carnegie Mellon, whose campus is less than a mile away. I came to associate the city with Sichuanese food, because I almost never ate anything else while meeting former students. Some of them, like Vincent, were trying to branch out into American activities, but for the most part they found it easy to maintain a Chinese life. Many still ordered from Taobao, which in the U.S. is slower than Amazon but has a much better selection of Chinese products. They also used various Chinese delivery apps: Fantuan, HungryPanda, FreshGoGo. The people I taught still relied heavily on V.P.N.s, although now they used them to hop in the other direction across China’s firewall. They needed the Chinese Internet in order to access various streaming apps and pop-music services, as well as to watch N.B.A. games with cheaper subscription fees and Mandarin commentary.
For students who wanted to play intercollegiate basketball, the Chinese even had their own league. An athletic boy named Ethan, who had been in my composition class at Sichuan University, was now the point guard for the Pittsburgh team. Ethan told me that about forty students had tried out and seventeen had made the cut. I asked if somebody like me could play.
“No white people,” Ethan said, laughing.
“What about hunxue’er ?” The term means a person of mixed race.
“I think that works.”
One weekend in 2022, I watched Pitt play Carnegie Mellon. Or, more accurately, I watched “UPitt,” because that was the name on the jerseys. My father attended Pitt in the late sixties, and I had grown up wearing school paraphernalia, but I had never heard anybody refer to the place as UPitt. The colors were also different. Rather than using Pitt’s royal and gold, the Chinese had made up uniforms in white and navy blue, which, in this corner of Pennsylvania, verged on sacrilege: Penn State colors.
The team received no university funding, so it had found its own sponsors. Moello, a Chinese-owned athletic-clothing company in New York, made the uniforms, and Penguin Auto, a local dealership, paid to have its logo on the back, because Chinese students were reliable car buyers.
The Northeastern Chinese Basketball League, which is not limited to the Northeast, has more than a hundred teams across the U.S. On the day that I watched, the Pitt team played a fast, guard-dominated game, running plays that had been named for local public bus lines. “ Qishiyi B!” the point guard would call out: 71B, a bus that runs to Highland Park. It was the first time I had attended a college basketball game in which the starting forward hit a vape pen in the huddle during time-outs.
The forward was originally from Tianjin, and his girlfriend was the team manager. She told me that she was trying to get him to stop vaping during games. Her name was Ren Yufan, and she was friendly and talkative; she went by the English name Ally. Ally had grown up in Shanghai and Nanjing, but she had attended high school at Christ the King Cathedral, a Catholic school in Lubbock, Texas, where she played tennis. “I was state sixth place in 2A,” she said. She noted that she had also been elected prom queen.
Ally often answered questions with “Yes, sir” or “No, sir,” and her English had a slight Texas twang. Her parents had sent her to Lubbock through a program that pairs Chinese children with American host families. Ally’s host family owned a farm, where she learned to ride a horse; she enjoyed Lubbock so much that she still returned for school holidays. In the past ten or so years, more Chinese have found ways to enroll their kids in U.S. high schools, in part to avoid gaokao agony. In Pittsburgh, my Sichuan University students described these Chinese as a class apart: typically, they come from wealthy families, and their English is better than that of the Chinese who arrive in college or afterward. Their work patterns are also different. Yingyi Ma, a Chinese-born sociologist at Syracuse University, who has conducted extensive surveys of students from the mainland, has observed that the longer the Chinese stay in the U.S. the less they report working harder than their American peers. Like any good Chinese math problem, this distinctly American form of regression toward the mean can be quantified. In Ma’s book “Ambitious and Anxious,” she reports on her survey results: “Specifically, one additional year of time in the United States can reduce the odds of putting in more effort than American peers by 14 percent.”
Ally’s boyfriend had attended a private high school in Pennsylvania that cost almost seventy thousand dollars a year, and he drove a Mercedes GLC. “We are using our parents’ money, but we can’t be as successful as our parents,” Ally said. Neither her father nor her mother had attended university, but they had thrived in construction and private business during the era of China’s rapid growth. Now the country’s economy was struggling, and Ally accepted the fact that her career opportunities would likely be worse than those of the previous generation. Nevertheless, she planned to return to China, because she wanted to be close to her parents. I asked if anything might make it hard to fit in after spending so many formative years in America.
“My personality,” she said. “I’m too outgoing.”
“There are no prom queens in China, right?”
By my second visit to Pittsburgh, in November, 2022, Vincent had decided to stay permanently in the U.S., been baptized in the Church of Jesus Christ of Latter-day Saints, and added an AK-47 and two Sig Sauer handguns to his arsenal. He had also downgraded to a less expensive car, because the Lexus had been damaged in a crash. Rather than getting the Glock 19 of automobiles, Vincent decided on the Camry’s cousin, a used Toyota Prius. He picked me up in the Prius, and we headed out for a traditional Steel City meal of lajiao and prickly ash. Vincent wore a Sig Sauer P365 XL with a laser sight in a holster on his right hip. The car radio was playing “Water Tower Town,” a country song by Scotty McCreery:
In a water tower town, everybody waves Church doors are the only thing that’s open on Sundays Word travels fast, wheels turn slow. . . .
Earlier in the year, some Mormon missionaries had struck up a conversation with Vincent on campus. “Their koucai is really good,” he told me, using a word that means “eloquence.” “It helps me understand how to interact with people. They say things like ‘Those shoes are really nice!’ And they start talking, and then they ask you a question: ‘Are you familiar with the Book of Mormon?’ ” Now Vincent had a Chinese app for the Book of Mormon on his phone, and he attended services every Sunday. He had been baptized on July 23rd, which was also the day that he had quit drinking and smoking cigarettes, a habit he’d had since Sichuan University. He thought that the church might be a good place to meet a girlfriend. He had a notion that someday he’d like to have a big family and live in a place like Texas, whose gun laws appealed to him.
Corn grows high, crime stays low There’s little towns everywhere where everybody knows. . . .
During the winter of Vincent’s first academic year in the U.S., his political transformation had been rapid. “I watched a lot of YouTube videos about things like June 4th,” he told me, referring to the date of the Tiananmen Square massacre, in 1989. He began to question the accommodationist views that he had previously held. “Young people are like this in China,” he said. “They tend to support the system.”
In the spring of 2022, Vincent became dismayed by the excessive COVID lockdown in Shanghai. He posted a series of critical remarks on social media, and in May he sent me an e-mail:
In recent months, I make some negative comments on WeChat on the humanitarian crisis caused by the lockdown in Shanghai and some other issues. My parents got nervous and asked me to delete these contents because their colleagues having me in their contact lists in WeChat read my “Pengyou Quan” [friends’ circle] and reminded my parents of potential risks of “Ju Bao” [political reporting] that would affect my parents’ jobs.
One day, a man who may have been from the Chinese security apparatus phoned Vincent’s parents. Unlike in the call from years before, this man didn’t identify himself as the police. But he said that Vincent’s actions could cause trouble for the family. Such anonymous warnings are occasionally made to the parents of overseas Chinese, and they weigh heavily on students.
Vincent deleted his WeChat comments. But he also decided that he couldn’t imagine returning to China. “I would say something and get arrested,” he told me. “I need to be in a place where I have freedom.” An older Chinese friend in Pittsburgh had made a similar decision, and he advised Vincent on how to eventually apply for a green card.
Vincent told his parents that he planned to stay in America for at least five years, but initially he didn’t say that his decision was permanent, because he worried that they would be upset. In the meantime, he didn’t want to waste their money, so he earned cash on the side by teaching Chinese students how to drive. Professional garages charged at least five hundred dollars to install a passenger brake, but Vincent found one on Taobao for about eighty-five dollars, including shipping from China. “I don’t know if it’s legal,” he told me. With his engineering skills, he was able to install the brake in the Prius.

The number of Chinese studying in the U.S. had dropped to the lowest level in nearly a decade. But there were still almost three hundred thousand, and many of them arrived in places like Pittsburgh and realized that qishiyi B and other public buses weren’t adequate for their needs. They preferred to hire driving instructors who spoke Mandarin, and Vincent’s rate was eighty dollars an hour. He charged even more for the use of his car during exams. Vincent told me that a Chinese-speaking driving instructor who hustled could earn at least two hundred thousand dollars a year. In my own business, the Chinese political climate had made it almost impossible for American journalists to get resident visas, and specialists of all sorts no longer had access to the country. Sometimes I envisioned a retraining program for old China hands: all of us could buy passenger brakes on Taobao and set up shop as mandarins of parallel parking.
I knew of only a few former students who, like Vincent, had already decided to make a permanent home outside China. It was viewed as an extreme step, and most of them preferred to keep their options open. But virtually all my former students in the U.S. planned to apply to graduate school here.
They were concerned about the economic and political situation in China, but they also often felt out of place in Pittsburgh. American racial attitudes sometimes mystified them. One engineer had taken a Pitt psychology class that frequently touched on race, and he said that it reminded him of the political-indoctrination classes at Sichuan University. In both situations, he felt that students weren’t supposed to ask questions. “They’re just telling you how to play with words,” he said. “Like in China when they say socialism is good. In America you will say, ‘Black lives matter.’ They are actually the same thing. When you are saying socialism is good, you are saying that capitalism is bad. You are hiding something behind your words. When you say, ‘Black lives matter,’ what are you saying? You are basically saying that Asian lives don’t matter, white lives don’t matter.”
It wasn’t uncommon for Chinese students to have been harassed on the streets. They often said, with some discomfort, that those who targeted them tended to be Black. Many of these incidents involved people shouting slurs from passing cars, but occasionally there was something more serious. One group of boys was riding a public bus at night when a passenger insulted them and stole some ice cream that they had just bought. Afterward, one of the students acquired a Beretta air pistol. He was wary of buying an actual gun, but he figured that the Beretta looked real enough to intimidate people.
One evening, I went out for Sichuanese food with four former students, including a couple who had been involved in that incident. They seemed to brush it off, and they were much more concerned about Sino-U.S. tensions. One mentioned that if there were a war over Taiwan he would have only three options. “I can go back to China, or I can go to Canada, or I can go somewhere else,” he said. “I won’t be able to stay here.”
“Look at what happened to the Japanese during World War Two,” another said. “They put them into camps. It would be the same here.”
They all believed that war was unlikely, although Xi Jinping made them nervous. Back in China, my students had generally avoided mentioning the leader by name, and in Pittsburgh they did the same.
“It all depends on one person now,” a student said at the dinner. “In the past, it wasn’t just one person. When you have a group of people, it’s more likely that somebody will think about the cost.”
I asked whether they would serve in the Chinese military if there were a war.
“They wouldn’t ask people like us to fight,” one boy said. He explained that, in a war, he wouldn’t return home if his country was the aggressor. “If China fires the first shot, then I will stay in America,” he said.
I asked why.
“Because I don’t believe that we should attack our tongbao , our compatriots.”
I knew of only one Pitt student who planned to return to China for graduate school. The student, whom I’ll call Jack, was accepted into an aerospace-engineering program at Jiao Tong University, in Shanghai. Jack was one of the top SCUPI students, and in an earlier era he would have had his pick of American grad schools. But Chinese aerospace jobs are generally connected to the military, and American institutions had become wary of training such students. Even if a university makes an offer of admission, it can be extremely difficult to get a student visa approved. “Ten years ago, it would have been fine,” Jack told me. “My future Ph.D. adviser got his Ph.D. at Ohio State in aerospace engineering.” He continued, “Everybody knows you can’t get this kind of degree in the U.S. anymore.”
When I met Jack for lunch, I initially didn’t recognize him. He had lost twenty pounds, because in Pittsburgh he had adopted a daily routine of a four-mile run. “In middle school and high school, my parents and grandparents always said you should eat a lot and study hard,” he said. “I became kind of fat.”
He had assimilated to American life more successfully than most of his peers, and his English had improved dramatically. He told me shyly that he had become good friends with a girl in his department. “Some of my friends from SCUPI are jealous because I have a friend who is a foreign girl, a white girl,” he said. “They make some jokes.”
He said that he would always remember Pittsburgh fondly, but he expected his departure to be final. “I don’t think I’ll come to the U.S. again,” he said. “They will check. If they see that you work with rockets, with the military, they won’t let you in.”
On the afternoon of January 10, 2023, at around three o’clock, in the neighborhood of Homewood, Vincent was stopped behind another vehicle at a traffic light when he heard a popping sound that he thought was fireworks. He was driving the Prius, and a Chinese graduate student from Carnegie Mellon sat in the passenger seat. Vincent wore a Sig Sauer P365 subcompact semi-automatic pistol in a concealed-carry holster on his right hip. The Carnegie Mellon student was preparing to get his driver’s license, and Vincent was taking him to practice at a test course in Penn Hills, an area that was known for occasional crime problems.
At the traffic light, Vincent saw a car approach at high speed and run a red light. Then there were more popping sounds. Vincent realized that they weren’t fireworks when a bullet cracked his windshield.
He ducked below the dashboard. In the process, his foot came off the brake, and the Prius struck the vehicle ahead of him. The shooting continued for a few seconds. After it stopped, the Carnegie Mellon student said, “ Ge , brother, you just hit the car in front!”
“Get your head down!” Vincent shouted. He backed up, swerved around the other vehicle, and tore through a red light. After a block, he saw a crossing guard waiting for children who had just finished the day at Westinghouse Academy, a nearby public school.
“Shots fired, shots fired!” Vincent shouted. “Call 911!”
He parked on the side of the road, and soon he was joined by the driver whose car he had struck. They checked the bumpers; there wasn’t any damage. The driver, an elderly woman, didn’t seem particularly concerned about the shooting. She left before the police arrived.
A woman from a nearby house came out to talk with Vincent. She remarked that shootings actually weren’t so common, and then she walked off to pick up her child from Westinghouse Academy. After a while, a police officer drove up, carrying an AR-15. Vincent explained that he was also armed, and the officer thanked him for the information. He asked Vincent to wait until a detective arrived.
For more than two hours, Vincent sat in his car. The Carnegie Mellon student took an Uber home. When the detective finally showed up, his questions were perfunctory, and he didn’t seem interested in Vincent’s offer to provide dashboard-camera footage. A brief report about the incident appeared on a Twitter account called Real News and Alerts Allegheny County:
Shot Spotter Alert for 20 rounds Vehicles outside of a school shooting at each other. 1 vehicle fled after firing shots.
Later that year, Vincent took me to the site. He recalled that during the incident he had repeatedly said, “Lord, save me!,” like Peter the Apostle on the Sea of Galilee. The lack of police response had surprised Vincent. “I didn’t know they didn’t care about a shooting,” he said. For our visit, he wore a Sig Sauer P320-M17 on his right hip. “Normally, I don’t open-carry,” he said. “But this gun can hold eighteen rounds.”
It had been four years since Vincent arrived in my class at Sichuan University. Have you ever been involved in a situation that was extremely threatening, or dangerous, or somehow dramatic ? Back then, he had written about what happened when the Chinese Internet police came to his home. Now Vincent’s American story was one in which the police effectively didn’t come after twenty rounds had been fired near a school. But there was a similar sense of normalcy: everybody was calm; nothing seemed out of the ordinary. The following month, four students were shot outside Westinghouse Academy.
I asked Vincent if the incident had changed his opinion about gun laws.
“No,” he said. “That’s why we should carry guns. Carrying a gun is more comfortable than wearing body armor.”
At Sichuan University, I also taught journalism to undergraduates from a range of departments. Last June, I sent out a detailed survey to more than a hundred and fifty students. One question asked if they intended to make their permanent home in China. A few weren’t certain, but, of the forty-three who answered, thirty said that they planned to live in China. There was no significant difference in the responses of students who were currently in China versus those abroad.
Since the pandemic, there have been increasing reports of young Chinese engaged in runxue , or “run philosophy,” escaping the country’s various pressures by going abroad permanently. A number of my students pushed back against the idea that runxue had wide appeal. “I think that’s just an expression of emotion, like saying, ‘I want to die,’ ” one student who was studying in Pittsburgh told me. “I don’t take it very seriously.” He planned to go to graduate school in America and then return home. He said that in China it was easy for him to avoid politics, whereas in Pittsburgh he couldn’t avoid the fact that he was a foreigner. During his initial few months in the city, he had experienced three unpleasant anti-Asian incidents. As a result, he had changed the route he walked to his bus stop. “I think I don’t belong here,” he said.
Yingyi Ma, the sociologist at Syracuse who has surveyed Chinese students in the U.S., has observed that almost sixty per cent of her respondents intend to return to their homeland. She told me that young Chinese rarely connect with the political climate in the U.S. “But what makes America appealing is the other aspects,” she said. “The agency. The self-acceptance. Over time, as they stay in the U.S., they figure out that they don’t have to change themselves.”
One former student told me that she might remain in America in part because people were less likely to make comments about her body. She’s not overweight, but she doesn’t have the tiny frame that is common among young Chinese women, and people in China constantly remarked on her size. In Pittsburgh, I met with Edith, the student who had written about her graduation banquet. Now she had dyed some of her hair purple and green, and she avoided video calls with her grandparents, who might judge her. Once, she had gone to a shooting range with Chinese classmates, and she had attended church-group meetings out of curiosity. She told me that recently she had taken up skateboarding as a hobby.
It was typical for students to pursue activities that would have been unlikely or impossible in China, and several boys became gun enthusiasts. Nationwide, rising numbers of Asian Americans have purchased firearms since the start of the pandemic, a trend that scholars attribute to fears of racism. One afternoon, I arranged to meet a former student named Steven at a shooting range outside Wexford, Pennsylvania. I knew that I was in the right parking lot when, amid all the pickup trucks, I saw a car with a bumper sticker that said “E=mc 2 .” On the range, whenever the call came for a halt in shooting—“All clear!”—a bunch of bearded white guys in camo and Carhartt stalked out with staple guns to attach new paper covers to the targets. Steven, a shy, round-faced engineer in glasses, was the only Chinese at the range, and also the only person who used quilting pins for his target. He told me that the quilting pins were reusable and thus cheaper than staples. He had come with a Smith & Wesson M&P 5.7 handgun, a Ruger American Predator 6.5 Creedmoor bolt-action rifle, and a large Benchmade knife that he wore in a leather holster. At the range, he shot his rifle left-handed. When he was small, his father had thought that he was a natural lefty, but he was taught to write with his right hand, like all Chinese students. He told me that shooting was the first significant activity in which he had used his left.
On the same trip, I met Bruce for a classic Allegheny County dinner of mapo tofu and Chongqing chicken. After the accident in the Himalayas, Bruce had sworn off motorcycles. At Pitt, in addition to his engineering classes, he had learned auto repair by watching YouTube videos. He bought an old BMW, fixed it up, and sold it for a fifty-per-cent profit. He used the money to purchase a used Ford F-150 truck, which he customized so he could sleep in the cab for hiking and snowboarding excursions to the mountains. He had decorated the truck with two “thin blue line” American-flag decals and another pro-police insignia around the license plate. “That’s so it looks like I’m a hongbozi ,” Bruce said, using the Mandarin translation of “redneck.” “People won’t honk at me or mess with me.” He opened the door and pointed out a tiny Chinese flag on the back of the driver’s seat. “You can’t see it from the outside,” he said, grinning.
Over time, I’ve also surveyed the people I taught in the nineties, and last year I asked both cohorts of former students the same question: Did the pandemic change anything significant about your personal opinions, beliefs, or values? The older group reported relatively few changes. Most are now around fifty years old, with stable teaching jobs that have not been affected by China’s economic problems. They typically live in third- or fourth-tier provincial cities, which were less likely to suffer brutal lockdowns than places like Shanghai and Beijing.
But members of the younger generation, who are likelier to live in larger cities and generally access more foreign information, responded very differently. “I can’t believe I’m still reading Mao Zedong Thought and Socialism with Chinese Characteristics,” one graduate student at a Chinese university wrote. “In this collectivist ideology, there is no respect for the dignity and worth of the individual.” Another woman, who was in graduate school in the United Kingdom, wrote, “Now I’ve switched to an anarchist. It reduces the stress when I have to read the news.”
Their generation is unique in Chinese history in the scope of their education and in their degree of contact with the outside world. But this doesn’t necessarily mean that their concerns are broader. In my survey, I asked what they worried about most, and, out of forty-seven responses, three mentioned politics. Another three worried about the possibility of war with Taiwan. Only one cited environmental issues. The vast majority of answers were personal, with more than half mentioning job opportunities or problems with graduate school. This seemed to reflect the tradition of “educated acquiescence”: there’s no point in concerning yourself with big questions and systemic flaws.
Nevertheless, their worldliness makes it harder to predict long-term outcomes, and I sense a new degree of unease. On a recent trip to California, I interviewed a former student who commented that even when she and her Chinese boyfriend were alone they instinctively covered their phones if they talked about politics, as if this would prevent surveillance. I noticed that, like many other former students, she never uttered the name Xi Jinping. Afterward, I asked her about it over e-mail, and she replied:
I do find myself avoiding mentioning Xi’s name directly in [California], even in private conversations and in places where I generally feel “safe.” . . . I guess it’s a thing that has been reinforced millions of times to the point that it just feels uncomfortable and daunting to say his full name, as it has too much association with unrestrained power and punishment.
In the survey of my Sichuan University students, I was most struck by responses to a simple query: Do you want to have children someday? The most common answer was no, and the trend was especially pronounced for women, at seventy-six per cent. Other surveys and studies in China indicate a similar pattern. One former student explained:
I think that Chinese children are more stressed and profoundly confused, which will continue. We are already a confused generation, and children’s upbringing requires long periods of companionship and observation and guidance, which is difficult to ensure in the face of intense social pressure. The future of Chinese society is an adventure and children do not “demand to be born.” I am worried that my children are not warriors and are lost in it.
By my third visit to Pittsburgh, in November, 2023, Vincent had graduated, been baptized again, and embarked on his first real American job. The previous year, I had attended Sunday services with him at a Mormon church, but this time he took me to the Church of the Ascension, an Anglican congregation near campus. When I asked why he had switched, he used a Chinese word, qihou . “Environment,” he said. “They aren’t pushy. The Mormons are too pushy.”
He liked the fact that the Anglicans were conservative but reasonable. He saw politics in similar terms: he disliked Donald Trump, but he considered himself most likely to vote as a traditional Republican if he became a citizen. He had been baptized in the Anglican Church on Easter. “I told them that I had already been baptized,” he explained. “But they said that because it was Mormon it doesn’t count.”
The previous summer, Vincent’s mother had visited Pittsburgh, where, among other places, he took her to church and to the shooting range. During the trip, he told her about his plan to live permanently in the U.S. When I spoke with her recently by phone, she still held out hope that he would someday return to China. “I don’t want him to stay in America,” she said. “But if that’s what he wants I won’t oppose it.” She said that she was impressed by how much her son had matured since going abroad.
After receiving his degree in industrial engineering, Vincent decided not to work in the field. He believed that he was best suited for a career in business, because he liked dealing with all kinds of people. He had started working for his landlord, Nick Kefalos, who managed real-estate properties around Pittsburgh. One morning, I accompanied Vincent when he stopped by Kefalos’s office to drop off a check from a tenant.
Kefalos was a wiry, energetic man of around seventy. He told me that on a couple of occasions a roommate had left an apartment and Vincent was able to find a replacement. At one point, he persuaded a Japanese American, a Serbian, and a Dane to share a unit, and all of them had got along ever since. “We could see that he had a knack,” Kefalos said. “He was able to find unrelated people and make good matches.” Kefalos also liked having a Chinese speaker on staff. “We think a diverse population is ideal,” he said. Vincent was currently studying for his real-estate license, and he hoped to start his own business someday.
Kefalos’s grandfather had come from Greece, and his father had worked as an electrical engineer in the steel industry. Many of his current tenants were immigrants. “My personal experience is that they are relatively hardworking,” he said. “And I think that’s true with most immigrants who come into the country. Whether it’s for education or a better life.” He looked up at Vincent and said, “My sense is that most U.S. citizens born in the United States don’t have any idea how fortunate they are.” ♦
New Yorker Favorites
Searching for the cause of a catastrophic plane crash .
The man who spent forty-two years at the Beverly Hills Hotel pool .
Gloria Steinem’s life on the feminist frontier .
Where the Amish go on vacation .
How Colonel Sanders built his Kentucky-fried fortune .
What does procrastination tell us about ourselves ?
Fiction by Patricia Highsmith: “The Trouble with Mrs. Blynn, the Trouble with the World”
Sign up for our daily newsletter to receive the best stories from The New Yorker .
By signing up, you agree to our User Agreement and Privacy Policy & Cookie Statement . This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

By Benjamin Kunkel

By Hannah Goldfield

By Alma Guillermoprieto

By Chang Che

IMAGES
VIDEO
COMMENTS
Instructions. Preparation. Reading. Check your writing: grouping - ideas. Check your writing: gap fill - useful phrases. Worksheets and downloads. A for and against essay about the internet - exercises 592.59 KB. A for and against essay about the internet - answers 136.91 KB. A for and against essay about the internet - essay 511.93 KB.
Harmful effects on cognitive development: Empirical evidence suggests that internet use can have both positive and negative impacts on cognitive development, depending on the person and the circumstances. There is evidence that children's cognitive development can be damaged by prolonged internet use, including the development of memory ...
Abstract. This essay presents a critical debate on whether the Internet is as dangerous as the physical world. First, the unique dangers posed by the Internet are outlined. This is followed by an examination of some of the major threats to safety that are present in the physical world but not in the virtual world.
There are many dangers on the Internet. This paper will try to cover some of them. The biggest dangers of the Internet are virus. Viruses are small programs that "infect" computers. Most viruses are made to "steal" and or "destroy" data stored on the infected computer. Viruses, that destroy data, write their code into a file and when that file ...
Apart from that, relying on technologies too much might weaken people and make it harder for them to adjust to the realities of the outer world. This essay, "Threats of the Internet" is published exclusively on IvyPanda's free essay examples database. You can use it for research and reference purposes to write your own paper.
Internet Danger #2: Sexual Predators. Internet Danger #4: Damaged Reputations. 7 min read. Mary Ellen Handy had a painful crash course in the dangers of the Internet. The trouble started in her ...
In conclusion, while the internet offers numerous benefits, it's crucial to use it responsibly to avoid its potential pitfalls. Also check: Paragraph on Uses and Abuses of Internet; 250 Words Essay on Uses and Abuses of Internet Introduction. The internet, a revolutionary invention of the 20th century, has transformed our lives in profound ways.
China's internet retailing sector posted $210 billion in revenue in 2012, a growth rate of 60% from 2011. America's internet retailing market is only slightly larger and growing much more slowly.
In this age, parents are forced to protect the eyes of their children from graphic content and sexual innuendos from the moment they touch their first device. Sexual addictions and crime rates across the country are on the rise and the vulgarity of the internet bears the brunt of the blame. For years there has been an ongoing argument regarding ...
2. Dangers of the Internet on the Youth. Anyone can be a victim on the internet, but kids are most vulnerable to cyberattacks and offenses. So first, cite the most common concerns kids can encounter while surfing online. A few examples you can include are cyberbullying, phishing, predators, and scams.
Teach your kids to keep personal information private. It's usually a bad idea to post personal information online such as phone numbers, addresses, and credit cards. If criminals gain access to this information, they can use it to harm you or your family. Teach your kids to use social networking sites safely.
After all, no one can physically harm you through a computer screen. But to stay safe online, you'll want to take a more cautious approach. Here's one way to think about it: Treat the Internet as you would a shopping mall. Most people don't consider a mall to be an especially dangerous place. You can go there to shop and meet up with friends.
The better-informed parents are about sex trafficking, the easier it is for them to know the potential signs of a dangerous interaction unfolding online. The Internet and Mental Health. In 1998, the term "internet addiction" was officially coined and as of now, the DSM-5 recognizes the problem as an official mental disorder.
Haidt's prevailing metaphor of thoroughgoing fragmentation is the story of the Tower of Babel: the rise of social media has "unwittingly dissolved the mortar of trust, belief in institutions ...
The internet, while being a powerful tool, can also be a dangerous weapon when misused. Cyberbullying, identity theft, and invasion of privacy are some of the significant issues arising from its misuse. ... 500 Words Essay on Misuse of Internet Introduction. The Internet, an invention of the late 20th century, has become an integral part of our ...
To return to our initial question, within the domain of terrorism, online radicalization, as a process dominated or entirely guided by Internet-related activity, does occur and poses a discernible threat, although both prevalence and threat level have so far been lower in comparison to other forms of radicalization.
Watchdog groups have identified Facebook and Instagram as avenues for cyberbullying, and reports have linked TikTok to dangerous and antisocial behavior, including a recent spate of school vandalism. As social media has proliferated worldwide—Facebook has 2.85 billion users—so too have concerns over how the platforms are affecting ...
976 Words | 4 Pages. Thesis statement: online dating has been successful, however there are some risks and dangers that should be avoided. Topic sentence#1: Online dating has been proven to be successful in the dating world. Topic sentence#2: Impostors are the number one thing to avoid when online dating.
Increased depression. Increased sleep issues. Lack of self-esteem. Lack of focus and concentration. "If kids are being asked to get off social media and do their homework, or any unpreferred ...
The Internet is a connection of computers across the world through a network. Its origin dates back to the 1960s when the U.S Military used it for research, but it became more available to the public from the late 1980s. The World Wide Web was created in 1989 and browsers began appearing in the early 1990s.
A.I.-Generated Garbage Is Polluting Our Culture. Mr. Hoel is a neuroscientist and novelist and the author of The Intrinsic Perspective newsletter. Increasingly, mounds of synthetic A.I.-generated ...
This essay presents a critical debate on whether the Internet is as dangerous as the physical world. First, the unique dangers posed by the Internet are outlined. This is followed by an examination of some of the major threats to safety that are present in the physical world but not in the virtual world.
Essay on Dangers of the Internet Many people view the internet as an ultimate resource for anything they desire. The people who say that the internet is a brilliant invention for the best ... She feels that it is an extremely dangerous asset that the internet has brought upon society. Baughman asserts in her essay "…Internet users who are ...
Internet is dangerous .Do you agree or disagree to this. #internet. The . internet. ... A great argument essay structure may be divided to four paragraphs, in which comprises of four sentences (excluding the conclusion paragraph, which comprises of three sentences).
The Chinese government wants the world to forget about Hong Kong, to forget what the city once was, to forget Beijing's broken promises. But Hong Kong's people will never forget. Don't look ...
Writer and editor Grazie Sophia Christie, 27, wrote an essay for New York Magazine's The Cut column extolling the virtues of marrying an older man, but the internet buzz is that her essay is more ...
Now, of course, there's artificial intelligence. According to new research from Pew, about 1 in 5 US teens who've heard of ChatGPT have used it for schoolwork. Kids in upper grades are more ...
By Jane Coaston. Ms. Coaston is a contributing Opinion writer. Last month, the House passed a bill that would require TikTok's parent company to sell its U.S. business to a company without ties ...
UCLA is creating "BruinHubs" for student commuters who need a place to rest and study before and after school — complete with rest pods, study tables, a microwave and a fridge.
COVID, guns, anti-Asian violence, and diplomatic relations have complicated the ambitions of the some three hundred thousand college students who come to the U.S. each year.