Suggestions or feedback?

MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Is online privacy possible?

Previous image Next image
Share this news article on:
Related links.
- Information Services & Technology
Related Topics
More mit news.
MIT economics to launch new predoctoral fellowship program
Read full story →
Programming functional fabrics
Does technology help or hurt employment?

Most work is new work, long-term study of U.S. census data shows
A first-ever complete map for elastic strain engineering

“Life is short, so aim high”
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
Hi there! We use cookies to give you the best site experience.
Privacy Preferences Center
We use cookies along with other tools to help the Clario website load faster. Our cookie files never contain personal data. This means information like your location, email, or IP address always remain unknown to us.
Help us improve your website experience by accepting the use of cookies. You can change your privacy settings whenever you like.
Manage consent
All cookies
These cookies are strictly necessary for enabling basic website functionality (including page navigation, form submission, language detection, post commenting), downloading and purchasing software. The website might malfunction without these cookies.
We stand with Ukraine to help keep people safe. Join us
Table of contents
Why is online privacy important?
Concerns around personal privacy on the internet, what is information privacy, how does digital privacy differ from information security, major internet privacy issues, our security tips to protect your privacy online, what online privacy is and why it's important.
Online privacy has become a pressing issue due to the number of data breaches and identity theft instances. It is astonishing how easy it is to learn anything you want about anyone you know. Fortunately, there are ways to protect privacy. The first step — educate yourself. Second — use VPN.
Get it for iOS , Android
The right to be forgotten: data privacy as a human right
Search engines user tracking, social media data harvesting, cookies/online tracking, mobile apps and privacy, identity theft.
Online privacy definition
Online privacy, also known as internet privacy or digital privacy, refers to how much of your personal, financial, and browsing data remains private when you’re online. It has become a growing worry, with browsing history and personal data at increased risk.
To give an example, the number of data breaches publicly reported in the US through September 2021 outstripped the whole last year by 17%.
Many people underestimate the importance of online privacy, but they should be aware of how much information they’re sharing — not just on social networks but just through browsing itself.
So what are those privacy issues that you might come across? And how can you securely share your personal data online? Read on to find it out.
The importance of digital privacy becomes clear once you try to make a mental list of personal things you’re ready to share with complete strangers — and those you’d rather not. For sure, you don’t want your medical records, bank statements, or even certain items from your shopping cart to be widely known. Anyone who watched You saw how easy it was for people to get hold of someone’s personal information like home address, friends’ names, tastes, or favorite places based on what they publicly shared.
Yes, you can make your social media account private and share only specific content with a specific group of people. But how can you really know what social media does with the data you share? And what about your other online traces, like browsing history, purchases, or even your online correspondence?
A poll of American internet users revealed that 81% of respondents believed they had no control over data collected by private companies. Even worse — the number climbed to 84% when people were asked if they could control what data the government collected.
To address similar concerns, the EU adopted the GDPR , or the General Data Protection Regulation. This set of laws, passed in 2016 and implemented in 2018, was intended to protect every EU citizen’s privacy and data.
California’s equivalent CCPA also gives consumers four basic rights to control personal information on the internet, including:
- The right to know what personal information a business collects about them and how it is used and shared
- The right to delete the personal information they shared
- The right to opt-out of the sale of their personal information
- The right to non-discrimination for exercising their CCPA rights
At the same time, some tech companies store customer information dating back to years ago. They’ve been logging every website they visited, all their preferences, shopping habits, political views, and many more. How can you address that?
The right to be forgotten is the right to ask companies to delete and surrender any information they’ve gathered about you. It covers online chatting and third-party discussions. People have fought to remove their names and images from “revenge porn,” including any relevant search engine results. Some have submitted take-down requests for uncomfortable personal stories from their past, for example, petty crime reports or embarrassing viral stories.
Arguably, the right to be forgotten protects those who want to forget about their old mistakes and restore privacy. The opposite camp, incidentally including some tech giants, criticizes this as censorship and rewriting of history.
Information privacy (also known as data privacy) is a branch of data security aimed at proper data handling, including consent, notice, and regulatory obligations. Simply put, it’s an ability to control what details you reveal about yourself on the internet and who can access it.
As a vital component of information sharing, data privacy is an umbrella term for:
- Online privacy
- Financial privacy
- Medical privacy
Data masking, encryption, and authentication are just a few methods used to ensure that information is made available only to the authorized parties.
Online privacy and security are closely related concepts that impact your cyber safety. There are some specific differences between them, though.
Digital privacy refers to the proper usage, handling, processing, and storage of personal information.
Information security is about protecting data against malicious attacks or unauthorized access.
A case in point: if you have a social media account, your password is an aspect of information security. The way social media handles your information is an aspect of digital privacy. As a rule, you consent to security and privacy regulations by clicking “I agree” to the company’s privacy policy and Terms and Conditions. But let’s be honest: when was the last time you carefully read through an app’s privacy policy before accepting it? Still, it’s not the only thing that can give you a headache with digital privacy issues.
Online privacy issues range from the information you don’t mind sharing (say, a public social media account) and annoying privacy trade-offs like targeted ads to public embarrassment or breaches that affect your personal life.
Let’s look at the most controversial, privacy-invading practices.
Search engines log not only things you’ve been looking for. They also track websites that you visit after that. If your search engine provider doubles as a browser, they keep all your browsing history, too.
Search engines can (and do) collect:
- Search history
- IP addresses
- Click-through history
Taken together, this information can be used for “profiling”, or making a customer persona based on the person’s browsing, shopping, and social media preferences. Among other things, customer personas are widely used in personalizing ads. Profiling becomes a serious privacy issue, though, when data-matching algorithms associate someone’s profile with their personally identifiable information, as this might lead to data breaches.
By blocking irritating pop-up ads and keeping trackers at bay, Clario will help you maintain your online privacy while enjoying web browsing.
In recent years, social media privacy hit the spotlight after a string of scandals, including the Cambridge Analytica story when they used data to manipulate voters, cyberbullying, and “doxing” (sharing private information publicly).
On top of that, major social networks have suffered data breaches, leaving millions of users exposed. A recent example is Facebook’s massive data breach that exposed the personal data of 533 million users, including their full names, phone numbers, locations, birth dates, bios, and email addresses.
For the most part, cookies are harmless and even helpful. These pieces of code collect your browsing information and let websites remember your login, preferences, language settings, and other details.
However, cookies might become a concern when it comes to vast amounts of data collected without user consent.
In December 2020, France’s data protection regulator, the Commission Nationale de l’informatique et des libertés (CNIL), ruled that Google and Amazon had to pay 121 million dollars and 35 million euros for breaching Article 82 of the French Data Protection Act. CNIL fined both companies for placing tracking cookies on their user’s computers without prior consent. Google went even further and tracked users who had deactivated ad personalization.
COVID-19 has pushed people to migrate into mobile. The recent App Annie report states that the users’ average time spent with their smartphones topped 4 hours 10 minutes in 2020 — up 20% from 2019. More time spent on mobile means more internet browsing, ads clicking, and, of course, app downloads. As a result, our apps have learned a lot more about us.
But can we be one hundred percent sure what exactly those apps know about us?
Many apps request location details, usernames, phone numbers, or email addresses. Yet, some go further and ask you for risky permissions — information that could cause trouble if it fell into the wrong hands. It could be access to your phone’s microphone/recorder, camera, contacts, or even messages.
A good rule of thumb is to consider whether you trust the app provider to keep this information. If there’s anything you feel uncomfortable about, you can deny access, either when the app asks you for permission or later in the app’s settings.
Identity theft is nothing new. It has been a crime long before the internet. But new technology has opened up fresh avenues for con artists and thieves.
Online identity theft happens when someone accesses your personally identifiable information (PII) to commit fraud. This information might be your driver’s license, bank account details, tax numbers, or anything else that can be used to impersonate you online. In the worst-case scenario, your information might end up for sale on the dark web .
To get this information, bad actors use the following tricks:
- Phishing . Criminals pose as reputable contacts, such as financial institutions, to trick you into surrendering sensitive information or opening malicious attachments
- Malware . Malicious software that can access your device’s operating system and allow hackers to steal your personal information
- Pharming . Hijacking information using a virus without your knowledge, often through a fake site
- Discarded computers and phones. Make sure you thoroughly scrub any device you get rid of before you sell it or give it away
According to the FTC report , the COVID-19 pandemic has been a ripe time for identity thieves, with the number of ID theft cases more than doubling in 2020 compared to 2019.
All those privacy and security issues on the internet might sound scary and can make you feel helpless, but there are simple steps you can take right now to cut the risk of online fraud.
If you worry about how much of your private information is available on the internet, here’s a list of recommendations the Clario team has prepared for you to help you manage and protect your personal information.
1. Secure your devices and use antivirus software
Hackers use various schemes to steal your data. Many of them may not be obvious at first sight. Consider using an up to date, industry-leading antivirus software on your device, whether it’s a mobile or computer. If you're looking for a solution for both, Clario easily combines an antivirus app for Android , iOS, and macOS - all within a single subscription, and even more:
- Anti-tracking tool to prevent websites from collecting your data
- VPN to hide your IP address and online activity
- Anti-spyware tool to stop hackers from spying on you
To maintain your privacy on the internet, please do the following:
- Install Clario
- Get a subscription to create an account
- On the dashboard, click Device
- Hit Start scan and wait for Clario to check your device for malware
- In case Clario detects malicious files, follow the on-screen instructions to protect your data.
Don't forget to encrypt your connection.
- Toggle the Browsing protection switch on
- Click Turn on
- Allow Clario to add VPN Configurations to the settings
- Choose a server location from our extended list
- Enjoy secure browsing!
Voila! Your browsing is now fully protected.
If you are a Chrome user, we would also suggest installing Clario's ad blocker . It’s a web extension that will keep all kinds of advertising, online tracking, and adware at bay. It’s completely free and works with Chrome (you can install it directly from the Chrome Web Store ) and Safari (you’ll need to install it from the Clario app).
2. Use the DNT setting
DNT stands for “do not track,” and you can change DNT settings in your browsers . When you enable it for your browsing — in Chrome, Firefox, or another browser — you tell websites and third-party partners that you do not want to be tracked.
3. Use cookie-blocking browser extensions
These extensions will limit tracking, especially data harvesting by third parties.
4. Opt out of app tracking
You can restrict your apps’ access to your personal information by going to your app or phone settings and opting out of location or other information tracking.
5. Review privacy policies carefully
A common mistake in online browsing is to simply click “agree” to any user agreements and privacy policies without reading them. We strongly recommend looking through any document before clicking “agree” or “accept.”
If you don’t have time to read it (and some user agreements are hundreds of pages long), do at least some research of what kind of information the app or website asks of its users and whether you’re comfortable with that.
6. Browse in incognito mode
Choose incognito mode , or private browsing, when doing things online. Then your online history won’t be stored or remembered.
7. Use a different search engine
If you’re concerned about what your search engine knows about you, it might be a good idea to switch to another engine. DuckDuckGo , for instance, markets itself as a more private and secure alternative to Google.
8. Be wary of what you click online
Don’t click on links to unsafe or bogus websites, or you risk falling victim to a phishing attack and giving up your sensitive data to a scammer. Some phishing threats are masked as ads, so be extra careful with those.
If you follow these recommendations, you’ll know where the danger may hide. This will help you keep your online privacy intact. If there’s anything else you’d like to know about privacy, security, or any online issues, just browse through Clario’s blog and enjoy your digital experience safely.
By Olga Sushko
Privacy and cybersecurity advocate. Mac lover with a passion for copywriting.
Keep reading

Clario News

Data Protection

Digital Wellness
Are you fully secured online? Get Clario for an all-round protection.

An Insight Into the Ethics of Online Privacy: A Thought-Provoking Analysis
In the vast and interconnected landscape of the internet, where personal information flows as freely as digital data packets, the guardians of the virtual realm find themselves faced with a profound ethical challenge: the protection of online privacy. As our lives become increasingly intertwined with the online world, the ethical considerations surrounding the collection, use, and safeguarding of personal data have never been more critical. In this digital age, where convenience often clashes with confidentiality, it is imperative to delve into the complex web of ethical principles that underpin our online interactions. Having an insight into the ethics of online privacy sheds light on the multifaceted dimensions of online privacy ethics, examining issues of consent, transparency, security, and the delicate balance between individual rights and the demands of the digital age.

Ethics in Privacy and Security
Ethics in privacy and security are crucial considerations when examining the intricate realm of online interactions. With the increasing reliance on technology and digital platforms, individuals’ personal information is constantly being collected, stored, and shared. The ethical challenges surrounding online privacy arise from the potential misuse of this data by companies or malicious actors. As such, it is essential to establish robust ethical guidelines for data protection to safeguard individuals’ privacy.
One of the key ethical challenges in online privacy is the collection and use of personal data without informed consent. Online platforms often collect vast amounts of data about individuals, including their browsing history, location information, and even biometric data. This raises concerns about how this information is used and whether individuals have given their explicit consent for its collection. Moreover, there are instances where companies sell or share personal data with third parties without adequate transparency or accountability measures in place.
Another ethical consideration relates to the potential harm that can result from a breach in online security. Data breaches can expose sensitive personal information, leading to identity theft or unauthorized access to financial accounts. Companies have an ethical responsibility to ensure they have robust security measures in place to protect users’ data from such breaches. Additionally, they must promptly notify users if a breach occurs so that appropriate actions can be taken to mitigate any potential harm.
The Importance of Ethics in Privacy and Security
The significance of upholding ethical principles in safeguarding personal information and ensuring digital security cannot be overstated. Adhering to ethical values helps establish trust between individuals and organizations that handle sensitive data, fostering a sense of accountability and responsibility toward the protection of personal information.
To emphasize the importance of ethics in internet privacy and security, consider the following:
Trust and Reputation
Ethics play a fundamental role in privacy and security by fostering trust and preserving reputation. Individuals and organizations that adhere to ethical principles in handling sensitive data and protecting privacy demonstrate their commitment to safeguarding the interests and trust of their data subjects. This trust is essential for maintaining strong relationships with customers, clients, and partners. Conversely, unethical behavior can lead to breaches of trust, damage to reputations, and a loss of credibility that can be difficult to repair. Ethical conduct in privacy and security practices is a cornerstone for building and preserving trust, which is vital in an interconnected world where data sharing and digital transactions are pervasive.
Individual Rights and Dignity
Respecting individual rights and dignity is a core ethical principle in privacy and security. Every person has the right to privacy, and ethical considerations require that these rights be upheld. This means that personal information should not be collected, used, or shared without informed consent, and individuals should have control over their data. Ethical practices recognize that privacy is a fundamental human right, and violating it not only breaches ethical norms but also undermines the dignity and autonomy of individuals. Upholding these rights is not only an ethical imperative but also a legal one in many jurisdictions, further emphasizing the importance of ethical behavior in privacy and security.
Avoiding Harm
Ethical considerations in privacy and security also emphasize the principle of avoiding harm. Unethical data practices can lead to significant harm, including identity theft, financial loss, emotional distress, and discrimination. Ethical behavior requires a commitment to minimizing these potential harms by implementing robust security measures, responsibly handling data, and promptly addressing security vulnerabilities. Prioritizing the avoidance of harm is not only a moral duty but also a practical one, as data breaches and privacy violations can have severe legal and financial consequences for individuals and organizations alike.
Compliance and Accountability

Ethics provide a framework for ensuring compliance with privacy and security laws and standards. Ethical behavior involves a commitment to following the law, which includes adhering to regulations such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Moreover, ethical organizations take responsibility for their actions and are accountable for any breaches or violations that occur. This accountability includes transparency in reporting breaches and taking appropriate corrective actions. Without ethical considerations, compliance may become a mere box-ticking exercise, lacking the genuine commitment to protect privacy and security.
Long-Term Sustainability
Ethical practices in privacy and security contribute to the long-term sustainability of businesses and organizations. Ethical behavior extends beyond short-term gains and focuses on building a resilient and trustworthy foundation for the future. Businesses that prioritize ethics are more likely to create lasting relationships with customers, partners, and stakeholders. By consistently safeguarding privacy and security, these organizations are better equipped to adapt to changing regulatory environments and emerging threats, ensuring their continued success in an evolving digital landscape.
Best Practices for Embedding Ethics Into Your Privacy and Security Practices
Implementing ethical guidelines is essential for embedding principles of privacy and security into organizational practices.
Below are some of the ethical practices that can promote ethical data use:
Build a Taxonomy for Data Privacy
A systematic categorization of data privacy can be constructed to provide a clear and comprehensive understanding of the different dimensions and aspects related to safeguarding personal information. This taxonomy would serve as a framework for organizing various ethical concerns, data ethics principles, privacy regulations, and considerations that guide ethical decisions regarding the handling of personal data. Such a taxonomy would enable individuals and organizations to better comprehend the complex landscape of data privacy and make informed choices about how they handle personal information.
Some key elements that could be included in this taxonomy are:
This category would encompass issues related to obtaining informed consent from individuals before collecting or using their personal data. It would explore questions such as what constitutes valid consent, how to ensure it is freely given, and how to respect an individual’s right to withdraw consent.
Data Minimization
This category would focus on the principle of collecting only the minimal amount of personal data necessary for a specific purpose. It would address strategies for minimizing data collection, retention periods, and anonymization techniques.
Data Security
This category would cover measures taken to protect personal information from unauthorized access or disclosure. It would include topics like encryption, secure storage practices, access controls, and incident response plans.

Transparency
This category would emphasize the importance of providing clear information about how personal data is collected, used, stored, and shared. It would discuss best practices for creating transparent privacy policies and ensuring individuals have access to their own data.
Accountability
This category would delve into mechanisms for holding organizations accountable for their handling of personal data. It would explore topics such as audits, certifications, compliance with privacy regulations, and effective remedies in case of violations.
By developing a comprehensive taxonomy for data privacy that includes these dimensions and aspects, stakeholders can gain a deeper understanding of the ethical considerations involved in protecting personal information. This knowledge can inform decision-making processes regarding the responsible use of technology while fostering trust between individuals and organizations in an increasingly digital world.
Developing a Code of Ethics
Developing a code of ethics is an essential step towards establishing clear guidelines and standards for responsible and ethical behavior in relation to data privacy. A code of ethics serves as a framework that outlines the principles and values that individuals or organizations should adhere to when handling sensitive information. It provides guidance on how to handle customer expectations regarding their privacy rights, ensuring that personal data is collected, stored, and utilized in an ethical manner.
Ethical behavior in the realm of online privacy involves respecting individuals’ autonomy, confidentiality and informed consent. A code of ethics can address these aspects by emphasizing the importance of obtaining explicit consent from individuals before collecting their personal information. Additionally, it can outline the steps necessary to ensure transparency in data collection practices, such as providing individuals with clear explanations about how their data will be used and shared. Moreover, a code of ethics can highlight the significance of maintaining strict measures for data security to protect against unauthorized access or breaches.
By developing a comprehensive code of ethics for data privacy, organizations can foster trust with their customers while also meeting legal requirements. Such a code not only promotes responsible behavior but also enables organizations to navigate through complex ethical dilemmas effectively. It provides employees with clear instructions on how to handle sensitive information ethically and equips them with tools to make informed decisions when faced with potential conflicts between business interests and customer privacy rights.
Data Collection Best Practices
Data collection best practices encompass a range of strategies and techniques aimed at ensuring the responsible and ethical handling of sensitive information in order to protect individuals’ privacy rights.
One important aspect of data collection best practices is obtaining informed consent from individuals before collecting their personal information. This means that data collectors should clearly communicate the purpose for which the data is being collected, how it will be used, and any potential risks involved. Additionally, data collectors should provide individuals with options to opt-out or withdraw their consent at any time.
Another key aspect of data collection best practices is ensuring that only relevant and necessary information is collected. Data collectors should avoid gathering excessive or unnecessary personal details that are not directly related to the intended purpose. By minimizing data collection to what is strictly required, organizations can reduce the risk of unauthorized access or misuse of sensitive information. Furthermore, it is essential for organizations to implement robust security measures to protect collected data from unauthorized access or breaches. This may involve encryption methods, firewalls, secure databases, and regular audits to identify vulnerabilities in systems. By doing so, organizations can ensure they handle individuals’ behavioral data responsibly while respecting their privacy rights.

Data Sharing Best Practices
Data collection best practices are crucial for maintaining the privacy and security of online users. However, once data has been collected, organizations must also consider how they handle and share this information. Data sharing best practices become paramount in ensuring that individuals’ personal information is protected and used responsibly. Sharing data can facilitate collaboration, and innovation, and improve services provided to users. However, it is imperative to approach data sharing with caution and adhere to ethical standards.
Organizations should prioritize the protection of sensitive personal information during the data-sharing process. This includes anonymizing or de-identifying data whenever possible to minimize the risk of privacy breaches. Additionally, implementing robust security measures such as encryption technologies can help safeguard shared data from unauthorized access or misuse.
Investing in Ethical Technology
Investing in ethical technology requires a thoughtful examination of the moral implications surrounding technological advancements and their potential impact on society. Ethical technology involves considering the collection and use of data in a manner that respects individuals’ privacy rights and ensures informed consent. Companies investing in ethical technology prioritize transparency, ensuring that users are aware of the types of data collected, how it is used, and what measures are taken to protect it.
In order to promote online privacy, companies investing in ethical technology should focus on implementing best practices such as:
Data minimization
Minimizing the amount of data collected is crucial for protecting individuals’ privacy. By only collecting necessary information, companies can reduce the risk of misuse or unauthorized access.
Investing in robust encryption algorithms helps safeguard sensitive data by encoding it so that only authorized parties can access and understand it.
Investing in ethical technology is not only a legal requirement but also a moral obligation for companies operating in today’s digital world.
Methods for Data Privacy Protection
Below are Methods that can be used to minimize privacy concerns online:
Encryption is a fundamental method for data privacy protection. It involves converting readable data into an unreadable format using complex algorithms and encryption keys. Only those with the appropriate decryption key can access and decipher the data. This method ensures that even if data is intercepted or stolen, it remains incomprehensible to unauthorized individuals. Encryption is used extensively in communications (e.g., SSL/TLS for secure web browsing), file storage (e.g., encrypted hard drives), and data transmission (e.g., end-to-end encryption in messaging apps) to safeguard sensitive information from prying eyes.
Access Control and Authentication
Implementing robust access control and authentication mechanisms is crucial for data privacy. Access control determines who can access specific data or systems, while authentication ensures that users are who they claim to be. Strong password policies, multi-factor authentication (MFA), and biometric verification are examples of authentication methods. Access control lists (ACLs), role-based access control (RBAC), and least privilege principles help limit access to data based on job roles and responsibilities, reducing the risk of unauthorized access and data breaches.
Regular Data Auditing and Monitoring
Continuous monitoring and auditing of data access and usage is vital for detecting suspicious or unauthorized activities. Security Information and Event Management (SIEM) systems and intrusion detection tools help organizations track who accesses data, when, and for what purpose. By analyzing logs and audit trails, organizations can identify potential breaches or privacy violations and take immediate action to mitigate risks. Regular audits also ensure compliance with privacy regulations.
Data Masking and Anonymization
To protect sensitive data in non-production environments, data masking and anonymization techniques are employed. These methods replace or scramble sensitive information, such as personal identifiers, with fictional or masked data while retaining the data’s format and structure. This allows organizations to use realistic but privacy-safe data for testing, development, and analytics without exposing sensitive details. Data masking and anonymization help prevent accidental exposure of personal information in situations where real data is not necessary.
Privacy by Design
Privacy by design is an approach that embeds data privacy considerations into the entire development and deployment process of systems and applications. It encourages organizations to proactively identify and address privacy risks from the outset, rather than as an afterthought. By conducting privacy impact assessments, implementing data protection features, and adhering to privacy regulations and best practices, organizations can create products and services that inherently prioritize data privacy. This approach ensures that data protection is not merely a compliance requirement but a fundamental aspect of an organization’s culture and operations.
Laws and Regulations That Reinforce Ethics of Online Privacy
Here are some key laws and regulations from various regions that promote ethical data management:
General Data Protection Regulation (GDPR) (European Union)

GDPR is a landmark regulation that enforces strong ethical principles in online privacy. It emphasizes transparency , informed consent, data minimization, and the rights of individuals to control their personal data. GDPR applies not only to EU member states but also to any organization worldwide that processes the personal data of EU residents.
California Consumer Privacy Act (CCPA) (United States)
CCPA is a state-level law in California that empowers consumers with rights over their personal information. It requires businesses to provide transparency about data collection, offer opt-out mechanisms, and refrain from selling personal information without consent. CCPA sets a high standard for ethical data handling practices.
Personal Information Protection Law (PIPL) (China)
China’s PIPL, which became effective in 2021, reinforces ethical standards for online privacy in the country. It mandates obtaining consent for data processing, provides data subject rights, and regulates cross-border data transfers to ensure that personal data is handled responsibly.
Personal Data Protection Bill (India)
While not yet law as of my last knowledge update in September 2021, India’s Personal Data Protection Bill includes principles that align with GDPR, emphasizing consent, data subject rights, and the ethical handling of personal data in the digital sphere.
Privacy Act (Australia)
Australia’s Privacy Act sets out principles for the ethical handling of personal information by government agencies and private sector organizations. It emphasizes transparency, data security, and individuals’ rights to control their data.
How Unethical Use of Data Compromises Privacy
The unethical use of data that compromises privacy is a growing concern in the digital age.
Here are some of the ethical issues in Online Privacy:
Data Breaches
Hackers and cybercriminals often target organizations to gain unauthorized access to personal data. When successful, these breaches can lead to the exposure of sensitive information, such as Social Security numbers, credit card details, and personal addresses, putting individuals at risk of identity theft and financial harm.
Data Monetization and Profiling
Many online companies collect vast amounts of user data without clear and transparent consent. They then monetize this data by creating detailed profiles of individuals, often for targeted advertising. This practice can feel invasive, eroding personal privacy and autonomy, and can lead to concerns about manipulation and discrimination based on the information collected.
Government Surveillance
Governments may engage in mass surveillance programs that collect data on their citizens without their knowledge or consent. Such programs can have a chilling effect on free speech, undermine democracy, and infringe upon individuals’ right to privacy.
Social Engineering and Phishing

Cybercriminals may use personal data to craft convincing phishing attacks or engage in social engineering tactics, tricking individuals into revealing even more sensitive information, such as login credentials, bank account details, or passwords.
Data Sharing Without Consent
Organizations, including tech giants and social media platforms, may share user data with third parties without explicit consent. This often happens behind opaque privacy policies, leaving users unaware of how their data is being used and by whom.
Deepfakes and Manipulated Content
Advances in technology have made it possible to create convincing deepfake videos and manipulated content that can deceive individuals and damage reputations. The unethical use of such content can lead to privacy violations and misinformation.
Frequently Asked Questions
How does the concept of ethics apply to online privacy and security.
The concept of ethics is highly relevant to online privacy and security as it dictates the moral principles and standards that guide individuals, organizations, and governments in their actions within the digital realm. Ethical considerations emphasize the importance of respecting individuals’ rights to privacy and autonomy, which include obtaining informed consent for data collection and ensuring data security to prevent harm. Additionally, ethics in online privacy and security underscore the responsibility of all stakeholders to maintain transparency, honesty, and accountability in their digital interactions, fostering trust and responsible behavior in the digital age.
What Are the Potential Consequences of Neglecting Ethics in Privacy and Security Practices?
Neglecting ethics in privacy and security practices can lead to severe consequences. First it can result in breaches of individuals’ privacy rights, eroding trust and damaging reputations. Also, unethical behavior can expose sensitive personal information, leading to identity theft, financial loss, and emotional distress for individuals. Moreover, legal and regulatory penalties, including substantial fines and legal action, can be imposed on organizations that fail to adhere to ethical data handling practices, further jeopardizing their sustainability and credibility.
What Are the Key Elements of a Comprehensive Code of Ethics for Data Privacy?
A comprehensive code of ethics for data privacy should encompass several key elements. It should prioritize informed consent, ensuring that individuals are fully aware of how their data will be collected, used, and shared. Additionally, it should emphasize data minimization, advocating for the collection of only the data necessary for a specific purpose and the deletion of unnecessary information. Lastly, such a code should underscore transparency, requiring organizations to openly communicate their data practices and regularly audit their processes to ensure compliance with privacy principles and relevant laws.
Can Online Privacy Ethics Adapt To Emerging Technologies Like AI and IoT?
Yes, online privacy ethics should adapt to emerging technologies to address new challenges and ensure that ethical principles are applied to AI, IoT, and other technologies.
Where information flows as freely as the thoughts and ideas of billions, the guardians of online privacy and ethics stand as sentinels of our digital age. As we journey through this interconnected virtual world, their role becomes increasingly vital, protecting the rights, dignity, and security of individuals in the face of complex challenges. In this age of rapid technological advancement, the ethical principles discussed within this exploration serve as a guiding light, reminding us that while the digital realm offers boundless opportunities, it also demands our unwavering commitment to preserving the values of privacy, security, and respect for one another.
Leave a Comment Cancel reply
Take 10% OFF— Expires in h m s Use code save10u during checkout.
Chat with us
- Live Chat Talk to a specialist
- Self-service options
- Search FAQs Fast answers, no waiting
- Ultius 101 New client? Click here
- Messenger
International support numbers
For reference only, subject to Terms and Fair Use policies.
- How it Works
Learn more about us
- Future writers
- Explore further
Ultius Blog
Sample essay on online privacy.

Select network
The advent of the Internet age has been characterized by an unprecedented proliferation of communication and availability of information. However, the dark side is that such developments also raise questions pertaining to the ethical value of privacy: either through direct efforts by stakeholders to access confidential information or through simple ignorance on the part of Internet users, the enormous resources of the Internet also imply that the Internet, used improperly, could seriously threaten the right to individual privacy.
The present sample essay will explore some of the issues that have emerged around this subject over recent times. In particular, it will discuss the National Security Administration (NSA), Snowden, Facebook, and the value of transparency. A key theme that will emerge over the course of the exposition is that in general, Americans believe that whereas they have a right to personal privacy, organizations have a duty to respect the value of transparency. This type of document would likely be found in a tech blog or as a writing assignment .
The NSA and Snowden
To start with, then, the NSA has been in the news recently as a result of the emergence of evidence that the organization had been unlawfully spying on the communications of Americans . As the Electronic Frontier Foundation has written:
"Secret government documents, published by the media in 2013, confirm the NSA obtains full copies of everything that is carried along major domestic fiber optic cable networks" (paragraph 4).
Such operations were conducted as part of a surveillance program known as Prism. The British newspaper The Guardian was instrumental in reporting on this issue as it was in the process of emerging. For example, in a news article from 2013, Greenwald and MacAskill have written:
"The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation—classified as top secret with no distribution to foreign allies—which was apparently used to train intelligence operatives on the capabilities of the program" (paragraph 3).
In any event, it is by now an indisputable fact that the NSA has in fact been spying on American citizens.
From a historical perspective, the activities of the NSA can be understood as related to the aftermath of the 9/11 terrorist attacks that occurred in 2001. During this time, for example, the Patriot Act was passed, which essentially consisted of provisions that infringed on civil liberties in the name of national security (see Library of Congress). The idea was that in a time of national crisis, individuals should be willing to compromise of some of the individual rights for the sake of the well-being of the broader community as a whole.
This would include the right to private communication, insofar as such privacy would potentially undermine the security of the nation. According to the Electronic Frontier Foundation, it was precisely the provisions of legislation such as the Patriot Act that the NSA has used to justify its activities; and rumors of unlawful spying have been present since at least the year 2005. It was only recently, though, that hard evidence emerged regarding these dubious activities.
The role of Edward Snowden in regards to online privacy
Edward Snowden was the man who was primarily responsible for bringing the domestic surveillance activities of the NSA to the light of the public eye. Not only did the documents leaked by Snowden reveal that the NSA had in fact been engaging in domestic surveillance, it also revealed that it was primarily ordinary Americans who had nothing to do with any kind of investigation who were getting caught by the surveillance. As Gellman, Tate, and Soltani have put it:
"Ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted by the National Security Agency from U.S. digital networks. . . . The daily lives of more than 10,000 account holders who were not targeted are catalogued and recorded nevertheless" (paragraphs 1 and 7).
In other words, the NSA was found to have violated the online privacy of Americans not simply within the context of legitimate investigations but rather as a matter of course, as if the value of individual privacy were no longer even a relevant factor to take into consideration when planning surveillance actions.
Such revelations have made a significant impact on the perceptions of Americans regarding online privacy. For example, Malden, writing on behalf of the Pew Internet Research Project, has delineated some key statistics regarding Americans' perceptions of online privacy; and among other things, it has been found that
"81% feel not very or not at all secure using social media sites when they want to share private information with another trusted person or organization," and "57% feel insecure sending private information via email" (paragraph 7).
Moreover, correlations were found between increased levels of insecurity on the one hand and greater awareness of the NSA's surveillance program on the other. In short, the events surrounding NSA and Snowden have had a strong effect on the popular culture of electronic communication within the United States. A strong majority of people now seem to take it almost for granted that some stakeholder or another is illicitly monitoring their private communications, and that they must take steps in order to protect themselves from such invasions of personal privacy. The general mindset within the nation regarding online privacy is thus marked by a very high level of suspicion and mistrust.
The case of Facebook and online privacy
At this point in the discussion, it may be useful to turn attention to a specific forum for online communication: Facebook. Despite denials from the founder of the company, there would seem to be a significant popular perception that Facebook did in fact collude with the NSA and gave up the personal information of its users to the government. Whether this is or is not true, it is rather revealing about the level of trust that Facebook users have in the integrity of the company. According to Debatin, Lovejoy, Horn, and Hughes, many Facebook users seem to exhibit an ambivalent behavioral trend in which they both report being highly aware of privacy issues and yet nevertheless upload significant amounts of personal information onto their Facebook accounts.
These researchers have addressed this issue from a somewhat anthropological perspective and concluded that the paradox can be explained by how ritualistically integrated social media sites become into users' lives:
"Social network sites deeply penetrate their users' everyday life and, as pervasive technology, tend to become invisible once they are widely adopted, ubiquitous and taken for granted" (Debatin et al. 83).
This significantly reduces users' practical concern for privacy even as they understand the concern in theory.
This also calls attention to a broader point regarding online privacy: the violation of privacy can occur not only because of direct malfeasance on the part of a given stakeholder but also due to ignorance on the part of Internet users. For example, a given Facebook user may upload compromising photographs onto his account without even thinking about the fact that (for example) his boss could access those photographs in a fully legal and legitimate way.
Something similar can be said about other forms of online communication as well: insofar as people are either not aware that they are being watched or do not take adequate action on the implications of this awareness, violations of privacy could occur in a "passive" as opposed to "active" way. That is, Internet users would make their lives essentially open to the public without even realizing they are doing so; and anyone who wanted the users' information could simply take it without even being in violation of the law. In this context, the NSA revelations may have ultimately had at least some positive effect, insofar as they have clearly contributed to Americans becoming more aware of the nature of the dangers at play (see Maden).
Privacy versus transparency
It is worth turning now to a more careful reflection on the ethical principles that are involved when discussing the subject of online privacy. In particular, one perceives something of a double standard that nevertheless is not illegitimate. On the one hand, when the NSA conducts a secret surveillance program against Americans, this is generally interpreted to mean that the NSA fundamentally lacks transparency, which is unacceptable for a governmental organization within a democratic society.
On the other, when Snowden leaks the NSA's "private" information to the public, this is generally interpreted not as an assault against the NSA's privacy but rather as a defense of the privacy of American citizens. Similarly, Facebook cannot demand that its users become "transparent" and thus willing to share private information with the public; rather, it is expected that Facebook will be transparent with its privacy policy and ensure the security of its users' information.
The general principle that emerges here, then, is that organizations are expected to be transparent toward their constituents, but that individual constituents are not therefore obliged to be transparent in turn toward the organization. This proposition would seem to be informed by a fundamentally libertarian political perspective, where libertarianism can be understood in the broadest sense as a
"political philosophy that affirms the rights of individuals to liberty, to acquire, keep, and exchange their holdings, and considers the protection of individual rights the primary role of the state" (Vallentyne and Bas van der Vossen, (paragraph 1).
Essentially, privacy is among the most individualistic of all ethical values; and whenever one insists on the value of privacy, one implicitly also insists on the priority of the individual over the community. Thus, if it is inappropriate for the NSA to spy on its own people, then this is because the NSA was only established by the constituent power of the people in the first place, and its fundamental obligation would thus be to protect the rights of those people (i.e. Americans) and not to violate those rights.
As a caveat, though, it should be noted that the extent to which this logic obtains depends to a certain extent on how much danger one imagines the community as a whole to be in. In general, when the existence of a community is threatened, emergency powers are granted to executives, and individual citizens are expected to compromise on their own rights until the danger has passed. When does this invasion of online privacy contridict the United States Consitution?
The logic here would be that if the community were to be annihilated, then this would cause serious harm to all members of the community. This would explain why it is only an appeal to national security that can even potentially justify activities such as the NSA's Prism surveillance program. In this context, Snowden's revelations may have been especially devastating because they showed that much of the information collected by the NSA had nothing to do with national security, and that the NSA thus had no right to violate its basic obligation regarding transparency.
In summary, this essay has consisted of a discussion of issues regarding online privacy in the modern United States. Subjects addressed have included the NSA and Snowden, the case of Facebook, and the interplay within the ethical values of privacy and transparency. Ultimately, these issues are related to political questions regarding the meaning of democracy, the rights and prerogatives of the individual, and the obligations that organizations have toward their constituents. Understood in this way, issues regarding online privacy merely continue discussions that have historically been in progress for quite a long time.
Does this look like one of your assignments? You can get a custom research paper on this subject from Ultius.
Works Cited
Debatin, Berhard, Jennette P. Lovejoy, Ann-Kathrin Horn, and Brittany N. Hughes. "Facebook and Online Privacy: Attitudes, Behaviors, and Unintended Consequences." Journal of Computer Mediated Communication 15 (2009): 83-108.
Electronic Frontier Foundation. NSA Spying on Americans. 2014. Web. 1 Dec. 2014. <https://www.eff.org/nsa-spying/>.
Gellman, Barton, Julie Tate, and Askan Soltani. "In NSA-Intercepted Data, Those Not Targeted Far Outnumber the Foreigners Who Are." The Washington Post 5 Jul. 2014. Web. 1 Dec. 2014. <http://www.washingtonpost.com/world/national-security/in-nsa-intercepted-data-those-not-targeted-far-outnumber-the-foreigners-who-are/2014/07/05/8139adf8-045a- 11e4-8572-4b1b969b6322_story.html>.
Greenwald, Glenn, and Ewen MacAskill. "NSA Prism Program taps in to user data of Apple, Google and Others." The Guardian 7 Jun. 2013. Web. 1 Dec. 2014.
<http://www.theguardian.com/world/2013/jun/06/us-tech-giants-nsa-data>.
Library of Congress. "H.R.3162: Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT ACT) Act of 2001." THOMAS, 2001. Web. 1 Dec. 2014. < http://thomas.loc.gov/cgi- bin/bdquery/z?d107:H.R.3162:>.
Maden, Mary. "Public Perceptions of Privacy and Security in the Post-Snowden Era." Pew Research Internet Project, 12 Nov. 2014. Web. 1 Dec. 2014. <http://www.pewinternet.org/2014/11/12/public-privacy-perceptions/#ftag=YHFb1d24ec>.
Vallentyne, Peter, and Bas van der Vossen. "Libertarianism." Stanford Encyclopedia of Philosophy. 2014. Web. 1 Dec. 2014. <http://plato.stanford.edu/entries/libertarianism/>.
https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
- Chicago Style
Ultius, Inc. "Sample Essay on Online Privacy." Ultius | Custom Writing and Editing Services. Ultius Blog, 01 Dec. 2014. https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
Copied to clipboard
Click here for more help with MLA citations.
Ultius, Inc. (2014, December 01). Sample Essay on Online Privacy. Retrieved from Ultius | Custom Writing and Editing Services, https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
Click here for more help with APA citations.
Ultius, Inc. "Sample Essay on Online Privacy." Ultius | Custom Writing and Editing Services. December 01, 2014 https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html.
Click here for more help with CMS citations.
Click here for more help with Turabian citations.
Ultius is the trusted provider of content solutions and matches customers with highly qualified writers for sample writing, academic editing, and business writing.

Tested Daily
Click to Verify
About The Author
This post was written by Ultius.

- Writer Options
- Custom Writing
- Business Documents
- Support Desk
- +1-800-405-2972
- Submit bug report
- A+ BBB Rating!
Ultius is the trusted provider of content solutions for consumers around the world. Connect with great American writers and get 24/7 support.
© 2024 Ultius, Inc.
- Refund & Cancellation Policy
Free Money For College!
Yeah. You read that right —We're giving away free scholarship money! Our next drawing will be held soon.
Our next winner will receive over $500 in funds. Funds can be used for tuition, books, housing, and/or other school expenses. Apply today for your chance to win!
* We will never share your email with third party advertisers or send you spam.
** By providing my email address, I am consenting to reasonable communications from Ultius regarding the promotion.
Past winner

- Name Samantha M.
- From Pepperdine University '22
- Studies Psychology
- Won $2,000.00
- Award SEED Scholarship
- Awarded Sep. 5, 2018
Thanks for filling that out.
Check your inbox for an email about the scholarship and how to apply.

How the pandemic has exacerbated online privacy threats
Subscribe to the center for technology innovation newsletter, niam yaraghi and niam yaraghi nonresident senior fellow - governance studies , center for technology innovation @niamyaraghi samantha lai samantha lai research analyst, center for technology innovation - the brookings institution @_samanthalai_.
January 13, 2022
Driven by lockdown policies and a fear of contracting COVID-19, many individuals have moved to seek online alternatives for many of their offline activities over the pandemic, leading to a surge in online traffic—and increased tracking by commercial and public websites. These websites then share the data they collect with third parties, who aggregate the data to create user profiles for advertising purposes. Many of these third parties are unknown to users and have access to users’ data without their explicit consent. Additionally, while users may agree to share one specific data type with a website, an aggregation of various data types across many different websites can enable third parties to use advanced data analytics to make very precise inferences about sensitive aspects of users’ lives. Such practices have enabled increased commercial and state surveillance that consumers have little awareness or control over. This significantly elevates privacy concerns about consumer welfare in the rapidly-digitizing world we live in today. In response to such concerns, legislative efforts such as Europe’s General Data Protection Rule (GDPR ) and its American counterpart, California’s Consumer Privacy Act (CCPA ) have sought to curb data collection and sharing with third parties.
Brookings Senior Fellow Niam Yaraghi, along with a series of co-authors, conducted statistical analyses and authored a paper on how often websites shared user information with third-party sites, and whether such behavior differed across websites. Between April 9th and August 27th, 2020, they collected data on the number of third parties each of the top 1,000 websites in the United States interacted with on a daily basis. This data was collected from a virtual server with a New York IP address. They then combined this with data on the weekly number of COVID-19 related deaths in the state of New York over the same period in order to examine how the spread of the COVID-19 pandemic affects third-party tracking and the extent to which it varies by website characteristics. Noted characteristics included the industry that each website operates in and whether the site asks for permission before placing cookies on users’ browsers. Websites in the News & Media , Health & Healthcare , Telecommunications , and Games industries were classified as “high traffic,” as they were in sectors that experienced a spike in user traffic over COVID-19 lockdown policies.
The analyses found that the extent of third-party data sharing by websites increased with internet use as the pandemic progressed and users relied more on online alternatives. Websites with more traffic did so at a larger scale compared to those that did not. Merely asking for consent before collecting users’ data did not necessarily reduce the number of third parties; privacy-respecting websites interacted with third parties at similar rates compared to other sites. However, websites that asked for permission before placing cookies on users’ browsers have been shown to reduce their third parties over time as their traffic surged over the pandemic.
Amid national discussions about the necessity of potential legislation to protect users’ privacy, this research highlights how the pandemic has exacerbated online privacy threats and the importance of addressing such threats to protect user welfare. It is also important to note the difference in behaviors of privacy-respecting and non-respecting websites when it comes to collecting and sharing their user data.
Related Content
Cameron F. Kerry
December 16, 2021
Cameron F. Kerry, Jules Polonetsky
December 1, 2021
August 16, 2021
Internet & Telecommunications
Governance Studies
Center for Technology Innovation
The Privacy Debate
Nicol Turner Lee
March 12, 2024
March 11, 2024
Darrell M. West, Steven Overly
Read our research on: Abortion | Podcasts | Election 2024
Regions & Countries
1. views of data privacy risks, personal data and digital privacy laws.
Online privacy is complex, encompassing debates over law enforcement’s data access, government regulation and what information companies can collect. This chapter examines Americans’ perspectives on these issues and highlights how views vary across different groups, particularly by education and age.
When managing their privacy online, most Americans say they trust themselves to make the right decisions about their personal information (78%), and a majority are skeptical that anything they do will make a difference (61%).
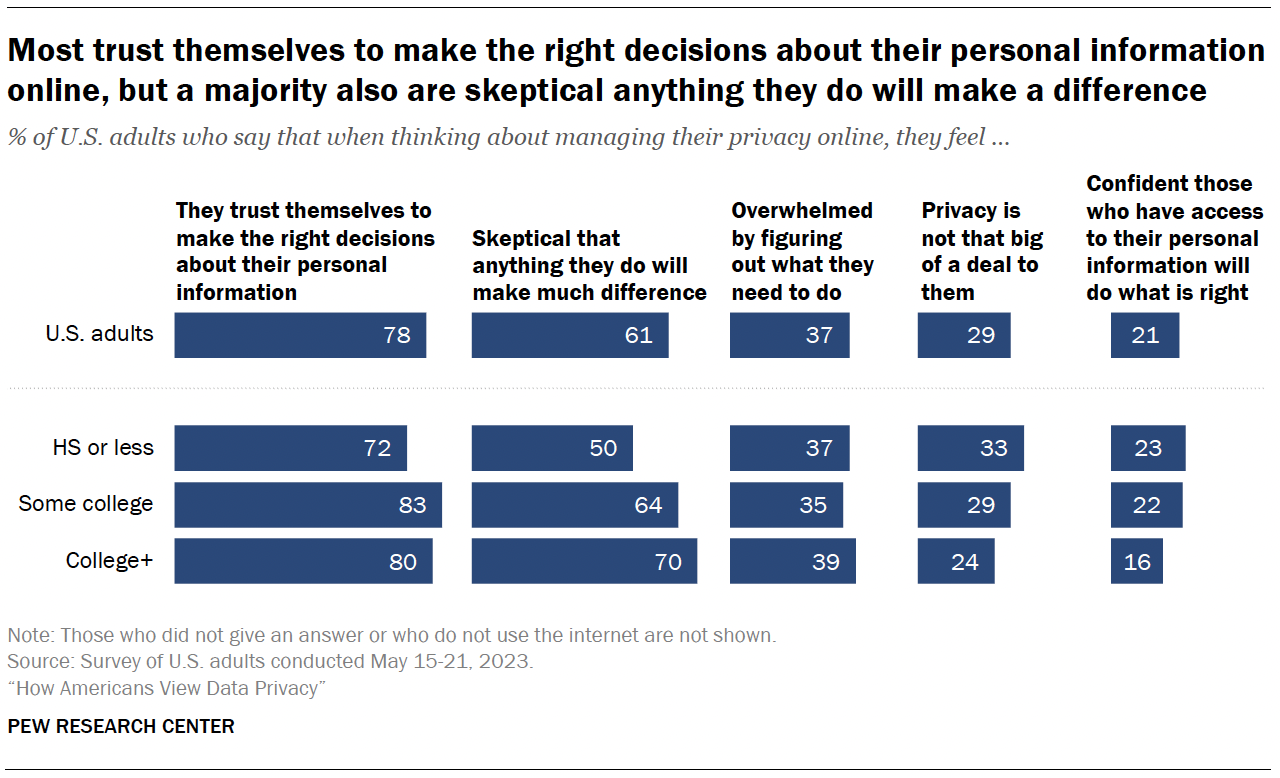
Far fewer mention being overwhelmed by figuring out what they need to do (37%) or say privacy is not that big of a deal to them (29%).
Another 21% are confident that those with access to their personal information will do what is right.
Education differences
- 81% of those with at least some college experience say they trust themselves to make the right decisions about their personal information online, compared with 72% of those with a high school diploma or less.
- 67% of those with at least some college are skeptical that anything they do to manage their online privacy will make a difference, compared with half of those with a high school diploma or less formal education.
On the other hand, those with a high school education or less are more likely than those with some college experience or more to say that privacy isn’t that big of a deal to them and that they are confident that those who have access to their personal information will do the right thing.
Personal data and information
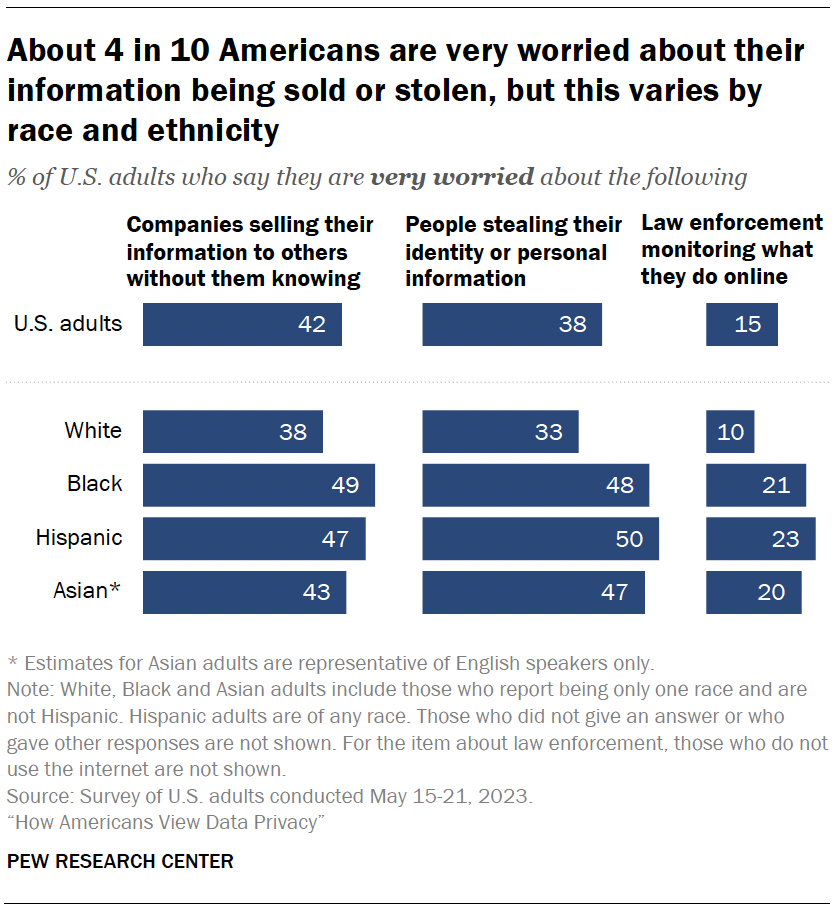
The survey also explores the concerns people have about data collection and security – specifically, how they feel about three scenarios around companies, law enforcement and identity theft.
Roughly four-in-ten Americans say they are very worried about companies selling their information to others without them knowing (42%) or people stealing their identity or personal information (38%). Fewer are apprehensive about law enforcement monitoring what they do online (15%).
Racial and ethnic differences
However, some of these shares are higher among Hispanic, Black or Asian adults: 1
- Roughly half of Hispanic, Black or Asian adults are very worried about people stealing their identity or personal information, compared with a third of White adults.
- About one-in-five of each group are very worried about law enforcement monitoring their online activity; 10% of White adults say this.
Feelings of concern, confusion and a lack of control over one’s data
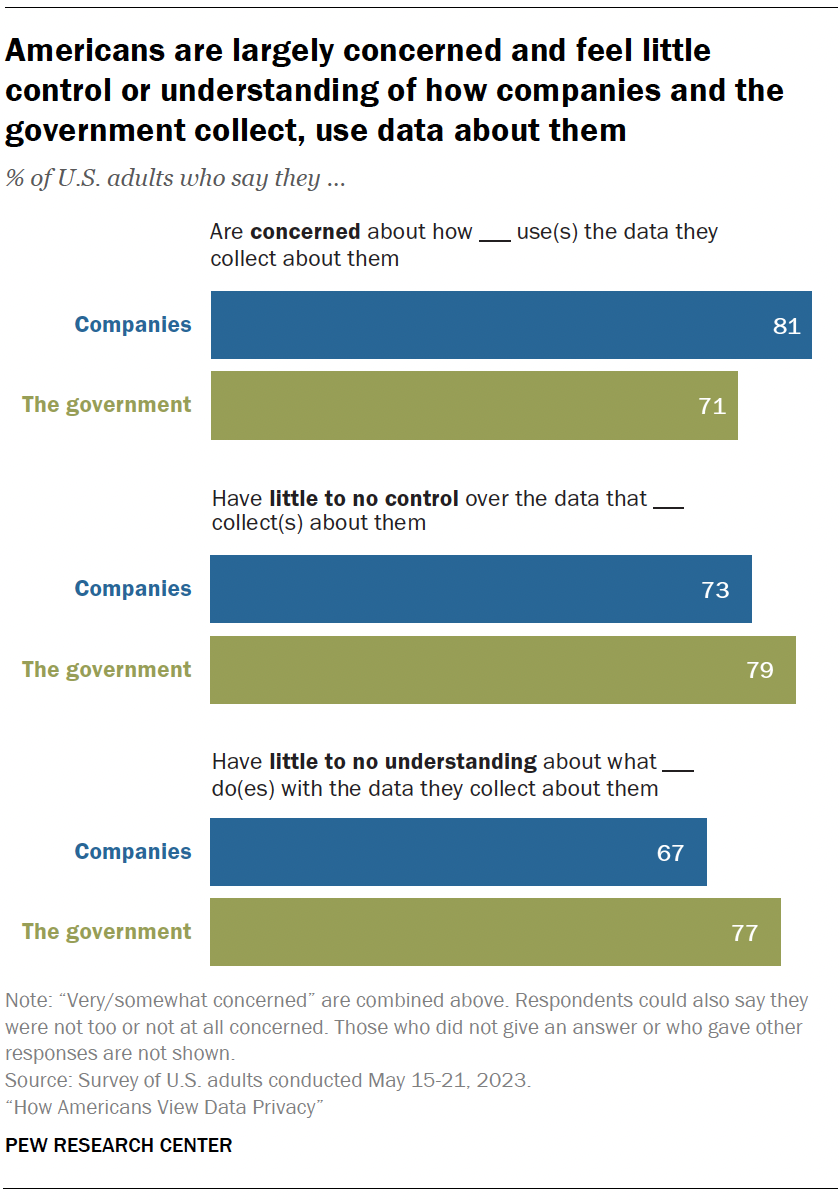
A majority of Americans say they are concerned, lack control and have a limited understanding about how the data collected about them is used. This is true whether it’s the government or companies using their data. Similar sentiments were expressed in 2019, when we last asked about this .
Concern is high: 81% say they feel very or somewhat concerned with how companies use the data they collect about them. Fully 71% say the same regarding the government’s use of data.
People don’t feel in control: Roughly three-quarters or more feel they have very little or no control over the data collected about them by companies (73%) or the government (79%).
Understanding is low: Americans also say they don’t understand what these actors are doing with the data collected about them. Majorities say they have very little or no understanding of this, whether by the government (77%) or companies (67%).
Americans are now less knowledgeable than before about how companies are using their personal data. The share who say they don’t understand this has risen from 59% in 2019 to 67% in 2023.
They have also grown more concerned about how the government uses the data it collects about them, with the share expressing concern up from 64% to 71% over this same period.
While these sentiments have not changed significantly since 2019 among Democrats and those who lean toward the Democratic Party, Republicans and GOP leaners have grown more wary of government data collection. Today, 77% of Republicans say they are concerned about how the government uses data it collects about them, up from 63% four years earlier.
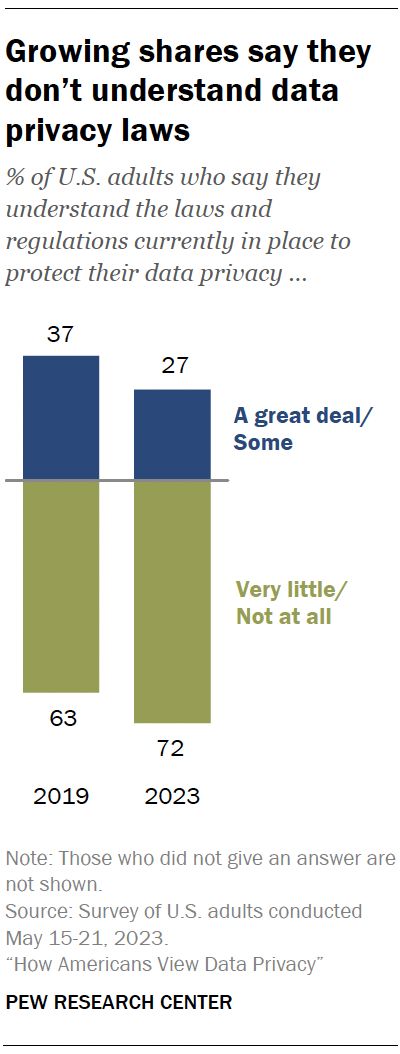
Privacy laws and regulation
Americans are less knowledgeable about data privacy laws today than in the past.
Today, 72% of Americans say they have little to no understanding about the laws and regulations that are currently in place to protect their data privacy. This is up from 63% in 2019.
By comparison, the shares who say they understand some or a great deal about these laws decreased from 37% in 2019 to 27% in 2023.
Americans largely favor more regulation to protect personal information
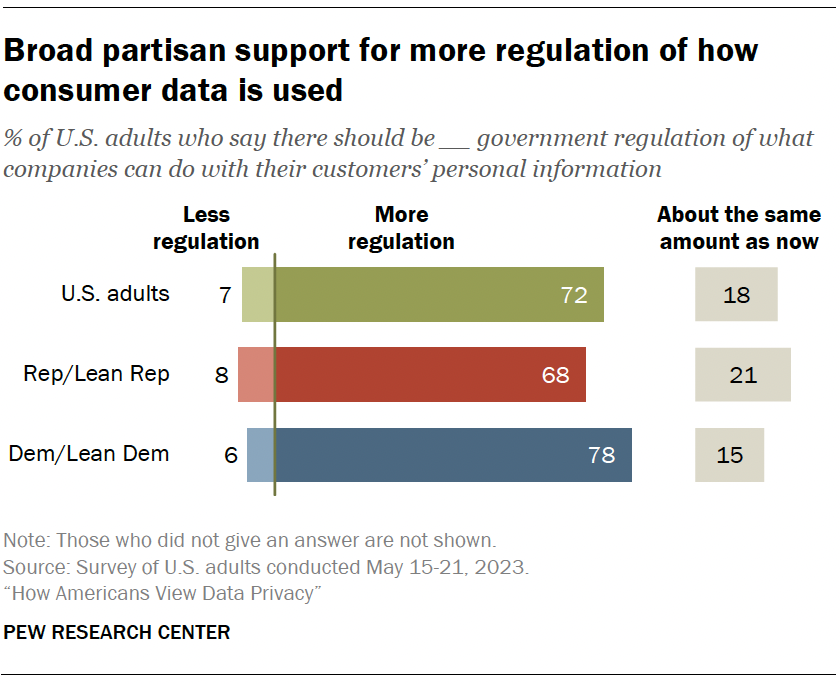
Overall, 72% say there should be more government regulation of what companies can do with their customers’ personal information. Just 7% say there should be less regulation. Another 18% say it should stay about the same.
Views by political affiliation
There is broad partisan support for greater involvement by the government in regulating consumer data.
A majority of Democrats and Republicans say there should be more government regulation for how companies treat users’ personal information (78% vs. 68%).
These findings are largely on par with a 2019 Center survey that showed strong support for increased regulations across parties.
Trust in social media executives
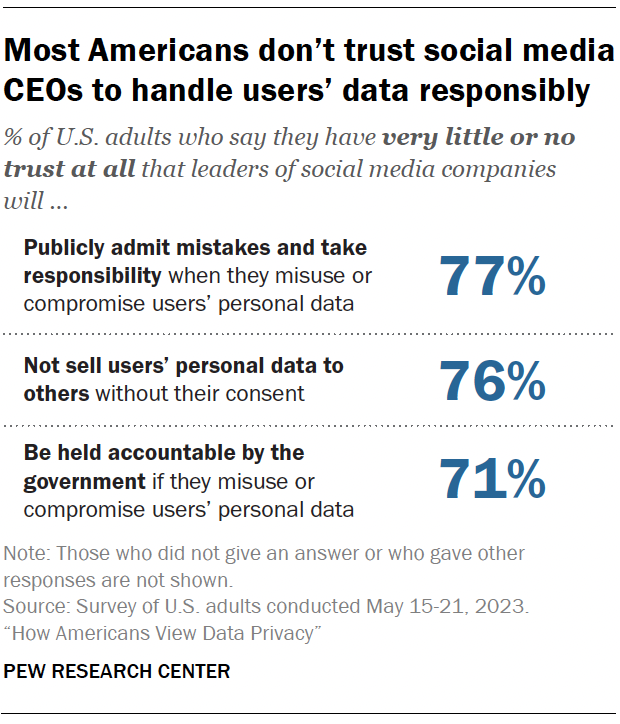
Majorities of Americans say they have little to no trust that leaders of social media companies will publicly admit mistakes regarding consumer data being misused or compromised (77%), that these leaders will not sell users’ personal data to others without their consent (76%), and that leaders would be held accountable by the government if they were to misuse or compromise users’ personal data (71%).
This includes notable shares who have no trust at all in those who are running social media sites. For example, 46% say they have no trust at all in executives of social media companies to not sell users’ data without their consent.
Children’s online privacy: Concerns and responsibility
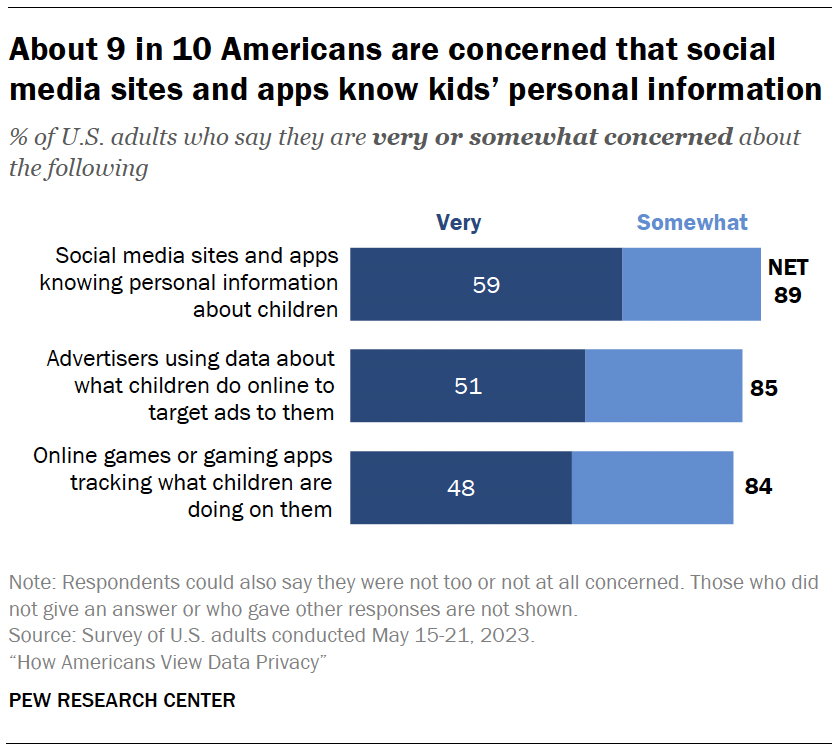
Most Americans say they are concerned about social media sites knowing personal information about children (89%), advertisers using data about what children do online to target ads to them (85%) and online games tracking what children are doing on them (84%).
Concern is widespread, with no statistically significant differences between those with and without children.
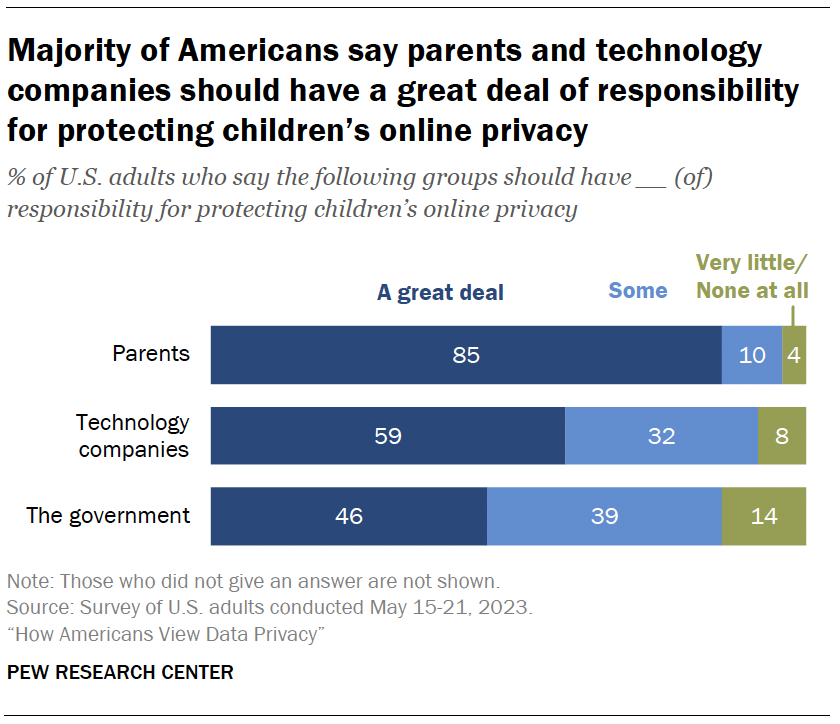
Another key question is who should be responsible for the actual protection of kids’ online privacy.
Fully 85% say parents bear a great deal of responsibility for protecting children’s online privacy. Roughly six-in-ten say the same about technology companies, and an even smaller share believe the government should have a great deal of responsibility.
Law enforcement and surveillance
The survey also measured how acceptable Americans think it is for law enforcement to use surveillance tools during criminal investigations.
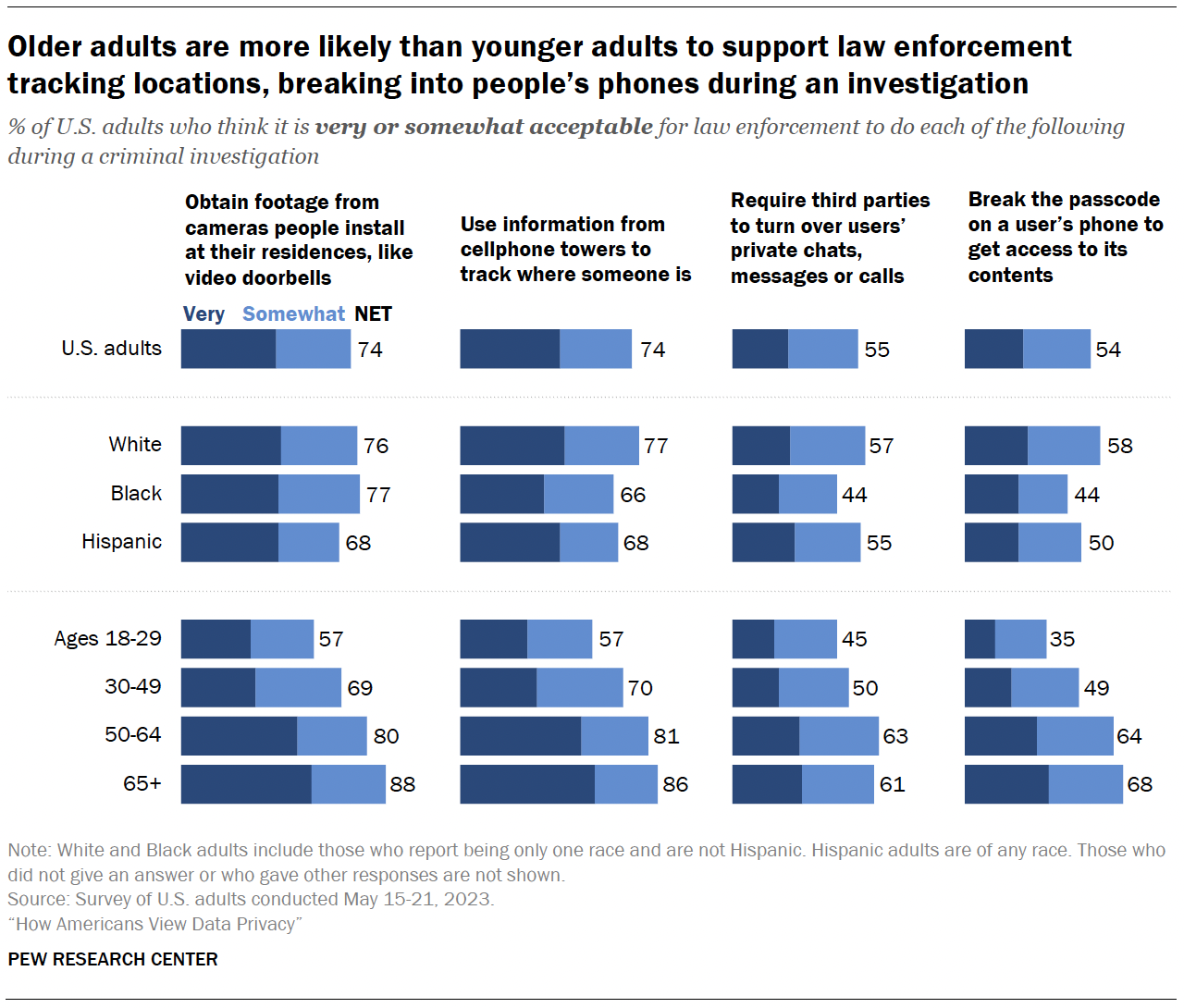
Roughly three-quarters of Americans say it’s very or somewhat acceptable for law enforcement to obtain footage from cameras people install at their residences during a criminal investigation or use information from cellphone towers to track where someone is.
About one-in-ten Americans say they aren’t sure how they feel about law enforcement doing each of these things.
Age differences
Older adults are much more likely than younger adults to say it’s at least somewhat acceptable for law enforcement to take each of these actions in criminal investigations.
For example, 88% of those 65 and older say it’s acceptable for law enforcement to obtain footage from cameras people install at their residences, compared with 57% of those ages 18 to 29.
In the case of a criminal investigation:
- White adults are more likely than Hispanic and Black adults to think it’s acceptable for law enforcement to use information from cellphone towers to track people’s locations and to break the passcode on a user’s phone to get access to its contents.
- White and Hispanic adults are more likely than Black adults to say it’s acceptable to require third parties to turn over users’ private chats, messages or calls.
AI and data collection
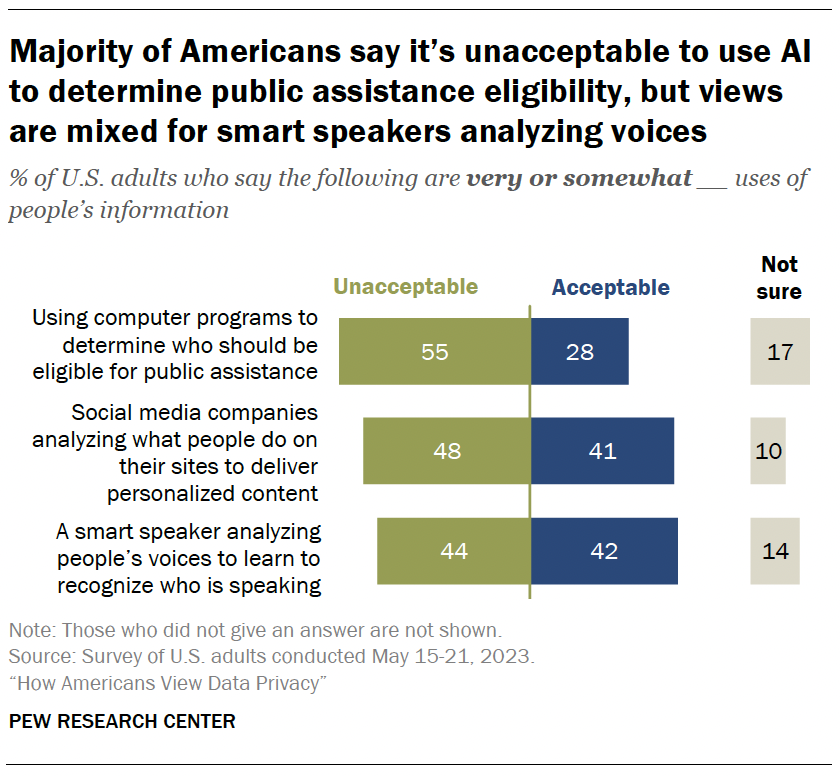
Artificial intelligence (AI) can be used to collect and analyze people’s personal information. Some Americans are wary of companies using AI in this way.
Fully 55% of adults say using computer programs to determine who should be eligible for public assistance is unacceptable. Roughly a quarter say it’s an acceptable use of AI.
Roughly half (48%) think it is unacceptable for social media companies to analyze what people do on their sites to deliver personalized content. Still, 41% are supportive of this.
Views are mixed when it comes to smart speakers analyzing people’s voices to learn who is speaking. Statistically equal shares say it’s unacceptable and acceptable (44% and 42%, respectively).
And some Americans – ranging from 10% to 17% – are uncertain about whether these uses are acceptable or not.
- 49% of adults 50 and older say it’s unacceptable for a smart speaker to analyze people’s voices to learn to recognize who’s speaking. This share drops to four-in-ten among adults under 50.
- Similarly, 56% of those 50 and older say social media companies analyzing what people do on their sites to deliver personalized content is unacceptable. But 41% of those under 50 say the same.
- There are no differences between those under 50 and those 50 and older over whether computer programs should be used to determine eligibility for public assistance.
Trust in companies that use AI
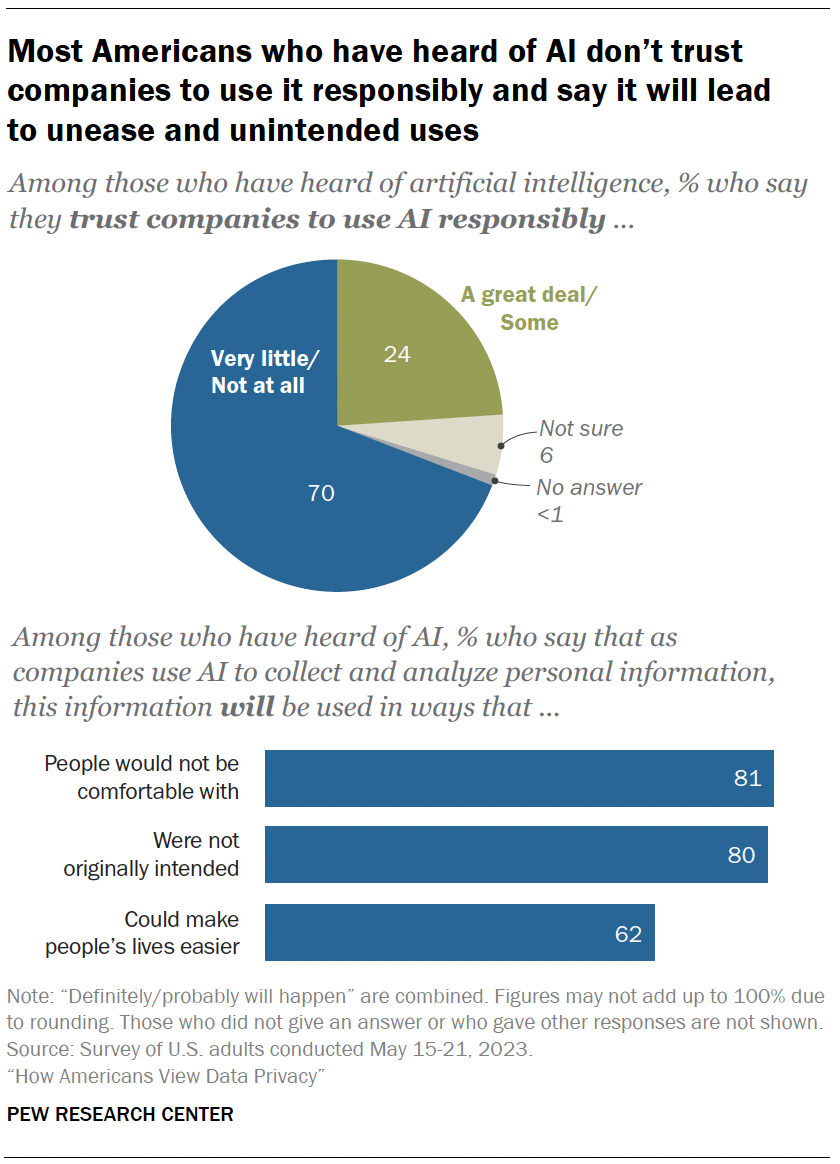
In addition to understanding people’s comfort level with certain uses of AI, the survey also measured the public’s attitudes toward companies that are utilizing AI in their products.
Among those who have heard of AI:
- 70% say they have little to no trust in companies to make responsible decisions about how they use AI in their products.
- Roughly eight-in-ten say the information will be used in ways people are not comfortable with or that were not originally intended.
- Views are more mixed regarding the potential that using AI to analyze personal details could make life easier. A majority of those who have heard of AI say this will happen (62%). Regarding differences by age, adults under 50 are more optimistic than those 50 and older (70% vs. 54%).
- 87% of those with a college degree or higher say companies will use AI to analyze personal details in ways people would not be comfortable with. Some 82% of those with some college experience and 74% with a high school diploma or less say the same.
- 88% of those with a bachelor’s degree or more say companies will use this information in ways that were not originally intended. This share drops to 80% among those with some college experience and 71% among those with a high school diploma or less.
- About three-quarters of those with a college degree or more (74%) say this information will be used in ways that could make people’s lives easier. But this share drops to 60% among those with some college experience and 52% among those with a high school diploma or less.
- This survey includes a total sample size of 364 Asian adults. The sample primarily includes English-speaking Asian adults and, therefore, it may not be representative of the overall Asian adult population. Despite this limitation, it is important to report the views of Asian adults on the topics in this study. As always, Asian adults’ responses are incorporated into the general population figures throughout this report. Asian adults are shown as a separate group when the question was asked of the full sample. Because of the relatively small sample size and a reduction in precision due to weighting, results are not shown separately for Asian adults for questions that were only asked of a random half of respondents (Form 1/Form 2). ↩
- Half of respondents were asked the questions above, and the other half received the same questions with the added context of it being a “criminal investigation where public safety is at risk.” Differences in response were largely modest. See Appendix A for these findings. ↩
Sign up for our Internet, Science and Tech newsletter
New findings, delivered monthly
Report Materials
Table of contents, what americans know about ai, cybersecurity and big tech, quiz: test your knowledge of digital topics, majority of americans say tiktok is a threat to national security, as ai spreads, experts predict the best and worst changes in digital life by 2035, how black americans view the use of face recognition technology by police, most popular.
About Pew Research Center Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Home — Essay Samples — Information Science and Technology — Internet — The Importance of Internet Privacy
The Importance of Internet Privacy
- Categories: Internet Internet Privacy
About this sample

Words: 1017 |
Published: Oct 2, 2020
Words: 1017 | Pages: 2 | 6 min read
Table of contents
Introduction, threats to personal data and privacy, legal and ethical considerations, protecting your digital sanctuary, works cited.
- Strong Passwords: Employ strong, unique passwords for online accounts and consider using a password manager to securely store and manage them.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an additional layer of security to your online accounts.
- Mindful Sharing: Be cautious about the personal information you share online, especially on social media platforms. Review and adjust privacy settings to control who can access your data.
- Virtual Private Networks (VPNs): Utilize VPNs to encrypt your internet connection, making it more difficult for third parties to monitor your online activities.
- Regular Software Updates: Keep your operating system, browser, and security software up to date to protect against vulnerabilities that could be exploited by cybercriminals.
- Stay Informed: Stay informed about the latest threats and best practices for online privacy. Knowledge is a powerful defense against potential threats.
- Brown, M. (2018). Facebook is watching and tracking you more than you probably realize. Business Insider. https://www.businessinsider.com/facebook-is-tracking-you-through-apps-and-websites-2018-4
- Debatin, B., Lovejoy, J.P., Horn, A-K., & Hughes, B.N. (2009). Facebook and online privacy: Attitudes, behaviors, and unintended consequences. Journal of Computer-Mediated Communication, 15(1), 83-108.
- National Conference of State Legislatures. (2019). Security breach notification laws. https://www.ncsl.org/research/telecommunications-and-information-technology/security-breach-notification-laws.aspx
- Online Privacy (2018). Peggy J. Parks. Greenhaven Publishing LLC.
- Pew Research Center. (2021). Internet/Broadband Fact Sheet.
- Rosenbach, M., & Stolte, J. (2018). Can you have both security and privacy in the internet age? Harvard Business Review.
- Soltani, A. (2010). Why privacy matters: Debunking the nothing-to-hide argument. The Chronicle of Higher Education, 57(3), B26.
- Statista. (2022). Number of internet users worldwide from 2005 to 2021 (in millions). https://www.statista.com/statistics/273018/number-of-internet-users-worldwide/
- Winston & Strawn. (2017). Internet Privacy: An Overview of Federal Law. Lexology.
- Zavodny, M. (2017). Why does online privacy matter? Mercatus Center at George Mason University.

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Information Science and Technology Law, Crime & Punishment

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
5 pages / 2391 words
2 pages / 812 words
3 pages / 1579 words
2 pages / 985 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Internet
Valkenburg, P. M., & Peter, J. (2007). Online communication and adolescent well-being: Testing the stimulation versus the displacement hypothesis. Journal of Computer-Mediated Communication, 12(4), 1169-1182.
The excessive use of the internet has become a prevalent concern in today's digital age. The internet, once a revolutionary tool for communication and information, has now transformed into an integral part of our daily lives. [...]
Alton, L. (2017, May 15). Is Working From Home Making You Feel Miserable?. NBC news. Retrieved from https://www.inc.com/amy-morin/heres-why-internet-has-made-us-lonelier-than-ever.html
Hawkley, L., Cacioppo, J. (2010). Loneliness is a bodily function like hunger. AoBM.Anderson, W. A. (n.d.). The Impact of ICT on Loneliness in Elder Individuals. University of Alabama.Sharifpoor, E., Mohammadzadeh, M. J., & [...]
The internet is accessible to almost everyone from around the world. It can do many things, like helping people with things like fixing or building an item. The internet has many effects on people, but these effects are mostly [...]
Do you ever lose focus while reading? Find yourself constantly on your phone scrolling through emails, articles, and social feeds?The Shallows: What The Internet Is Doing To Our Brains by Nicholas Carr deeply examines the [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Skip to main content
- Keyboard shortcuts for audio player

- LISTEN & FOLLOW
- Apple Podcasts
- Google Podcasts
- Amazon Music
Your support helps make our show possible and unlocks access to our sponsor-free feed.
Your Technology Is Tracking You. Take These Steps For Better Online Privacy

Laurel Wamsley

Before I became a reporter at NPR, I worked for a few years at tech companies.
One of the companies was in the marketing technology business — the industry that's devoted in part to tracking people and merging their information, so they can be advertised to more effectively.
That tracking happens in multiple senses: physical tracking, because we carry our phones everywhere we go. And virtual tracking, of all the places we go online.
The more I understood how my information was being collected, shared and sold, the more I wanted to protect my privacy. But it's still hard to know which of my efforts is actually effective and which is a waste of time.
So I reached out to experts in digital security and privacy to find out what they do to protect their stuff – and what they recommend most to us regular folks.
Here's what they told me.

How Are Apple, Amazon, Facebook, Google Monopolies? House Report Counts The Ways
1. to protect your accounts, practice good security hygiene..
There are some steps that make sense for almost all of us, says Eva Galperin , director of cybersecurity at the Electronic Frontier Foundation. Those include using strong passwords, two-factor authentication, and downloading the latest security updates.
She and other experts make a distinction between privacy and security when it comes to your data. Security generally refers to protecting against someone trying to access your stuff — such as stealing your credit card number or hacking your accounts. Privacy is more often used to talk about keeping your movements from being tracked for purposes of advertising or surveillance.
It turns out that the steps to protect your security are more clear-cut than those for privacy — but we'll come back to that.

TED Radio Hour
Edward snowden: why does online privacy matter.
Use strong passwords or passphrases for your accounts. Longer than a password, passphrases should be strong and unique for each site. Don't use 1234. Bring some randomness and special characters into it. And don't use the same password for different websites: You don't want all your accounts to be compromised just because one gets hacked.
Use a password manager to keep track of your passwords, Galperin says — then all you have to do is remember the passphrase for your password manager.
Turn on two-factor authentication for your important accounts. You've seen this: Usually you're asked to put in your mobile number so that you can receive a text with an additional number you input before you can log in.
That's the most common type of two-factor authentication — but it's not the strongest, Galperin says, because SMS messages can be intercepted by your Internet provider, law enforcement or the government.
If you want to go a step further, Galperin recommends using an application that sends the second factor to an app on your phone, such as Authy or Google Authenticator , as these are harder to intercept. (Full disclosure here: NPR receives funding from Google and Facebook.) You can also use a physical key you carry with you that plugs into your computer's USB port and serves as the second factor.

6 Tips For Making A Career Change, From Someone Who Has Done It
Download the latest security updates.
Those nudges you get from your computer or phone to install the latest security update? You should download those.
"Most applications, when they're compromised, are not compromised by scary zero-day bugs that nobody knows about," Galperin says. "They are compromised by problems that everybody knows exist that have been publicly reported, and that the company has fixed and they have issued a patch in their security update. But if you do not take the security update, you do not get the benefit of the work of the security engineers at that company."

How To Sign Up To Work The Polls On Election Day
2. beware of phishing..
Not all attacks on our security come through malware or hackers invisibly breaking into your account. It's common that we're tricked into handing over our passwords or personal information to bad actors.
These attempts can happen via email, text message or a phone call. And generally they're trying to get your username and password, or perhaps your Social Security number. But there are often signs that these messages aren't legit – spelling or grammar errors, links to websites other than the one it should be linking to, or the email is coming from a weird domain.
If it feels fishy, it might be phishing.

Twitter Expands Warning Labels To Slow Spread of Election Misinformation
3. protect what matters most..
Depending on your situation, you might want to take additional precautions to safeguard your privacy and security.
To figure out what steps people should take to safeguard their stuff, Galperin suggests you make a security plan. The Electronic Frontier Foundation has a guide to doing this, which starts by asking yourself these questions:
- What do I want to protect?
- Whom do I want to protect it from?
- How bad are the consequences if I don't?
- How likely is it to need protecting?
- And how much trouble am I willing to go through to try to protect it?
Resources For Securing Your Data
The Surveillance Self-Defense site from the Electronic Frontier Foundation is a good place to start. Here's its guide to making your own security plan and figuring out what you most want to protect.
From Tactical Tech, here are handy how-to kits for different scenarios, including securing your data , increasing your online privacy and making your phone less addictive .
You can use the answers to those questions to focus your efforts on securing the things that matter most to you.
4. Delete some apps from your phone. Use a browser instead.
Matt Mitchell is a tech fellow at the Ford Foundation, and the founder of CryptoHarlem , an organization that teaches people to protect their privacy, including from surveillance.
Apps can learn a lot about you due to all the different types of data they can access via your phone. Seemingly harmless apps – like say, a flashlight app — could be selling the data they gather from you.
That's why Mitchell recommends "Marie Kondo-ing" your apps: Take a look at your smartphone and delete all the apps you don't really need. For many tasks, you can use a browser on your phone instead of an app.
Privacy-wise, browsers are preferable, because they can't access as much of your information as an app can.
I mentioned to Mitchell that even though I use Facebook and Twitter, I don't have those apps on my phone — partly so that I'll use them less, and partly for privacy reasons. I wanted to know — did I accomplish anything by not having those apps on my phone?
"You've accomplished a lot," he says. He compares it to oil companies turning crude into petrol: Your data can be turned into profit for these companies. "Every time you don't use an app, you're giving them less data, which is less money."
Mitchell says that's true even if you've been on Facebook a long time, and it feels like the company already knows everything about you. He compares it to smoking: It's never too late to cut back or quit — you'll still benefit by giving it less data to harvest.
5. To protect your chats, use an encrypted app for messaging.
If you want the contents of your messages to be secure, it's best to use an app that has end-to-end encryption, such as Signal or WhatsApp. That means you and the recipient can read the message you send — but no one in the middle.
But even though the contents of your messages are protected by encryption in apps such as Signal and WhatsApp, your metadata isn't — and someone could learn a lot about you from your metadata, Galperin warns. She compares it to what you can learn just by looking at the outside of an envelope in the mail: who sent it to whom, when and where it was sent from.
And WhatsApp is owned by Facebook — so when you share your contacts with WhatsApp, Facebook is getting that info, though it can't read the contents of your messages.
If you're on an iPhone, iMessages are encrypted when you're messaging another iOS device — but not when you're messaging an Android phone. Signal offers encrypted messaging on both Android and iPhone.
What about Facebook Messenger? Jen King , director of privacy at Stanford Law School's Center for Internet and Society, advises against using the Messenger app.
The app "has access to far more info on your phone than using Facebook through a browser," she says, recommending something such as WhatsApp or regular SMS texting instead.
And if encryption matters to you, be careful about backing up your chats to the cloud. If you back up your WhatsApp messages to iCloud or Google Drive , for example, they're no longer encrypted.
"That backup is just a database. And that database is easy for someone to open and read," Mitchell says, if they were able to access your cloud account. To keep your messages from prying eyes, turn off cloud backups and delete existing WhatsApp backups from iCloud or Google Drive.

California Rings In The New Year With A New Data Privacy Law
6. turn off ad personalization..
Whenever possible, Mitchell recommends going into your settings and turning off ad personalization, which often gives companies permission to do invasive tracking.
Opting Out Of Ad Personalization On Some Major Platforms
Google and Android
Here's a link to limit ad personalization on Google and Android.
This page shows you how to opt out of ad personalization on Apple. As of this writing, it hasn't been updated for iOS 14. If you have updated to iOS 14, go to Settings > Privacy > Apple Advertising > turn off Personalized Ads.
- On this page , you can go to the ad settings tab and toggle the settings to not allowed.
- This page has steps to disconnect your activity off Facebook that is shared with Facebook, and clear that history.
- On the Off-Facebook activity page , under What You Can Do, you can click on More Options > Manage Future Activity > and toggle it to off. ( This page has those steps.)
This page explains how to opt out of ad personalization.
He also recommends going to myactivity.google.com and deleting everything you can. On the left, there's a tab that says "Delete activity by." Select "All time." On your My Google Activity page, you can turn off Web & App Activity, Location History and YouTube History.
"It will show you every search term and everything you've ever done, every YouTube video you've ever looked at, all that stuff," he says. "It'll say, are you sure you want to delete this? 'Cause if you delete this, it might affect some stuff." Mitchell says: Delete it.
7. It's difficult to protect your privacy online if there aren't laws to protect your privacy online.
Tighter privacy settings only get you so far without laws that protect your privacy, says Ashkan Soltani , the former chief technologist for the Federal Trade Commission and one of the architects of the 2018 California Consumer Privacy Act .
Activist Aims To Strengthen California's Consumer Privacy Act
There are laws around health information and credit and financial information, he explains, and some states have Internet privacy-related laws .
But nationally, the U.S. doesn't have a universal data privacy law safeguarding everyday online privacy.
Soltani says he rarely recommends steps such as using ad blockers or VPNs for most people. They require too much attention and persistence to deliver on privacy, and even then they are limited in their effectiveness.
"The incentives are so high on the other side," Soltani says, "to uniquely identify people and track them that [users] will never have enough motivation and incentive to do it to the degree of this multibillion dollar ad tech industry."
So how do you protect your privacy? Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy.
8. Start small and take it one step at a time.
Faced with this landscape, getting a tighter hold on your digital privacy and security can feel daunting. But Galperin has this sound advice: Just do a little bit at a time.
You don't need to make a list of all of your accounts to integrate into a password manager — you can just do each account as you log into it.
Even just doing the basics — strengthening your passwords, turning on two-factor authentication and watching out for scammers — can make your accounts a lot more secure. Then keep going: There are a lot of other steps you might want to take, depending on your needs.
We're going to be on the Internet for a long time. The more each of us understands how our data are collected and used — and how to keep private what we want to keep private — the better, safer and healthier our digital lives will be.
The podcast portion of this episode was produced by Audrey Nguyen. She also contributed research.
We'd love to hear from you. Leave us a voicemail at 202-216-9823, or email us at [email protected] .
For more Life Kit, subscribe to our newsletter .
- Life Kit: Life Skills
- Share full article
Advertisement
Supported by
The Battle for Digital Privacy Is Reshaping the Internet
As Apple and Google enact privacy changes, businesses are grappling with the fallout, Madison Avenue is fighting back and Facebook has cried foul.

By Brian X. Chen
Listen to This Article
Open this article in the New York Times Audio app on iOS.
SAN FRANCISCO — Apple introduced a pop-up window for iPhones in April that asks people for their permission to be tracked by different apps.
Google recently outlined plans to disable a tracking technology in its Chrome web browser.
And Facebook said last month that hundreds of its engineers were working on a new method of showing ads without relying on people’s personal data.
The developments may seem like technical tinkering, but they were connected to something bigger: an intensifying battle over the future of the internet. The struggle has entangled tech titans, upended Madison Avenue and disrupted small businesses. And it heralds a profound shift in how people’s personal information may be used online, with sweeping implications for the ways that businesses make money digitally.
At the center of the tussle is what has been the internet’s lifeblood: advertising .
More than 20 years ago, the internet drove an upheaval in the advertising industry. It eviscerated newspapers and magazines that had relied on selling classified and print ads, and threatened to dethrone television advertising as the prime way for marketers to reach large audiences.
Instead, brands splashed their ads across websites, with their promotions often tailored to people’s specific interests. Those digital ads powered the growth of Facebook, Google and Twitter, which offered their search and social networking services to people without charge. But in exchange, people were tracked from site to site by technologies such as “ cookies, ” and their personal data was used to target them with relevant marketing.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data collection. Apple, citing the mantra of privacy, has rolled out tools that block marketers from tracking people. Google, which depends on digital ads, is trying to have it both ways by reinventing the system so it can continue aiming ads at people without exploiting access to their personal data.

If personal information is no longer the currency that people give for online content and services, something else must take its place. Media publishers, app makers and e-commerce shops are now exploring different paths to surviving a privacy-conscious internet, in some cases overturning their business models. Many are choosing to make people pay for what they get online by levying subscription fees and other charges instead of using their personal data.
Jeff Green, the chief executive of the Trade Desk, an ad-technology company in Ventura, Calif., that works with major ad agencies, said the behind-the-scenes fight was fundamental to the nature of the web.
“The internet is answering a question that it’s been wrestling with for decades, which is: How is the internet going to pay for itself?” he said.
The fallout may hurt brands that relied on targeted ads to get people to buy their goods. It may also initially hurt tech giants like Facebook — but not for long. Instead, businesses that can no longer track people but still need to advertise are likely to spend more with the largest tech platforms, which still have the most data on consumers.
David Cohen, chief executive of the Interactive Advertising Bureau, a trade group, said the changes would continue to “drive money and attention to Google, Facebook, Twitter.”
The shifts are complicated by Google’s and Apple’s opposing views on how much ad tracking should be dialed back. Apple wants its customers, who pay a premium for its iPhones, to have the right to block tracking entirely. But Google executives have suggested that Apple has turned privacy into a privilege for those who can afford its products.
For many people, that means the internet may start looking different depending on the products they use. On Apple gadgets, ads may be only somewhat relevant to a person’s interests, compared with highly targeted promotions inside Google’s web. Website creators may eventually choose sides, so some sites that work well in Google’s browser might not even load in Apple’s browser, said Brendan Eich, a founder of Brave, the private web browser.
“It will be a tale of two internets,” he said.
Businesses that do not keep up with the changes risk getting run over. Increasingly, media publishers and even apps that show the weather are charging subscription fees, in the same way that Netflix levies a monthly fee for video streaming. Some e-commerce sites are considering raising product prices to keep their revenues up.
Consider Seven Sisters Scones, a mail-order pastry shop in Johns Creek, Ga., which relies on Facebook ads to promote its items. Nate Martin, who leads the bakery’s digital marketing, said that after Apple blocked some ad tracking, its digital marketing campaigns on Facebook became less effective. Because Facebook could no longer get as much data on which customers like baked goods, it was harder for the store to find interested buyers online.
“Everything came to a screeching halt,” Mr. Martin said. In June, the bakery’s revenue dropped to $16,000 from $40,000 in May.
Sales have since remained flat, he said. To offset the declines, Seven Sisters Scones has discussed increasing prices on sampler boxes to $36 from $29.
Apple declined to comment, but its executives have said advertisers will adapt. Google said it was working on an approach that would protect people’s data but also let advertisers continue targeting users with ads.
Since the 1990s, much of the web has been rooted in digital advertising. In that decade, a piece of code planted in web browsers — the “cookie” — began tracking people’s browsing activities from site to site. Marketers used the information to aim ads at individuals, so someone interested in makeup or bicycles saw ads about those topics and products.
After the iPhone and Android app stores were introduced in 2008, advertisers also collected data about what people did inside apps by planting invisible trackers. That information was linked with cookie data and shared with data brokers for even more specific ad targeting.
The result was a vast advertising ecosystem that underpinned free websites and online services. Sites and apps like BuzzFeed and TikTok flourished using this model. Even e-commerce sites rely partly on advertising to expand their businesses.
But distrust of these practices began building. In 2018, Facebook became embroiled in the Cambridge Analytica scandal, where people’s Facebook data was improperly harvested without their consent. That same year, European regulators enacted the General Data Protection Regulation , laws to safeguard people’s information. In 2019, Google and Facebook agreed to pay record fines to the Federal Trade Commission to settle allegations of privacy violations.
In Silicon Valley, Apple reconsidered its advertising approach. In 2017, Craig Federighi, Apple’s head of software engineering, announced that the Safari web browser would block cookies from following people from site to site.
“It kind of feels like you’re being tracked, and that’s because you are,” Mr. Federighi said. “No longer.”
Last year, Apple announced the pop-up window in iPhone apps that asks people if they want to be followed for marketing purposes. If the user says no, the app must stop monitoring and sharing data with third parties.
That prompted an outcry from Facebook , which was one of the apps affected. In December, the social network took out full-page newspaper ads declaring that it was “standing up to Apple” on behalf of small businesses that would get hurt once their ads could no longer find specific audiences.
“The situation is going to be challenging for them to navigate,” Mark Zuckerberg, Facebook’s chief executive, said.
Facebook is now developing ways to target people with ads using insights gathered on their devices, without allowing personal data to be shared with third parties. If people who click on ads for deodorant also buy sneakers, Facebook can share that pattern with advertisers so they can show sneaker ads to that group. That would be less intrusive than sharing personal information like email addresses with advertisers.
“We support giving people more control over how their data is used, but Apple’s far-reaching changes occurred without input from the industry and those who are most impacted,” a Facebook spokesman said.
Since Apple released the pop-up window, more than 80 percent of iPhone users have opted out of tracking worldwide, according to ad tech firms. Last month, Peter Farago, an executive at Flurry, a mobile analytics firm owned by Verizon Media, published a post on LinkedIn calling the “time of death” for ad tracking on iPhones.
At Google, Sundar Pichai, the chief executive, and his lieutenants began discussing in 2019 how to provide more privacy without killing the company’s $135 billion online ad business. In studies, Google researchers found that the cookie eroded people’s trust. Google said its Chrome and ad teams concluded that the Chrome web browser should stop supporting cookies.
But Google also said it would not disable cookies until it had a different way for marketers to keep serving people targeted ads. In March, the company tried a method that uses its data troves to place people into groups based on their interests, so marketers can aim ads at those cohorts rather than at individuals. The approach is known as Federated Learning of Cohorts, or FLOC.
Plans remain in flux. Google will not block trackers in Chrome until 2023 .
Even so, advertisers said they were alarmed.
In an article this year, Sheri Bachstein, the head of IBM Watson Advertising, warned that the privacy shifts meant that relying solely on advertising for revenue was at risk. Businesses must adapt, she said, including by charging subscription fees and using artificial intelligence to help serve ads.
“The big tech companies have put a clock on us,” she said in an interview.
Kate Conger contributed reporting.
Brian X. Chen is the lead consumer technology writer for The Times. He reviews products and writes Tech Fix , a column about the social implications of the tech we use. Before joining The Times in 2011, he reported on Apple and the wireless industry for Wired. More about Brian X. Chen
A Guide to Digital Safety
A few simple changes can go a long way toward protecting yourself and your information online..
A data breach into your health information can leave you feeling helpless. But there are steps you can take to limit the potential harm.
Don’t know where to start? These easy-to-follow tips and best practices will keep you safe with minimal effort.
Your email address has become a digital bread crumb that companies can use to link your activity across sites. Here’s how you can limit this .
Protect your most sensitive accounts by creating unique passwords and adding extra layers of verification .
There are stronger methods of two-factor authentication than text messages. Here are the pros and cons of each .
Do you store photos, videos and important documents in the cloud? Make sure you keep a copy of what you hold most dear .
Browser extensions are free add-ons that you can use to slow down or stop data collection. Here are a few to try.
- Advanced Search
- All Categories
- Metaphysics and Epistemology
- Epistemology
- Metaphilosophy
- Metaphysics
- Philosophy of Action
- Philosophy of Language
- Philosophy of Mind
- Philosophy of Religion
- Value Theory
- Applied Ethics
- Meta-Ethics
- Normative Ethics
- Philosophy of Gender, Race, and Sexuality
- Philosophy of Law
- Social and Political Philosophy
- Value Theory, Miscellaneous
- Science, Logic, and Mathematics
- Logic and Philosophy of Logic
- Philosophy of Biology
- Philosophy of Cognitive Science
- Philosophy of Computing and Information
- Philosophy of Mathematics
- Philosophy of Physical Science
- Philosophy of Social Science
- Philosophy of Probability
- General Philosophy of Science
- Philosophy of Science, Misc
- History of Western Philosophy
- Ancient Greek and Roman Philosophy
- Medieval and Renaissance Philosophy
- 17th/18th Century Philosophy
- 19th Century Philosophy
- 20th Century Philosophy
- History of Western Philosophy, Misc
- Philosophical Traditions
- African/Africana Philosophy
- Asian Philosophy
- Continental Philosophy
- European Philosophy
- Philosophy of the Americas
- Philosophical Traditions, Miscellaneous
- Philosophy, Misc
- Philosophy, Introductions and Anthologies
- Philosophy, General Works
- Teaching Philosophy
- Philosophy, Miscellaneous
- Other Academic Areas
- Natural Sciences
- Social Sciences
- Cognitive Sciences
- Formal Sciences
- Arts and Humanities
- Professional Areas
- Other Academic Areas, Misc
- About PhilArchive
- Frequently Asked Questions
- OAI Handler
- Journal policies
- Code of conduct
- Create an account
Philosophical theories of privacy: Implications for an adequate online privacy policy
Archival history, reprint years.

Online Privacy: Definition and Significance Essay
Do you often, spending almost all your free time online, chatting with friends or watching a movie, worry about the safety of your leisure time? Technology is continually developing and is being incorporated into almost all aspects of people’s daily operations. It is widely used in communication, the medical field, industrial production, and scientific research. Technology has simplified the way things are; operations are now faster, more reliable, and more efficient. Information and communication technology is one of the commonly used forms of technology that has seen the number of users rising up, leading to immense growth in this sector. This has enabled people to communicate and share information with ease and at a cheaper cost. However, the growth has come with a lot of concerns about online privacy. This concern has left many people wondering what online privacy is all about, how it affects this sector and its significance. Online privacy is a debatable topic in civilized societies, as companies that provide websites and applications can secretly trade user information for their benefit; it makes people look for ways to protect their data.
Online privacy is based on personal information that should not be allowed to settle in the hands of third parties. This information is critical, and the internet user or the person in charge of keeping such information in an organization should always ensure no one gets access. When users are asked to provide personal information while using the internet, they should ensure they log out, delete or encrypt the information. This will make it impossible for a third party to access and retrieve this sensitive data (Black et al.). The internet users should also turn off ad personalization which companies may be using to track their online activities and profile them for tailored ads. On the hand, companies handling data should ensure during collection, sharing, and storage, no third party has access to this personal information by enhancing security. Therefore, online privacy can be defined as the seclusion of internet users’ personal information from access and usage by an unauthorized third party.
Targeting and advertising cookies are meant to monitor your internet usage and collect information about browsing data used to display advertisements tailored to the user. The information gathered has internet users browsing history, which advertising companies can use to determine your favorite browsing sites and send their ads there. These companies can also collect users’ personal information and build a profile that they can use to determine which ads can be sent to particular users (Black et al.). Some cookies can also be used to gather information on the movements and location of the user and use the data to send related to the location. The biggest concern about these advertising companies is the criteria used to design these tailored ads. Collecting users’ data without prior consent is an infringement of that person’s right to online privacy. Therefore, online privacy can be defined as the entitlement of an internet user to be free from unwarranted solicitation of personal information while using or connected to the internet.
The dictionary definition of online privacy is insufficient to bring out the intended meaning; its definition is brief with technical terms. In this case, the definition has been achieved by a broader description of what online privacy is and a case scenario that aids in understanding it deeper. These cases will simplify the understanding of online privacy and advocate for it to be embraced. These People do not take the issue of online privacy with the intensity it deserves, and that is why a case study had to be attached to reflect on the reality. This has led to uncalled-for suffering for the victims whose personal information has been used for selfish personal interests. A common example is impersonation, where someone uses the personal information of another person to commit fraud or crime. Such cases are contributed by personal negligence in keeping personal information away from the public. When people take the privacy of personal information seriously, no one will be subjected to suffering; as a result, crimes are conducted through impersonation.
In conclusion, this paper has brought a clearer meaning of what online privacy means and its significance. It guides what to do with the personal information that has been shared over the internet to ensure that no third party should have access. The steps to secure the privacy of such information include logging out, deleting, or even encrypting such data. Internet users are advised to turn off ad personalization on their devices to prevent advertising companies from tracking their devices’ internet usage and acquiring information to build the ads’ profile. Companies handling personal information should have a strong security system to guarantee information safety. Companies use targeting and advertising cookies to keep track of users’ internet usage and location. The information gathered by these cookies is used to determine which types of ads suit the internet user. It can be used to build a personal profile on activities and preferences. The dictionary definition of online privacy is inadequate, and it does not bring full meaning. However, better meanings have been derived by incorporating a case study to aid the understanding.
Black, Carolyn, et al. “Online Data Privacy from Attitudes to Action: an Evidence Review.” The Carnegie UK Trust , 2018.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2023, March 24). Online Privacy: Definition and Significance. https://ivypanda.com/essays/online-privacy-definition-and-significance/
"Online Privacy: Definition and Significance." IvyPanda , 24 Mar. 2023, ivypanda.com/essays/online-privacy-definition-and-significance/.
IvyPanda . (2023) 'Online Privacy: Definition and Significance'. 24 March.
IvyPanda . 2023. "Online Privacy: Definition and Significance." March 24, 2023. https://ivypanda.com/essays/online-privacy-definition-and-significance/.
1. IvyPanda . "Online Privacy: Definition and Significance." March 24, 2023. https://ivypanda.com/essays/online-privacy-definition-and-significance/.
Bibliography
IvyPanda . "Online Privacy: Definition and Significance." March 24, 2023. https://ivypanda.com/essays/online-privacy-definition-and-significance/.
- Computer Cookies: What Are They and How Do They Work
- The Concept of Internet Etiquette (Netiquette)
- Home Style Cookies Production Management
- Impersonation in Emily Dickinson’s Poem
- Monkey Cookies Company's Promotion in Media
- Healthcare Research: Personalization
- Fashionable Women in Alfred Hitchcock's Films
- Personalization and Learning Analytics Relationship
- Hunting Netiquette Violations
- Home-Style Cookies and Waste-Free Production
- Surveillance and Data: Tech & Engineering
- The Binary Search Tree (BST): Definition, Description, and Use
- Blockchain Technology and Potential Issues
- Database Security for the Schumer Company
- Effectiveness of Data Protection-Related Policies for Businesses

Essay on Internet Privacy
Students are often asked to write an essay on Internet Privacy in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Privacy
Understanding internet privacy.
Internet privacy is about protecting your personal data online. It’s important because when you use the internet, you share information that others could misuse.
Why is Internet Privacy Important?
Internet privacy is crucial to protect your identity and personal information. Without it, strangers could access your data, leading to potential harm.
How to Maintain Internet Privacy?
You can maintain internet privacy by using strong passwords, enabling privacy settings on social media, and avoiding sharing sensitive information online. Always remember, your online safety is in your hands.
250 Words Essay on Internet Privacy
Introduction to internet privacy.
Internet privacy, often synonymous with online privacy, is a subset of data privacy focusing on the protection of personal information in the digital realm. As the internet becomes increasingly integral to our daily lives, privacy issues have surged to the forefront of societal discourse.
The Importance of Internet Privacy
Internet privacy is crucial for numerous reasons. It safeguards personal data, prevents identity theft, and preserves freedom of speech. In the era of digitalization, a breach in privacy can lead to damaging consequences, ranging from financial loss to emotional distress.
Threats to Internet Privacy
Threats to internet privacy are manifold. They include cybercriminal activities, surveillance by government agencies, data mining by corporations, and even seemingly innocuous social media platforms that collect and utilize user data.
Internet Privacy: A Human Right?
Many argue that internet privacy is a fundamental human right. This perspective highlights the need for stringent laws and policies to protect individuals from intrusive surveillance and unauthorized data collection.
The Role of Individuals in Protecting Privacy
While legislation plays a vital role, individuals must also take proactive steps to safeguard their online privacy. This can include using encrypted communication, regularly updating software, and being mindful of the information shared online.
Internet privacy is a complex and critical issue in the digital age. The collective efforts of individuals, corporations, and governments are necessary to ensure the protection of personal information in the online sphere. As we continue to navigate this interconnected world, the importance of internet privacy will only increase.
500 Words Essay on Internet Privacy
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is crucial for numerous reasons. Primarily, it protects individuals’ identity and personal information from potential cybercriminals. With the rise of the digital economy, people are increasingly sharing their sensitive data online, making them vulnerable to identity theft, cyberstalking, and other forms of cybercrime. Internet privacy also ensures the freedom of speech and thought online, as it allows individuals to express their views without fear of being tracked or monitored.
Despite its importance, internet privacy is under constant threat. Cybercriminals often exploit security breaches to steal sensitive data. Also, many online platforms and services thrive on data collection, often without clear consent from users. Governments, too, may infringe upon internet privacy for surveillance and security purposes.
The Role of Legislation in Internet Privacy
Legislation plays a crucial role in protecting internet privacy. Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of attempts to regulate data collection and usage. However, enforcing these laws across borders is challenging, and loopholes often exist that allow for continued privacy infringements.
Individual Responsibility and Internet Privacy
While legislation is important, individual responsibility is equally critical in ensuring internet privacy. Users should be aware of the data they share online and the potential risks involved. They should also use privacy-enhancing tools, such as Virtual Private Networks (VPNs), secure browsers, and encryption, to protect their data.
Conclusion: The Future of Internet Privacy
The future of internet privacy is uncertain. On one hand, advancements in technology, such as blockchain and quantum computing, could potentially enhance data security. On the other hand, the increasing digitization of our lives threatens to erode privacy further. The challenge lies in finding a balance between the benefits of the digital age and the preservation of privacy. As we move forward, the discourse on internet privacy will remain a pivotal aspect of our digital lives.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Uses and Abuses of Internet
- Essay on These Days Exposure to Television and Internet
- Essay on Internet Influence on Kids
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
How-To Geek
Online privacy is a myth: what you can and can't do about it.
It never really existed in the first place.
Quick Links
Yes, a myth, breaking the privacy illusion, what can you even do, what's the point threat modeling 101.
We all want to recover (and maintain) our online privacy. There are lots of features and industries built around fighting for privacy, from private-browsing modes and tracker blockers to private VPNs. But online privacy is a myth---and offline privacy might be one, too.
Myths are stories (or narratives) that are often foundational to a society's beliefs. The myth of online privacy is like that: Privacy feels foundational in our society. To the extent we accept we don't have privacy online, it feels like something we've lost---something that we can perhaps recover with the right software tweaks, behaviors, or perhaps regulations.
When you think about it, the myth of online privacy is even beneficial to those industries that benefit from the lack of it. We all might agree that there's no privacy online, but leave us to a search engine, and we'll search an endless list of everything that comes into our minds, including potentially sensitive topics like medical questions. Police even dig through those search histories to look for criminals .
We may all agree that online privacy isn't something we have. But do you realize how little privacy you actually have?
First of all, when you go online, your internet service provider---whether that's a home internet connection or a cellular data connection---can see all the websites you're accessing. In the USA, they can even sell your browsing data . Your mobile carrier may even be tracking and selling your app usage activity .
When you visit a website, it can see your IP address and use that to track you across visits. But it likely loads a lot of tracking scripts, too. Those tracker networks can track your activity across multiple websites. That's one reason you see shopping ads chase you across the web after you look up a particular product. Even if you're clearing cookies , there are a lot of ways to fingerprint your web browser .
"The cloud" is just someone else's computer. If you upload your files to the cloud without using end-to-end encryption ---something most services don't offer---your files can be viewed and accessed by the company that owns the cloud service. The same goes for messages and emails , which generally aren't encrypted either.
Okay, you might know all that---but did you know that advertisers can tie your in-store purchases and visits back to ads you see? For example, Google has a product that does this , and one of the data sources it uses is the nebulous "transaction data uploaded by the advertiser or aggregated and anonymized data from third parties." Your credit card usage is being used to track you , too.
Did you know that Facebook's advertising tools are so granular that you can target ads so narrowly that you can show them to only one individual ?
Government surveillance is a given: Edward Snowden famously drew attention to massive warrantless government surveillance of internet and phone data. The NSA's XKeyScore software reportedly allows real-time search and access to the massive amount of data being logged about online activity.
The online world isn't something completely separate from the real, physical world, of course. The USA is full of automatic license plate readers , and many of them are now linked together in a big network . Even if you get off the computer and go for a drive, your movements are being tracked and logged. Amazon may be handing videos from your Ring doorbell camera over to the authorities without your explicit consent. Your cell phone location data is being used to track you , too.
An article like this one could go on and on with examples. Do a little digging, and you can find many more examples. The amount of data being collected, crunched, and analyzed about us at all times is tough to conceptualize.
There are no perfect fixes. Private browsing will stop your browser from remembering your history and give you a fresh set of temporary cookies , but your IP address is still out there. You can avoid using Facebook, but Facebook has a shadow profile on you anyway. You can use a VPN , but you're going to sign into something eventually---which will tie your identity to your browsing in the VPN---and you're placing your trust in a VPN that hopefully doesn't keep logs .
So what can you do? Well, you can still make a dent in it. If you're currently broadcasting your life as a 24/7 live stream, turning off the camera means less data is out there.
You can use a VPN along with private browsing mode to disguise your browsing---but don't just rely on a VPN alone, and understand that you're trusting the VPN. You could use Tor ---though there have been vulnerabilities in Tor, too. You can use more private, encrypted services---for example, chatting on Signal instead of plain-old SMS messages . You can keep your sensitive files more private, storing them locally or securely encrypting them before uploading them to online storage.
And yes, you can go further: Using cash, for example, and putting together facial accessories that will stop facial recognition cameras .
But as you're sitting there using Tor on a computer running Tails trying to figure out how to go off the grid without actually going off the grid, you might want to ask yourself: What's the point?
No, we don't mean give up---we mean consider what you're actually defending against.
- You might not care if Facebook realizes you're interested in seeing the latest movie. But you might want to fire up that VPN and private browsing mode when you're searching for information about a medical issue.
- You might be fine with storing photos of your vacation unencrypted in the cloud, but you might want to keep sensitive financial documents more secure.
- You might be fine chatting with your plumber over SMS, but you might want to have a private conversation with your spouse on Signal .
Related: What Is Signal, and Why Is Everyone Using It?
It's all about your threat model---what are you actually trying to defend against? Once you know what you care about keeping private, you can take steps to keep that individual sensitive thing private rather than be overwhelmed with all the data collection going on all the time.
Unfortunately, that's not a recipe for "online privacy." There's no easy way to flip a privacy switch and regain a mythical state of privacy. But there are things you can do to better shield specific things and keep them more private.

This website aims to help you…
Discover the latest global research about what social media may or may not reveal about its users.
Discuss what the available research about social media and privacy could mean for you and the society you live in.
Decide if you want to adapt your online behaviour and what society in general should do about online privacy issues.
OPF Research
Psychographic Targeting
Psychology and the EU Referendum
Predicting Susceptibility to Social Bots on Twitter
Predicting personality through Twitter
Determining psychological traits from Facebook use and related privacy concerns diflucan over the counter cipro over the counter zovirax generic
Brexiters and Bremainers also divided on rights to online privacy
Irrational thinking and the EU Referendum result
Are you what you Tweet?
The media on issues OPF raise
Just how accurate is Facebook personality prediction?
The economics of online privacy?
Social media and psychology research bibliography
All OPF papers and statistical results
OPF reference material and methodological notes
This is a unique website which will require a more modern browser to work! Please upgrade today!
- EssayBasics.com
- Pay For Essay
- Write My Essay
- Homework Writing Help
- Essay Editing Service
- Thesis Writing Help
- Write My College Essay
- Do My Essay
- Term Paper Writing Service
- Coursework Writing Service
- Write My Research Paper
- Assignment Writing Help
- Essay Writing Help
- Call Now! (USA) Login Order now
- EssayBasics.com Call Now! (USA) Order now
- Writing Guides
The Internet Privacy (Essay/Paper Sample)
Table of Contents
The Internet Privacy
Internet privacy entails securing personal data that is published on the internet. This kind of privacy encompasses safeguarding of sensitive and private information, data, preferences, and communications. In the current cyberspace, different people have raised complaints regarding loss of personal information whenever they do online transactions, visit social media sites, and participate in online games as well as attending forums. In such circumstances, many people exhibit incidences of compromised passwords, the revelation of victims’ identities, and fraud. Such privacy issues come as a result of negligence by the users or website developers who do not comply with the regulations and standards that curb privacy violation. Thus, internet privacy is under threat due to the inability of the internet service providers who have no explicit permission to gain access or share confidential information. This essay presents a discussion of internet privacy and how online users fall victims due to increased vulnerability of online security.
Internet privacy is a paradoxical and difficult to understand. People are aware of their behaviors online and are bound to use strong passwords when before accessing their own accounts. In the same note, users are supposed to log out their own accounts when ceasing access to the internet so that they leave it safe and secure from intruders. However, regardless of such knowledge and clear understanding of the privacy policy, they do not bother. Instead, they lament of the increased vulnerability due to such negligence. On a separate note, people tend to care about protecting their personal information and normally feel insecure when issuing it on the internet. Therefore, this behavior brings about privacy paradox since they are unable to gain control of their own digital information.
Internet privacy faces numerous risks that include phishing that encompasses hacking activities that are used to obtain secured information, usernames, passwords, security PIN, credit card numbers and bank account numbers. Furthermore, users have been under attack through pharming which covers redirection of legitimate website users to a new and different IP address. Others include the use of offline applications that get information without user’s consent. In such circumstances, a computer that is online can be accessed to get the previously acquired data that is sent to the spyware source. On a separate note, there is a rise in the usage of malware which allows an illegal damage of computers both online and offline through application viruses, Trojan, and spyware.
Need an essay customized under your requirements? We can help you

In addition to the above measures, users should always keep their operating systems and windows up to date to avoid vulnerability. A rise in software vulnerability is enhanced through the use of outdated systems. This increases loopholes for cyber criminals. For example, Flash and Java are normally vulnerable to security threats hence expose their users to cyber attacks. On the same note, users should avoid accessing free Wi-Fi networks since such networks are used by hackers with network sniffers that retrieve crucial information. Lastly, users should always update and change their privacy settings on regular basis.
In conclusion, the essay has elaborated on internet privacy based on the different risks and vulnerability that users are facing besides highlighting the different measures that should be put in place. However, reduction of vulnerability of internet privacy begins with the user’s behavior regarding internet usage. Users should incorporate all the measures and should be careful when revealing their personal information online. Lastly, users should be aware of their privacy rights and should fight for such rights especially in cases when breaches occur.


IMAGES
VIDEO
COMMENTS
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
Anonymity on the Internet is possible, but it isn't guaranteed. To do it right, a person needs to know what pieces of information are used to track a user. Cookies, IP addresses, and media access control (MAC) addresses are some of the bits of information to mask, because they can point back to a real person.
Online privacy definition. Online privacy, also known as internet privacy or digital privacy, refers to how much of your personal, financial, and browsing data remains private when you're online. It has become a growing worry, with browsing history and personal data at increased risk.
The ethical challenges surrounding online privacy arise from the potential misuse of this data by companies or malicious actors. As such, it is essential to establish robust ethical guidelines for data protection to safeguard individuals' privacy. One of the key ethical challenges in online privacy is the collection and use of personal data ...
Conclusion. In summary, this essay has consisted of a discussion of issues regarding online privacy in the modern United States. Subjects addressed have included the NSA and Snowden, the case of Facebook, and the interplay within the ethical values of privacy and transparency. Ultimately, these issues are related to political questions ...
The analyses found that the extent of third-party data sharing by websites increased with internet use as the pandemic progressed and users relied more on online alternatives. Websites with more ...
1. Views of data privacy risks, personal data and digital privacy laws. Online privacy is complex, encompassing debates over law enforcement's data access, government regulation and what information companies can collect. This chapter examines Americans' perspectives on these issues and highlights how views vary across different groups ...
While the internet has revolutionized the way we communicate, work, and access information, it has also brought about critical concerns regarding privacy and security. This essay explores the paramount importance of internet privacy, shedding light on the threats to personal data, the legal and ethical considerations, and the measures ...
Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy. 8. Start small and take it one step at a time. Faced with this landscape, getting a ...
While a recent survey on Internet privacy indicates that 25 percent of Americans consider themselves victimized by invasion of their Internet privacy (Son & Kim, 2008), another study has concluded that the personal information of 33.6 million Americans has been schemed from online sources and used for malicious and fraudulent agendas since the ...
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
Internet privacy is the security of a user's personal data that is stored or published on the internet. The internet is an important part of every individual's daily life. In today's society, the internet is used by many different people for many reasons. It can be used for research, communication, and purchasing items.
This essay critically examines some classic philosophical and legal theories of privacy, organized into four categories: the nonintrusion, seclusion, limitation, and control theories of privacy. Although each theory includes one or more important insights regarding the concept of privacy, I argue that each falls short of providing an adequate ...
Online privacy is based on personal information that should not be allowed to settle in the hands of third parties. This information is critical, and the internet user or the person in charge of keeping such information in an organization should always ensure no one gets access. When users are asked to provide personal information while using ...
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
View our collection of internet privacy essays. Find inspiration for topics, titles, outlines, & craft impactful internet privacy papers. Read our internet privacy papers today!
We all want to recover (and maintain) our online privacy. There are lots of features and industries built around fighting for privacy, from private-browsing modes and tracker blockers to private VPNs. But online privacy is a myth---and offline privacy might be one, too. Yes, a Myth
It's convenience over security. If you're one of those people who doesn't think much about online privacy or computer security, then perhaps you should take a listen to what Jameson Lopp has ...
After learning about the information that has come to light, students need the opportunity to explore their own thoughts and feelings on this important issue. These 50 new journal prompts offer students the chance to think about their own right to privacy, the government's motives for surveillance, and the ramifications of wide-scale public ...
Discover the latest global research about what social media may or may not reveal about its users. Discuss. Discuss what the available research about social media and privacy could mean for you and the society you live in. Decide. Decide if you want to adapt your online behaviour and what society in general should do about online privacy issues.
Hire writer. 14). The use of unique passwords is therefore the first step in online privacy protection. The second step involves ignoring suspicious emails and links. Phishing is a general threat to people's online privacy. Phishing is mostly done through rogue links sent in emails and messages.
This essay presents a discussion of internet privacy and how online users fall victims due to increased vulnerability of online security. Internet privacy is a paradoxical and difficult to understand. People are aware of their behaviors online and are bound to use strong passwords when before accessing their own accounts.
Online privacy is a huge issue for most people but especially for teenagers. Teenagers are more at risk than older adults, because teenagers are more gullible and easier to trick online. The internet is a huge part of the lives of most teenagers but it may not be the safest place for them.