- Skip to main content
- Keyboard shortcuts for audio player

Beyond 'Good' Vs. 'Bad' Touch: 4 Lessons To Help Prevent Child Sexual Abuse
Tennessee Watson

More than 58,000 children were sexually abused in the U.S. in 2017, according to the U.S. Department of Health and Human Services .
Many states are trying to curb those numbers — 20 now require sexual abuse prevention education by law. In 2009, Vermont became one of the first.
K-12 schools in Vermont are required to provide sexual violence prevention to all students. Schools must also provide information to parents. Additionally, all schools and childcare facilities are required to train teachers and adult employees.
Vermont is a testing ground for states like Wyoming, which is one of nine other states that allow or recommend this type of education, but don't require it.
Jody Sanborn, the prevention specialist for the Wyoming Coalition Against Domestic Violence and Sexual Assault, wants all Wyoming communities to work to keep kids safe from sexual abuse. But she says Wyoming isn't there yet.
"Wyoming is at a stage of what we call denial or resistance that the issue even exists in the first place," Sanborn says.
Eventually, she'd like to see something in place to guarantee schools are teaching prevention statewide. But she knows Wyoming's strong culture of local control makes that hard.
In Vermont, it's up to local school boards to pick the curriculum they'd like to use.

California Lawmakers Consider How To Regulate Home Schools After Abuse Discovery

How Schools Can Reduce Sexual Violence
Linda Johnson, the executive director of Prevent Child Abuse Vermont , strongly encourages schools to adopt the evidence-based model that her organization has been using since the 1990s. It's a series of age-appropriate lessons designed to help protect little kids from sexual abuse.
That may sound like a scary topic, but this curriculum takes a positive approach by focusing on healthy relationships : How to pay attention to your feelings, knowing about your body and your boundaries, and, if something doesn't feel right, knowing you can ask for help.
Joy Kitchell, who runs a child advocacy center in Bennington, Vt., teaches the curriculum distributed by Johnson's organization. Kitchell worked as a teacher and a principal for years before turning her focus entirely to sexual abuse prevention.
She says parents feel more at ease knowing that their kids aren't explicitly talking about sex or sexual violence.
Still, she says, it's up to adults to know the signs and symptoms of abuse — and teach behaviors that could prevent it.
What can parents and teachers do to keep their kids safe? Kitchell and Johnson offer some key lessons geared toward sexual abuse prevention.
The lessons also address sexual abuse between kids. Johnson says talking about these things early might keep kids from doing harm as they get older.
Teach kids to pay attention to their feelings
Around 90 percent of child sexual abusers are someone the child knows, according to the Crimes Against Children Research Center.
Kitchell says that makes it even harder for kids to understand that something bad is happening.
"A person who is grooming a child to be their victim, they are going to do it in such a way that it's not going to be painful. It's going to be confusing," she says.
That's an important departure from teaching "good" versus "bad" touch.
"If a child is taught that it's good touch or bad touch, and it's not a bad touch but it's confusing, then they might not understand that it's OK to go to a trusted adult and figure that out," Kitchell says.
Let kids know they can talk to trusted grown-ups
Linda Johnson of Prevent Child Abuse Vermont says teaching children they can tell other grown-ups any time they're confused means they don't have to decide for themselves if the touch is good or bad.
And there's an important difference between teaching a kid they should tell versus teaching a kid they can tell, she says.
"We don't want to add guilt and sense of responsibility to children who have been victimized," she says.
Learning 'no' means no
One recurring theme in the curricula is the meaning of no. "That is the foundation of consent," Johnson says.
When one kid isn't willing to share with another kid, grown-ups often jump in to force them to share. But Johnson teaches adults to take a different approach. She says it's important to remind kids that hearing "no" is part of life.
"We can teach this to 2-year-olds, and then again at 3 and 4 and 5, 6, 7, 8, 9, 10, until — there they are in that situation in the car and one wants to and one doesn't want to," Johnson says. "And they have to be able to accept 'no' for an answer."
Start the conversation at home
When working with preschoolers and younger elementary schoolers, Kitchell uses picture books to help start conversations about boundaries and consent.
She also uses anatomically correct dolls to help kids learn the names of their body parts. She says these are things parents can also do at home.
Among the many books she uses are:
How Are You Peeling? by Saxton Freymann and Joost Elffers
Hands Off, Harry! by Rosemary Wells
Uncle Willy's Tickles: A Child's Right to Say No by Marcie Aboff
All By Myself by Mercer Mayer
The New Baby by Mercer Mayer
The Bare Naked Book by Kathy Stinson and Heather Collins
How Can I Protect My Child From Sexual Assault?
Para leer en español, haga clic aquí .
Sexual abuse can happen to children of any race, socioeconomic group, religion or culture. There is no foolproof way to protect children from sexual abuse, but there are steps you can take to reduce this risk. If something happens to your child, remember that the perpetrator is to blame—not you and especially not the child. Below you’ll find some precautions you can take to help protect the children in your life.
If your child is in immediate danger, don’t hesitate to call 911. If you aren’t sure of the situation but you suspect the child is being harmed , you can take steps to gauge the situation and put an end to the abuse.
Be involved in the child’s life.
Being actively involved in a child’s life can make warning signs of child sexual abuse more obvious and help the child feel more comfortable coming to you if something isn’t right. If you see or hear something that causes concern, you can take action to protect your child.
- Show interest in their day-to-day lives . Ask them what they did during the day and who they did it with. Who did they sit with at lunchtime? What games did they play after school? Did they enjoy themselves?
- Get to know the people in your child’s life . Know who your child is spending time with, including other children and adults. Ask your child about the kids they go to school with, the parents of their friends, and other people they may encounter, such as teammates or coaches. Talk about these people openly and ask questions so that your child can feel comfortable doing the same.
- Choose caregivers carefully . Whether it’s a babysitter, a new school, or an afterschool activity, be diligent about screening caregivers for your child.
- Talk about the media . Incidents of sexual violence are frequently covered by the news and portrayed in television shows. Ask your child questions about this coverage to start a conversation. Questions like, “Have you ever heard of this happening before?” or “What would you do if you were in this situation?” can signal to your child that these are important issues that they can talk about with you. Learn more about talking to your kids about sexual assault.
- Know the warning signs . Become familiar with the warning signs of child sexual abuse , and notice any changes with your child, no matter how small. Whether it’s happening to your child or a child you know, you have the potential to make a big difference in that person’s life by stepping in .
Encourage children to speak up.
When someone knows that their voice will be heard and taken seriously, it gives them the courage to speak up when something isn’t right. You can start having these conversations with your children as soon as they begin using words to talk about feelings or emotions. Don’t worry if you haven't started conversations around these topics with your child—it is never too late.
- Teach your child about boundaries . Let your child know that no one has the right to touch them or make them feel uncomfortable — this includes hugs from grandparents or even tickling from mom or dad. It is important to let your child know that their body is their own. Just as importantly, remind your child that they do not have the right to touch someone else if that person does not want to be touched.
- Teach your child how to talk about their bodies . From an early age, teach your child the names of their body parts. Teaching a child these words gives them the ability to come to you when something is wrong. Learn more about talking to children about sexual assault .
- Be available . Set time aside to spend with your child where they have your undivided attention. Let your child know that they can come to you if they have questions or if someone is talking to them in a way that makes them feel uncomfortable. If they do come to you with questions or concerns, follow through on your word and make the time to talk.
- Let them know they won’t get in trouble . Many perpetrators use secret-keeping or threats as a way of keeping children quiet about abuse. Remind your child frequently that they will not get in trouble for talking to you, no matter what they need to say. When they do come to you, follow through on this promise and avoid punishing them for speaking up.
- Give them the chance to raise new topics . Sometimes asking direct questions like, “Did you have fun?” and “Was it a good time?” won’t give you the answers you need. Give your child a chance to bring up their own concerns or ideas by asking open-ended questions like “Is there anything else you wanted to talk about?”
To speak with someone who is trained to help, call the National Sexual Assault Hotline at 800.656.HOPE (4673) or chat online at online.rainn.org .
Related Content
Talking to your kids about sexual assault.
Conversations about sexual assault can be a part of the safety conversations you’re already having, like knowing when to speak up, how to take care of friends, and listening to your gut.
Evaluating Caregivers
There are steps you can take to evaluate caregivers, such as babysitters or nursing homes, to reduce the risk of something happening to your loved one.
Child Sexual Abuse
When a perpetrator intentionally harms a minor physically, psychologically, sexually, or by acts of neglect, the crime is known as child abuse.
What are the warning signs for child sexual abuse?
Every 68 seconds, another american is sexually assaulted., 91¢ of every $1 goes to helping survivors and preventing sexual violence..

- High contrast
- Press Centre
Search UNICEF
Sexual violence against children, sexual violence knows no boundaries. it occurs in every country, across all parts of society..

- Violence against children
- Sexual violence
Every year, millions of girls and boys around the world face sexual abuse and exploitation. Sexual violence occurs everywhere – in every country and across all segments of society. A child may be subjected to sexual abuse or exploitation at home, at school or in their community. The widespread use of digital technologies can also put children at risk.
Most often, abuse occurs at the hands of someone a child knows and trusts.
At least 120 million girls under the age of 20 – about 1 in 10 – have been forced to engage in sex or perform other sexual acts, although the actual figure is likely much higher. Roughly 90 per cent of adolescent girls who report forced sex say that their first perpetrator was someone they knew, usually a boyfriend or a husband.
But many victims of sexual violence, including millions of boys, never tell anyone.
About 1 in 10 girls under the age of 20 have been forced to engage in sex or perform other sexual acts.
Although sexual violence occurs everywhere, risks surge in emergency contexts. During armed conflict, natural disasters and other humanitarian emergencies , women and children are especially vulnerable to sexual violence – including conflict-related sexual violence, intimate partner violence and trafficking for sexual exploitation – as well as other forms of gender-based violence .
Sexual violence results in severe physical, psychological and social harm. Victims experience an increased risk of HIV and other sexually transmitted infections, pain, illness, unwanted pregnancy, social isolation and psychological trauma. Some victims may resort to risky behaviours like substance abuse to cope with trauma. And as child victims reach adulthood, sexual violence can reduce their ability to care for themselves and others.
While sexual violence is fundamentally a crime of power, it is increasingly driven by economic motives. The internet has opened a rapidly growing global market for the production, distribution and consumption of child sexual abuse materials, such as photographs and videos. When online , children may be susceptible to sexual coercion and in-contact sexual abuse by offenders who attempt to extort them for content and financial gain.
The harmful norms that perpetuate sexual violence take a heavy toll on families and communities too. Most children who face sexual abuse experience other kinds of violence. And as abuse and exploitation become entrenched, progress towards development and peace can stall – with consequences for entire societies.
UNICEF’s response

UNICEF plays a key role in preventing and responding to sexual violence worldwide – both in emergency and non-emergency contexts – through programmes, partnerships and advocacy.
Globally, we build advocacy tools and develop technical guidance for violence prevention and response, helping to ensure services are appropriate and sensitive to the needs of survivors. We work closely with partners on a variety of global initiatives, including the Global Partnership to End Violence against Children , Together for Girls and the WePROTECT Global Alliance to End Child Sexual Exploitation Online .
At the national level, we work with governments to develop and strengthen laws and policies, and to increase access to justice, health, education and social services that help child and adolescent survivors recover. We also invest in national prevention programmes to change social norms that condone sexual violence and perpetuate a culture of silence.
Throughout all we do, we focus on supporting children and parents. We work directly with children to build their knowledge on how and where to seek help and protection; and with parents, teachers and adults to identity signs of abuse and make sure children receive ongoing care.
More from UNICEF

Stories of hope, courage and change
Read stories about the work of UNICEF and the Spotlight Initiative to end violence against women and girls across Latin America and Africa

DR Congo: Children killed, injured, abducted, and face sexual violence in conflict at record levels for third consecutive year – UNICEF
UNICEF calls for urgent action to respond to alarming levels of increasing sexual violence against girls and women in eastern DRC
On world poetry day, hundreds of children affected by conflict and war share poems for peace, action to end child sexual abuse and exploitation: a review of the evidence 2020.
This evidence review documents the evidence on effective interventions and strategies to prevent and respond to child sexual abuse and exploitation.
Action to End Child Sexual Abuse and Exploitation
The Action to End Child Sexual Abuse and Exploitation proposed a framework of action to prevent and respond to child sexual abuse and exploitation.
UNICEF Humanitarian Practice: COVID-19 Technical Guidance
Terminology guidelines for the protection of children from sexual exploitation and abuse, promising programmes to prevent and respond to child sexual abuse and exploitation , preventing and responding to child sexual abuse and exploitation: evidence review, government, civil society and private sector responses to the prevention of sexual exploitation of children in travel and tourism , protecting children from online sexual exploitation: a guide to action for religious leaders and communities, unicef and leap: a new reality – child helplines report on online child sexual exploitation and abuse, optional protocol to the convention on the rights of the child on the sale of children, child prostitution and child pornography, implementation handbook on the optional protocol on the sale of children, child prostitution and child pornography, child safety online: global challenges and strategies, world congress iii against sexual exploitation of children and adolescents, council of europe convention on the protection of children from sexual exploitation and sexual abuse, code of conduct for the protection of children from sexual exploitation in travel and tourism, ecpat international, together for girls initiative to end sexual violence, un special representative of the secretary-general on violence against children, online course: action to end child sexual exploitation and abuse, legislating for the digital age: global guide on improving legislative frameworks to protect children from online sexual exploitation and abuse framing the future: how the model national response framework is supporting national efforts to end child sexual exploitation and abuse online.
Last updated 23 June 2022
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- HHS Author Manuscripts

A systematic review of primary prevention strategies for sexual violence perpetration ☆
Associated data.
This systematic review examined 140 outcome evaluations of primary prevention strategies for sexual violence perpetration. The review had two goals: 1) to describe and assess the breadth, quality, and evolution of evaluation research in this area; and 2) to summarize the best available research evidence for sexual violence prevention practitioners by categorizing programs with regard to their evidence of effectiveness on sexual violence behavioral outcomes in a rigorous evaluation. The majority of sexual violence prevention strategies in the evaluation literature are brief, psycho-educational programs focused on increasing knowledge or changing attitudes, none of which have shown evidence of effectiveness on sexually violent behavior using a rigorous evaluation design. Based on evaluation studies included in the current review, only three primary prevention strategies have demonstrated significant effects on sexually violent behavior in a rigorous outcome evaluation: Safe Dates ( Foshee et al., 2004 ); Shifting Boundaries (building-level intervention only, Taylor, Stein, Woods, Mumford, & Forum, 2011 ); and funding associated with the 1994 U.S. Violence Against Women Act (VAWA; Boba & Lilley, 2009 ). The dearth of effective prevention strategies available to date may reflect a lack of fit between the design of many of the existing programs and the principles of effective prevention identified by Nation et al. (2003) .
1. Introduction
Sexual violence 2 is a significant public health problem affecting millions of individuals in the United States and around the world ( Black et al., 2011 ; Krug, Dahlberg, Mercy, Zwi, & Lozano, 2002 ; World Health Organization/London School of Hygiene & Tropical Medicine, 2010 ). Efforts to prevent sexual violence before it occurs (i.e., primary prevention) are increasingly recognized as a critical and necessary complement to strategies aimed at preventing re-victimization or recidivism and ameliorating the adverse effects of sexual violence on victims (e.g., Black et al., 2011 ; Centers for Disease Control & Prevention, 2004 ; DeGue, Simon, et al., 2012 ; Krug et al., 2002 ). Successful primary prevention efforts, however, require an understanding of what works to prevent sexual violence and implementing effective strategies. Currently, there are no comprehensive, systematic reviews of evaluation research on primary prevention strategies for sexual violence perpetration. Such a review is needed to inform prevention practice and guide additional research to build the evidence base. To address this gap, the current paper provides a systematic review and summary of the existing literature and identifies gaps and future directions for research and practice in the prevention of sexual violence perpetration.
Primary prevention strategies, as defined here, include universal interventions directed at the general population as well as selected interventions aimed at those who may be at increased risk for sexual violence perpetration ( Centers for Disease Control & Prevention, 2004 ). To capture the breadth of possible sexual violence prevention efforts, we defined primary prevention strategies to include any primary prevention efforts, including policies and programs (similar to Saul, Wandersman, et al., 2008 ). Consistent with the public health approach to sexual violence prevention ( Cox, Ortega, Cook-Craig, & Conway, 2010 ; DeGue, Simon, et al., 2012 ; McMahon, 2000 ), strategies to prevent violence perpetration, rather than victimization, are the focus of this review. Although risk reduction approaches that aim to prevent victimization can be important and valuable pieces of the prevention puzzle 3 , a decrease in the number of actual and potential perpetrators in the population is necessary to achieve measurable reductions in the prevalence of sexual violence ( DeGue, Simon, et al., 2012 ).
1.1. Goals of the current review
1.1.1. describing the state of the field in sexual violence prevention.
The first goal of this review is to describe the broad field of sexual violence prevention research and identify patterns of results associated with evaluation methodology or programmatic elements. Although a number of qualitative reviews, meta-analyses, and one meta-review (e.g., Anderson & Whiston, 2005 ; Breitenbecher, 2000 ; Carmody & Carrington, 2000 ; Vladutiu, Martin, & Macy, 2011 ) have been conducted over the past two decades, no reviews examine methodological and programmatic elements and sexual violence outcomes across the broad spectrum of sexual violence primary prevention efforts. Several existing reviews focus solely on describing approaches being implemented in the field and the use of underlying theory ( Carmody & Carrington, 2000 ; Fischhoff, Furby, & Morgan, 1987 ; Paul & Gray, 2011 ). Two non-systematic reviews identified methodological and programmatic issues associated with sexual violence prevention efforts with college students ( Breitenbecher, 2000 ; Schewe & O’Donohue, 1993 ) and called attention to the need to measure behavioral outcomes (in addition to changes in attitudes and behavioral intentions) to demonstrate an impact on sexual violence. These reviews also pointed out that the small statistically significant effects reported on the, primarily attitudinal, measures in existing studies may not be truly meaningful (i.e., clinically significant). These existing reviews focused solely on college-based strategies, limiting the generalizability of these findings to community-based and younger audiences.
Three meta-analyses examined the effectiveness of educational prevention programming with college students ( Anderson & Whiston, 2005 ; Brecklin & Forde, 2001 ; Flores & Hartlaub, 1998 ), but two of these focused only on attitudinal outcomes (i.e., Brecklin & Forde, 2001 ; Flores & Hartlaub, 1998 ). All three reported small to moderate mean effects on attitudes ranging from 0.06 to 0.35 (e.g., rape myth acceptance) and noted that the magnitude of effects decreased as the interval between strategy implementation and data collection increased. In addition, Anderson and Whiston (2005) reported a moderate mean effect size for knowledge (0.57), but reported small mean effect sizes for behavioral intentions (0.14), incidence of sexual violence (0.12), and attitudes considered more distal to sexual violence (0.10; e.g., adversarial sexual beliefs, hostile attitudes toward women), suggesting that the changes may have little clinical significance. Mean effect sizes for rape empathy and indicators of greater rape awareness (e.g., willingness to volunteer at rape crisis centers) were not significantly different from zero. The results from these meta-analyses suggest that knowledge and attitudes are assessed most frequently in prevention programming with college students, with attitudinal measures showing the largest effect sizes in evaluations of those programs. Although attitudes and behaviors are related, attitudes typically account for a relatively small proportion of the variance in behavior (e.g., Glasman & Albarracín, 2006 ; Kraus, 1995 ), suggesting that achieving attitude change may not be enough to impact sexual violence behaviors.
The one meta-review ( Vladutiu et al., 2011 ) also focused on reviews of college-based programs. Vladutiu and colleagues noted that reviews often made inconsistent recommendations, primarily due to differences in program context and content and the outcomes examined in the studies. For example, Vladutiu et al. (2011) concluded that longer programs were generally associated with greater effectiveness, but some shorter programs were able to document change when rape myth acceptance was the only outcome of interest. Single-gender audience approaches were generally considered more effective, but primarily when the program focused on attitudes, empathy, and knowledge outcomes related to sexual violence. The meta-review also identified a wide range of content and delivery components that were associated with changes on different outcomes. Finally, Vladutiu et al. (2011) noted that of the reviews included in their meta-review, only one had been published in the last decade (i.e., Anderson & Whiston, 2005 ). As indicated previously, there are no comprehensive reviews of the sexual violence prevention evaluation literature, and the only systematic reviews have dealt solely with college-based strategies. Relatively few patterns have been identified or recommendations made with respect to improving primary prevention of sexual violence or the rigor of evaluations conducted in the field. An updated, systematic, and comprehensive review of the literature on sexual violence primary prevention programs is warranted.
1.1.2. Summarizing “what works” in sexual violence prevention
The second goal of this review is to identify and summarize the best available evidence on specific sexual violence primary prevention strategies. Prevention practitioners are increasingly being asked to select and implement evidence-based practices and to devote resources toward strategies most likely to have an impact on health outcomes, but guidance and information on navigating this process are lacking ( Saul, Duffy, et al., 2008 ; Tseng, 2012 ). In particular, we wish to identify effective strategies for preventing sexual violence perpetration behaviors, as that is the ultimate goal of sexual violence prevention efforts. Although targeting risk and protective factors such as attitudes and knowledge are common prevention approaches, the most critical objective is to prevent sexual violence perpetration behaviors and their adverse effects ( Centers for Disease Control & Prevention, 2004 ; World Health Organization/London School of Hygiene & Tropical Medicine, 2010 ). Evidence regarding change in sexual violence perpetration behavior, however, is generally absent from the literature ( Schewe & O’Donohue, 1993 ; Vladutiu et al., 2011 ; World Health Organization/London School of Hygiene & Tropical Medicine, 2010 ). By summarizing the evidence on strategies that have been rigorously evaluated for sexually violent behavior, we can identify and categorize programs that currently appear to have evidence of effectiveness, those that are ineffective, and others that are potentially harmful strategies to assist practitioner efforts at better selecting and implementing sexual violence prevention strategies.
2.1. Search strategy
To identify studies meeting selection criteria for this review, we first conducted searches of the following online databases between May and August of 2009 and repeated these searches in March and April of 2010 and May of 2012: PsycNet, PsycExtra, PubMed, ERIC, Sociological Abstracts, MEDLINE, Web of Knowledge, Dissertation Abstracts International, and GoogleScholar. Search terms included combinations of the following: (intervention, prevent*, program, effectiveness, efficacy or evaluation) and (perpetration, rape, rapist, sex*, coercion, violence, aggression, assault, offender, or abuse). Second, manual reviews of issues from relevant journals (i.e., Aggression and Violent Behavior , Journal of Adolescent Health , Journal of Interpersonal Violence , Journal of Women’s Health , Prevention Science , Psychology of Violence , Sexual Abuse: Journal of Research and Treatment , Trauma , Violence , & Abuse , Violence Against Women , Violence & Victims ) published between January 2008 and May 2012 were also conducted to identify recent work in this area that may not have been cataloged yet in searchable databases. Third, to identify unpublished evaluation reports, solicitations were sent to relevant email lists and e-newsletters, including Prevent Connect, VAWnet, and the Sexual Violence Research Initiative. Fourth, for each article or report identified, we scanned the reference list to identify and retrieve additional reports that might meet inclusion criteria. During each of these iterative search steps, we were over-inclusive to ensure that all abstracts with the potential for inclusion were identified. The initial searches identified more than 10,600 reports, from which 330 were retained for full-text retrieval because they appeared to describe an outcome evaluation of a sexual violence prevention strategy.
2.2. Study selection criteria
Studies were eligible for inclusion if they examined the effectiveness of primary prevention strategies for sexual violence perpetration and were published in print or online between January 1985 4 and May 2012. Journal articles, book chapters, and reports from government agencies or other institutions were included. Efforts were made to gather unpublished manuscripts, conference presentations, theses, and dissertations (see above). Because the focus on this review is to summarize the evidence base for the primary prevention of sexual violence perpetration, this review did not include studies that exclusively examined secondary and tertiary prevention approaches (e.g., treatment or recidivism prevention), strategies targeting victimization prevention (i.e., risk reduction), or etiological research. In order to avoid double-counting studies, existing reviews and meta-analyses of interventions for sexual violence prevention were excluded.
Only studies that compared one intervention condition to a no-treatment or waitlist control group (i.e., experimental and quasi-experimental designs) or that utilized a single-group pre–post design were included in this review, as the goal was to ascertain changes or differences in the outcomes following exposure to a specific treatment program. Thus, we excluded studies in which data from two different intervention groups were combined and compared to a control group as it was not possible to determine which intervention was responsible for any observed changes on the outcome measures. In addition, we excluded studies in which the intervention and the comparison conditions received different sexual violence prevention programs, because these studies examine the relative benefits of one program compared to another program as opposed to an individual program’s overall effectiveness relative to no intervention. Similarly, studies in which the comparison condition included a combined sample of control participants and participants who received a different sexual violence preventative intervention were also excluded. Because our focus was to examine the effectiveness of strategies to prevent sexual violence, studies that did not measure outcomes relevant to sexual violence perpetration were excluded (see below for a description of the outcomes included).
Of the 330 full-text reports retrieved, 226 reports were excluded. Reports were excluded because they did not describe an outcome evaluation study (45%; n = 101; e.g., review or meta-analysis, program description, theoretical paper, etiological research), did not measure sexual violence-related outcomes (11%; n = 25), evaluated a victimization prevention strategy only (10%; n = 23), did not evaluate a primary prevention strategy (8%; n = 18; e.g., sex offender treatment or recidivism prevention), did not utilize a research design with a comparison group or pre–post measurement (7.5%; n = 17), or met other exclusion criteria (8.1%; n = 27; e.g., non-English language). In addition, we identified several reports that described outcomes from the same study (e.g., a dissertation and a peer-reviewed journal article). In these cases, the peer-reviewed journal article was coded as the primary source and other reports were excluded as a duplicate report (3%; n = 7). In some cases, the excluded reports (e.g., dissertations) were used to provide supplemental information about the sexual violence prevention program or the evaluation design during the coding process. Numerous attempts were made to retrieve all reports identified in the initial searches, including contacting the first author directly and utilizing inter-library loan resources to obtain print copies. However, another eight reports (3.5%) identified through database searches could not be retrieved and were excluded as unavailable. These missing reports were nearly all dissertations and most were published more than 15 years ago; thus, this review may underrepresent these older dissertations.
2.3. Data extraction
2.3.1. coding process.
The review team developed a structured coding sheet 5 to extract, quantify, and summarize information from studies. A detailed coding manual was developed to ensure consistency across coders. Before coding began, the review team completed several reviews in order to refine the coding sheet and manual and to increase reliability. The review team consisted of six doctoral-level researchers with expertise in violence prevention. Two reviewers independently coded each of the 104 reports meeting inclusion criteria for this study between November of 2009 and December of 2012. Coding dyads were randomized such that no two coders coded more than one-sixth of the studies together. After each study was coded independently by two reviewers, coding sheets were compared and discrepancies were discussed. Initial agreement by independent coders was acceptable, with reviewers initially agreeing on 75.6% of codes. The coding dyad discussed any items on which there was disagreement until consensus was reached on the best possible response for each item, and the final consensus code was used in analyses.
2.3.2. Study variables and outcomes coded
The variables coded included the report type, study design, sample, nature of the prevention strategy (i.e., setting, delivery, dose, stated program goals, program content), and relevant program outcomes. Study outcomes relevant to sexual violence were coded within eight key categories: sexually violent behavior 6 including rates or reports of perpetration or victimization; rape proclivity or self-reported likelihood of future sexual perpetration; attitudes about gender roles, sexual violence, sexual behavior, or bystander intervention; knowledge about sexual violence rates, definitions, and laws; bystanding behavior related to sexual violence, such as intervening in a risky situation or speaking up about violence; bystanding intentions or self-reported likelihood of intervening in a hypothetical scenario; relevant skills related to communication, relationships, or bystanding behavior, and affect / arousal to violence including victim-related empathy and sexual attraction to violence.
The patterns of intervention effects within each study were summarized within and across outcome categories. Intervention effects were considered positive if significant effects were reported on all relevant outcomes in the hypothesized direction at all measurement time points. Study effects were categorized as null if all findings on relevant outcomes were non-significant. Effects were mixed if findings were a combination of positive and null. Studies that had at least one significant finding on any relevant outcome in a negative direction, suggesting potentially harmful effects of the intervention, were categorized as having negative effects. Given the diversity of study designs, outcome measures, and follow-up periods examined, it was necessary to collapse findings from multiple measures and measurement periods within each study to characterize the overall patterns of effectiveness. For example, findings from multiple attitudinal measures relevant to sexual violence were collapsed into a composite “attitudes” category. For some analyses, these findings were further collapsed across outcome types (e.g., attitudes, knowledge) to obtain a summary of the overall effects. Similarly, intervention effects observed at different time points (i.e., post-test, follow-up) were combined into one code to represent the overall pattern of outcomes for that study.
2.3.3. Study sample
Of the 104 reports coded, 73 described a single study in which one prevention strategy was evaluated using a comparison group or pre–post design. The remaining 31 reports described findings from more than one evaluation study. The majority of these reports ( n = 25) compared two or more prevention strategies to a single control group, resulting in non-independent data across the various studies. Four reports described two or more separate studies in which samples were distinct and data were independent. Two reports included one study with independent data and two with non-independent data in the same report. To examine outcome data for each separate preventative program or strategy evaluated, we coded information about the study design, program characteristics and content, and outcome data for each of these studies separately. This approach is consistent with the process for systematic reviews recommended by the Task Force on Community Preventive Services ( Briss et al., 2000 ). Thus, the review team identified and coded 140 separate evaluation studies from the 104 reports meeting inclusion criteria. References for all studies included in this review are available in an online supplemental archive (see supplemental materials ); studies mentioned in the text are also referenced below.
2.4. Criteria for defining rigorous evaluation designs
Studies were classified as having either a rigorous or non-rigorous evaluation design. Rigorous evaluation designs included experimental studies with random assignment to an intervention or control condition (e.g., randomized controlled trial [RCT], cluster RCT) or rigorous quasi-experimental designs, such as interrupted time series or regression-discontinuity, for strategies where random assignment is not possible due to implementation restrictions (e.g., evaluation of policy). Other quasi-experimental designs (e.g., comparison groups without randomization to condition, including matched groups) and pre–post designs were considered non - rigorous evaluation designs , for the purposes of examining effectiveness in this review, consistent with standards of prevention science and evaluation research (e.g., Eccles, Grimshaw, Campbell, & Ramsay, 2003 ; Flay et al., 2005 ; Shadish, Cook, & Campbell, 2002 ).
In addition to design considerations, studies meeting criteria for a rigorous evaluation design were required to have at least one follow - up assessment beyond an immediate post-test assessment. Prior research has established the presence of a rebound effect on attitudinal and knowledge outcomes for sexual violence prevention programs wherein effects are seen immediately after the program but are not evident at longer-term follow-up ( Anderson & Whiston, 2005 ; Brecklin & Forde, 2001 ; Carmody & Carrington, 2000 ). In addition, studies without a follow-up assessment often conducted the pre-test and the post-test measurement and the intervention all within the same session, increasing the potential influence of demand characteristics and test–retest effects. Thus, studies that did not include at least one follow-up measurement beyond immediate post-test, regardless of the research design, were also considered to be non-rigorous.
2.5. Criteria for evaluating evidence of effectiveness for preventing sexual violence
To identify prevention strategies with rigorous evidence of effectiveness, we developed criteria to classify specific interventions based on the strength of evidence of effectiveness for preventing sexually violent behavior. These criteria, illustrated in Fig. 1 , emphasize sexual violence behavioral outcomes and rigorous experimental research designs that permit inferences about causality. Based on these criteria, interventions were placed into one of five categories: Effective for Sexual Violence Behavioral Outcomes includes those interventions with evidence of any positive impact on sexual violence victimization or perpetration in at least one rigorous evaluation. Interventions categorized as Not Effective for Sexual Violence Behavioral Outcomes were evaluated on sexual violence outcomes using a rigorous evaluation design and had consistently null effects on those measures. Interventions categorized as Potentially Harmful for Sexual Violence Behavioral Outcomes include those with at least one negative effect on sexually violent behavior in a rigorous evaluation. Interventions categorized as More Research Needed included those with evidence of positive effects on sexual violence behavior in a non-rigorous evaluation or positive effects on sexual violence risk factors or related outcomes in a rigorous evaluation. Interventions were considered to have Insufficient Evidence if they were not published in a peer-reviewed journal or formal government report, if they measured outcomes at immediate post-test only without a longer follow-up period, if they found null effects on sexual violence behavioral outcomes using a non-rigorous design; and/or if they only examined risk factors or other related outcomes using a non-rigorous design (regardless of the type of effect).

Decision tree for evaluating evidence of effectiveness on sexual violence behavioral outcomes in rigorous evaluation.
We attempted to identify and combine findings from multiple studies or reports examining the same intervention based on the program name or description and used outcomes from the most rigorous evaluation(s) available to categorize the program’s effects. In some cases, researchers may have evaluated modified versions of the same program over time; findings from these evaluations were considered together if the program name did not change and there were no indications that modifications to the structure or content of the program model over time substantially altered the core content or strategy.
3.1. Study and intervention characteristics
Evaluation of sexual violence perpetration prevention programs peaked in the late 1990s and again in 2010 and 2011 (see Fig. 2 ). Table 1 describes characteristics of the 140 studies and interventions, including the research design, study population, intervention length, setting, participant and presenter sex, and mode of delivery. Notably, almost two-thirds ( n = 84; 60%) of the included studies examined one-session interventions with college populations; these programs had an average length of 68 min. The majority of studies utilizing pre–post designs measured outcomes at immediate post-test only ( n = 13, 56.5%). Studies with quasi-experimental designs measured outcomes most often at post-test ( n = 12, 34.3%) or with a follow-up period of one month or less ( n = 10, 28.6%). In contrast, evaluations using experimental designs had the lowest proportion of studies with post-test only outcomes ( n = 19, 23.2%) and the highest proportion with follow-ups at 5 months or longer ( n = 17, 20.7%).

Number of studies meeting inclusion criteria by publication year (Jan 1985–May 2012).
Study and intervention characteristics.
To examine changes in evaluation methodology over time, we compared studies published in 1999 or earlier ( n = 73; 52.1%) to those published in 2000 or later ( n = 67; 47.9%). Before 2000, 63% ( n = 46) of published studies were RCTs, 30.1% ( n = 22) used quasi-experimental designs, and 6.8% ( n = 5) used pre–post designs; 28.8% ( n = 21) assessed outcomes at immediate post-test only and only 6.8% ( n = 5) followed participants for 5 months or longer. Since 2000, 53.7% ( n = 36) of published studies were RCTs, 19.4% ( n = 13) were quasi-experimental, and 26.9% ( n = 18) were pre–post designs; 34.3% ( n = 23) of these studies measured outcomes at immediate post-test only, but another 26.9% ( n = 18) of studies assessed outcomes after at least 5 months.
3.2. Intervention effects by study characteristics and outcome type
Table 2 summarizes patterns of intervention effects by study characteristic and outcome types. Studies with mixed effects across outcome types and follow-up periods were most common (41.4%; n = 58). More than one-quarter of studies (27.9; n = 39) reported only positive effects and another 21.4% ( n = 30) reported only null findings. Nine studies (6.4%) had at least one negative finding suggesting that the intervention was associated with increased reporting of sexually violent behavior ( Potter & Moynihan, 2011 ; Stephens & George, 2009 ), rape proclivity ( Duggan, 1998 ; Hillenbrand-Gunn, Heppner, Mauch, & Park, 2010 ), or attitudes toward sexual violence ( Echols, 1998 ; McLeod, 1997 ; Murphy, 1997 ). Peer-reviewed studies and government reports tended to have positive or mixed findings more often than dissertations and unpublished manuscripts. Examination of outcomes by study design suggested that evaluations employing more rigorous methodologies (i.e., experimental or quasi-experimental designs with comparison groups) were less likely to identify consistently positive effects than studies using a pre–post design. Similarly, studies that examined outcomes at immediate post-test only were more likely to identify positive effects than studies with a longer follow-up period.
Patterns of intervention effects by study characteristics and outcome type.
Note . Of the 140 studies reviewed, 136 conducted sufficient outcome analyses to determine the effects of the intervention on relevant measures; the remaining four studies from three reports ( Feltey, Ainslie, & Geib, 1991 ; Heppner, Humphrey, Hillenbrand-Gunn, & DeBord, 1995 ; Wright, 2000 ) are not included in these analyses.
Looking at the pattern of intervention effects by outcome type, results suggest that null effects were more common and positive effects less common on sexually violent behavior and rape proclivity outcomes than on other outcome types. Specifically, about half of all studies measuring sexually violent behavior or rape proclivity found only null effects (47.6%; n = 10); very few studies (4.8%; n = 4) reported only significant, positive effects on these main outcomes of interest. In contrast, the majority of studies measuring knowledge, bystanding behavior or intentions or skills found consistently significant positive effects on these outcomes. No clear pattern was evident for studies assessing attitudinal or affective/arousal outcomes.
To examine the potential impact of intervention length, we estimated the average intervention exposure (i.e., sessions × length) for studies with positive, mixed, negative, and null effects. Findings indicate that interventions with consistently positive effects were about 2 to 3 times longer, with an average length of 6 h ( SD = 11.4), than interventions with mixed ( M = 3.2 h; SD = 6.6), negative ( M = 2.2 h; SD = .9), or null ( M = 2.8 h; SD = 4.3) effects.
3.3. Evidence of effectiveness for preventing sexual violence perpetration
As shown in Table 3 , only three interventions (based on 3 studies; 2.1%) were categorized as effective for sexual violence behavioral outcomes: Safe Dates (e.g., Foshee et al., 2004 , 2005 ), Shifting Boundaries building-level intervention ( Taylor, Stein, Mumford, & Woods, 2013 ; Taylor et al., 2011 ), and funding associated with the 1994 U.S. Violence Against Women Act ( Boba & Lilley, 2009 ). Five interventions (based on 11 studies; 6.4%) were found to be not effective for sexual violence behavioral outcomes and three interventions (based on 2 studies; 2.1%) reported evidence suggesting that they were potentially harmful. Another ten interventions (based on 17 studies; 12.1%) were categorized as needing more research in order to understand their effects. Findings within each of these categories are discussed below. The majority of studies reviewed ( n = 108; 77.1%) provided insufficient evidence to adequately evaluate the effectiveness of the intervention for preventing sexual violence; these studies were unpublished manuscripts or dissertations which had not been subjected to independent peer review ( n = 53; 38%), measured outcomes at immediate post-test only ( n = 57; 41%), and/or examined only risk factors or related outcomes for sexual violence using a non-rigorous design ( n = 71; 51%). Interventions with insufficient evidence are not included in Table 3 due to the large number of studies in this category and the lack of practical value for this information when the findings are inconclusive.
Summary of the best available evidence for the primary prevention of sexual violence (SV) perpetration.
4. Conclusions and discussion
The current systematic review sought to address two key objectives in an effort to inform and advance the research and practice fields of sexual violence primary prevention. First, by examining evaluation research on the primary prevention of sexual violence perpetration over nearly 30 years, we aimed to describe and assess the breadth, quality, and evolution of evaluation research and prevention programming in order to identify gaps for future development, implementation, and evaluation work. Second, we categorized sexual violence prevention programs on their evidence of effectiveness in an effort to inform decision-making in the practice field based on the best available research evidence.
4.1. State of the field: research on the primary prevention of sexual violence perpetration
In the last three decades, a sizable literature has emerged examining the effectiveness of strategies to prevent sexual violence perpetration with more than 100 evaluation reports identified since 1985. The number of studies published in the last two years of this review increased notably, suggesting a possible resurgence of research interest in this area. However, our results suggest that the sexual violence prevention evaluation literature has not seen a steady increase in publications over time to mirror the large increases in other types of sexual violence research. A bibliometric analysis of sexual violence research found that publications with the keywords “rape,” “sexual assault,” or “sexual violence” increased over 250% between 1990 and 2010, from approximately 5990 citations in 1990 to about 15,400 citations in 2010 ( Centers for Disease Control & Prevention, 2012 ). Despite this marked increase in general research attention to sexual violence, the current review suggests that the prevention evaluation literature has remained relatively stagnant both in terms of quantity and quality. In part, this trend may reflect the relatively limited resources available during this period for development and rigorous evaluation of sexual violence primary prevention approaches ( Jordan, 2009 ; Koss, 2005 ). Fortunately, funding for sexual violence evaluation research has increased over the last decade. For example, CDC funded 27 research projects with a focus on sexual violence between 2000 and 2010, resulting in the increased availability of more than $19 million in federal funding for the field; more than half of these projects involved prevention evaluation research ( Centers for Disease Control & Prevention, 2012 ; DeGue, Simon, et al., 2012 ). Although this funding represents a large proportional increase in federal dollars available for sexual violence research, the total research funding available remains low compared to other forms of violence and other areas of public health ( Backes, 2013 ; DeGue, Massetti, et al., 2012 ).
In addition to limiting the quantity of evaluation research studies, fiscal constraints may have also resulted in less rigorous research designs, as large randomized controlled trials of prevention strategies are generally considered costly to implement. Indeed, this review found two-thirds of the evaluation studies conducted over nearly 30 years examined brief, one-session interventions with college populations, approaches that are relatively inexpensive to implement and evaluate. In terms of measurement, few of these studies ( n = 11) measured sexually violent behavior, and none found consistently positive effects on these key behavioral outcomes. Of course, the predominance of brief awareness and education strategies in the literature not only reflects resource limitations for research but also implementation challenges in the field. Many colleges may limit access to students to only one class period or have policies requiring only 1 h of relevant training—spurring the development of programs to fit this need. Nevertheless, future research is needed that rigorously evaluates a more diverse and comprehensive set of prevention approaches with various populations.
Although the vast majority of preventative interventions evaluated to date have failed to demonstrate sufficient evidence of impact on sexual violence perpetration behaviors, progress is being made. Findings from several large, federally-funded 7 effectiveness trials of comprehensive, multi-component primary prevention strategies have been published more recently, with interventions targeting a broader, and younger, segment of the population (e.g., Foshee et al., 2004 , 2012 ; Miller et al., 2012b ; Taylor et al., 2013 ) with additional evaluations underway (e.g., Cook-Craig et al., in press ; Espelage, Low, Polanin, & Brown, 2013 ; Tharp, Burton, et al., 2011 ). This new research is providing the primary prevention practice field with additional evidence on which to base decisions about resource allocation and implementation in order to prevent sexual violence. However, as we discuss below, more rigorous evaluation research on various prevention approaches is needed before we can expect to see measurable reductions in sexual violence at the population level.
4.1.1. Evaluation methodology
A movement toward evidence-based policymaking has been gaining traction in the US. In 2012, the U.S. Office of Management and Budget directed federal agencies to prioritize rigorous research evidence in budget, management, and policy decisions in order to improve effectiveness and reduce costs ( Office of Management & Budget, 2012 ). These shifting federal priorities reflect a growing push in the field by researchers and advocacy organizations such as the Coalition for Evidence-Based Policy ( www.coalition4evidence.org ) for increased investment in evaluation research and the implementation of evidence-based programs. Evaluation guidelines provided by these various stakeholders emphasize the value of well-conducted, rigorous evaluations with an emphasis on randomized controlled trials to permit the strongest possible conclusions regarding causality (e.g., Flay et al., 2005 ; Office of Management & Budget, 2012 ).
A small majority (58.6%) of the studies in this review utilized an experimental design with randomization, and about three-quarters of these collected follow-up data beyond an immediate post-test. Thus, fewer than half (45%; n = 63) of the included studies met our minimum criteria for a rigorous evaluation. Further, only 17 of the rigorous evaluations included measures of sexually violent behavior, the intended public health outcome of the programs. In summary, after nearly 30 years of research, the field has produced very few evaluation studies using a research design that, if well-conducted, would permit conclusions regarding the effectiveness of the intervention for preventing sexually violent behavior. This shortage of rigorous research accounts, in large part, for the lack of evidence-based interventions available to practitioners to date.
The use of less rigorous methodologies, such as single-group or quasi-experimental designs, is often necessary and cost-effective for the purposes of program development, improvement, and to establish initial empirical support for an intervention ( Tharp, DeGue, et al., 2011 ). However, there is an implicit expectation that the rigor of evaluation research will continue to increase over time, both for individual interventions with promising initial outcomes and for the literature as a whole ( Tharp, DeGue, et al., 2011 ). However, this review did not find evidence of a general shift toward more rigorous evaluation methodology in the field over time. A comparison of studies published before and after 2000 found that evaluations completed from 2000 to 2012 were actually less likely to utilize an experimental design with randomization (53.7% vs. 63%) and more likely to utilize a pre–post design (26.9% vs. 6.8%) than studies from 1985 to 1999. Further, most of the identified interventions were the subject of a single evaluation rather than an evolving program of research, regardless of the initial study quality or findings. Progress in the field is dependent on systematic research initiatives that build off of the existing evidence base and move toward the ultimate goal of identifying “what works”.
4.1.2. Prevention approach
Much has been learned from the prevention science and public health fields about the characteristics of effective prevention strategies. For example, Nation et al. (2003) identified nine “principles of prevention” that were strongly associated with positive effects across multiple literatures and found that effective interventions had the following characteristics: (a) comprehensive, (b) appropriately timed, (c) utilized varied teaching methods, (d) had sufficient dosage, (e) were administered by well-trained staff, (f) provided opportunities for positive relationships, (g) were socio-culturally relevant, (h) were theory-driven, and (i) included outcome evaluation. Similar sets of “best practices” for prevention have been articulated elsewhere (e.g., Small, Cooney, & O’Connor, 2009 ). With the exception of outcome evaluation which we addressed above, we consider how well the sexual violence literature to date aligns with each of these principles.
4.1.2.1. Comprehensive
Comprehensive strategies should include multiple intervention components and affect multiple settings to address a range of risk and protective factors for sexual violence ( Nation et al., 2003 ). However, the vast majority of interventions evaluated for sexual violence prevention have been fairly one-dimensional — implemented in a single setting, typically a school or college, and often utilizing a narrow set of strategies to address individual attitudes and knowledge related to sexual violence. A minority of programs included content to address individual-level risk factors other than attitudes and knowledge (e.g., relevant skills and behaviors). Fewer than 10% included content to address factors beyond the individual level, such as peer attitudes, social norms, or organizational climate and policies, despite evidence that relationship and contextual factors are also important in shaping risk for sexual violence perpetration ( Casey & Lindhorst, 2009 ; Tharp et al., 2013 ). Several relatively recent studies have evaluated interventions that utilize a more comprehensive approach by combining educational or skills-building curricula with social norms campaigns, policy changes, community interventions, and/or environmental changes (e.g., Ball et al., 2012 ; Foshee et al., 2004 ; Taylor et al., 2011 ); however, comprehensive interventions remain the exception and not the norm. In order to potentially reduce and prevent sexual violence, program developers should build off of this work and develop a range of comprehensive strategies geared toward multiple populations.
4.1.2.2. Appropriately-timed
More than two-thirds of sexual violence prevention strategies evaluated thus far have targeted college samples. There is consensus that college men and women are at a particularly high risk for sexual violence perpetration and victimization, making this a key population for intervention. However, because many college men have already engaged in sexual violence before arriving on campus or will shortly thereafter ( Abbey & McAuslan, 2004 ), prevention initiatives that address this age group may miss the window of opportunity to prevent sexual violence before it starts. Primary prevention efforts may be best targeted at younger populations—before college. Sexually violent behavior is often initiated in adolescence ( Abbey & McAuslan, 2004 ), and more than 40% of victims will experience their first completed rape before age 17 ( Black et al., 2011 ). Only about one-quarter of the studies reviewed here evaluated interventions in high schools, middle schools, or elementary schools. However, younger populations are getting increased attention from program developers and evaluators in recent years. One-third of the evaluations involving school-aged youth in this review were published in 2010 or later, and several randomized trials of school-based strategies are underway in the field ( Cook-Craig et al., in press ; Espelage et al., 2013 ; Tharp, Burton, et al., 2011 ). It is notable that the only strategies with evidence of effectiveness on sexually violent behavior, to date, target adolescents. This is consistent with findings from a recent review of intimate partner violence prevention strategies ( Whitaker, Murphy, Eckhardt, Hodges, & Cowart, 2013 ), suggesting that adolescence may represent a critical window to intervene on these related behaviors. Better targeting our prevention strategies to adolescents and evaluating these efforts into the college years will aid in our understanding about the preventative effects of these interventions.
4.1.2.3. Varied teaching methods
Research indicates that preventative interventions are most successful when they include interactive instruction and opportunities for active, skills-based learning ( Nation et al., 2003 ). Prior reviews of sexual violence prevention programs also suggest that engaging participants in multiple ways (e.g., writing exercises, role plays) and with greater participation may be associated with more positive outcomes ( Paul & Gray, 2011 ). In the current review, nearly one-third of interventions utilized a single mode of intervention delivery (or teaching method) and another 40% utilized two modes of instruction. The most common modes of intervention delivery involved interactive presentations (i.e., presentations with opportunities for questions or discussion), didactic-only lectures, and/or videos. Only about one-third of the programs involved active participation in the form of role playing, skills practice, or other group activities. The effectiveness of program development efforts may be increased by focusing on integrating more active learning methods in order to increase the likelihood that participants acquire and retain skills and knowledge.
4.1.2.4. Sufficient dose
Prevention approaches must provide a sufficient “dose” of the intervention, as measured by total exposure to program content or contact hours, to have an effect on the behavior of participants ( Small et al., 2009 ). The intensity needed to be effective will vary by the type of approach, the needs and risk level of participants, and the nature of the targeted behavior, but longer programs may be more likely to achieve lasting results ( Nation et al., 2003 ). Our findings suggest that the dose received by participants is often small. Three-quarters of interventions had only one session, and half of all studies involved a total exposure of 1 h or less. While it may be possible to impact some behaviors with a brief, one-session strategy, it is likely that behaviors as complex as sexual violence will require a higher dosage to change behavior and have lasting effects. Indeed, we found that interventions with consistently positive effects in this review tended to be 2 to 3 times longer, on average, than interventions with null, negative, or mixed effects. Of course, there are practical limitations on the time and resources available to implement prevention strategies in most settings. The most efficient interventions would balance the necessity of providing a sufficient dose to achieve intended outcomes with the need for long-term sustainability and scalability. But, outcomes are critical: No matter how brief or low-cost an intervention may be, if it does not impact the outcomes of interest, implementation will not be an efficient or effective use of resources.
4.1.2.5. Fosters positive relationships
Strategies that foster positive relationships between participants and their parents, peers, or other adults have been associated with better outcomes in past prevention research ( Nation et al., 2003 ). Although the short length and didactic nature of most interventions reviewed here do not lend themselves well to relationship-building, strategies that work to nurture or capitalize on positive relationships are beginning to gain traction in the field. For example, programs that engage youth in facilitated peer support groups (e.g., Expect Respect; Ball et al., 2012 ) can leverage positive peer influences to reduce violent behavior. Further, strategies that train and empower youth to serve as active bystanders (e.g., Bringing in the Bystander; Banyard, Moynihan, & Plante, 2007 ; or, Green Dot; Cook-Craig et al., in press ) utilize existing peer networks to diffuse positive social norms and messages about dating and sexual violence. In addition, recent work to involve parents in dating violence prevention is a promising new direction (see for example, Families for Safe Dates ; Fo et al., 2012). Although these particular interventions have not yet demonstrated effects on sexual violence perpetration in a rigorous evaluation, research is ongoing, and the attention to the role of relationships in behavior modification and risk may prove fruitful.
4.1.2.6. Sociocultural relevance
Prevention programs that are sensitive to and reflective of community norms and cultural beliefs may be more successful in recruitment, retention, and achieving outcomes ( Nation et al., 2003 ; Small et al., 2009 ). Only three interventions were identified that included content designed for specific racial/ethnic groups, including Asian-Pacific Islander ( Stephens, 2008 ), African-American ( Weisz & Black, 2001 ) and Latino/a ( Nelson et al., 2010 ) populations. Fourteen studies (10% of the total) evaluated programs targeting fraternity men, male athletes, or members of the military. No studies evaluated programs targeting sexual minority populations. Overall, about two-thirds of the interventions reviewed were implemented with majority-White samples. Nation et al. (2003) note that involving members of the target population in the development and implementation of prevention strategies may improve the programs’ perceived relevance to the community’s needs. Future program development and evaluation research efforts should gauge the extent to which interventions with culturally specific approaches result in increased cultural relevance, recruitment, retention, and impact on preventing sexual violence.
4.1.2.7. Well-trained staff
Effective programs tend to have staff or implementers that are stable, committed, competent, and can connect effectively with participants ( Mihalic, Irwin, Fagan, Ballard, & Elliott, 2004 ). Sufficient “buy-in” to the program model is also important to credibly deliver and reinforce program messages ( Nation et al., 2003 ). Although researchers are increasingly recognizing the importance of measuring and describing characteristics of implementers and training procedures, few reports included this information. Reports were typically limited to a basic description of the type of implementer (e.g., peer, school staff, professional). About one-quarter of the interventions were implemented by professionals with expertise related to sexual violence prevention and extensive knowledge of the program model (e.g., program developers, sexual violence prevention practitioners). The majority of programs were implemented by peer facilitators, advanced students, or school/agency staff who may not have specific expertise in the topic. The sexual violence prevention field would benefit from more extensive descriptions of program staff and training and implementation research to determine characteristics of program staff that may enhance the preventative effects of our programs.
4.1.2.8. Theory-driven
A recent review by Paul and Gray (2011) concluded that sexual violence prevention strategies often lack a strong theoretical framework and fail to utilize established social psychological and behavior change research to inform program development. Etiological theories that identify modifiable points for intervention in the development of health risk behaviors are extremely valuable as a basis for prevention development ( Nation et al., 2003 ), especially when supported by evidence that the factors identified represent causal influences in a theoretical model. Although we did not systematically examine the theoretical underpinnings of interventions, attention to etiological theory (e.g., risk and protective factors and processes; Nation et al., 2003 ) was implicit in many studies with a focus on changing presumed sexual violence risk factors. The most common risk factors addressed were knowledge and attitudes about rape, women, and sex. There is limited empirical evidence linking legal or sexual knowledge to sexual violence perpetration ( Tharp, DeGue, et al., 2011 ) and virtually no theoretical reason to believe that rape is caused by a lack of awareness about laws prohibiting it. However, education about rape laws and statistics remains a frequent component of sexual violence prevention strategies. Attitudes are similarly attractive targets for intervention because they are relatively easy to measure and assess for change in the short-term. However, more empirical and theoretical work is needed to establish these factors as functional pieces in violence development rather than merely correlates or indicators and to provide well-developed, integrative theories to explain the role of attitudes and their potential value as primary prevention targets. On the other hand, cognitive factors, including hostility toward women, traditional gender role adherence, and hypermasculinity, have shown consistent links to sexual violence perpetration ( Tharp et al., 2013 ) but are rarely addressed directly in prevention programs. Strategies that involve working with young men to shape and support healthy views of masculinity and relationships, such as Men Can Stop Rape ( www.mencanstoprape.org ) or Coaching Boys into Men ( Miller et al., 2012b ), are promising exceptions, but more evaluation research is needed in order to ascertain whether these programs have an impact on sexual violence.
4.2. What works (and what doesn’t) to prevent sexual violence perpetration?
Emphasizing rigorous evaluation and behavioral outcomes, we developed and applied a set of criteria to identify specific interventions with more or less evidence of effectiveness for the primary prevention of sexual violence perpetration in order to serve as a guide for decision-making. Communities and organizations are increasingly interested in and required to implement evidence-based interventions with an expectation of achieving reductions in sexual violence. Table 3 is intended to serve as a resource and tool for this purpose. Although we believe that this approach has many practical advantages, it has notable limitations as well. Most importantly, it is limited by the ever-growing and evolving nature of the evaluation research literature. Over time, additional effective interventions will be identified, some will be found to be ineffective, and others will find that their effects can be replicated—or not—in different populations. The current review provides only a snapshot of knowledge regarding “what works” currently to prevent sexual violence. Practitioners are encouraged to consider this information in the context of the needs, goals, and resources of their organization and to supplement this summary with additional information about the strategy and new research findings as they become available. This summary may also be useful in identifying promising strategies in need of further research or when developing new comprehensive strategies that combine the strengths of multiple evidence-based approaches. Future research investments should reflect the best available science and theory, and move beyond approaches that have proven ineffective or insufficient.
4.2.1. What works (so far)?
Only three strategies, to date, have evidence of at least one positive effect on sexual violence perpetration behavior using a rigorous, controlled evaluation design. The best available evidence suggests that these strategies, if well-implemented with an appropriate population, may be effective in preventing sexually violent behavior. Notably, none of these evaluations have been replicated and it is not known whether their effects will generalize to other populations, age groups, or to forms of sexual violence that were not assessed. In addition, it is likely that none of these approaches, in isolation, will be sufficient to reduce rates of sexual violence at the population-level, even if brought “to scale” ( Dodge, 2009 ). Instead such approaches should be viewed as potential components of an evidence-based, comprehensive, multi-level strategy to combat sexual violence.
Safe Dates is a universal dating violence prevention program for middle- and high-school students involving a 10-session curriculum addressing attitudes, social norms, and healthy relationship skills, a 45-minute student play about dating violence, and a poster contest. Results from one rigorous evaluation using an RCT design showed that four years after receiving the program, students in the intervention group were significantly less likely to be victims or perpetrators of self-reported sexual violence involving a dating partner relative to students in the control group ( Foshee et al., 2004 ).
Shifting Boundaries is a universal, school-based dating violence prevention program for middle school students with two components: a 6-session classroom-based curriculum and a building-level intervention addressing policy and safety concerns in schools. Results from one rigorous evaluation indicated that the building-level intervention, but not the curriculum alone, was effective in reducing self-reported perpetration and victimization of sexual harassment and peer sexual violence, as well as sexual violence victimization (but not perpetration) by a dating partner ( Taylor et al., 2011 , 2013 ).
The U.S. Violence Against Women Act of 1994 (VAWA) aimed to increase the prosecution and penalties associated with sexual assault, stalking, intimate partner violence and other forms of violence against women, as well as to fund research, education and awareness programs, prevention activities, and victim services ( Boba & Lilley, 2009 ). Results of a rigorous, controlled quasi-experimental evaluation suggest that VAWA-related grant funding through the U.S. Department of Justice for criminal justice-related activities was associated with a .066% annual reduction in rapes reported to the police, as well as reductions in aggravated assault. Given the deficit of policy, environmental, or community-level change strategies with empirical, or even theoretical, evidence in this field ( DeGue, Holt, et al., 2012 ), communities and researchers may be able to learn from the programs and strategies funded by VAWA to inform development or implementation of similar approaches to prevent sexual violence.
4.2.2. What (probably) doesn’t work, or might be harmful?
This review identified five interventions with evidence of null effects on sexually violent behavior in at least one rigorous evaluation. It is notable that most of these programs have shown positive effects on other related outcomes, including potential risk factors or moderators. In some cases, positive effects on behavioral outcomes were identified using non-rigorous evaluation designs. Additional research that evaluates these strategies with different measures of sexual violence perpetration, stronger implementation, different populations, longer follow-up periods, or larger sample sizes may possibly reveal positive effects on behavior. However, the most rigorous evidence currently available suggests that these strategies have so far not been effective in changing rates of sexual violence perpetration after a reasonable follow-up period.
Three interventions were identified as having potentially harmful effects on sexual violence behavioral outcomes in at least one rigorous evaluation. Interestingly, all three interventions included content utilized in other programs that were classified as not effective in this review (i.e., The Men’s Program, Foubert, 2000 ; Shifting Boundaries classroom-based curriculum, Taylor et al., 2011 ). It is possible that these negative outcomes reflect increased awareness and enhanced reporting in the intervention group, as suggested by some authors (e.g., Taylor et al., 2011 ). Alternatively, the findings might indicate that respondents had an adverse reaction to the content. More research is needed to understand why these interventions are not working as intended with their target populations. In the absence of additional research, practitioners may wish to select other strategies without evidence of potentially iatrogenic effects.
Importantly, based on the criteria applied here, interventions could only be identified as effective, ineffective, or potentially harmful when they were subjected to rigorous evaluation measuring sexually violent behavior. However, the vast majority of interventions evaluated in the last three decades did not utilize rigorous designs with behavioral outcome measures. It is possible that many, if not most, of the interventions identified as having insufficient evidence or being in need of more research would not prove effective if rigorously evaluated. Most of the programs reviewed were brief, one-session psycho-educational programs conducted with college students. The development and implementation of brief education and awareness programs has served as an important stepping stone for the field — arguably increasing administrators’ and students’ awareness and knowledge of sexual violence and sexual violence prevention. However, none of these programs have provided consistent evidence of impact on sexual violence outcomes, and most have not shown evidence of lasting impact on the risk factors or related outcomes that were measured. Thus, we join others in the field (e.g., Casey & Lindhorst, 2009 ) in calling for a paradigm shift in sexual violence prevention that moves us away from low-dose educational programming in adulthood and toward investment in the development and rigorous evaluation of more comprehensive, multi-level strategies (e.g., those that include individuals, parents, and peers) that target younger populations and seek to modify community and contextual supports for violence.
4.2.3. What else might work to prevent sexual violence?
Ten interventions had positive or mixed effects on risk factors for sexual violence or related outcomes in a rigorous evaluation. Although these initial findings are positive and promising, we do not know whether change in these risk characteristics will result in actual reductions in sexual violence perpetration behavior; additional rigorous evaluation on sexual violence behavioral outcomes would be needed to examine those effects. Studies that found consistently positive effects on sexual violence outcomes in a non-rigorous evaluation also met criteria for consideration in this category—but none were identified.
When determining whether strategies in this category should be considered for implementation in communities or further research investments, the prevention principles outlined above may serve as a useful guide. Researchers and practitioners should consider whether a strategy’s content, delivery method, dose, target audience, and theoretical base are consistent with lessons learned from the sexual violence and general prevention literatures. Based on their prevention approach and initial evidence from large RCTs with longer follow-up periods, Coaching Boys Into Men ( Miller et al., 2012b ) and Bringing in the Bystander ( Banyard et al., 2007 ), for example, stand out as two strategies with substantial potential for impacting sexually violent behavior if subjected to rigorous evaluation on these outcomes. Coaching Boys Into Men is based on social norms theory and utilizes high school coaches to engage male athletes in 11 brief, structured discussions about dating violence through the sports season. At one-year follow-up the program showed positive effects on a general measure of dating violence perpetration, but effects on sexual violence specifically were not measured ( Miller et al., 2012b ). Bringing in the Bystander is a bystander education and training program that aims to engage participants as potential witnesses to violence (rather than as perpetrators or victims) and provides them with skills to help when they see behavior that puts others at risk, including speaking out against rape myths and sexist language, supporting victims, and intervening in potentially violent situations. Some positive effects were found across studies on risk factors for sexual violence; sexual violence behavioral outcomes have not yet been examined ( Banyard et al., 2007 ). Although more research is needed, the bystander approach to prevention is already gaining traction in the field. Other programs using a bystander engagement approach, such as Green Dot ( Cook-Craig et al., in press ), are also being evaluated but the findings have not yet been published.
4.3. Moving forward: gaps and priorities for progress
There have been substantial gains in the field of sexual violence prevention over the last 30 years with regard to public education and awareness, legal protections for victims, federal funding and infrastructure for prevention work, community mobilization, and research on the prevalence, etiology, and prevention of sexual violence. But important gaps remain, hindering progress toward the ultimate goal of reducing sexual violence at the population level. Rates of sexual violence remain alarmingly high, and we still know very little about how to prevent it.
The field’s ability to identify effective strategies for sexual violence perpetration is severely constrained by the quality of the available research. Without more rigorous research designs that examine the primary behavioral outcomes of interest, it is not possible to determine with sufficient confidence whether a strategy is likely to have the desired outcomes or be cost-effective. Evaluation research need not always involve an RCT; other rigorous quasi-experimental designs, such as regression discontinuity or interrupted time series, may be the most practical options for evaluating policy or environmental strategies, for example. In contrast, less rigorous designs, such as pre–post studies, may be the best approach for formative research to develop and refine strategies. Likewise, measurement of risk characteristics provides important information about potential mediators and moderators of effectiveness, but without identification of true causal risk factors, these outcomes cannot tell us whether or not a program “works.” Thus, measurement of key behavioral outcomes, including perpetration behavior, is a critical component of rigorous effectiveness research. Of course, the use of RCTs and behavioral measures represent only the minimum criteria necessary to allow for causal inferences from the data; these design features alone do not ensure that a study is well-conducted or reliable. Additional factors, such as sample size and retention, measurement validity, group equivalence, and appropriate data analysis, are also important in determining whether study findings represent valid evidence of effectiveness ( Coalition for Evidence-Based Policy, 2010 ). Thus, a critical priority for the field to ensure the growing availability of effective, evidence-based prevention strategies for sexual violence involves improving study rigor. The limited available resources for prevention should be directed toward methodologies most likely to advance practical knowledge of what works.
There is also a need in the field to consider not only statistical significance, but also the magnitude or clinical significance of any effects identified. If a strategy is widely implemented, even a small effect on perpetration behavior may have a large impact. However, a small effect on an attitudinal or knowledge outcome, for example, may not have any practical value. One limitation of this review is that we examined this field as it is — categorizing outcomes by the direction of effect rather than by the size of the effect. The broad scope of the current review and the wide variability in the quality and design of included studies made meta-analytic techniques impractical. However, prior meta-analyses conducted with smaller subsets of the literature have found relatively small effects, especially on the most direct or proximal outcomes ( Anderson & Whiston, 2005 ; Brecklin & Forde, 2001 ; Flores & Hartlaub, 1998 ). As noted by these prior reviews ( Breitenbecher, 2000 ; Schewe & O’Donohue, 1993 ), more attention to issues of clinical significance is needed within the sexual violence evaluation literature to better understand the value and potential impact of specific strategies when applied at the population-level.
The lack of effective prevention strategies for sexual violence is due not only to a lack of rigorous evaluation to identify those effects but also to the nature and quality of the approaches being developed and evaluated. A key conclusion from this review is that a large portion of research (and, presumably, programmatic) resources, to date, have been invested in brief psycho-educational strategies that are not consistent with the principles of prevention and have not demonstrated effectiveness despite numerous evaluations. Prevention strategies based in a coherent theory of change with a plausible likelihood for impact on sexual violence perpetration and addressing a broader range of risk and protective factors for sexual violence may be more likely to be effective. With most of the attention in existing programs focused on knowledge and attitudes, many sexual violence risk factors—well-grounded in theory—have been ignored. For example, childhood exposure to violence, general delinquency and aggression, and early sexual behavior have consistent empirical support across numerous studies and are included in the Confluence Model, a well-supported theoretical model of sexual violence perpetration, but they are rarely addressed in sexual violence prevention efforts ( Tharp et al., 2013 ). Explicit attention to an expanded range of risk factors in intervention development and a broader set of behavior change theories, such as those identified by Paul and Gray (2011) , may result in more integrative and effective models of prevention.
The lack of community- and societal-level prevention approaches for sexual violence perpetration also remains a critical gap in this field. The social–ecological model ( Bronfenbrenner, 1977 ) conceptualizes violence as a product of multiple, interacting levels of influence at the individual, relationship, community, and societal levels of the social ecology. Most prevention strategies evaluated thus far have focused solely or primarily on creating change at the individual level, with a few also addressing peer influences or small-scale social norms change through bystander intervention or school poster campaigns. Individual-and relationship-based approaches are likely key pieces of the prevention puzzle given the plethora of risk correlates identified at these levels. But, achieving long-term behavior change with such programs is unlikely when they are delivered in a social, cultural, or physical environment that counteracts those messages and discourages safe, healthy behaviors or rewards violent behavior ( DeGue, Holt, et al., 2012 ). This would necessitate drawing on theory and lessons learned in other areas of public health to identify innovative policy, environmental, and structural approaches that support and encourage healthy behavior, positive social norms, and non-violence. Such strategies would target modifiable risk and protective factors that are characteristic of communities and that are empirically or theoretically associated with sexual violence (e.g., neighborhood disorganization, availability of alcohol; Casey & Lindhorst, 2009 ; DeGue, Massetti, et al., 2012 ; Tharp et al., 2013 ). In late 2013, CDC released a funding opportunity announcement to encourage innovation in this area by providing potential funding for the rigorous evaluation of such an approach (See RFA-CE-14-005 on www.grants.gov ). More work is needed to develop and identify community-level measures, indicators, or proxies of sexual violence beyond law enforcement record data for use in evaluating these outer-level approaches ( DeGue, Holt, et al., 2012 ).
Continued progress is needed toward the development and rigorous evaluation of effective, comprehensive, theory-based primary prevention strategies for sexual violence perpetration that address risk and protective factors at multiple levels of the social ecology. This progress is dependent on the innovation and methodological expertise of sexual violence researchers and program developers, well-directed research funding, and support from prevention professionals implementing these strategies in the field. Sexual violence is a complex problem with social, structural, cultural, and individual roots. By designing prevention efforts that are equally complex, multifaceted, and embedded within our lives and environments we can enhance their effectiveness. With increasing pressure to demonstrate effectiveness and economic efficiency, stronger evidence of impact will be required to justify investments in evidence-based primary prevention strategies. Thus, further investment in rigorous evaluation research is critical to ensuring sustained movement toward the identification of evidence-based strategies for the prevention of sexually violent behavior. Such research should focus on comprehensive, theory-based strategies across levels of the social ecology and build on the best available research evidence to identify a complement of effective approaches for implementation and move us closer to ending sexual violence in communities.

Supplementary Material
Supplemental materials: appendix a, appendix a. supplementary materials.
Supplementary data to this article can be found online at http://dx.doi.org/10.1016/j.avb.2014.05.004 .
2 Sexual violence is defined as any nonconsensual sexual act committed or attempted against someone, including forced or alcohol/drug facilitated penetration of a victim; or used to facilitate making the victim penetrate a perpetrator or someone else; nonphysically pressured unwanted penetration; intentional sexual touching and non-contact sexual acts ( Basile, Smith, Breiding, Black, & Mahendra, in press ).
3 A recent Special Issue of Violence Against Women (March 2014, Vol 20) addressed current research and theory related to self-defense approaches to sexual violence victimization prevention: http://vaw.sagepub.com/content/20/3.toc .
4 The start date of 1985 was chosen to capture the 25-year period prior to the initial intended end date of 2010. The review was later extended through May 2012 to capture the most recent evaluation studies at that time.
5 A copy of the coding sheet is available from the first author upon request.
6 Studies were coded as measuring sexual violence behavioral outcomes if they utilized: a) rates of sexual violence victimization or perpetration based on official records (e.g., police or hospital data), or b) self-reported sexual violence victimization or perpetration assessed via survey, including the range of abusive contact and non-contact behaviors falling within the CDC’s definition of sexual violence ( Basile et al., in press ).
7 Four of the five clinical trials cited here were funded by CDC’s Division of Violence Prevention. The evaluation of Shifting Boundaries (cite) was funded by the National Institutes of Justice.
☆ The findings and conclusions in this report are those of the authors and do not necessarily represent the official position of the Centers for Disease Control and Prevention.
- Abbey A, McAuslan P. A longitudinal examination of male college students’ perpetration of sexual assault. Journal of Consulting and Clinical Psychology. 2004; 72 (5):747. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Anderson LA, Whiston SC. Sexual assault education programs: a meta-analytic examination of their effectiveness. Psychology of Women Quarterly. 2005; 29 (4):374–388. [ Google Scholar ]
- Backes BL. Building a solid foundation for sexual violence research applying lessons learned to inform research priorities. Violence Against Women. 2013; 19 (6):737–755. [ PubMed ] [ Google Scholar ]
- Ball B, Tharp AT, Noonan RK, Valle LA, Hamburger ME, Rosenbluth B. Expect respect support groups: preliminary evaluation of a dating violence prevention program for at-risk youth. Violence Against Women. 2012; 18 (7):746–762. http://dx.doi.org/10.1177/1077801212455188 . [ PubMed ] [ Google Scholar ]
- Banyard VL, Moynihan MM, Plante EG. Sexual violence prevention through bystander education: an experimental evaluation. Journal of Community Psychology. 2007; 35 (4):463–481. [ Google Scholar ]
- Basile KC, Smith S, Breiding M, Black M, Mahendra R. Sexual violence surveillance: uniform definitions and recommended data elements, version 2.0. Atlanta, GA: Centers for Disease Control and Prevention (CDC); 2014s. (in press) [ Google Scholar ]
- Beardall NG. US: 69, ProQuest Information & Learning. 2008. A program evaluation research study on the implementation of the mentors in violence prevention program in a public high school. [ Google Scholar ]
- Black MC, Basile KC, Breiding MJ, Smith SG, Walters ML, Merrick MT, et al. National intimate partner and sexual violence survey. Atlanta, GA: CDC. Centers for Disease Control and Prevention; 2011. [ Google Scholar ]
- Boba R, Lilley D. Violence against women act (VAWA) funding: a nationwide assessment of effects on rape and assault. Violence Against Women. 2009; 15 (2):168–185. http://dx.doi.org/10.1177/1077801208329146 . [ PubMed ] [ Google Scholar ]
- Borges AM, Banyard VL, Moynihan MM. Clarifying consent: primary prevention of sexual assault on a college campus. Journal of Prevention & Intervention in the Community. 2008; 36 (1–2):75–88. [ PubMed ] [ Google Scholar ]
- Brecklin LR, Forde DR. A meta-analysis of rape education programs. Violence and Victims. 2001; 16 (3):303–321. [ PubMed ] [ Google Scholar ]
- Breitenbecher KH. Sexual assault on college campuses: is an ounce of prevention enough? Applied and Preventive Psychology. 2000; 9 (1):23–52. [ Google Scholar ]
- Briss PA, Zaza S, Pappaioanou M, Fielding J, Wright-De Agüero L, Truman BI, et al. Developing an evidence-based guide to community preventive services-methods. American Journal of Preventive Medicine. 2000; 18 (1, Supplement 1):35–43. http://dx.doi.org/10.1016/S0749-3797(99)00119-1 . [ PubMed ] [ Google Scholar ]
- Bronfenbrenner U. Toward an experimental ecology of human development. American Psychologist. 1977; 32 (7):513. [ Google Scholar ]
- Carmody M, Carrington K. Preventing sexual violence? Australian and New Zealand Journal of Criminology. 2000; 33 (3):341–361. [ Google Scholar ]
- Casey EA, Lindhorst TP. Toward a multi-level, ecological approach to the primary prevention of sexual assault prevention in peer and community contexts. Trauma, Violence & Abuse. 2009; 10 (2):91–114. [ PubMed ] [ Google Scholar ]
- Centers for Disease Control and Prevention. Sexual violence prevention: beginning the dialogue. Atlanta, GA: Centers for Disease Control and Prevention; 2004. [ Google Scholar ]
- Centers for Disease Control and Prevention. A review of the sexual violence prevention portfolio at CDC’s division of violence prevention, 2000–2010 (for internal use only) GA: Atlanta: 2012. [ Google Scholar ]
- Coalition for Evidence-Based Policy. Checklist for reviewing a randomized controlled trial of a social program or project, to assess whether it produced valid evidence. 2010 Retrieved from. http://coalition4evidence.org/468-2/publications/
- Cook-Craig PG, Coker AL, Clear ER, Garcia LS, Bush HM, Brancato CJ, et al. Challenge and opportunity in evaluating a diffusion based active bystanding prevention program: green dot in high schools. Violence Against Women. 2014s (in press) [ PubMed ] [ Google Scholar ]
- Cox PJ, Ortega S, Cook-Craig PG, Conway P. Strengthening systems for the primary prevention of intimate partner violence and sexual violence: CDC’s delta and empower programs. Journal of Family Social Work. 2010; 13 (4):287–296. [ Google Scholar ]
- DeGue S, Holt MK, Massetti GM, Matjasko JL, Tharp AT, Valle LA. Looking ahead toward community-level strategies to prevent sexual violence. Journal of Women’s Health. 2012; 21 (1):1–3. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- DeGue S, Massetti GM, Holt MK, Tharp AT, Valle LA, Matjasko JL, et al. Identifying links between sexual violence and youth violence perpetration: new opportunities for sexual violence prevention 2012 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- DeGue S, Simon TR, Basile KC, Yee SL, Lang K, Spivak H. Moving forward by looking back: reflecting on a decade of CDC’s work in sexual violence prevention, 2000–2010. Journal of Women’s Health. 2012; 21 (12):1211–1218. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Dodge KA. Community intervention and public policy in the prevention of antisocial behavior. Journal of Child Psychology and Psychiatry. 2009; 50 (1–2):194–200. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Duggan LM. US: 59, ProQuest Information & Learning. 1998. The effectiveness of an acquaintance sexual assault prevention program in changing attitudes/beliefs and behavioral intent among college students. [ Google Scholar ]
- Eccles M, Grimshaw J, Campbell M, Ramsay C. Research designs for studies evaluating the effectiveness of change and improvement strategies. Quality and Safety in Health Care. 2003; 12 (1):47–52. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Echols KL. PhD. Tuscaloosa: University of Alabama; 1998. Dating relationships and sexual victimization: an intervention program with college freshman males. [ Google Scholar ]
- Espelage DL, Low S, Polanin JR, Brown EC. The impact of a middle school program to reduce aggression, victimization, and sexual violence. Journal of Adolescent Health. 2013; 53 (2):180–186. [ PubMed ] [ Google Scholar ]
- Fay KE, Medway FJ. An acquaintance rape education program for students transitioning to high school. Sex Education. 2006; 6 (3):223–236. [ Google Scholar ]
- Feltey KM, Ainslie JJ, Geib A. Sexual coercion attitudes among high school students: the influence of gender and rape education. Youth & Society. 1991; 23 (2):229–250. [ Google Scholar ]
- Fischhoff B, Furby L, Morgan M. Rape prevention: a typology of strategies. Journal of Interpersonal Violence. 1987; 2 (3):292–308. [ Google Scholar ]
- Flay BR, Biglan A, Boruch RF, Castro FG, Gottfredson D, Kellam S, et al. Standards of evidence: criteria for efficacy, effectiveness and dissemination. Prevention Science. 2005; 6 (3):151–175. [ PubMed ] [ Google Scholar ]
- Flores SA, Hartlaub MG. Reducing rape-myth acceptance in male college students: a meta-analysis of intervention studies. Journal of College Student Development. 1998; 39 (5):438–448. [ Google Scholar ]
- Fonow M. Feminist rape education: does it work? Gender & Society. 1992; 6 (1):108–121. [ Google Scholar ]
- Foshee V, Bauman KE, Arriaga XB, Helms RW, Koch GG, Linder GF. An evaluation of safe dates, an adolescent dating violence prevention program. American Journal of Public Health. 1998; 88 (1):45–50. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Foshee VA, Bauman KE, Ennett ST, Linder GF, Benefield T, Suchindran C. Assessing the long-term effects of the safe dates program and a booster in preventing and reducing adolescent dating violence victimization and perpetration. American Journal of Public Health. 2004; 94 (4):619–624. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Foshee VA, Bauman KE, Ennett ST, Suchindran C, Benefield T, Linder GF. Assessing the effects of the dating violence prevention program “safe dates” using random coefficient regression modeling. Prevention Science. 2005; 6 (3):245–258. [ PubMed ] [ Google Scholar ]
- Foshee VA, Bauman KE, Greene WF, Koch GG, Linder GF, MacDougall JE. The safe dates program: 1-year follow-up results. American Journal of Public Health. 2000; 90 (10):1619–1622. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Foshee VA, McNaughton Reyes HL, Ennett ST, Cance JD, Bauman KE, Bowling JM. Assessing the effects of families for safe dates, a family-based teen dating abuse prevention program. Journal of Adolescent Health. 2012; 51 (4):349–356. [ PubMed ] [ Google Scholar ]
- Foubert JD. The longitudinal effects of a rape-prevention program on fraternity men’s attitudes, behavioral intent, and behavior. Journal of American College Health. 2000; 48 (4):158–163. [ PubMed ] [ Google Scholar ]
- Foubert J, Marriott K. Effects of a sexual assault peer education program on men’s belief in rape myths. Sex Roles. 1997; 36 (3):259–268. [ Google Scholar ]
- Foubert JD, McEwen MK. An all-male rape prevention peer education program: decreasing fraternity men’s behavioral intent to rape. Journal of College Student Development. 1998; 39 (6):548–556. [ Google Scholar ]
- Foubert JD, Newberry JT. Effects of two versions of an empathy-based rape prevention program on fraternity men’s survivor empathy, attitudes, and behavioral intent to commit rape or sexual assault. Journal of College Student Development. 2006; 47 (2):133–148. [ Google Scholar ]
- Foubert JD, Newberry JT, Tatum J. Behavior differences seven months later: effects of a rape prevention program. NASPA Journal. 2007; 44 (4):728–749. [ Google Scholar ]
- Gidycz CA, Layman MJ, Rich CL, Crothers M, Gylys J, Matorin A, et al. An evaluation of an acquaintance rape prevention program: impact on attitudes, sexual aggression, and sexual victimization. Journal of Interpersonal Violence. 2001; 16 (11):1120–1138. [ Google Scholar ]
- Gidycz CA, Orchowski LM, Berkowitz AD. Preventing sexual aggression among college men: an evaluation of a social norms and bystander intervention program. Violence Against Women. 2011; 17 (6):720–742. http://dx.doi.org/10.1177/1077801211409727 . [ PubMed ] [ Google Scholar ]
- Glasman LR, Albarracín D. Forming attitudes that predict future behavior: a meta-analysis of the attitude–behavior relation. Psychological Bulletin. 2006; 132 (5):778. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Heppner MJ, Humphrey CF, Hillenbrand-Gunn TL, DeBord KA. The differential effects of rape prevention programming on attitudes, behavior, and knowledge. Journal of Counseling Psychology. 1995; 42 (4):508–518. [ Google Scholar ]
- Hillenbrand-Gunn TL, Heppner MJ, Mauch PA, Park H. Men as allies: the efficacy of a high school rape prevention intervention. Journal of Counseling & Development. 2010; 88 (1):43–51. [ Google Scholar ]
- Intons-Peterson MJ, Roskos-Ewoldsen B, Thomas L, Shirley M, Blut D. Will educational materials reduce negative effects of exposure to sexual violence? Journal of Social and Clinical Psychology. 1989; 8 (3):256–275. [ Google Scholar ]
- Johansson-Love J, Geer JH. Investigation of attitude change in a rape prevention program. Journal of Interpersonal Violence. 2003; 18 (1):84–99. http://dx.doi.org/10.1177/0886260502238542 . [ Google Scholar ]
- Jordan CE. Advancing the study of violence against women evolving research agendas into science. Violence Against Women. 2009; 15 (4):393–419. [ PubMed ] [ Google Scholar ]
- Koss MP. Empirically enhanced reflections on 20 years of rape research. Journal of Interpersonal Violence. 2005; 20 (1):100–107. [ PubMed ] [ Google Scholar ]
- Kraus SJ. Attitudes and the prediction of behavior: a meta-analysis of the empirical literature. Personality and Social Psychology Bulletin. 1995; 21 (1):58–75. [ Google Scholar ]
- Krug E, Dahlberg L, Mercy J, Zwi A, Lozano R. World health report on violence and health. Geneva: World Health Organization; 2002. [ Google Scholar ]
- Langhinrichsen-Rohling J, Foubert JD, Brasfield HM, Hill B, Shelley-Tremblay S. The men’s program: does it impact college men’s self-reported bystander efficacy and willingness to intervene? Violence Against Women. 2011; 17 (6):743–759. [ PubMed ] [ Google Scholar ]
- Lenihan G. Gender differences in rape supportive attitudes before and after a date rape education intervention. Journal of College Student Development. 1992; 33 (4):331–338. [ Google Scholar ]
- McLeod PA. PhD. Columbia: University of South Carolina; 1997. The impact of rape education on rape attributions and attitudes: comparison of a feminist intervention and a miscommunication model intervention. [ Google Scholar ]
- McMahon PM. The public health approach to the prevention of sexual violence. Sexual Abuse: A Journal of Research and Treatment. 2000; 12 (1):27–36. http://dx.doi.org/10.1177/107906320001200104 . [ PubMed ] [ Google Scholar ]
- Meraviglia MG, Becker H, Rosenbluth B, Sanchez E, Robertson T. The expect respect project: creating a positive elementary school climate. Journal of Interpersonal Violence. 2003; 18 (11):1347–1360. http://dx.doi.org/10.1177/0886260503257457 . [ PubMed ] [ Google Scholar ]
- Mihalic SF, Irwin K, Fagan A, Ballard D, Elliott D. Successful program implementation: lessons from blueprints. US Department of Justice, Office of Justice Programs, Office of Juvenile Justice and Delinquency Prevention; 2004. [ Google Scholar ]
- Miller E, Tancredi DJ, McCauley HL, Decker MR, Virata MCD, Anderson HA, et al. “Coaching boys into men”: a cluster-randomized controlled trial of a dating violence prevention program. Journal of Adolescent Health. 2012a; 51 (5):431–438. [ PubMed ] [ Google Scholar ]
- Miller E, Tancredi DJ, McCauley HL, Decker MR, Virata MCD, Anderson HA, et al. “Coaching boys into men”: a cluster-randomized controlled trial of a dating violence prevention program. Journal of Adolescent Health. 2012b; 51 (5):431–438. [ PubMed ] [ Google Scholar ]
- Miller E, Tancredi DJ, McCauley HL, Decker MR, Virata MCD, Anderson HA, et al. One-year follow-up of a coach-delivered dating violence prevention program: a cluster randomized controlled trial. American Journal of Preventive Medicine. 2013; 45 (1):108–112. [ PubMed ] [ Google Scholar ]
- Moynihan MM, Banyard VL, Arnold JS, Eckstein RP, Stapleton JG. Engaging intercollegiate athletes in preventing and intervening in sexual and intimate partner violence. Journal of American College Health. 2010; 59 (3):197–204. [ PubMed ] [ Google Scholar ]
- Murphy DK. Unpublished doctoral dissertation. Ball State University; Muncie, Indiana: 1997. Date rape prevention programs: Effects on college students’ attitudes. [ Google Scholar ]
- Nation M, Crusto C, Wandersman A, Kumpfer KL, Seybolt D, Morrissey-Kane E, et al. What works in prevention: principles of effective prevention programs. American Psychologist. 2003; 58 (6–7):449. [ PubMed ] [ Google Scholar ]
- Nelson A, Lewy R, Ricardo F, Dovydaitis T, Hunter A, Mitchell A, et al. Eliciting behavior change in a US sexual violence and intimate partner violence prevention program through utilization of Freire and discussion facilitation. Health Promotion International. 2010; 25 (3):299–308. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Nelson ES, Torgler CC. A comparison of strategies for changing college students’ attitudes toward acquaintance rape. Journal of Humanistic Education and Development. 1990; 29 :69–85. [ Google Scholar ]
- Office of Management and Budget. Memorandum to the heads of executive departments and agencies, m-12–14. 2012 Retrieved from. http://www.whitehouse.gov/sites/default/files/omb/memoranda/2012/m-12-14.pdf .
- Paul LA, Gray MJ. Sexual assault programming on college campuses: using social psychological belief and behavior change principles to improve outcomes. Trauma, Violence & Abuse. 2011; 12 (2):99–109. [ PubMed ] [ Google Scholar ]
- Pinzone-Glover HA, Gidycz CA, Jacobs CD. An acquaintance rape prevention program. Psychology of Women Quarterly. 1998; 22 (4):605–621. [ Google Scholar ]
- Post LA, Klevens J, Maxwell CD, Shelley GA, Ingram E. An examination of whether coordinated community responses affect intimate partner violence. Journal of Interpersonal Violence. 2010; 25 (1):75–93. [ PubMed ] [ Google Scholar ]
- Potter SJ, Moynihan MM. Bringing in the bystander in-person prevention program to a us military installation: results from a pilot study. Military Medicine. 2011; 176 (8):870–875. [ PubMed ] [ Google Scholar ]
- Sanchez E, Robertson TR, Lewis CM, Rosenbluth B, Bohman T, Casey DM. Preventing bullying and sexual harassment in elementary schools: the expect respect model. Journal of Emotional Abuse. 2001; 2 (2–3):157–180. http://dx.doi.org/10.1300/J135v02n02_10 . [ Google Scholar ]
- Saul J, Duffy J, Noonan R, Lubell K, Wandersman A, Flaspohler P, et al. Bridging science and practice in violence prevention: addressing ten key challenges. American Journal of Community Psychology. 2008; 41 (3–4):197–205. [ PubMed ] [ Google Scholar ]
- Saul J, Wandersman A, Flaspohler P, Duffy J, Lubell K, Noonan R. Research and action for bridging science and practice in prevention. American Journal of Community Psychology. 2008; 41 (3–4):165–170. [ PubMed ] [ Google Scholar ]
- Schewe P, O’Donohue W. Rape prevention: methodological problems and new directions. Clinical Psychology Review. 1993; 13 (7):667–682. [ Google Scholar ]
- Schewe P, O’Donohue W. Rape prevention with high-risk males: short-term outcome of two interventions. Archives of Sexual Behavior. 1996; 25 (5):455–471. [ PubMed ] [ Google Scholar ]
- Shadish WR, Cook TD, Campbell DT. Experimental and quasi-experimental designs for generalized causal inference 2002 [ Google Scholar ]
- Small SA, Cooney SM, O’Connor C. Evidence-informed program improvement: using principles of effectiveness to enhance the quality and impact of family-based prevention programs. Family Relations. 2009; 58 (1):1–13. [ Google Scholar ]
- Stephens K. Unpublished doctoral dissertation. University of Washington; Washington: 2008. Rape prevention with Asian/Pacific Islander and Caucasian college men: The roles of culture and risk status. [ Google Scholar ]
- Stephens KA, George WH. Rape prevention with college men: evaluating risk status. Journal of Interpersonal Violence. 2009; 24 (6):996–1013. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Taylor B, Stein N, Burden F. The effects of gender violence/harassment prevention programming in middle schools: a randomized experimental evaluation. Violence and Victims. 2010a; 25 (2):202–223. [ PubMed ] [ Google Scholar ]
- Taylor BG, Stein N, Burden FF. Exploring gender differences in dating violence/harassment prevention programming in middle schools: results from a randomized experiment. Journal of Experimental Criminology. 2010b; 6 (4):419–445. [ Google Scholar ]
- Taylor BG, Stein ND, Mumford EA, Woods D. Shifting boundaries: an experimental evaluation of a dating violence prevention program in middle schools. Prevention Science. 2013; 14 (1):64–76. [ PubMed ] [ Google Scholar ]
- Taylor B, Stein N, Woods D, Mumford E, Forum PER. Shifting boundaries: final report on an experimental evaluation of a youth dating violence prevention program in New York City middle schools 2011 [ PubMed ] [ Google Scholar ]
- Tharp AT, Burton T, Freire K, Hall DM, Harrier S, Latzman NE, et al. Dating matters ™ : strategies to promote healthy teen relationships. Journal of Women’s Health. 2011; 20 (12):1761–1765. [ PubMed ] [ Google Scholar ]
- Tharp AT, DeGue S, Lang K, Valle LA, Massetti G, Holt M, et al. Commentary on Foubert, Godin, & Tatum (2010) the evolution of sexual violence prevention and the urgency for effectiveness. Journal of Interpersonal Violence. 2011; 26 (16):3383–3392. [ PubMed ] [ Google Scholar ]
- Tharp AT, DeGue S, Valle LA, Brookmeyer KA, Massetti GM, Matjasko JL. A systematic qualitative review of risk and protective factors for sexual violence perpetration. Trauma, Violence & Abuse. 2013; 14 (2):133–167. [ PubMed ] [ Google Scholar ]
- Tseng V. Society for Research in Child Development. 2012. The uses of research in policy and practice. [ Google Scholar ]
- Vladutiu CJ, Martin SL, Macy RJ. College-or university-based sexual assault prevention programs: a review of program outcomes, characteristics, and recommendations. Trauma, Violence & Abuse. 2011; 12 (2):67–86. [ PubMed ] [ Google Scholar ]
- Weisz AN, Black BM. Evaluating a sexual assault and dating violence prevention program for urban youths. Social Work Research. 2001; 25 (2):89–102. [ Google Scholar ]
- Whitaker DJ, Murphy CM, Eckhardt CI, Hodges AE, Cowart M. Effectiveness of primary prevention efforts for intimate partner violence. Partner Abuse. 2013; 4 (2):175–195. http://dx.doi.org/10.1891/1946-6560.4.2.175 . [ Google Scholar ]
- World Health Organization/London School of Hygiene and Tropical Medicine. Preventing intimate partner and sexual violence against women: taking action and generating evidence. Geneva: World Health Organization; 2010. [ Google Scholar ]
- Wright V. The community awareness rape education (care) program for high school students. Journal of Emergency Nursing. 2000; 26 (2):182–185. [ PubMed ] [ Google Scholar ]
Fast Facts: Preventing Sexual Violence

Sexual violence is sexual activity when consent is not obtained or freely given. It is a serious public health problem in the United States that profoundly impacts lifelong health, opportunity, and well-being. Sexual violence impacts every community and affects people of all genders, sexual orientations, and ages. Anyone can experience or perpetrate sexual violence. The perpetrator of sexual violence is usually someone the survivor knows, such as a friend, current or former intimate partner, coworker, neighbor, or family member. Sexual violence can occur in person, online, or through technology, such as posting or sharing sexual pictures of someone without their consent, or non-consensual sexting.
For more information about sexual violence definitions please see Sexual Violence Surveillance: Uniform Definitions and Recommended Data Elements, Version 2.0 [2.01 MB, 136 Pages, 508] .
For information about child sexual abuse, please see Preventing Child Sexual Abuse .
Sexual violence affects millions of people each year in the United States. Researchers know the numbers underestimate this problem because many cases are unreported. Survivors may be ashamed, embarrassed, or afraid to tell the police, friends, or family about the violence. Victims may also keep quiet because they have been threatened with further harm if they tell anyone or do not think anyone will help them. The data shows:
- Sexual violence is common. Over half of women and almost 1 in 3 men have experienced sexual violence involving physical contact during their lifetimes. One in 4 women and about 1 in 26 men have experienced completed or attempted rape. About 1 in 9 men were made to penetrate someone during his lifetime. Additionally, 1 in 3 women and about 1 in 9 men experienced sexual harassment in a public place.
- Sexual violence starts early. More than 4 in 5 female rape survivors reported that they were first raped before age 25 and almost half were first raped as a minor (i.e., before age 18). Nearly 8 in 10 male rape survivors reported that they were made to penetrate someone before age 25 and about 4 in 10 were first made to penetrate as a minor.
- Sexual violence disproportionately affects some groups. Women and racial and ethnic minority groups experience a higher burden of sexual violence. For example, more than 2 in 5 non-Hispanic American Indian or Alaska Native and non-Hispanic multiracial women were raped in their lifetime.
- Sexual violence is costly. Recent estimates put the lifetime cost of rape at $122,461 per survivor, including medical costs, lost productivity, criminal justice activities, and other costs.
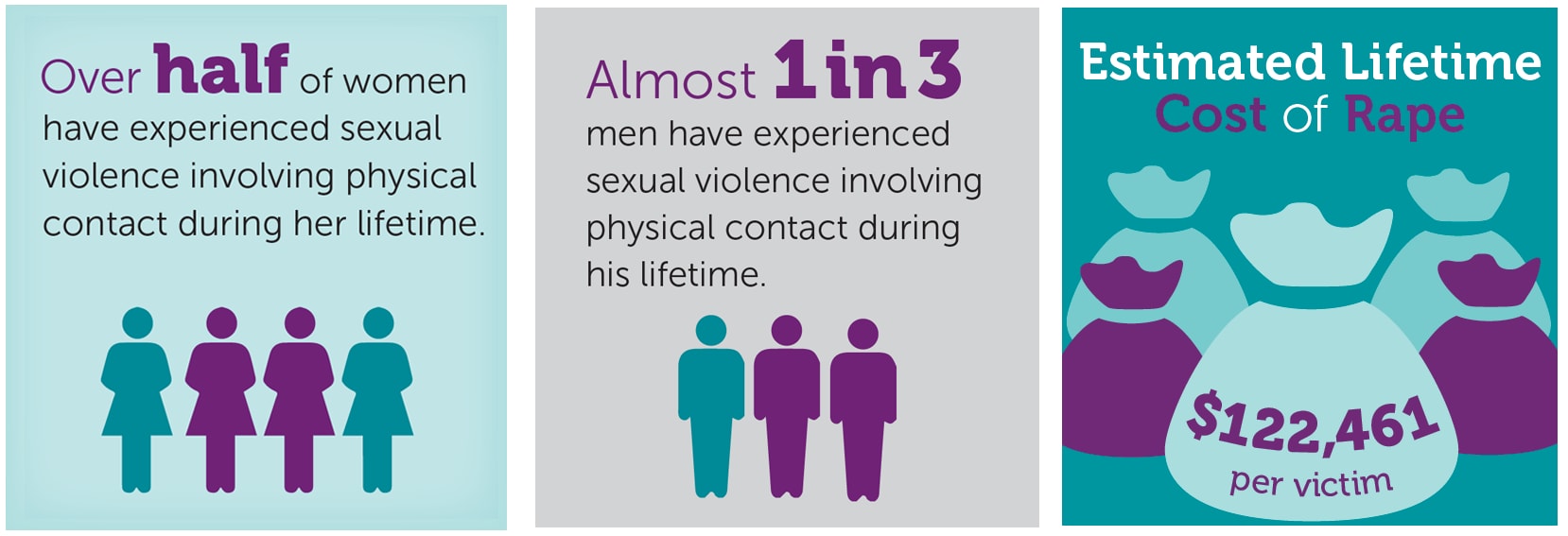
Sexual violence consequences are physical, like bruising and genital injuries, sexually transmitted infections, and pregnancy (for women) and psychological, such as depression, anxiety, and suicidal thoughts.
The consequences may be chronic. Survivors may suffer from post-traumatic stress disorder and experience re-occurring reproductive, gastrointestinal, cardiovascular, and sexual health problems.
Sexual violence is also linked to negative health behaviors. Sexual violence survivors are more likely to smoke, abuse alcohol, use drugs, and engage in risky sexual activity.
The trauma from sexual violence may impact a survivor’s employment in terms of time off from work, diminished performance, job loss, or inability to work. These issues disrupt earning power and have a long-term effect on the economic well-being of survivors and their families. Coping and completing everyday tasks after victimization can be challenging. Survivors may have difficulty maintaining personal relationships, returning to work or school, and regaining a sense of normalcy.
Additionally, sexual violence is connected to other forms of violence. For example, girls who have been sexually abused are more likely to experience additional sexual violence and violence types and become victims of intimate partner violence in adulthood. Bullying perpetration in early middle school is linked to sexual harassment perpetration in high school.
Certain factors may increase or decrease the risk for perpetrating or experiencing sexual violence. To prevent sexual violence, we must understand and address the factors that put people at risk for or protect them from violence . We must also understand how historical trauma and structural inequities impact health.
CDC developed, Sexual Violence Prevention Resource for Action [3 MB, 46 Pages] to help communities use the best available evidence to prevent sexual violence. This resource is available in English and Spanish [17MB, 48 Pages, 508] and can impact individual behaviors and relationship, family, school, community, and societal factors that influence risk and protective factors for violence.
Different violence types are connected and often share root causes. Sexual violence is linked to other violence types through shared risk and protective factors . Addressing and preventing one violence type may have an impact on preventing other violence types.
- Basile KC, Smith SG, Breiding MJ, Black MC, & Mahendra, R. (2014). Sexual violence surveillance: uniform definitions and recommended data elements, Version 2.0. Atlanta (GA): National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
- Basile KC, Smith SG, Kresnow M, Khatiwada S, & Leemis RW. (2022). The National Intimate Partner and Sexual Violence Survey: 2016/2017 Report on Sexual Violence. Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
- Peterson C, DeGue S, Florence C, Lokey C. (2017). Lifetime Economic Burden of Rape in the United States. American Journal of Preventive Medicine 52(6): 691-701.
- Basile KC and Smith SG. (2011). Sexual Violence Victimization of Women: Prevalence, Characteristics, and the Role of Public Health and Prevention. American Journal of Lifestyle Medicine (5): 407-417.
- Basile KC, Clayton HB, Rostad WL, & Leemis RW. (2020). Sexual violence victimization of youth and health risk behaviors. American Journal of Preventive Medicine, 58(4), 570-579.
- Preventing Multiple Forms of Violence: A Strategic Vision for Connecting the Dots. (2016). Atlanta, GA: National Center for Injury Prevention and Control, Centers for Disease Control and Prevention.
- Espelage DL, Basile KC, Hamburger ME. (2012). Bullying perpetration and subsequent sexual violence perpetration among middle school students. Journal of Adolescent Health 50(1): 60-65.
To receive email updates about this page, enter your email address:
- Data & Statistics (WISQARS)
- Opioid Overdose Prevention
- Traumatic Brain Injury
- Motor Vehicle Safety
Exit Notification / Disclaimer Policy
- The Centers for Disease Control and Prevention (CDC) cannot attest to the accuracy of a non-federal website.
- Linking to a non-federal website does not constitute an endorsement by CDC or any of its employees of the sponsors or the information and products presented on the website.
- You will be subject to the destination website's privacy policy when you follow the link.
- CDC is not responsible for Section 508 compliance (accessibility) on other federal or private website.
Bay Shore case shows we must confront sexual abuse in schools
The allegations against teacher Thomas Bernagozzi, of the Bay Shore school district, are troubling and a stark reminder of the vulnerability of our children within the educational system. Credit: James Carbone
Recent reports of sexual abuse cases involving educators have once again brought the issue of safeguarding our children to the forefront of public discourse. Allegations against individuals like retired teacher Thomas Bernagozzi of the Bay Shore school district, and countless others nationwide, make clear we must address the systemic failures that allow such misconduct to occur and persist.
The allegations against Bernagozzi are troubling and a stark reminder of the vulnerability of our children within the educational system. Schools should be places of safety, trust, and growth; when those entrusted with our children’s education and well-being betray that trust, the repercussions are profound and long-lasting.
It is essential that we acknowledge the courage of survivors who come forward to share their stories, often in the face of skepticism and institutional resistance. Their bravery underscores the urgency for comprehensive reforms in how schools prevent, respond to, and address instances of sexual abuse.
First and foremost, accountability must be at the forefront of any response. Institutions must conduct thorough and impartial investigations into allegations of abuse, and perpetrators must be held accountable to the fullest extent of the law. This includes not only criminal prosecution but also civil remedies.
This guest essay reflects the views of Ralph Kohl, a graduate of Bay Shore schools, former state Assembly staff member, and government affairs professional specializing in health care in Alexandria, Virginia.
We also must prioritize prevention through education and training for educators, students, and parents. This includes fostering open dialogue about boundaries, consent, and healthy relationships from an early age, as well as implementing robust policies and procedures for reporting and addressing instances of misconduct.
From our Editorial Board, get inside the local, city and state political scenes.
By clicking Sign up, you agree to our privacy policy .
Beyond individual cases, we must also confront the broader cultural and systemic factors that enable sexual abuse to occur unchecked. This includes challenging harmful power dynamics, dismantling barriers to reporting, and fostering a culture of accountability and transparency within schools.
Ultimately, confronting sexual abuse in schools requires a collective effort from educators, administrators, lawmakers, and the broader community. It is incumbent on all of us to stand in solidarity with survivors, to demand accountability from those in positions of power, and to work tirelessly to ensure that every child has the right to learn and thrive in an environment free from fear and harm.
One of the most concerning aspects in Bay Shore is the apparent repetition of mistakes by the current administration, mirroring the mishandlings of past cases. By not believing their former students, victim-shaming, and failing to accept accountability, administrators not only undermine the trust of current students and parents but also send a chilling message that victims will not be believed or supported if they come forward with allegations of abuse.
This perpetuates an environment of fear, silence, and mistrust, further entrenching the barriers that prevent survivors from seeking justice and healing. Educational leaders must break this cycle of impunity and indifference by prioritizing the voices and experiences of survivors, fostering a culture of transparency and accountability and ensuring that every student feels empowered and supported to speak out against abuse. That’s how we can begin to rebuild trust, safeguard our children, and create safer learning environments for all.
It is time for the superintendent and school board to demonstrate courage and integrity by admitting the failures of the district, addressing them, and ensuring that survivors receive the support and justice they deserve. Anything less is a betrayal of trust and a grave disservice to the victims and their families, many of whom reside and have children in the district.
105 Sexual Abuse Essay Topic Ideas & Examples
🏆 best sexual abuse topic ideas & essay examples, 📌 simple & easy sexual abuse essay titles, 👍 good essay topics on sexual abuse, ❓ questions about sexual abuse.
- New South Wales vs. Lepore: Sexual Abuse by Teachers The plaintiff sued the State of New South Wales and the teacher in the District Court of New South Wales. The plaintiff argued that there was a fault or negligence on the part of the […]
- Life After Sexual Abuse. Counseling Intervention The latter implies the analysis of the problem from the perspective of a sexual abuse survivor who has experienced the lack of attachment in infancy and, therefore, is incapable of handling the issue of their […] We will write a custom essay specifically for you by our professional experts 808 writers online Learn More
- Sexual Abuse in the “Fifty Shades of Grey” The impact can be either positive or negative depending on the quality of the movie itself and the audience’s understanding of its purpose and themes.
- MMPI Test in Determining Women Who Were Exposed to Childhood Sexual Abuse Furthermore, to conduct a successful psychological assessment, a complete medical assessment should be included in the process so that the psychologists performing the test ascertain that the participants’ symptoms are not subject to ailments or […]
- Sexual Abuse of Children in Modern Literature By concentrating on the fictional portrayal of these cycles of violence via the perspective of literary justice, this research will study and consider how childhood sexual abuse is depicted in modern fiction.
- Sexual Abuse in the Workplace as an Ethical Issue It is also ruinous indirectly through the turnover of both the victim and the harasser. It is also advisable to forward a copy of the email to your email and keep a printed copy.
- Insecure Attachment Orientations After Sexual Abuse This prospective study assesses the temporal relations between the 2 attachment dimensions of anxiety and avoidance and PTS among a treatment-seeking sample of female survivors of childhood sexual abuse. The independent variable in the study […]
- #MeToo: A Social Movement Against Sexual Abuse and Sexual Harassment The #MeToo movement started as a response to the pervasiveness of sexual abuse and sexual harassment against women. In the founder’s words, the original purpose of the #MeToo campaign was to spread the message to […]
- Sexual Abuse in Bachelor of Social Work Students The abstract clearly delineates that the research is on the experience of sexual abuse victimization of the BSW students in their childhood.
- The Issue of Child Sexual Abuse Many studies address that issue discussing potential consequences of child sexual abuse and available prevention measures.
- Childhood Sexual Abuse and HIV Risk in San Salvador Still, the women interviewed presented a peculiar layer of the society that made it possible to understand the clear connection of the CSA to HIV/AIDS and drug addictions.
- Memories of Sexual Abuse: Robbins vs. Benatar The significance of the topic of child sexual abuse is heavy enough to make society pay sufficient attention to the issue so as to find out how to verify adulthood disclosures of childhood sexual abuse. […]
- The Phenomenon of Child Sexual Abuse in the Society The Catholic Church has argued that the public’s generalization of the issue to involve the whole unit of the Catholic Church was simply a result of the structural characteristics of the church’s monolithic centralized organization.
- Sexual Abuse in Children: Application Project In this article, the researcher uses the interview method to assess the memory and suggestibility of the children in which children are required to perceive an event through retention and retrieval as instructed by the […]
- Reporting the Act of Sexual Abuse Against Children The problem of child abuse has now become the subject of active discussion in society and the direction of multiple initiatives by the state designed to significantly improve the situation with regard to children.
- The Child Sexual Abuse Assesment For instance, the response to the disclosure of the abuse determines the future of the child. For instance, in the current placement I have used the concept of how to respond to the disclosure to […]
- Childhood Sexual Abuse and False Memories The independent variable was general plausibility to do with how common the events were in a general population of students from where the participants were drawn.
- Sexual Abuse and Workplace Investigation In addition to the statement, several documents will be used during the planning stage of the investigation: the organization’s harassment policy, personnel files of the complainant and the respondent, and attendance records.
- Child Sexual Abuse by Catholic Priests The law allowed the victims of sexual abuse to come forward and report the abuse to the police, regardless of the time when the crime had happened.
- Transforming Trauma: Adult Survivors of Sexual Abuse Salter not only describes and explains the experience of the victim but also gives an insight into the psychology of the offender, which allows the reader to view the problem from a different angle.
- School Sexual Abuse and Unethical Leadership The discussed case is one of the disturbing examples of unethical behavior on the part of the school authorities that covered up for the individuals that abused their students.
- Boys’ and Girls’ Sexual Abuse Relationship Unfortunately, the research proved the spread opinion that the cases of girls’ abuse are more prevalent in comparison to boys’ one, however, this tendency is changing and the number of sexually abused boys increases.
- Sexual Abuse in Male and Female Adolescents The relationship between the categories of sexual abuses and the resultant psychological distress experienced by girls and boys will be measured. Finally, the study will examine the class performance variations between sexually abused boys and […]
- Sexual Abuse in Boys and Girls and Its Implications In most cases, Primary School children are the affected group of sexual abuse, both the girls and boys since their age are believed to be unaware of sexual activities and abuse.
- News Coverage of Child Sexual Abuse and Prevention The tool helped to identify the frame of a newspaper article, as well as it allowed to code the details related to the case such as the description language or the relationship of the victim […]
- Cultural Issues in Disclosures of Child Sexual Abuse Also, another issue that needs to be discussed is that it is entirely possible that members of the family are depressed and tension is present.
- Sexual Abuse on Erin Merryn The Megan’s Law responds to violent crimes on children driven by sex through a public notification as an approach to preventing predatory children sexual abuse.
- Randomized Trial of Cognitive-Behavioral Therapy for Chronic Post-Traumatic Stress Disorders in Adult Female Survivors of Childhood Sexual Abuse However, in spite of the fact that there exist a wealth of clinical literature on treatment methodologies of victims of sexual abuse, the evidence base concerning the treatment of victims of childhood sexual abuse exhibiting […]
- Child Sexual Abuse: Impact and Consequences Due to the adverse consequences of sexual abuse, efforts to have Jody share her ordeal and get immediate help would be my priority.
- Psychological Impacts of Sexual Abuse on Ryan With regards to the case at hand, Ryan is likely to suffer psychologically as a result of trauma and depression. Through family support, Ryan will therefore find it easier to accept and cope with the […]
- Who Is the Victim: The Power Struggle of Sexual Abuse in The Rape of Lucrece
- Substance Abuse in Adolescents and the Predictor of Childhood Sexual Abuse
- The Role of School Counselors in Sexual Abuse Prevention and Intervention
- The Effects of Adlerian Art Therapy on Sexual Abuse and Assault
- Sexual Abuse of Black Female Slaves
- The Characteristics and Forms of Child Abuse: Physical Abuse, Physical Neglect, Sexual Abuse, and Emotional Abuse
- Sexual Abuse of People with Developmental Disabilities
- The Role Of Social Work In Relation To Protecting Children From Sexual Abuse
- The Impact of Physical, Mental, and Sexual Abuse and Neglect in the Child’s Emotions
- The Discouragement of Biracials and Mulattoes and the Sexual Abuse of White Slave Owners Before the Civil War in America
- The Connection Between Child Sexual Abuse & Dissociative Identity Disorder
- The Role Of A Guidance Counselor When Sexual Abuse Is Reported Within The Public School System
- The New Complexities of Child Sexual Abuse in the Internet Age
- The Effect of Childhood Sexual Abuse during Adulthood
- Sexual Abuse as a Cause of Borderline Personality Disorder (BPD)
- The Relationship of Childhood Sexual Abuse to Teenage Pregnancy
- The Impact of Sexual Abuse on Childs Emotions
- Sexual Abuse and Its Effects on the Emotions of the Child
- Understanding the Impact of Childhood Sexual Abuse on Women’s Sexuality
- Sexual Abuse: The Most Devastating Forms Of Child Abuse
- Understanding Childhood Sexual Abuse in Latina Youth
- The Psychological Effects of Sexual Abuse on Children and Their Brain Development
- The Sexual Abuse in the Kidnapping Story of Jaycee Lee Dugard
- The Importance of Teaching Children about Sexual Abuse by an Acquaintance
- Sexual Abuse Of Women Prisoners In The United States
- Sexual Abuse in the Society and Its Consequence
- The Problem of Sexual Abuse of Children in the United States
- The Long-Term Effects of Child Sexual Abuse by Female Perpetrators
- The Trauma of Childhood Sexual Abuse
- Violence And Sexual Abuse At The Health Care Agencies
- Sexual Abuse Definition, Effects, and Recovery
- The Role of Parents in Protecting Their Children from Sexual Abuse
- The Short and Long-Term Effects of Sexual Abuse on a Child’s Behavior
- The Inspiration and Enlightenment from the Film Confronting Child Sexual Abuse
- Sexual Abuse and the Changing Nature of Vicarious Liability
- Why Are Child Victims Of Sexual Abuse At Greater Risk Of HIV
- The Treatment Of Young Victims Of Child Sexual Abuse
- The Psychological and Social Effects of Sexual Abuse against Young Teenage Girls in Battered Families
- The Validity of Sexual Abuse Charges Made by Children
- The Growing Problem of Childhood Sexual Abuse Among the Active Sadomasochistic Population in Finland
- Sex Trafficking, Domestic Violence, And Sexual Abuse
- Sexual Abuse During The Life Of A Slave Girl By Linda Brent
- The Impact of Sexual Abuse on the Successful Development of Children
- The Debate About the Constitutionality of Speech that Is Clearly Sexual Abuse
- The Lasting Effects Of Sexual Abuse On Children
- Does Sexual Abuse Lead to Homosexuality?
- How Can Adlerian Art Therapy Impact Sexual Abuse and Assault?
- Why Might the Experience of Child Sexual Abuse Lead to Mental Health Problems in Adulthood?
- How Often Does Child Sexual Abuse Get Reported?
- At Which Age Are Females at the Highest Risk for Sexual Abuse?
- What Is the Most Common Form of Sexual Abuse?
- Is There Sexual Abuse in the French Foreign Legion?
- How Can Sexual Abuse Affect Intimate Relationships?
- What Is Stockholm Syndrome With Sexual Abusers?
- How Does Sexual Abuse Affect Women Mentally and Socially?
- What Are the Causes of Sexual Abuse in Society?
- Can Victims of Sexual Abuse Be Predisposed to Depression?
- What Are the Factors That Can Contribute to the Impact of Sexual Abuse?
- How Is Common Sexual Abuse in the Christian Church?
- Is Sexual Abuse a Social Phenomenon?
- Do the Internet and Cyberspace Encourage Pedophiles to Engage in Sexual Abuse?
- What Are the Psychological Effects of Sexual Abuse?
- Is There a Connection Between Sexual Fantasies and the Trauma of Childhood Sexual Abuse?
- Who Are the Main Perpetrators of Sexual Abuse?
- How Should the Legal System Respond to Recovered Memories of Childhood Sexual Abuse?
- What Are the Signs of Non-physical Sexual Abuse?
- How Bad Is the Problem of Sexual Abuse in the Catholic Church?
- Why Do Turkish Soldiers Sexually Abuse Kurdish Girls?
- Is It Possible to Recover From Childhood Sexual Abuse?
- How Does the #MeToo Movement Help Victims of Sexual Abuse?
- Does Sexualization in the Society of Girls and Tweens Promote Child Sexual Abuse?
- Did the Police Sexually Abuse the Women Suffragettes?
- Do Victims of Sexual Abuse Turn Into Abusers?
- What Is the Link Between Sexual Abuse and Eating Disorders?
- Are Aspergers More Likely to Suffer Sexual Abuse, Especially as Children?
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 29). 105 Sexual Abuse Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/sexual-abuse-essay-topics/
"105 Sexual Abuse Essay Topic Ideas & Examples." IvyPanda , 29 Feb. 2024, ivypanda.com/essays/topic/sexual-abuse-essay-topics/.
IvyPanda . (2024) '105 Sexual Abuse Essay Topic Ideas & Examples'. 29 February.
IvyPanda . 2024. "105 Sexual Abuse Essay Topic Ideas & Examples." February 29, 2024. https://ivypanda.com/essays/topic/sexual-abuse-essay-topics/.
1. IvyPanda . "105 Sexual Abuse Essay Topic Ideas & Examples." February 29, 2024. https://ivypanda.com/essays/topic/sexual-abuse-essay-topics/.
Bibliography
IvyPanda . "105 Sexual Abuse Essay Topic Ideas & Examples." February 29, 2024. https://ivypanda.com/essays/topic/sexual-abuse-essay-topics/.
- Abuse Research Topics
- Alcohol Abuse Paper Topics
- Sex Education Essay Titles
- Child Abuse Essay Topics
- Drug Abuse Research Topics
- Same Sex Marriage Questions
- Domestic Violence Paper Topics
- Elder Abuse Ideas
- Sex Offender Essay Topics
- Rape Essay Titles
- Sexual Assault Essay Titles
- Mental Health Essay Ideas
- Sex Trafficking Research Ideas
- Prison Paper Topics
- Bullying Research Topics
- Undergraduate
- High School
- Architecture
- American History
- Asian History
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- Linguistics
- Criminal Justice
- Legal Issues
- Anthropology
- Archaeology
- Political Science
- World Affairs
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Pharmacology
- Earth science
- Agriculture
- Agricultural Studies
- Computer Science
- IT Management
- Mathematics
- Investments
- Engineering and Technology
- Engineering
- Aeronautics
- Medicine and Health
- Alternative Medicine
- Communications and Media
- Advertising
- Communication Strategies
- Public Relations
- Educational Theories
- Teacher's Career
- Chicago/Turabian
- Company Analysis
- Education Theories
- Shakespeare
- Canadian Studies
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
- Movie Review
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Marketing Plan
- Multiple Choice Quiz
- Personal Statement
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Reaction Paper
- Research Paper
- Research Proposal
- SWOT analysis
- Thesis Paper
- Online Quiz
- Literature Review
- Movie Analysis
- Statistics problem
- Math Problem
- All papers examples
- How It Works
- Money Back Policy
- Terms of Use
- Privacy Policy
- We Are Hiring
Sexual Abuse, Essay Example
Pages: 3
Words: 751
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.
Introduction
- Vulnerability of children predisposes many to sexual abuse
- Abuse can be physical or psychological
- Effects of physical abuse include isolation and depression
- It can also lead to inability to engage in normal sexual behavior
- Post traumatic stress disorder is a common psychological disorder among the victims
- Sexually abused children more likely to develop deviant and promiscuous behavior
- Some engage in promiscuous behavior leading to sexually leading to sexually transmitted disease
- Others are unable to form lasting relationships
- Preventive measures should be put in place to prevent abuse
- Treatment is not a guaranteed remedy for the victims
- Prevention is the best remedy
The vulnerability of children makes them the most common targets of sexual abusers. In the US, it has become a significant issue regarding public health. Child sex abuse is categorized as abuse of an individual below the age of 18. The effects can be classified as physical and psychological and occur immediately and also later in life. Changes in personality character in children are the main recognition features of abuse. Having an appreciation of the long term effects of sexual abuse is very important when ones to understand personality characters of the victims who go through the experience. For effective management of victims of sexual abuse, it is imperative that we recognize the cause of the observed disorder and determine the Adversity to the child.
Post-traumatic stress disorder (PTSD) is common among children who have been victims of sexual abuse as outlined by Kinnear (p 18). This results due the nature of the abuse. The violence that is involved during the act in addition to the pain causes is bound to have delayed reaction on the child. If the abuser is known to the child, the extent of stress is more due to frequent exposure. The signs are normally related with association of the circumstances preceding and during the abuse with any other circumstance the child is presented with. As a result, the child will avoid such situation and may appear withdrawn. Reports have shown that sexually abused children develop anxiety and deviant sexual behaviors including promiscuity.
Mental health of an abused child is also affected adversely. Owing to the heinous nature of the offense, the child is bound to become isolated and depressed. Over time, the child becomes withdrawn from society. Kinnear (19) postulated that the stigma attached to abuse of child also fosters the guilty feeling. As a result, the child enters adulthood without having experienced the challenges which normally stimulate response behavior for survival as an adult.
Physically, some victims are rendered unable to engage in normal sexual practices owing to the physical trauma to the affected organs. The abuser is obviously in a hurry to avoid being caught. The element of struggle implies that injury is bound to occur. As result, the ability to function as normal adult and fulfill their reproductive duties is greatly hampered even in the absence of psychological tendencies. The fear involved in correlating sexual activity wit abuse becomes a hindering factor hence making the individuals unable to form lasting relationships.
Sexual abuse is bound to lead to sexually transmitted diseases to the child. Most abusers are adults who have previously engaged in sexual activities and could thus be carriers of such diseases. Transmission rates are also higher owing to the injury sustained. As observed from most instances, such treatment for such disease is hampered by the diagnostic challenges since the victim may hide the fact they were abused Finkelman (p 41). The shame and trauma involved may prevent the child from opening up to responsible adults.
According to Kinnear (18), inclination to crime has been observed to occur in children who have been sexually abused. Their appreciation of danger is compromised due to loss of self-esteem thus propagating tendencies of disruptive behavior and conduct. Besides, the abused child is bound to feel dejected. This feeling propels most abused children to risk taking behavior. The withdrawal period also takes away valuable time for personal development and the individual may lack a source of income. Substance abuse is also rife among individuals who have been abused. This originates from the search of a coping mechanism.
In conclusion therefore, it is imperative that society protects children from abuse of any form. Sexual abuse has adverse effects running into adult life. Treatment and care of victims is not a guaranteed remedy for the victims. As a result, it is better prevention than care.
Works Cited
Finkelman, Byrgen “Child Abuse: Short- And Long-Term Effects” USA: Taylor & Francis, 1995p
Kinnear, Karen L. ‘Childhood Sexual Abuse: A Reference Handbook”, California: ABC- CLIO, 2007
Stuck with your Essay?
Get in touch with one of our experts for instant help!
Children With Attachment Disorders From Orphanages, Essay Example
Non-Human Rights, Essay Example
Time is precious
don’t waste it!
Plagiarism-free guarantee
Privacy guarantee
Secure checkout
Money back guarantee

Related Essay Samples & Examples
Voting as a civic responsibility, essay example.
Pages: 1
Words: 287
Utilitarianism and Its Applications, Essay Example
Words: 356
The Age-Related Changes of the Older Person, Essay Example
Pages: 2
Words: 448
The Problems ESOL Teachers Face, Essay Example
Pages: 8
Words: 2293
Should English Be the Primary Language? Essay Example
Pages: 4
Words: 999
The Term “Social Construction of Reality”, Essay Example
Words: 371
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 03 April 2024
Investigating child sexual abuse material availability, searches, and users on the anonymous Tor network for a public health intervention strategy
- Juha Nurmi 1 ,
- Arttu Paju 1 ,
- Billy Bob Brumley 2 ,
- Tegan Insoll 3 ,
- Anna K. Ovaska 3 ,
- Valeriia Soloveva 3 ,
- Nina Vaaranen-Valkonen 3 ,
- Mikko Aaltonen 4 &
- David Arroyo 5
Scientific Reports volume 14 , Article number: 7849 ( 2024 ) Cite this article
273 Accesses
37 Altmetric
Metrics details
- Human behaviour
- Information technology
- Public health
Tor is widely used for staying anonymous online and accessing onion websites; unfortunately, Tor is popular for distributing and viewing illicit child sexual abuse material (CSAM). From 2018 to 2023, we analyse 176,683 onion domains and find that one-fifth share CSAM. We find that CSAM is easily available using 21 out of the 26 most-used Tor search engines. We analyse 110,133,715 search sessions from the Ahmia.fi search engine and discover that 11.1% seek CSAM. When searching CSAM by age, 40.5% search for 11-year-olds and younger; 11.0% for 12-year-olds; 8.2% for 13-year-olds; 11.6% for 14-year-olds; 10.9% for 15-year-olds; and 12.7% for 16-year-olds. We demonstrate accurate filtering for search engines, introduce intervention, show a questionnaire for CSAM users, and analyse 11,470 responses. 65.3% of CSAM users first saw the material when they were children themselves, and half of the respondents first saw the material accidentally, demonstrating the availability of CSAM. 48.1% want to stop using CSAM. Some seek help through Tor, and self-help websites are popular. Our survey finds commonalities between CSAM use and addiction. Help-seeking correlates with increasing viewing duration and frequency, depression, anxiety, self-harming thoughts, guilt, and shame. Yet, 73.9% of help seekers have not been able to receive it.
Similar content being viewed by others
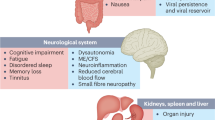
Long COVID: major findings, mechanisms and recommendations
Hannah E. Davis, Lisa McCorkell, … Eric J. Topol
Adults who microdose psychedelics report health related motivations and lower levels of anxiety and depression compared to non-microdosers
Joseph M. Rootman, Pamela Kryskow, … Zach Walsh
Negativity drives online news consumption
Claire E. Robertson, Nicolas Pröllochs, … Stefan Feuerriegel
Introduction
Society benefits from the responsible use of anonymity; for instance, newspapers and police departments use anonymous tips as a source of information, people in countries with strict political systems hide their identities to avoid persecution for their political views, and individuals are permitted to speak freely about personal matters, such as religious issues.
The Onion Router (Tor) provides online anonymity for millions of internet users every day, and it is often portrayed favourably as a method to avoid surveillance by concealing the origin of communications, resisting web browser fingerprinting, circumventing traffic for unrestricted internet access without censorship, and providing anonymous online hosting using onion domains.
On the other hand, online anonymity serves as a catalyst for the dark side of human behaviour: it is one of the principal causes of the online disinhibition effect, characterised by lowered psychological restraints resulting in intensified aggressive, illicit, or unethical behaviour 1 —including higher levels of harassment, threats, racial agitation, and sexism 2 . Tor users hosting anonymous onion websites behave accordingly: the websites predominantly host unethical or illicit content, including illegal drug trade, fraud, computer crime, and the distribution of child sexual abuse material (CSAM) 1 .
We use the term ‘CSAM’ instead of ‘child pornography’ to emphasise the distinction. The term ‘pornography’ implies consent, and whilst it is contested to what extent consent is present in the production and dissemination of adult pornography, in the case of CSAM it is not possible for any child to consent in the first place. CSAM means media, including images, videos, and live streaming, that depict sexual violence against a child.
It is common for those who search for and view CSAM to engage in other related compulsive behaviours, such as collecting and organising CSAM by age, gender, sex act, and fantasy 3 . In order to encompass all activities, we refer to these individuals as ‘CSAM users’ in this article. This group includes individuals who search for, view, disseminate, and/or trade CSAM. A large portion of this group is likely to have sexual interest in children (i.e., paedophilia or hebephilia) 4 . These sexual preferences are classified as mental health disorders because they result in self-harm and harm to others, and therapy can improve well-being and prevent harm to children 5 .
Many users are not just passive observers of CSAM; rather, they are sexually motivated 6 . Previous research has suggested that problematic use of legal pornography can escalate to violent sexual behaviour and the use of CSAM. Consumers who view legal pornography and engage in masturbation fuel this process of escalation by providing themselves with a ‘powerful neurochemical reward’ through orgasm 7 . This process, along with repeated exposure, may condition users into continuing to use the material despite possibly wanting to stop 6 .
The fact that CSAM is easy to access through the Tor network—and other anonymous networks—increases the likelihood that more children will be sexually abused: one study found that 41.8% (N = 647 of 1546) of anonymous people who answered a survey after searching for CSAM on Tor search engines said they had tried to seek direct contact with children online after viewing CSAM, and 57.9% (N = 895 of 1546) said they were afraid that viewing CSAM could lead to sexual acts with a child 8 . This suggests that roughly half of CSAM users do not expect to become offline offenders, which is relevant for subsequent public health interventions, as this may indicate a separation between the populations of online-only offenders and online and in-person offenders.
Despite abundant evidence of the growing prevalence and severe consequences of CSAM accessible through the Tor network, computer science research on CSAM remains limited. A report to the US Congress in 2022 9 addresses the lack of research regarding CSAM accessible through the Tor network, as well as: ‘The ethical failure of computer science researchers with respect to acknowledging the harms against children carried out via Tor and Freenet is vast. Dozens of papers on Tor, Freenet, and I2P have been written in the past decade and published in the flagship security and privacy conferences of the computer science research community: USENIX Security, ACM Computer and Communications Security, ISOC Network and Distributed Systems Security, and the Proceedings of Privacy Enhancing Technology. Virtually none have mentioned the harms of these anonymous services.’
All of these venues have rules for stating harms and disclosing and discussing ethical issues, but the sponsoring organisations, chairs, and reviewers do not strictly enforce these rules 9 .
Articles in top computer science and security venues even conduct research on Tor usage; one even poses the research question, ‘Why do people use Tor?’, and despite the fact that one of their interview responses raises the issue, the authors make no mention of child abuse 10 . Similarly, even when the subject of one article is sexual abuse and it references Tor Browser usage, child abuse is not mentioned 11 .
In 2018, the USENIX Security Symposium article ‘How Do Tor Users Interact With Onion Services?’ presents an online survey of 517 Tor users where several users are concerned about CSAM; however, this does not lead to any further analysis in the paper, and it avoids mentioning child abuse 12 .
Similarly, a 2019 article in the Proceedings of the Web Science Conference (WebSci) titled ‘A Broad Evaluation of the Tor English Content Ecosystem’ omits any mentions of CSAM, despite the authors’ claims to have performed an exhaustive evaluation of the content and use of Tor 13 .
There are surely articles covering the harms and studying CSAM accessible through the Tor network, but mainly outside of the top computer science venues. In 2020, an article published in The Proceedings of the National Academy of Sciences (PNAS) acknowledged that ‘The Tor anonymity network allows users to protect their privacy and circumvent censorship restrictions but also shields those distributing child abuse content 14 ’.
As early as 2011, research revealed the widespread distribution of CSAM in peer-to-peer networks 15 . This issue affects not only Tor but also the I2P and Freenet anonymity networks; in a 2022 investigation, a Freenet content analysis revealed that 12.0% of the 7161 analysed freesites contained CSAM 16 . The first systematic analysis in 2013 indicated that 17.6% (206 of 1171) of the onion services surveyed shared CSAM and concluded ‘The support for the further development of Tor hidden services should hence stop 1 ’. Measurements on onion service visits find CSAM sites to be the most popular ones 17 . In 2014, an estimated 17% of the onion websites provided sexual material, of which about half was CSAM 18 . In 2018, additional research pointed in the same direction 19 .
We collect and analyse web content accessible through onion websites, study user searches on the Tor search engine, Ahmia.fi , and demonstrate that CSAM is widely available and Tor users actively seek this material. We show a questionnaire for those who search for CSAM and analyse 11,470 responses.
Our research questions (RQs) are:
What is the distribution volume of CSAM hosted through the Tor network?
What is the CSAM search volume, and what exactly are users seeking?
What does the survey reveal about CSAM users?
How can search engine-based intervention reduce child abuse?
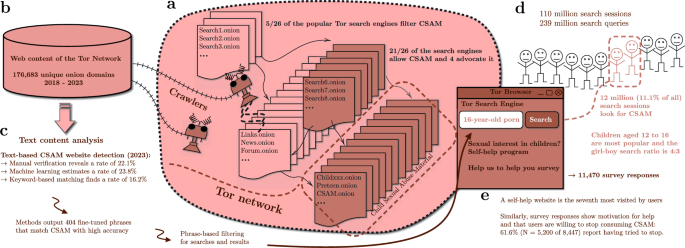
We investigate the availability of CSAM hosted through the Tor network and its users. ( a ) Tor enables anonymous web publishing through onion domains. These websites host a variety of content, and there are Tor-specific search engines for searching. 21/26 of the popular Tor search engines allow CSAM websites. ( b ) Our web crawlers collected online content from 176,683 different onion domains from 2018 to 2023. ( c ) Using text-based CSAM detection methods, we investigate the number of websites sharing CSAM. The identification methods provide us with 404 phrases that accurately identify CSAM content. ( d ) This enables text-based detection and filtering for Tor search engines. CSAM-related searches are among the most popular of the 239 million total queries. Out of 110 million search sessions, 11.1% are seeking CSAM. ( e ) The search engine directs CSAM-seekers to self-help websites and asks them to complete our survey. The results indicate that they want assistance and are motivated to stop using CSAM.
Figure 1 shows our approaches for analysing CSAM availability and usage on Tor. The Methods section presents our research methodology in detail. Our contributions are: (1) We measure the CSAM distribution hosted through the Tor network over a five-year period using onion website crawling, which indicates that through the years 2018–2023 about one-fifth of the websites share CSAM. (2) We show that these CSAM websites can be reached directly from the majority (21/26) of the top Tor search engines used today, and four Tor search engines even advertise CSAM. (3) We find that 11.1% (N = 12,270,042 of 110,133,715) of the search sessions are explicitly searching for CSAM; the single phrase ‘child porn’ is one of the top queries. (4) When we prompt those who search for CSAM with a survey, we find that 61.6% (N = 5200 of 8447 who replied to the question) of CSAM users have tried to stop watching CSAM, 48.1% (N = 4120 of 8566 who replied to the question) want to stop using CSAM, and there is an unmet demand for help resources. (5) Search engines are a key part of the solution; hence, we demonstrate the effectiveness of CSAM detection and the ability of search engines to intervene and steer CSAM users towards help.
Surge of CSAM hosted through the Tor network
RQ1: What is the distribution volume of CSAM hosted through the Tor network?
We investigate the years 2018–2023 and use a sample of 10,000 unique onion domains for each year. We then subject the text content to duplicate content filtering, fine-tuned phrase search, and supervised learning classifiers. This returns the detected CSAM percentage for each year, as shown in Fig. 2 .
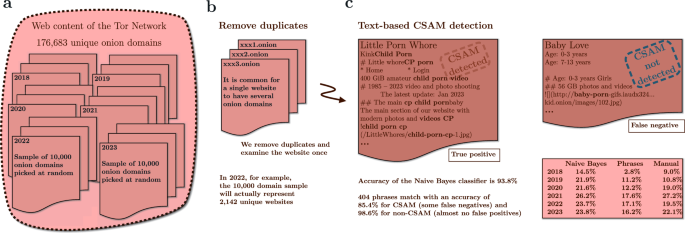
We measure the proportion of CSAM onion websites inside the Tor network in 2018–2023. ( a ) We use a sample of 10,000 unique onion domains for each year. ( b ) Many websites have several onion domains. We compare the title and sentences of the pages to detect duplicates, and restrict to a single domain if multiple domains share identical content. ( c ) We execute text-based CSAM detections against the content of these distinct domains. Some CSAM websites do not use explicit sexual language, and text-based detection fails. Using three separate methods – manual validation, phrase matching, and the naive Bayes classifier – we discover that the detected percentage of websites sharing CSAM is 16.2–23.8% in 2023. Comparing automated methods to human validation by hand yields consistent results (22.1% in 2023 and 19.5% in 2022). We randomly select the plain text representations of 1000 onion websites for each year, 2018–2023, and read the text content of these websites to determine whether they share CSAM and what the English vocabulary is for this type of page.
The phrase matching fails to detect anything that does not describe CSAM with the obvious phrases. Furthermore, there are real CSAM websites that do not use explicit sexual language and instead refer to content such as ‘baby love videos’. Our text-based detection does not match these websites. In addition, there are link directory websites that provide descriptions of CSAM website links. Our text-based detection matches the description phrases despite the fact that this type of website does not share CSAM, rather merely links to websites that do.
We achieve 93.8% accuracy with a basic naive Bayes classifier (see Supplementary Methods A.2 ). Some legal adult pornography websites, like PornHub , provide an alternative onion domain accessible via Tor. We manually review a sample set of PornHub pages, and there is no indication of anything other than adult material; therefore, we include these in our training data to teach the classifier to differentiate between legal and illegal content. The classifier performs well and can distinguish between legitimate pornography websites and unlawful CSAM websites. The accuracy is as expected and actually quite consistent with previous research (93.5%) for Tor content classification 20 .
We anticipate that the phrase matching method will generate few false positives due to the explicit nature of the matching phrases. It is rare for a website to contain these phrases unless it also contains CSAM, and even those exceptions are describing linked CSAM websites. We anticipate – for the same reason – that this method will generate false negatives, as it requires exact CSAM-describing language. Indeed, the matching works accordingly: its accuracy is 85.4% with CSAM websites (some false negatives) and 98.6% with non-CSAM websites (almost no false positives).
When law enforcement has seized control of CSAM servers operating through the Tor network, they have documented terabytes of content with hundreds of thousands of users (see Supplementary Discussion C.2 ). In a comparable manner, we find indicators that suggest the distribution of extensive CSAM collections. While we read texts from the websites, we see numerous CSAM websites that claim to share gigabytes of media and thousands of videos and images.
Using three separate methods – manual validation, phrase matching, and the naive Bayes classifier – we conclude that around one-fifth of the unique websites hosted through the Tor network share CSAM. Previous research, in 2013, found that 17.6% of onion services shared CSAM, which corresponds with our findings 1 .
Examining CSAM user behaviour
RQ2: What is the CSAM search volume, and what exactly are users seeking?
11.1% of the search sessions seek CSAM
We examine search chains generated by users who enter consecutive queries. We follow the searches entered by users, track queries per user, and study 110,133,715 total search sessions, and discover that 32.5% (N = 35,751,619) include sexual phrases. Finally, we find that 11.1% (N = 12,270,042) of the search sessions reveal that the user is explicitly searching for content related to the sexual abuse of children. Some of these CSAM search sessions include either ‘girl(s)’ (393,261) or ‘boy(s)’ (289,407); searching for girls is more prevalent, with a ratio of 4:3. Seeking torture material is not typical: 0.5% of CSAM search sessions (57,429) contain the terms ‘pain’, ‘hurt’, ‘torture’, ‘violence’, ‘violent’, ‘destruction’, or ‘destroy’.
During the COVID-19 pandemic and the first months of lockdowns, there was a significant surge in the user base of legal pornography websites across nations 21 . Surprisingly, we find that before and after COVID-19 pandemic measures (lockdowns, individuals spending more time at home), there were no significant changes in the behaviour of CSAM users (see more in Supplementary Methods A.8 ).
54.5% are searching for 12- to 16-year-olds
We determine if the search session reveals the exact age in which the CSAM user is interested. For example, for a 13-year-old, we count search sessions that include 13y(*), 13+y(*), 13teen, thirteen+year, 13boy(s) or 13girl(s). We use the same logic for other ages. In addition, to compare these searches for CSAM to legal adult sexual content searches, we include search sessions seeking 18-year-old (N = 12,347 from 110,133,715) and 19-year-old adults (N = 458 from 110,133,715). We find the age information in total for 479,555 search sessions. Figure 3 illustrates the age distribution of CSAM queries. This age distribution aligns with findings from previous studies 22 . An article titled ‘Pedophilia, Hebephilia, and the DSM-V’ finds qualitative differences between offenders who preferred pubertal and those with a prepubertal preference (a clinical trial of 881 men with problematic sexual behavior) 23 . The authors also note that the majority of child abuse victims are 14 years old. They concluded that the psychiatric diagnoses should be improved to include the following: sexually attracted to children younger than 11 (paedophilic type), sexually attracted to children aged 11–14 (hebephilic type), or sexually attracted to both (pedohebephilic type). Our data suggests that it may be more appropriate to observe the high percentage of individuals who have a sexual interest in 12-year-olds but not 11-year-olds. This finding is consistent with the national average age at menarche in the United States, which is 12.54 years 24 . Additionally, observe the decline in sexual interest that occurs across the ages of 17, 18, and 19, which indicates a distinct sexual interest in those aged 12 to 16 years old.
Moreover, in Fig. 4 , we investigate CSAM search sessions containing age-indicating search terms and find that users are predominantly interested in 12- to 14-year-old teen content; for example, ‘lolita’ is the most popular term when compared to other age-related terms, with 33.2% (N = 746,786 of 2,287,057). In Vladimir Nabokov’s 1955 novel ‘Lolita’, a middle-aged male is sexually attracted to a 12-year-old girl and sexually abuses her. In the 1962 Stanley Kubrick film adaptation of the novel, ‘Lolita’ is 14 years old.
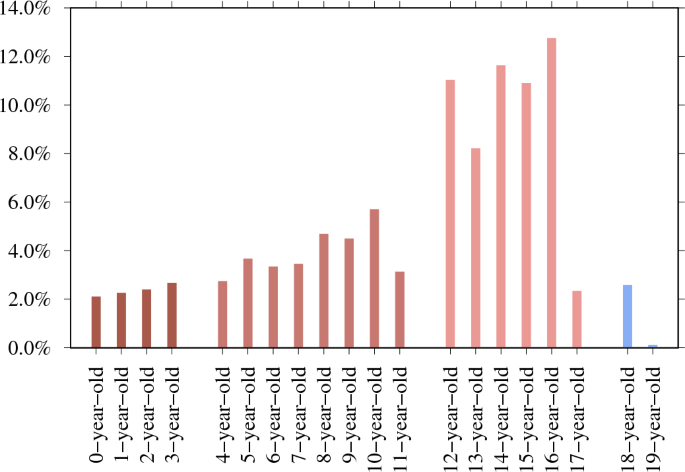
Ages between zero and 17 included in the CSAM search sessions and search sessions seeking 18-year-old and 19-year-old adults as a comparison (N = 479,555). 16-year-old (N = 61,083 of 479,555 – 12.7%) is the top-mentioned age. 54.5% of age-revealing searches (N = 261,162 of 479,555) target those aged 12–16 years old. Outside of this age range, the interest declines.
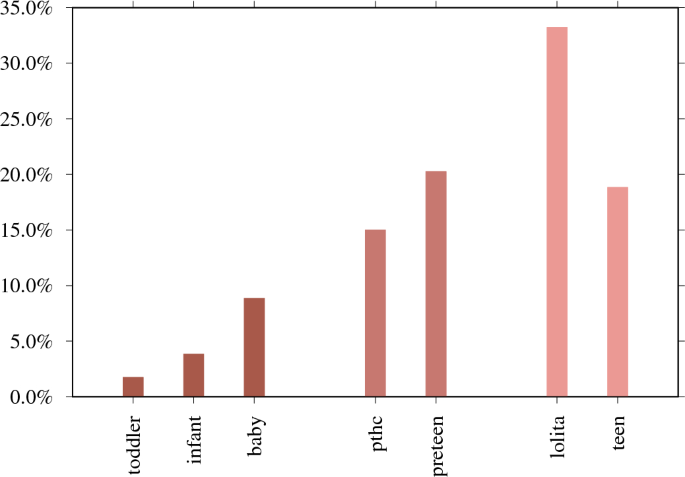
In the context of explicit CSAM search sessions, there are a total of 2,287,057 broad age-indicating searches with terms ‘toddler’, ‘infant’, ‘baby’, ‘pthc’ (preteen hardcore), ‘preteen’ (preadolescence, ages between nine and 12), ‘lolita’ (refers to a girl around 12–14 years old), and ‘teen’ (when included with CSAM terms).
How accessible is CSAM using Tor?
Based on result click statistics, we rank the top 26 most visited search engines online on 17 March 2023. To determine whether CSAM is permitted in search results, we test the searches ‘child’, ‘sex’, ‘videos’, ‘love’, and ‘cute’, then study the search results. 21 out of 26 search engines provide CSAM results. Four search engines even promote and advocate CSAM. One of them even states that ‘child porn’ is the number one search phrase. It is positive that five Tor search engines attempt to block CSAM. Yet, a user can utilise these search engines to locate other search engines and ultimately locate CSAM through the latter. Even if search engines block sites that directly share CSAM, it is still possible to find other entry points for onion sites that provide links to CSAM websites. With any major Tor website entrypoint, search engine, or link directory, a Tor user is only a few clicks away from CSAM content.
Self-help services are reaching users
When we study the searches, we discover that there are a few hundred queries from people who want to cease viewing CSAM and are concerned about their sexual interest in children, including queries ‘overcome child porn addiction’ and ‘how to stop watching child porn’ (see more in Supplementary Methods A.6 ).
When a person searches for CSAM, three prominent Tor search engines provide only links to self-help programmes for those who are concerned about their thoughts, feelings, or behaviours. The intervention of CSAM searches directs individuals away from CSAM and towards help. Data from one of the self-help websites indicates that CSAM users actively visit the website, and those who start the self-help programme are very likely to continue following the programme (see more in Supplementary Methods A.6 ). In the next section, we show that when we present a survey for those who search for CSAM, many reply with motivation to stop using CSAM.
Intervention for CSAM users
RQ3: What does the survey reveal about CSAM users?
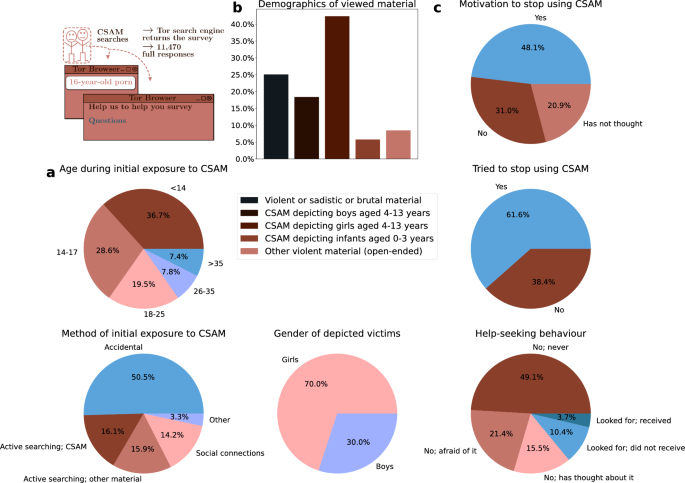
Our anonymous survey received responses from 11,470 individuals who sought CSAM on three popular Tor search engines. ( a ) The survey results indicate that 65.3% (N = 7199 of 11,030 who replied to the question) of CSAM users first saw the material when they were under 18 years old. 36.7% (N = 4048 of 11,030) first saw CSAM when they were 13 years old or younger. 50.5% (N = 4843 of 9599 who replied to the question) report that they first saw CSAM accidentally. ( b ) We asked the respondents what types of images and videos they view. Viewing CSAM depicting girls is more prevalent, with a ratio of 7:3. ( c ) The survey results indicate that 48.1% (N = 4120 of 8566 who replied to the question) of CSAM users are willing to change their behaviour to stop using CSAM, and 61.6% (5200 of 8447 who replied to the question) have tried to stop using CSAM. However, only 14.0% (N = 985 of 7013 who replied to the question) of CSAM users have sought help to stop using CSAM, and an even smaller portion of 3.7% (N = 257) have actually received help. Notably, 21.4% (N = 1498) are afraid to seek help.
Individuals who seek CSAM on Tor search engines answered our survey that aims at developing a self-help programme for them. Figure 5 aggregates statistics from the responses.
Most CSAM users were first exposed to CSAM while they were children themselves, and half of the respondents (N = 4843 of 9599 who replied to the question) first saw the material accidentally, demonstrating the accessibility and availability of CSAM online. Exposure to sexually explicit material in childhood is associated, inter alia, with risky sexual behaviour in adulthood 25 , sexual harassment perpetration 26 , and the normalisation of violent sexual behaviour 27 , and has been defined as an adverse childhood experience and a form of noncontact sexual abuse 28 .
We ask for information regarding two age ranges in the survey: zero to three years and four to 13 years. We structured the question with the intention of focusing on pre-pubescent children, aged 0–13. Respondents were able to specify the age in the option ‘Other violent material, what?’ The majority (60.7%, N = 5342 of 8796 who replied to the question) of respondents say they view CSAM depicting girls or boys aged between four and 13 years, indicating a preference for images and videos depicting prepubescent and pubescent children. Of the respondents, 69.7% (N = 3725 of 5342) say they view girls, compared to 30.3% (N = 1617 of 5342) who view boys. There is also a small group 5.8% (N = 506) of CSAM users with a preference for CSAM depicting infants and toddlers aged between zero and three years old. Additionally, 25.1% (N = 2205) reported viewing images and videos related to violent or sadistic and brutal material.
8.4% (N = 743) of respondents say they view ‘other violent material’, and 458 provide explanatory open-ended responses. 61.6% (N = 282) of these responses explicitly mention the age of children depicted in the CSAM viewed, providing N = 1637 mentions of age, as Fig. 6 illustrates. Most responses refer to age brackets, for example ‘over 12 years old’, in which we define this to mean 12–17. The most common age is 15-year-old (N = 234), followed by 16-year-old (N = 221), and 14-year-old (N = 209).
The survey data provides an age distribution that appears similar but is distinct from the search data (see statistical tests in Supplementary Methods A.5 ). The survey responses give the age ranges that respondents say they are interested in – whereas the search sessions reveal the precise age that people are most interested in. 54.5% of age-revealing CSAM search sessions target sexual content aimed at 12- to 16-year-olds. This survey’s age distribution yields an almost identical percentage: the range between 12 and 16 years old accounts for 56.8% (N = 929 mention age in this range from all 1637 mentioned ages).
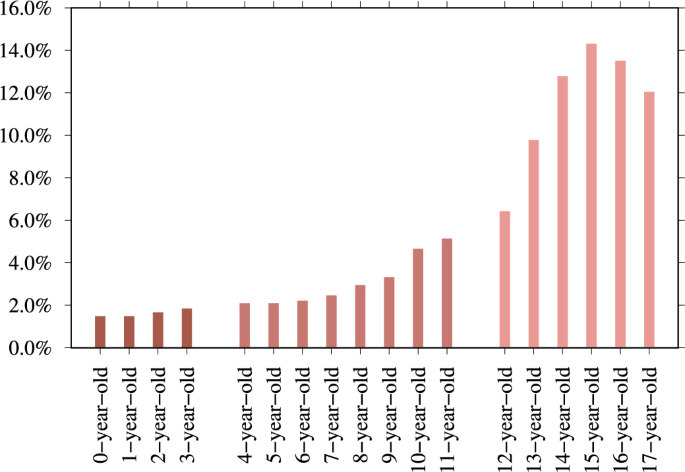
282 of the open-ended responses explicitly mention the age of children depicted in the CSAM viewed, providing 1637 mentions of age.
Our analysis of 458 open-ended responses for ‘Other violent material, what?’ supports the prevalence of viewing material depicting girls. 33.8% (N = 155) of the 458 open-ended responses explicitly mention the gender of children. 91.6% (N = 142) of the responses that mention gender refer to girls, and 30.3% (N = 47) refer to boys. 21.9% (N = 34) of the responses mention both girls and boys. Considering the quantitative and qualitative data together (N = 5488), viewing CSAM depicting girls (N = 3839, 70.0%) is more prevalent than viewing CSAM depicting boys (N = 1649, 30.0%), with a ratio of 7:3.
Overall, these findings are consistent with the latest Internet Watch Foundation’s Annual Report 2022 (see Supplementary Methods A.9 ).
CSAM users do want assistance
The Prevention Project Dunkelfeld offers clinical and support services to men who experience sexual attraction towards children and reaches these individuals with media campaigns 29 . Similarly, in collaboration with some legal adult pornography websites, including Pornhub , the Stop It Now! organisation alerts users who conduct CSAM searches of the illegality of their actions and directs them to help resources 21 .
Our results verify the feasibility of this type of intervention: a large proportion of CSAM users report that they want and have tried to change their behaviour to stop using CSAM. Almost half of the respondents report wanting to stop viewing CSAM monthly, weekly, or nearly every time (48.1%, N = 4120 of 8566 who replied to the question), and the majority of respondents report having tried to stop (61.6%, N = 5200 of 8447 who replied to the question). 31.0% (N = 2656) say that they do not want to stop, and 20.9% (N = 1790) say they have not thought about it.
Despite self-reported willingness and attempts to change behaviour, the fact that they are responding to the survey is evidence of their continued search for CSAM – albeit temporarily stepping away from CSAM to contemplate the concerns posed in the survey and provide a response. This raises the question of the commonalities between CSAM use and addiction. While addiction to the internet is not listed as a diagnostic disorder in the Diagnostic And Statistical Manual Of Mental Disorders, Fifth Edition, Text Revision (DSM-5-TR) 5 , there is extensive debate over whether problematic use of the internet – in particular in the context of legal pornography and CSAM use – can be considered an addiction. The International Classification of Diseases 11th Revision (ICD-11) includes compulsive sexual behaviour disorder, characterised by ‘persistent pattern of failure to control intense, repetitive sexual impulses or urges resulting in repetitive sexual behaviour’ – including repetitive use of legal pornography 30 .
Repetitive pornography use has similar effects to substance addiction 31 . Many people continually use CSAM and display addictive behaviours 32 , and the intensity of CSAM use often has properties that users call addictive 33 . In the search engine data, we notice that users who seek help often refer to their condition as ‘child porn addiction’. Understanding the commonalities between CSAM use and addiction is beneficial to prevention and treatment.
Help-seeking behaviour among CSAM users
Despite many respondents reporting that they would like to stop using CSAM, help-seeking behaviour among CSAM users remains low. Only 14.0% (N = 985 of 7013 who responded to the question) of CSAM users have sought help. Many report that they feel afraid to seek help (21.4%, N = 1498 of 7013), and the majority 64.6% (N = 4530 of 7013) report that they have not sought help.
Of those who have actively sought help to change their illicit behaviour, 73.9% (N = 728 of 985) have not been able to get help. This population has an unmet demand for effective intervention resources 34 . This may be due to a lack of awareness of the resources available 35 or because the available resources are not desirable. Recent studies 34 , 35 , 36 found the following barriers to seeking and receiving psychological services for child sexual offenders and people concerned about their sexual interest in children: fear of legal consequences; fear of stigmatisation; shame; affordability; and a perceived or actual lack of understanding by professionals.
The unmet demand for help resources demonstrates the urgent need for investment and further implementation of perpetration prevention programmes in order to effectively reach those who require intervention 37 .
Through bivariate analysis, we examine the associations between a number of covariates and the outcome of help-seeking in the survey data. We find the following to be determinants of help-seeking: duration and frequency of CSAM use; depression, anxiety, self-harming thoughts, guilt, and shame. We have only included the respondents with non-missing answers; for all results on determinants of help-seeking, see Supplementary Methods A.4 and Supplementary Tables.
Individuals who have used CSAM for a longer duration and those who use it more frequently are more likely to actively seek assistance to change their behaviour. There is an opportunity to intervene with those who have been viewing CSAM for a shorter duration in order to increase help-seeking at an earlier stage. Those who use CSAM more frequently may be more likely to seek help due to the detrimental impact that frequent use of CSAM may have on an individual’s daily life, including impaired social and occupational functioning and deep distress, which may be a strong motivator to seek help to reduce use of CSAM in order to improve life situations. Common reasons for seeking help for substance abuse include habitual use, taking a substance for a long time, and a need to take it daily 38 . Such driving factors for help-seeking appear to be similar in this sample of CSAM users. Respondents who face more difficulties in carrying out ordinary daily routines and activities are more likely to have sought help to stop using CSAM. Those who experience such difficulties daily have one of the highest rates of help-seeking.
RQ4: How can search engine-based intervention reduce child abuse?
We demonstrate that not only are CSAM websites widely hosted through the Tor network, but that they are also actively sought. However, in contrast, instead of watching CSAM, individuals voluntarily participate in the search engine-prompted survey. Consequently, even this intervention reduces CSAM usage.
We propose an intervention strategy based on our observation that some CSAM users do indeed recognise their problem. Even when CSAM users are seeking CSAM, they are willingly visiting self-help pages and continuing to study cognitive behavioural therapy information. Search engines, which are the main way people find onion sites, should start filtering CSAM and diverting people towards help to stop seeking CSAM. This is technically possible because of the accurate, text-based detection of CSAM that we demonstrate, and furthermore, the CSAM phrase detection list can be shared between search engines.
Lack of interdisciplinary research
Technical and non-technical scientists work in separate silos and publish in separate venues, and these venues – including their peer-review processes – promote these silos by focusing on technical or non-technical research. In the present era of 2024 – when the online environment is common and data facilitates innovative research – psychology journals display a hesitancy to publish articles that employ technical methodologies (such as a Naive Bayes classifier). This leads to a lack of an overall methodology to seek solutions to reduce child abuse and CSAM. Interdisciplinary research provides key insights to our work: we combine survey methods and social scientists with computer scientists to produce holistic research instead of fragmented views.
Unwillingness to acknowledge CSAM in the top-ranked computer science venues
How is it possible that there are so many studies classifying Tor websites and usage without addressing CSAM? A plausible explanation is that the researchers omitted the CSAM findings from their data without providing an explanation in the articles (i.e., ‘A Broad Evaluation of the Tor English Content Ecosystem 13 ’).
We find a big gap in relevant research in the top-ranked venues in the field of computer science. Prior investigations encompassed a limited number of scholarly articles of comparable calibre, and these yielded consistent results with our own: in 2013, a systematic analysis determined that 17.6% of onion websites distribute CSAM 1 , and in 2016, research revealed that CSAM websites are the most popular among Tor users 17 . However, despite these findings, computer scientists have continued to neglect CSAM distribution through the Tor network. Could this be due to the contentious nature of CSAM?
Computer scientists should evolve Tor and other anonymity networks so that the privacy goals are consistent with ethical and legal concerns 39 , 40 . Current peer-to-peer networks have essentially no remedies for widespread abuse; this is a problem that we intend to investigate in our future research.
Policy to combat CSAM and implement public health programmes for CSAM users
CSAM provides a paramount example of how technology can be used in harmful ways. As highlighted in the ninth report about model legislation and global review by the International Centre for Missing and Exploited Children 41 , a global effort must be further conducted to harmonise the legal and regulatory framework in the international arena.
Policies aimed at preventing the spread and use of online CSAM should be implemented. Situational Crime Prevention (SCP) is a criminological approach that employs five strategies and 25 techniques to reduce crime opportunities 42 . SCP has been shown to reduce criminal behaviour 43 , and these tactics might be effective against CSAM 44 . As an illustration, a study examining individuals who accessed a honeypot website that displayed pornography portraying adult actresses as children found that online warning messages offer an effective and scalable tactic to reduce access to CSAM 45 .
It is urgent to deploy public health programmes for CSAM users. These individuals are motivated to seek help, but the help is largely currently unavailable. There is a growing global epidemic of CSAM usage, and some describe masturbation and pornography as coping mechanisms to alleviate economic strain, feelings of isolation, depression, and anxiety 21 . Such public health prevention programmes should be initiated, financed, evaluated, and developed not by a single industry or actor but as part of a holistic approach. It must be the task of a broad range of actors to take responsibility for the prevention of sexual violence against children, including but not limited to governments, the technology industry, international organisations, and civil society.
Established in Germany, the Prevention Project Dunkelfeld offers cognitive behaviour therapy to improve coping skills, stress management, and control sexual attraction towards children 29 . The impact assessment of the ‘Stop It Now!’ campaign demonstrates the high effectiveness of the public health approach in preventing child sexual abuse. A series of awareness-raising films widely disseminated through media channels can successfully reach people concerned about their or others’ behaviour, directing them to help services. After establishing trust and committing to treatment, individuals who are sexually attracted to children can gain the ability to consistently regulate their impulses. The favourable confidentiality legislation in Germany, which prohibits therapists from disclosing planned or actual child abuse offences, naturally strengthens this trust. Project evaluation shows that post-treatment recidivism is lower among individuals who commit contact offences as opposed to child sexual abuse material users. This demonstrates the need to develop tailored interventions based on the offender’s background and behaviour.
Previous research indicates that anonymous online therapy reduces the use of CSAM: the Prevent It study, a clinical trial of an online therapist-supported cognitive behavioural therapy, indicates promising results in terms of the feasibility of dark web recruitment and the effectiveness of anonymous online interventions 46 . These public health programmes should offer in-person psychotherapy, anonymous online self-help material in all languages, anonymous online person-to-person support, and an overall drive towards treatment.
Participants
The study and its methods are in accordance with relevant guidelines and regulations. The Board of Suojellaan Lapsia, Protect Children ry. approved the experimental protocols with human participants, in accordance with the Declaration of Helsinki Ethical Principles for Medical Research Involving Human Subjects: (i) All participants in the Help us to help you survey have provided informed consent. (ii) These participants received clear information on the purposes of the study before beginning the survey. (iii) Without compensation, they volunteered to respond to the questions. (iv) No personal or identifiable information was collected. (v) The survey data is stored and managed exclusively by the research team at Suojellaan Lapsia, Protect Children ry. without anyone else – not even the co-authors – having access to the collected survey answers.
Previous research discovers how people find onion websites 12 : ‘The three most popular ways that almost half of our survey participants discovered onion sites by were via (i) social networking sites such as Twitter and Reddit (48%), (ii) search engines such as Ahmia, (46%) and (iii) randomly encountering links when browsing the Web (46%).’ Since Tor search engines serve as popular entry points to CSAM, we requested that search engines recruit Tor users who access CSAM to answer our survey.
Three prominent Tor search engines – Ahmia.fi , OnionLand, and Onion Search Engine – display our questionnaire to the user who searched for CSAM. In this research, we analyse the responses of users who searched for CSAM on Tor web search engines using at least one of the 179 search phrases used to find CSAM. The search phrases in English, Russian, Spanish, and Swedish are only used to locate CSAM, e.g., the term ‘childporn’. When a user submits a query containing any of these terms on one of these three Tor search engines, they are instead given the opportunity to voluntarily participate in the survey, which is available in 21 languages.
We may potentially be targeting a specific population due to the fact that the demographics of Tor users are probably not representative of all internet users. Furthermore, there is a possibility that the English-speaking population is overrepresented, as users who conduct their initial search in English may have limited vocabulary and thus be unable to identify our survey invitation in order to continue responding.
The participants in the sample are Tor users who (i) conducted a search for CSAM and (ii) opted to complete the survey; thus, they constitute a convenience sample. Although the sample is informative, it does not generalise to all CSAM users, and there is a high probability of selection effects at play. The absence of identifying information in the survey permits multiple responses from a single respondent. The trend of decreasing new responses over time suggests that users who have previously encountered the survey are less likely to respond to it.
The Help us to help you survey consists of 32 questions, takes about 15 to 20 minutes to complete, and participants receive no compensation. For this study, we analyse responses to 12 survey questions: 1, 2, 3, 4, 5, 7, 8, 13, 20, 22, 24, and 28 (see Supplementary Tables B).
The survey does not request any personally identifiable information from respondents – such as age, country, or gender – that would put privacy at risk. Questions avoid specifics of criminal conduct (e.g., time, date, place, or victim details). We ask CSAM users about their thoughts, feelings, and actions related to their use of CSAM so that in the future we can build a cognitive behavioural theory-based anonymous rehabilitation programme for CSAM users.
We included the term ‘illegal violent material’ for those respondents who do not categorise the material they view as CSAM but indicated to us via their search terms that they are in fact searching for material depicting sexual abuse of children.
We analyse responses from all participants who answered our Help us to help you survey from 5 May 2021 to 28 February 2023 (N = 11,470) and compare the tendencies and habits of people who searched for CSAM (see Supplementary Methods A.4 and Supplementary Tables).
Measuring CSAM hosted through the Tor network
In our study, we crawl webpages hosted on onion services. According to the Tor Project statistics, there were 693,683 onion domains on 1 January 2023 47 . Onion domains can and do provide any internet service; not all of them host websites.
In practice, we employ parallel crawlers to follow onion links on onion websites, which are subsequently fed to fresh crawlers. This allows us to continue harvesting in both depth and breadth. From 2018 to 2023, we collect online content from 176,683 unique onion domain addresses.
We investigate the years 2018–2023 and use a random sample of 10,000 unique onion domains for each year. Computer-generated random sampling guarantees the genuine randomness of our methods when we refer to random selection in this study. We then subject the text content to duplicate content filtering, phrase search, and classification. This returns the detected CSAM percentage for each year, as shown in Fig. 2 .
To extract only the textual content, we use the html2text Python library to convert the HTML pages to plain text representation. See an example of such a CSAM website in Fig. 2 and more examples in Supplementary Information A.3 .
In our textual representation of websites, we can see the file names for images and videos, and also their corresponding caption text (see detailed examples in Supplementary Methods A.3 ). Even websites that offer their full content only after authentication (see Supplementary Methods A.3 , Fig. 2 ) or behind a paywall serve limited CSAM samples immediately on the landing page.
It would be simple to do true, accurate validation by selecting a random sample of 1000 distinct domains that – according to the opening lines of the text – are unique websites, and opening these in the Tor Browser to see if they share CSAM. Although this is one possible assessment method and yields the ground truth, we do not download, open, or view any media content in this research, rather solely focus on textual data. Accessing CSAM websites would raise ethical, safety, and legal concerns, even in the context of academic research.
Web crawling as a method is biased towards websites that are frequently linked, and it cannot locate onion websites if there are no links to them. As a separate issue, the sampling includes onion websites that employ multiple alternative onion addresses. Despite the fact that we eliminate duplicates, a website with multiple publicly linked onion domains on other onion websites has not only a greater chance of being crawled but – through random sampling – there is also a higher likelihood of being selected for measurements. Therefore, our methodology favours and estimates popular linked onion websites with several domains – not all possible onion websites. By using a large dataset and continual onion link discovery, we minimise this bias.
Manual investigation
We randomly select the plain text representations of 1000 onion websites for each year, 2018–2023. We read the text content of these websites to determine whether they share CSAM and what the English vocabulary is for this type of page. Websites that share CSAM make this fact abundantly evident on the front page (see Supplementary Methods A.3 ), as well as through the use of explicit, distinct wording.
We have identified 22.1% (N = 221 of 1000) domain addresses that share CSAM in January 2023. We repeated this test for the years 2018–2022 (see Supplementary Methods A.3.1 ) and find that 19.5% (N = 195 of 1000) of onion domains possess CSAM in 2022, 27.2% (N = 272 of 1000) in 2021, and 19.0% (190 of 1000) in 2020. While in 2019, 10.8% (N = 108 of 1000) and in 2018, 9.0% (N = 90 of 1000) of onion domains shared CSAM.
Basic keyword search
Now, we randomly select 10,000 onion websites that were online in December 2022 and perform a basic case-insensitive keyword search (see Supplementary Methods A.1 ). This modest matching with 11 explicit CSAM phrases – including ‘child porn’, ‘childxxx’, ‘lolita’, ‘preteen’, and similar – produces 2642 domains from 10,000 onion domains.
When a website has multiple alternate onion domains, we eliminate duplicates. We execute the search against the content of these distinct websites. As expected, the algorithm returns a smaller subset – 2142 domains that present unique websites. The search returns 306 matches from these 2142 domains.
Manually reading the websites, we estimate the false positive (20 from 306, 6.5%) and false negative (6.0%) rates (see Supplementary Equations D). According to this keyword-based basic search with the stated false positive and false negative estimation, 18.5% of unique websites hosted through the Tor network share CSAM in December 2022.
Text-based CSAM detection classifiers
Using the NLTK Python library, we construct a naive Bayes classifier and a decision tree classifier (see Supplementary Methods A.2 ). To train classifiers, we manually produce representative CSAM (positive) and other (negative) website datasets. We curate 1006 pages from 306 unique CSAM websites and 6271 pages from 733 unique non-CSAM websites. These methods have simplistic designs and apparently unrealistic assumptions, but are known to be accurate for text classification; a naive Bayes classifier even outperforms sophisticated support vector machines (SVMs) in text classification, or reaches similar accuracy 48 , 49 . For us, they offer a clear benefit: we can understand and interpret them, and after training, output the detection phrases, combine them, and fine-tune a powerful detection algorithm.
Shareable text-based detection for CSAM
Our goal is to provide search engines with shareable matching phrases so that they can filter CSAM and we can continue to update the phrases. The classifiers use obvious phrases without much extra logic to match CSAM websites. This enables us to create a detection algorithm with 404 accurate English phrases (‘childxxx’, ‘childrenxxx’, ‘underage slut’, etc.). This is effective, as the vast majority of onion websites are written in English, and search data indicates that almost all users seek explicit material using English terminology.
While selecting the 404 phrases, we only include those that explicitly refer to sexual activity with children; therefore, we exclude phrases such as ‘baby love’ – although it does not generate false positives in the context of Tor. The inclusion of implicit terminology would give rise to ethical concerns about censorship.
A total of 32.5% (N = 35,751,619) of searches on Ahmia.fi include sexual phrases, and many of them implicitly might seek CSAM (i.e., ‘young teen girls sex’). Thus, the creator of the search engine – the first author of this paper – decided after the research in November 2023 to filter all sexual and suspicious searches, despite the collateral damage. This is in response to the widespread search and distribution of illegal child sexual abuse content via Tor, as opposed to legal pornography.
Measuring CSAM searches on the Tor search engine
We analyse search queries from a well-known public search engine for onion websites. Ahmia.fi provided us with a list of all search queries from February 2018 to February 2023. During these five years, search engine users performed 238,794,231 queries. We analyse these search phrases to determine what Tor users are seeking primarily from onion services.
We conducted limited initial experiments using small-scale interference techniques with our partner Tor search engine to prevent users from accessing CSAM. Hence, a priori we expected that users would seek little to no CSAM content because the search engine removes detected CSAM from search results; redirects users who search for such material using obvious terminology to seek assistance; and bans any sex-related queries, including legal ones. Nevertheless, in January 2023, 25 of the top 100 queries seek CSAM content, despite these previous interference techniques.
We examine searches (N = 238,794,231, Ahmia.fi , February 2018 – February 2023) from users seeking content from the Tor network and discover that explicit CSAM-related search phrases account for 6.7% of the queries (see separate analysis of individual queries in Supplementary Methods A.7 ).
Investigating the user’s search sessions
We track queries per user. We examine the entire search history to follow a total of 110,133,715 search sessions and study how many search sessions include at least one search phrase exclusive to underage content (see Supplementary Discussion C.1 ).
Even without cookies or IP addresses, it is simple to track a user’s searches by looking at the HTTP referring metadata. This means that the HTTP request for the new search includes the previous search. We assume that a user inputs new searches within five minutes of the last search. See an example snippet from the web server logs in Fig. 7 .
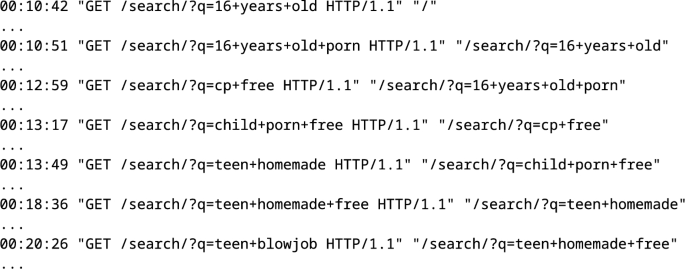
User-entered search phrases produce a search session in the HTTP logs.
During this illustrative search session, the user entered seven distinct queries, some of which reveal that the user is not only interested in teen sex by adults (age eighteen or nineteen) but also explicit underage sexual material:
16 years old → 16 years old porn → cp free → child porn free → teen homemade → teen homemade free → teen blowjob
Data availability
We believe that scientists should share research data whenever possible (e.g., when it does not violate GDPR or privacy, or when it does not weaponise attacks or sexual abuse). Our study employs the following three datasets: (i) website text data from the Tor network, (ii) web server logs from a search engine, and (iii) questionnaire responses from CSAM users. We do not share information that gives direct access to CSAM, such as the website text of onion websites (i) that share or link to CSAM. Although the web search logs (ii) do not necessarily contain personal information, it seems feasible to combine or extract such information from the data; thus, we do not release the web search logs. We release (iii) questionnaire responses from CSAM users and a step-by-step tutorial to help researchers become familiar with our survey data and replicate our findings ( Zenodo Open Science repository https://zenodo.org/doi/10.5281/zenodo.10457587 ). Supplementary Information includes Python code for the search using CSAM-related vocabulary, a Naive Bayes classifier, and p-value tests to determine the similarity between the distributions.
Guitton, C. A review of the available content on Tor hidden services: The case against further development. Comput. Hum. Behav. 29 , 2805–2815. https://doi.org/10.1016/j.chb.2013.07.031 (2013).
Article Google Scholar
Fox, J., Cruz, C. & Lee, J. Y. Perpetuating online sexism offline: Anonymity, interactivity, and the effects of sexist hashtags on social media. Comput. Hum. Behav. 52 , 436–442. https://doi.org/10.1016/j.chb.2015.06.024 (2015).
Quayle, E. & Taylor, M. Child Pornography: An Internet Crime (Routledge, 2004).
Book Google Scholar
Babchishin, K. M., Hanson, R. K. & VanZuylen, H. Online child pornography offenders are different: A meta-analysis of the characteristics of online and offline sex offenders against children. Arch. Sex. Behav. 44 , 45–66 (2015).
Article PubMed Google Scholar
Diagnostic and Statistical Manual of Mental Disorders, Fifth Edition, Text Revision (DSM-5-TR). https://doi.org/10.1176/appi.books.9780890425787 (2022).
Knack, N., Holmes, D. & Fedoroff, J. P. Motivational pathways underlying the onset and maintenance of viewing child pornography on the Internet. Behav. Sci. Law 38 , 100–116 (2020).
Sharpe, M. & Mead, D. Problematic pornography use: Legal and health policy considerations. Curr. Addict. Rep. https://doi.org/10.1007/s40429-021-00390-8 (2021).
Article PubMed PubMed Central Google Scholar
Insoll, T., Ovaska, A. K., Nurmi, J., Aaltonen, M. & Vaaranen-Valkonen, N. Risk factors for child sexual abuse material users contacting children online: Results of an anonymous multilingual survey on the dark web. J. Online Trust Saf. https://doi.org/10.54501/jots.v1i2.29 (2022).
Levine, B. N. Increasing the efficacy of investigations of online child sexual exploitation. https://www.ojp.gov/library/publications/increasing-efficacy-investigations-online-child-sexual-exploitation-report (2022).
Gallagher, K., Patil, S. & Memon, N. D. New me: Understanding expert and non-expert perceptions and usage of the tor anonymity network. In Thirteenth symposium on usable privacy and security, SOUPS 2017, Santa Clara, CA, USA, July 12-14, 2017 , 385–398 (USENIX Association, 2017).
Obada-Obieh, B., Spagnolo, L. & Beznosov, K. Towards Understanding Privacy and Trust in Online Reporting of Sexual Assault. In Sixteenth Symposium on Usable Privacy and Security, SOUPS 2020, August 7-11, 2020 , (eds Lipford, H. R. & Chiasson, S.) 145–164 (USENIX Association, 2020).
Winter, P. et al. How Do Tor Users Interact With Onion Services? In 27th USENIX Security Symposium, USENIX Security 2018, Baltimore, MD, USA, August 15-17, 2018 , (eds Enck, W. & Felt, A. P.) 411–428 (USENIX Association, 2018).
Zabihimayvan, M., Sadeghi, R., Doran, D. & Allahyari, M. A Broad Evaluation of the Tor English Content Ecosystem. In Proceedings of the 11th ACM Conference on Web Science, WebSci 2019, Boston, MA, USA, June 30 - July 03, 2019 , (eds Boldi, P. et al. ) 333–342, https://doi.org/10.1145/3292522.3326031 (ACM, 2019).
Jardine, E., Lindner, A. M. & Owenson, G. The potential harms of the Tor anonymity network cluster disproportionately in free countries. Proc. Natl. Acad. Sci. 117 , 31716–31721. https://doi.org/10.1073/pnas.2011893117 (2020).
Article ADS CAS PubMed PubMed Central Google Scholar
Aked, S. An investigation into darknets and the content available via anonymous peer-to-peer file sharing. 9th Australian Information Security Management Conference (2011).
Figueras-Martín, E., Magán-Carrión, R. & Boubeta-Puig, J. Drawing the web structure and content analysis beyond the Tor darknet: Freenet as a case of study. J. Inf. Secur. Appl. 68 , 103229. https://doi.org/10.1016/j.jisa.2022.103229 (2022).
Owen, G. & Savage, N. Empirical analysis of Tor hidden services. IET Inf. Secur. 10 , 113–118. https://doi.org/10.1049/iet-ifs.2015.0121 (2016).
Spitters, M., Verbruggen, S. & van Staalduinen, M. Towards a Comprehensive Insight into the Thematic Organization of the Tor Hidden Services. In IEEE Joint Intelligence and Security Informatics Conference, JISIC 2014, The Hague, The Netherlands, 24-26 September, 2014 , 220–223, https://doi.org/10.1109/JISIC.2014.40 (IEEE, 2014).
Dalins, J., Wilson, C. & Carman, M. J. Criminal motivation on the dark web: A categorisation model for law enforcement. Digit. Investig. 24 , 62–71. https://doi.org/10.1016/j.diin.2017.12.003 (2018).
He, S., He, Y. & Li, M. Classification of illegal activities on the dark web. In Proceedings of the 2nd International Conference on Information Science and Systems , 73–78 (2019).
Harris, M., Allardyce, S. & Findlater, D. Child sexual abuse and Covid-19: Side effects of changed societies and positive lessons for prevention. Crim. Behav. Ment. Health 31 , 289 (2021).
Steel, C. M., Newman, E., O’Rourke, S. & Quayle, E. Collecting and viewing behaviors of child sexual exploitation material offenders. Child Abus. Negl. 118 , 105133 (2021).
Blanchard, R. et al. Pedophilia, hebephilia, and the DSM-V. Arch. Sex. Behav. 38 , 335–350 (2009).
Anderson, S. E., Dallal, G. E. & Must, A. Relative weight and race influence average age at menarche: Results from two nationally representative surveys of us girls studied 25 years apart. Pediatrics 111 , 844–850 (2003).
Lin, W.-H., Liu, C.-H. & Yi, C.-C. Exposure to sexually explicit media in early adolescence is related to risky sexual behavior in emerging adulthood. PLoS ONE 15 , e0230242 (2020).
Article CAS PubMed PubMed Central Google Scholar
Brown, J. D. & L’Engle, K. L. X-rated: Sexual attitudes and behaviors associated with US early adolescents’ exposure to sexually explicit media. Commun. Res. 36 , 129–151 (2009).
Hunter, J. A., Figueredo, A. J. & Malamuth, N. M. Developmental pathways into social and sexual deviance. J. Family Violence 25 , 141–148 (2010).
Asmussen, K., Fischer, F., Drayton, E. & McBride, T. Adverse childhood experiences: What we know, what we don’t know, and what should happen next. Early Interv. Found. 129 (2020).
Beier, K. M. et al. Can pedophiles be reached for primary prevention of child sexual abuse? first results of the berlin prevention project Dunkelfeld (PPD). J. Forensic Psychiatry Psychol. 20 , 851–867 (2009).
The International Classification of Diseases 11th Revision (ICD-11) – 6C72 Compulsive sexual behaviour disorder. https://icd.who.int/browse11/l-m/en#/http://id.who.int/icd/entity/1630268048 (2022).
Laier, C., Pawlikowski, M., Pekal, J., Schulte, F. P. & Brand, M. Cybersex addiction: Experienced sexual arousal when watching pornography and not real-life sexual contacts makes the difference. J. Behav. Addict. 2 , 100–107 (2013).
Quayle, E. & Taylor, M. Model of problematic internet use in people with a sexual interest in children. Cyberpsychol. Behav. 6 , 93–106 (2003).
Quayle, E., Vaughan, M. & Taylor, M. Sex offenders, internet child abuse images and emotional avoidance: The importance of values. Aggress. Violent. Beh. 11 , 1–11 (2006).
Levenson, J. S., Willis, G. M. & Vicencio, C. P. Obstacles to help-seeking for sexual offenders: Implications for prevention of sexual abuse. J. Child Sex. Abus. 26 , 99–120 (2017).
Schmidt, A. F. & Niehaus, S. Outpatient therapists’ perspectives on working with persons who are sexually interested in minors. Arch. Sex. Behav. 51 , 4157–4178 (2022).
Grady, M. D., Levenson, J. S., Mesias, G., Kavanagh, S. & Charles, J. “I can’t talk about that’’: Stigma and fear as barriers to preventive services for minor-attracted persons. Stigma and Health 4 , 400 (2019).
Letourneau, E. J., Eaton, W. W., Bass, J., Berlin, F. S. & Moore, S. G. The need for a comprehensive public health approach to preventing child sexual abuse (2014).
Nebhinani, N., Sarkar, S., Ghai, S. & Basu, D. Reasons for help-seeking and associated fears in subjects with substance dependence. Indian J. Psychol. Med. 34 , 153–158 (2012).
Collier, B. & Stewart, J. Privacy worlds: Exploring values and design in the development of the tor anonymity network. Sci. Technol. Hum. Values 47 , 910–936. https://doi.org/10.1177/01622439211039019 (2022).
Sardá, T. An onion with layers of hope and fear: A cross-case analysis of the media representation of Tor network reflecting theoretical perspectives of new technologies. Secur. Priv. 6 , e296 (2023).
ICMEC. Child Sexual Abuse Material: Model Legislation and Global Review. 9th Edition. https://www.icmec.org/child-pornography-model-legislation-report/ (2018).
Clarke, R. V. Situational crime prevention. Crim. Justice 19 , 91–150 (1995).
Ho, H., Ko, R. & Mazerolle, L. Situational crime prevention (SCP) techniques to prevent and control cybercrimes: A focused systematic review. Comput. Secur. 115 , 102611. https://doi.org/10.1016/j.cose.2022.102611 (2022).
Krone, T. et al. Child sexual abuse material in child-centred institutions: situational crime prevention approaches. J. Sex. Aggress. 26 , 91–110. https://doi.org/10.1080/13552600.2019.1705925 (2020).
Prichard, J. et al. Effects of automated messages on internet users attempting to access “barely legal’’ pornography. Sex. Abus. 34 , 106–124 (2022).
Lätth, J. et al. Effects of internet-delivered cognitive behavioral therapy on use of child sexual abuse material: A randomized placebo-controlled trial on the Darknet. Internet Interv. 30 , 100590. https://doi.org/10.1016/j.invent.2022.100590 (2022).
Tor metrics – onion services. The Tor Project. https://metrics.torproject.org/hidserv-dir-v3-onions-seen.html?start=2022-11-23 &end=2023-01-03 (2023).
Yu, B. An evaluation of text classification methods for literary study. Lit. Linguistic Comput. 23 , 327–343. https://doi.org/10.1093/llc/fqn015 (2008).
Pranckevicius, T. & Marcinkevicius, V. Comparison of Naive bayes, random forest, decision tree, support vector machines, and logistic regression classifiers for text reviews classification. Balt. J. Mod. Comput. https://doi.org/10.22364/bjmc.2017.5.2.05 (2017).
Download references
Acknowledgements
This project has received funding from the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation programme under project numbers 804476 (SCARE) and 952622 (SPIRS). The survey data was collected under Suojellaan Lapsia, Protect Children ry. The Safe Online Initiative at End Violence is funding their ReDirection project.
Author information
Authors and affiliations.
Tampere University, FI-33720, Tampere, Finland
Juha Nurmi & Arttu Paju
Rochester Institute of Technology, Rochester, NY, 14623-5608, USA
Billy Bob Brumley
Suojellaan Lapsia, Protect Children ry., FI-00580, Helsinki, Finland
Tegan Insoll, Anna K. Ovaska, Valeriia Soloveva & Nina Vaaranen-Valkonen
University of Eastern Finland, FI-80101, Joensuu, Finland
Mikko Aaltonen
Consejo Superior de Investigaciones Científicas, 28014, Madrid, Spain
David Arroyo
You can also search for this author in PubMed Google Scholar
Contributions
J.N. led the article writing and administration. J.N. operates the Ahmia.fi Tor search engine. J.N. collected and analysed the Tor website and search engine data. J.N., N.V.V., and T.I. designed the research. T.I., A.O., and N.V.V. designed the survey. M.A. analysed the survey data. A.P. validated and verified our work and contributed to the figures. D.A. and J.N. wrote the discussion section. T.I., J.N., M.A., and B.B. proofread the article. B.B. acquired funding and edited the article. J.N.: Conceptualisation, Data curation, Formal Analysis, Investigation, Methodology, Project administration, Resources, Software, Supervision, Visualisation, Writing–original draft, Writing–review & editing. A.P.: Conceptualisation, Formal Analysis, Validation, Visualisation, Writing–original draft, Writing–review & editing. B.B.: Conceptualisation, Data curation, Funding acquisition, Project administration, Resources, Supervision, Writing–review & editing. T.I.: Conceptualisation, Investigation, Methodology, Project administration, Writing–original draft, Writing–review & editing. A.O.: Conceptualisation, Investigation, Methodology, Supervision. V.S.: Investigation, Writing–original draft. N.V.V.: Conceptualisation, Funding acquisition, Investigation, Methodology, Project administration, Resources, Supervision. M.A.: Data curation, Formal Analysis, Methodology, Validation, Writing–original draft, Writing–review & editing. D.A.: Funding acquisition, Writing–original draft, Writing–review & editing.
Corresponding author
Correspondence to Juha Nurmi .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary information., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Nurmi, J., Paju, A., Brumley, B.B. et al. Investigating child sexual abuse material availability, searches, and users on the anonymous Tor network for a public health intervention strategy. Sci Rep 14 , 7849 (2024). https://doi.org/10.1038/s41598-024-58346-7
Download citation
Received : 12 September 2023
Accepted : 27 March 2024
Published : 03 April 2024
DOI : https://doi.org/10.1038/s41598-024-58346-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.

IMAGES
VIDEO
COMMENTS
Introduction. Sexual violence remains a critical public health concern for students attending colleges and universities. The Centers for Disease Control and Prevention (CDC) defines sexual violence as "a sexual act that is committed or attempted by another person without freely given consent of the victim or against someone who is unable to consent or refuse." 1(p.11) Such acts range from ...
Table 1 includes discussion or review papers (n = 20) and Table 2 details empirical studies (n = 23). Table 1. Summary of discussion sources. Download CSV ... *Levine, J. A., & Dandamudi, K. (2016). Prevention of child sexual abuse by targeting pre-offenders before first offense. Journal of Child Sexual Abuse, 25, 719-737 ...
The volume of child sexual abuse materials in circulation both in the surface web as well as the hidden web have reached new highs, ranging in millions of images. 6 There is a risk that specialised responses to online child sexual abuse are conceived in isolation of proven strategies to address child sexual abuse in the physical, offline world.
Prevention Strategies. Sexual violence (SV) is a serious problem that can have lasting, harmful effects on victims and their family, friends, and communities. CDC's goal is to stop SV from happening in the first place. The solutions are just as complex as the problem. In order to prevent SV, we must understand and address risk and protective ...
Table 1. Prevalence of child sexual abuse by region from two meta-analyses, Andrews et al. 2004 and Stoltenborgh et al. 2011 (percentages) Table 2. Risks of child sexual abuse and exploitation Table 3. The impacts of child sexual abuse and exploitation Table 4. Common protective factors for child maltreatment Table 5.
Some form of sexual abuse — including inappropriate touching, incest, child pornography and rape — happens each year to 120 million girls age 18 and younger around the world, or 1 in 10.
Many states are trying to curb those numbers — 20 now require sexual abuse prevention education by law. In 2009, Vermont became one of the first. K-12 schools in Vermont are required to provide ...
To speak with someone who is trained to help, call the National Sexual Assault Hotline at 800.656.HOPE (4673) or chat online at online.rainn.org. There is no foolproof way to protect children from sexual abuse, but there are steps you can take to reduce this risk.
UNICEF/UN014958/Estey. Every year, millions of girls and boys around the world face sexual abuse and exploitation. Sexual violence occurs everywhere - in every country and across all segments of society. A child may be subjected to sexual abuse or exploitation at home, at school or in their community. The widespread use of digital ...
This finding is consistent with recent research on sexual assault prevention, including feminist self-defense and resistance training among high school and college students.[21-23] A recent review suggests that K-12 comprehensive sex ed has the qualities of effective prevention programs and has the potential to mitigate the risk factors ...
Abstract. This systematic review examined 140 outcome evaluations of primary prevention strategies for sexual violence perpetration. The review had two goals: 1) to describe and assess the breadth, quality, and evolution of evaluation research in this area; and 2) to summarize the best available research evidence for sexual violence prevention ...
Sexual violence starts early. More than 4 in 5 female rape survivors reported that they were first raped before age 25 and almost half were first raped as a minor (i.e., before age 18). Nearly 8 in 10 male rape survivors reported that they were made to penetrate someone before age 25 and about 4 in 10 were first made to penetrate as a minor.
Prevention of Child Sexual Abuse. Child sexual abuse and assault currently affect 1 in 4 girls and 1 in 20 boys in the United States. 1 The effects of child sexual abuse and assault are traumatic, long-lasting, and costly. Although rates of sexual abuse declined during the 1990s, they have plateaued in recent years, 2 suggesting a renewed effort is needed to protect children.
Specifically, we recommend: creating dialogue, not monologue, when teaching students; knowing your policy and conduct code; using technology to help engage students; teaching students that good sex begins with good communication; and. embracing the prevention year, not the prevention month (such as Sexual Assault Awareness Month during the ...
The importance of grooming the institution or 'institutional grooming' - a term coined by McAlinden (2006) - has emerged in recent studies of child sexual abuse. Institutional grooming involves perpetrators using features unique to the organisational setting to sexually abuse a child (McAlinden, 2006).
Although childhood sexual abuse was associated with a wide range of psychosocial and health outcomes, systematic reviews on only two psychiatric disorders (post-traumatic stress disorder and schizophrenia) and one psychosocial outcome (substance misuse) were of a high quality. Whether services should prioritise interventions that mitigate developing certain psychiatric disorders following ...
Furthermore, the societal costs of child sexual abuse are substantial, including increased healthcare expenses, lost productivity, and the perpetuation of cycles of abuse. Prevention Strategies for Child Sexual Abuse. Preventing child sexual abuse requires a multi-pronged approach that involves education, parental support, and community ...
Final persuasive essay child sexual abuse prevention mattison nicholson english department, southern new hampshire university amy manning october 17, 2021 every. Skip to document. ... Child sexual abuse prevention cannot be successful without raising awareness about the frequency of these crimes and the psychological trauma that can be caused ...
We also found that most of the abuse occurred on school property during the school day while school was in session, and that one third of the educators who perpetrated the CSA were gym teachers or coaches. The findings are discussed as they relate to policies for the prevention of child sexual abuse within educational settings.
The Child Sexual Abuse Accommodation syndrome (CSAAS), introduced by Roland Summit, M.D in 1983, is a simple and logical model to understand and accept the ways in which children react to sexual abuse. The followings are the five most typical reactions of child sexual abuse victims which is defined by CSAAS: Secrecy. Helplessness.
Here are some child abuse essay topics that we can suggest: The problem of child abuse in the US (Canada, the UK) Child abuse: Types and definitions. Child neglect crimes and their causes. Current solutions to the problem of sexual abuse of children. The importance of child maltreatment prevention programs.
Experiencing child sexual abuse is associated with increased risk for a range of short- and long-term negative effects. This short report defines and explores the annual incidence rates of child sexual abuse in the United States over 25 years between 1996 and 2021 (the most recent data released) and, comparatively, annual incidence rates of child maltreatment, more generally.
Beyond individual cases, we must also confront the broader cultural and systemic factors that enable sexual abuse to occur unchecked. This includes challenging harmful power dynamics, dismantling ...
This prospective study assesses the temporal relations between the 2 attachment dimensions of anxiety and avoidance and PTS among a treatment-seeking sample of female survivors of childhood sexual abuse. The independent variable in the study […] #MeToo: A Social Movement Against Sexual Abuse and Sexual Harassment.
This study identified 35 papers that were strictly limited to the prospect of AI interventions for online child sexual abuse. The review helped in deducing 3 major themes, namely, current trends in the field of AI for preventing online child sexual abuse, algorithm evaluation (advantages and disadvantages of AI tools) in preventing OCSA, and ...
Body. Abuse can be physical or psychological. Effects of physical abuse include isolation and depression. It can also lead to inability to engage in normal sexual behavior. Post traumatic stress disorder is a common psychological disorder among the victims. Sexually abused children more likely to develop deviant and promiscuous behavior.
Identify strengths and weaknesses of stakeholder current prevention practices; Create an action plan to improve the prevention of child sexual abuse within your organization/agency (internally) and throughout your community (externally) Registration deadline is June 27, 2024.
In April, the Pee Dee Coalition recognizes both Child Abuse Prevention and Sexual Assault Awareness Month to encourage families and surrounding communities to work together toward prevention.
Child Sexual Abuse Prevention Essay example. The purpose of this literature review is to evaluate the information that has been collected in the area of child sexual abuse prevention. From the research studies critically examined, a decision will be made as to what areas improvements need to be made in, in order to adequately outfit children ...
Tor is widely used for staying anonymous online and accessing onion websites; unfortunately, Tor is popular for distributing and viewing illicit child sexual abuse material (CSAM). From 2018 to ...