61 Internet Privacy Essay Topic Ideas & Examples
🏆 best internet privacy topic ideas & essay examples, 💡 good research topics about internet privacy, 📌 interesting topics to write about internet privacy.
- The Children’s Online Privacy Protection Act (COPPA) and the Children’s Internet Another negative aspect that raises opposition to COPPA and CIPA is the impossibility of controlling children in places other than home or a school library.
- What Are the Causes of the Increased Lack of Internet Privacy? Although every individual has the right to accuse the government and internet service providing companies over their failure to protect their customers’ privacy, individuals should recognize, they have a crucial duty to play as far […] We will write a custom essay specifically for you by our professional experts 808 writers online Learn More
- The Internet of Things: Revolutionizing Connectivity, Privacy, and Security The information that the devices may collect is first stored in the internal memory of a device and then sent into the gateway of IoT.
- The Decision of PIPA and SOPA and Internet Privacy Timm Trevor uses a lot of arguments against PIPA and SOPA and aims at the reader’s persuasion of the importance of this issue and he wants to impel the public to stop these bills.
- Ethical Issues of Internet Privacy Some of the methods include the use of interview schedules, where respondents are asked questions and the respondents respond directly while the researcher records the answers.
- Privacy and Fair Use Issues in Social Networking Sites Conceptually, section 2i of the “Terms of Use” grants Classmates.com the sweeping right to use any and all personal information in advertising on third-party sites: “Classmates may create applications or other tools for use on […]
- Personal Privacy of Employees at Workplaces: Internet Usage It is thus highly important that the employees of an organization understand the importance of the internet as a resource and efficiently utilize it for the betterment of the organization.
- Facebook as a Social Network and Its Privacy Policy The case study explains that the privacy policy and privacy settings on Facebook are such that they considerably violate the privacy of the social network’s users by selling their data to third parties for a […]
- Internet Issues: Teens, Social Media and Privacy I argue that it is our understanding of privacy that provides the solution and that the Internet is the biggest factor that influences it.
- Privacy Threats in Internet, Work and Drug Testing The analysis of the factors mentioned above and exploration of the way they influence one’s life is crucial to understanding the scope of activities violating one of the primary human rights the right to keep […]
- Internet Usage and Privacy in the Army Historically, the army had been banned from the use of the internet for communication or for socialization. From this time onwards, the army has been able to use the internet for communication and well as […]
- Web Privacy: What’s Happening Now? In addition, he has noted that the government and other stakeholders are not in a position to control or regulate the use of the internet in their area.
- PIPA and SOPA’ Decision on Internet Privacy The right to access information is fundamental in any open society, the and so is the protection of intellectual property. Gillmor’s sentiments are on point and I agree that the intention of the lawmakers was […]
- Social Network Services: Privacy Issues Drip’s first point is that the owners of the SNS can use targeted advertisements to gather information about users for greedy marketers, and the user is not protected against this.
- Effects of Social Networking on Privacy This has been attributed to the fact that on social networking sites, people do not need to meet physically to communicate.
- Government Internet Surveillance: Privacy Threat Perhaps the most troubling applications of the internet in current times are the mass surveillance efforts by the US government. The internet age has dramatically increased the ability of government to engage in surveillance.
- Computer Science: Threats to Internet Privacy Allegedly, the use of the Internet is considered to be a potential threat to the privacy of individuals and organizations. Internet privacy may be threatened by the ease of access to personal information as well […]
- The Privacy and Trust for Wireless Network Security Aim The aim of this project is to design and implement a completely secure wireless sensor network into each node of the wireless sensor network.
- Privacy on the Internet: A Critical Analysis The present paper looks into the issues of privacy on the Internet by analyzing literature on how to protect your computer and confidential information from such vulnerabilities.
- Privacy and Safety on the Internet The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information. The final security measure to ensure safety […]
- Web Privacy – Reliance on Internet Internet regulation imposes strict policies regarding the nature of the data collected, the specific purpose that does not serve to violate the interest of the users and using the data without the knowledge of the […]
- Anonymity and Internet Privacy: Reality or Myth
- Internet Privacy and the Threats of Internet Privacy
- Computer Ethical Controversies: Porn and the Right to Internet Privacy
- The Problem of Cookies and Internet Privacy
- Controversies About Cyberbullying and Internet Privacy
- The Relationships Between Cyberspace and Internet Privacy
- Correlation Between Data Protection and Internet Privacy
- Digital Freedom: The Question of Internet Privacy
- Reasons Why America Needs Internet Privacy Laws
- Google and Its Role in Internet Privacy
- Relations Between Internet Privacy and Business Ethics
- Overview of Internet Privacy and Email Issues
- Internet Privacy and Its Effects on the Internet
- The Link Between Internet Privacy and Personal Rights
- Internet Privacy and Its Importance
- Collisions of Internet Privacy and Personal Safety
- The Relationships Between Internet Privacy and Social Media Websites
- Internet Privacy and Security in the Digital Age
- The Problem of Internet Privacy Cookies and Privacy on the Internet
- Internet Privacy Concerns Versus Behavior: A Protection Motivation Approach
- Analysis of Moral Issues With Internet Privacy
- Internet Privacy, Cookies, and Data Mining Practices
- Perceived Internet Privacy Concerns on Social Network in Europe
- Internet Privacy: The Case of Edward Snowden
- Conflicts Between Personalized Ads and Internet Privacy
- Evaluating the Importance of Regulating Internet Privacy
- Internet Privacy: Government Should Not Regulate Encryption or Cryptography
- Linking Social Media Postings and the Internet Privacy
- Internet Privacy: How Long Until We Lose It All
- Stronger Internet Privacy Laws Are Unnecessary
- Internet Privacy: How Secure Are You When You’re Browsing the Internet
- The Digital Panopticon: Foucault and Internet Privacy
- Internet Privacy Policy and the Job That the Government Is Taking On
- Overview of the Issue Around Internet Privacy
- Internet Privacy: Analysis of Pros and Cons
- The Role and Importance of Internet Privacy Policy
- Internet Privacy Protection Laws: Have They Been Useful
- Why Internet Privacy Matters to Consumer
- Internet Privacy: Should More Be Done to Protect Privacy
- Internet Privacy vs. Job Seeking: Analysis of Contradictions
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 28). 61 Internet Privacy Essay Topic Ideas & Examples. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/
"61 Internet Privacy Essay Topic Ideas & Examples." IvyPanda , 28 Feb. 2024, ivypanda.com/essays/topic/internet-privacy-essay-topics/.
IvyPanda . (2024) '61 Internet Privacy Essay Topic Ideas & Examples'. 28 February.
IvyPanda . 2024. "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.
1. IvyPanda . "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.
Bibliography
IvyPanda . "61 Internet Privacy Essay Topic Ideas & Examples." February 28, 2024. https://ivypanda.com/essays/topic/internet-privacy-essay-topics/.
- Computers Essay Ideas
- Data Mining Titles
- Cyber Bullying Essay Ideas
- Hacking Essay Topics
- CyberCrime Topics
- Identity Theft Essay Ideas
- Online Community Essay Topics
- Internet of Things Topics
- Online Shopping Questions
- Viruses Research Topics
- Cyber Security Topics
- Safety Essay Ideas
- Cyberspace Topics
- Google Paper Topics
- Social Networking Essay Ideas

Why We Should All Be Concerned About Digital Privacy
by Jacqueline Lipton, author of Our Data, Ourselves: A Personal Guide to Digital Privacy
It may surprise many Americans to know that there is no expressly articulated right to privacy in the federal Constitution. In fact, as several Supreme Court justices implied recently in Dobbs v Jackson , a number of rights many of us assume we have may be on shaky ground as they are implied from combinations of other constitutional provisions such as the rights to free speech, due process, and equal treatment. To the extent that the Supreme Court takes a more literal or originalist interpretation of the constitution going forward, significant freedoms based on notions of privacy, personhood and autonomy may be under threat.

My book, Our Data, Ourselves: A Personal Guide to Digital Privacy , was written before the decision in Dobbs and focuses more generally on privacy in the digital world. However, one of the main reasons I wrote the book was to explain why we often do not have the rights we assume we do, and how we can become more aware of the information that others know about us in the digital age. I also offer practical tips for what individuals can do to better protect their personal data and digital privacy.
Privacy has been a thornier issue in the United States than in many other countries because our Constitution expressly protects free speech but doesn’t protect privacy, and the two values are often in tension. A law that restricts what information you can disseminate about someone else might be challenged under the First Amendment. Other countries, like Canada, New Zealand and the European Union member countries, enshrine both privacy and free speech in their bills of rights. To the extent the United States doesn’t hold up privacy as a constitutional value —except as implied in other sections of the Constitution— our lawmakers are at a disadvantage when they want to protect privacy. The legislative approach to privacy in the United States has been piecemeal and has only arisen in limited circumstances with respect to certain classes of sensitive data like health information, educational records, and financial information.
Many of us assume we must have a basic right to privacy (we don’t) that is protected by the constitution (it isn’t) and/or by other laws (sometimes). We are often surprised when we are confronted by targeted advertising—our digital devices seeming to know exactly what we’ve purchased, where we’ve been, or what goods or services we might like to purchase. Lots of people do not see any particular harm in these digital suggestions, which can actually be quite useful from the point of view of consumers who are bombarded with high volumes of information all the time. When Amazon makes a suggestion for the next book I might want to read based on my past browsing habits, or Netflix recommend the next movie or TV series, that can be helpful and save time.
But there are pros and cons to this convenience. While consumer suggestions and reminders can be helpful, the same aggregations of personal data can be used to cause harmful discrimination in education, employment, housing and law enforcement.
When surveyed about the importance of privacy in the abstract, most of us rate privacy highly. Yet, when confronted by discounts for goods or services —say, by joining loyalty programs— many of us will give away large volumes of personal information in return for a $5 discount on our next meal. And this data can be aggregated with other data about us from other sources, and then find its way into the hands of data brokers who will sell detailed dossiers to anyone prepared to pay for them. In other words, privacy has become a commodity. Most of us are not aware of how much personal information about us is available for purchase, let alone what role we may have played in enabling the collection of that data by clicking on “I agree” before reading a privacy policy or by failing to take simple precautions to protect sensitive data—like robust passwords changed regularly for online accounts.
The government has very little obligation to protect our private information, as a constitutional or policy matter. Recent high-profile investigations into the role of social media platforms like Facebook and Twitter evidence how little the government can—or at least is prepared to—do to curtail practices of corporate giants that trade in our private information. And the harms that can be caused by manipulation of personal data across social platforms are legion: Twitter and Facebook can and have been used to organize disruptions of our basic political processes.
Privacy rights are implicated in these activities because, in order to target political messages to sympathetic audiences, organizations need to know who will be sympathetic to them. That knowledge can only be obtained by having a window into individuals’ private lives, including their political and personal preferences. Most people don’t realize that the same sets of data that allow companies to target helpful advertisements to us can easily be used to subvert the political process.
In a world where Target’s marketing department knows you purchased a home pregnancy test before your parents or your partner do, the costs of not being able to have some measure of control over how that information is disseminated are higher than ever. While privacy is not, and may never be, a clearly protected right in the United States, the least we can do is educate ourselves about the risks of failing to understand who can access our data and for what purposes. And we can take certain steps to protect our personal data, in a society that doesn’t guarantee us this security.
TAGS: 9780520390508 , data privacy , data security , handbook , Jacqueline Lipton , Our Data Ourselves , personal guide
CATEGORIES: From Our Authors , Legal Studies , Technology Studies
About the Author

Jacqueline D. Lipton is a faculty member at the University of Pittsburgh School of Law whose research and writing focus on digital technology law. She is also the author of Law and Authors: A Legal Handbook for Writers, and has co-authored several editions of leading casebooks relating to cyberlaw as well as over 100 law review articles and several academic monographs (including Rethinking Cybleraw and Internet Domain Names, Trademarks and Free Speech ). She is a frequent presenter on these issues in both academic venues and in the media. She teaches a variety of courses including cyberlaw, intellectual property courses, commercial courses and legal writing.
- Share full article
Advertisement
Supported by
The Battle for Digital Privacy Is Reshaping the Internet
As Apple and Google enact privacy changes, businesses are grappling with the fallout, Madison Avenue is fighting back and Facebook has cried foul.

By Brian X. Chen
Listen to This Article
Open this article in the New York Times Audio app on iOS.
SAN FRANCISCO — Apple introduced a pop-up window for iPhones in April that asks people for their permission to be tracked by different apps.
Google recently outlined plans to disable a tracking technology in its Chrome web browser.
And Facebook said last month that hundreds of its engineers were working on a new method of showing ads without relying on people’s personal data.
The developments may seem like technical tinkering, but they were connected to something bigger: an intensifying battle over the future of the internet. The struggle has entangled tech titans, upended Madison Avenue and disrupted small businesses. And it heralds a profound shift in how people’s personal information may be used online, with sweeping implications for the ways that businesses make money digitally.
At the center of the tussle is what has been the internet’s lifeblood: advertising .
More than 20 years ago, the internet drove an upheaval in the advertising industry. It eviscerated newspapers and magazines that had relied on selling classified and print ads, and threatened to dethrone television advertising as the prime way for marketers to reach large audiences.
Instead, brands splashed their ads across websites, with their promotions often tailored to people’s specific interests. Those digital ads powered the growth of Facebook, Google and Twitter, which offered their search and social networking services to people without charge. But in exchange, people were tracked from site to site by technologies such as “ cookies, ” and their personal data was used to target them with relevant marketing.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data collection. Apple, citing the mantra of privacy, has rolled out tools that block marketers from tracking people. Google, which depends on digital ads, is trying to have it both ways by reinventing the system so it can continue aiming ads at people without exploiting access to their personal data.

If personal information is no longer the currency that people give for online content and services, something else must take its place. Media publishers, app makers and e-commerce shops are now exploring different paths to surviving a privacy-conscious internet, in some cases overturning their business models. Many are choosing to make people pay for what they get online by levying subscription fees and other charges instead of using their personal data.
Jeff Green, the chief executive of the Trade Desk, an ad-technology company in Ventura, Calif., that works with major ad agencies, said the behind-the-scenes fight was fundamental to the nature of the web.
“The internet is answering a question that it’s been wrestling with for decades, which is: How is the internet going to pay for itself?” he said.
The fallout may hurt brands that relied on targeted ads to get people to buy their goods. It may also initially hurt tech giants like Facebook — but not for long. Instead, businesses that can no longer track people but still need to advertise are likely to spend more with the largest tech platforms, which still have the most data on consumers.
David Cohen, chief executive of the Interactive Advertising Bureau, a trade group, said the changes would continue to “drive money and attention to Google, Facebook, Twitter.”
The shifts are complicated by Google’s and Apple’s opposing views on how much ad tracking should be dialed back. Apple wants its customers, who pay a premium for its iPhones, to have the right to block tracking entirely. But Google executives have suggested that Apple has turned privacy into a privilege for those who can afford its products.
For many people, that means the internet may start looking different depending on the products they use. On Apple gadgets, ads may be only somewhat relevant to a person’s interests, compared with highly targeted promotions inside Google’s web. Website creators may eventually choose sides, so some sites that work well in Google’s browser might not even load in Apple’s browser, said Brendan Eich, a founder of Brave, the private web browser.
“It will be a tale of two internets,” he said.
Businesses that do not keep up with the changes risk getting run over. Increasingly, media publishers and even apps that show the weather are charging subscription fees, in the same way that Netflix levies a monthly fee for video streaming. Some e-commerce sites are considering raising product prices to keep their revenues up.
Consider Seven Sisters Scones, a mail-order pastry shop in Johns Creek, Ga., which relies on Facebook ads to promote its items. Nate Martin, who leads the bakery’s digital marketing, said that after Apple blocked some ad tracking, its digital marketing campaigns on Facebook became less effective. Because Facebook could no longer get as much data on which customers like baked goods, it was harder for the store to find interested buyers online.
“Everything came to a screeching halt,” Mr. Martin said. In June, the bakery’s revenue dropped to $16,000 from $40,000 in May.
Sales have since remained flat, he said. To offset the declines, Seven Sisters Scones has discussed increasing prices on sampler boxes to $36 from $29.
Apple declined to comment, but its executives have said advertisers will adapt. Google said it was working on an approach that would protect people’s data but also let advertisers continue targeting users with ads.
Since the 1990s, much of the web has been rooted in digital advertising. In that decade, a piece of code planted in web browsers — the “cookie” — began tracking people’s browsing activities from site to site. Marketers used the information to aim ads at individuals, so someone interested in makeup or bicycles saw ads about those topics and products.
After the iPhone and Android app stores were introduced in 2008, advertisers also collected data about what people did inside apps by planting invisible trackers. That information was linked with cookie data and shared with data brokers for even more specific ad targeting.
The result was a vast advertising ecosystem that underpinned free websites and online services. Sites and apps like BuzzFeed and TikTok flourished using this model. Even e-commerce sites rely partly on advertising to expand their businesses.
But distrust of these practices began building. In 2018, Facebook became embroiled in the Cambridge Analytica scandal, where people’s Facebook data was improperly harvested without their consent. That same year, European regulators enacted the General Data Protection Regulation , laws to safeguard people’s information. In 2019, Google and Facebook agreed to pay record fines to the Federal Trade Commission to settle allegations of privacy violations.
In Silicon Valley, Apple reconsidered its advertising approach. In 2017, Craig Federighi, Apple’s head of software engineering, announced that the Safari web browser would block cookies from following people from site to site.
“It kind of feels like you’re being tracked, and that’s because you are,” Mr. Federighi said. “No longer.”
Last year, Apple announced the pop-up window in iPhone apps that asks people if they want to be followed for marketing purposes. If the user says no, the app must stop monitoring and sharing data with third parties.
That prompted an outcry from Facebook , which was one of the apps affected. In December, the social network took out full-page newspaper ads declaring that it was “standing up to Apple” on behalf of small businesses that would get hurt once their ads could no longer find specific audiences.
“The situation is going to be challenging for them to navigate,” Mark Zuckerberg, Facebook’s chief executive, said.
Facebook is now developing ways to target people with ads using insights gathered on their devices, without allowing personal data to be shared with third parties. If people who click on ads for deodorant also buy sneakers, Facebook can share that pattern with advertisers so they can show sneaker ads to that group. That would be less intrusive than sharing personal information like email addresses with advertisers.
“We support giving people more control over how their data is used, but Apple’s far-reaching changes occurred without input from the industry and those who are most impacted,” a Facebook spokesman said.
Since Apple released the pop-up window, more than 80 percent of iPhone users have opted out of tracking worldwide, according to ad tech firms. Last month, Peter Farago, an executive at Flurry, a mobile analytics firm owned by Verizon Media, published a post on LinkedIn calling the “time of death” for ad tracking on iPhones.
At Google, Sundar Pichai, the chief executive, and his lieutenants began discussing in 2019 how to provide more privacy without killing the company’s $135 billion online ad business. In studies, Google researchers found that the cookie eroded people’s trust. Google said its Chrome and ad teams concluded that the Chrome web browser should stop supporting cookies.
But Google also said it would not disable cookies until it had a different way for marketers to keep serving people targeted ads. In March, the company tried a method that uses its data troves to place people into groups based on their interests, so marketers can aim ads at those cohorts rather than at individuals. The approach is known as Federated Learning of Cohorts, or FLOC.
Plans remain in flux. Google will not block trackers in Chrome until 2023 .
Even so, advertisers said they were alarmed.
In an article this year, Sheri Bachstein, the head of IBM Watson Advertising, warned that the privacy shifts meant that relying solely on advertising for revenue was at risk. Businesses must adapt, she said, including by charging subscription fees and using artificial intelligence to help serve ads.
“The big tech companies have put a clock on us,” she said in an interview.
Kate Conger contributed reporting.
Brian X. Chen is the lead consumer technology writer for The Times. He reviews products and writes Tech Fix , a column about the social implications of the tech we use. Before joining The Times in 2011, he reported on Apple and the wireless industry for Wired. More about Brian X. Chen
A Guide to Digital Safety
A few simple changes can go a long way toward protecting yourself and your information online..
A data breach into your health information can leave you feeling helpless. But there are steps you can take to limit the potential harm.
Don’t know where to start? These easy-to-follow tips and best practices will keep you safe with minimal effort.
Your email address has become a digital bread crumb that companies can use to link your activity across sites. Here’s how you can limit this .
Protect your most sensitive accounts by creating unique passwords and adding extra layers of verification .
There are stronger methods of two-factor authentication than text messages. Here are the pros and cons of each .
Do you store photos, videos and important documents in the cloud? Make sure you keep a copy of what you hold most dear .
Browser extensions are free add-ons that you can use to slow down or stop data collection. Here are a few to try.
Home — Essay Samples — Information Science and Technology — Internet — The Importance of Internet Privacy
The Importance of Internet Privacy
- Categories: Internet Internet Privacy
About this sample

Words: 1017 |
Published: Oct 2, 2020
Words: 1017 | Pages: 2 | 6 min read
Table of contents
Introduction, threats to personal data and privacy, legal and ethical considerations, protecting your digital sanctuary, works cited.
- Strong Passwords: Employ strong, unique passwords for online accounts and consider using a password manager to securely store and manage them.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an additional layer of security to your online accounts.
- Mindful Sharing: Be cautious about the personal information you share online, especially on social media platforms. Review and adjust privacy settings to control who can access your data.
- Virtual Private Networks (VPNs): Utilize VPNs to encrypt your internet connection, making it more difficult for third parties to monitor your online activities.
- Regular Software Updates: Keep your operating system, browser, and security software up to date to protect against vulnerabilities that could be exploited by cybercriminals.
- Stay Informed: Stay informed about the latest threats and best practices for online privacy. Knowledge is a powerful defense against potential threats.
- Brown, M. (2018). Facebook is watching and tracking you more than you probably realize. Business Insider. https://www.businessinsider.com/facebook-is-tracking-you-through-apps-and-websites-2018-4
- Debatin, B., Lovejoy, J.P., Horn, A-K., & Hughes, B.N. (2009). Facebook and online privacy: Attitudes, behaviors, and unintended consequences. Journal of Computer-Mediated Communication, 15(1), 83-108.
- National Conference of State Legislatures. (2019). Security breach notification laws. https://www.ncsl.org/research/telecommunications-and-information-technology/security-breach-notification-laws.aspx
- Online Privacy (2018). Peggy J. Parks. Greenhaven Publishing LLC.
- Pew Research Center. (2021). Internet/Broadband Fact Sheet.
- Rosenbach, M., & Stolte, J. (2018). Can you have both security and privacy in the internet age? Harvard Business Review.
- Soltani, A. (2010). Why privacy matters: Debunking the nothing-to-hide argument. The Chronicle of Higher Education, 57(3), B26.
- Statista. (2022). Number of internet users worldwide from 2005 to 2021 (in millions). https://www.statista.com/statistics/273018/number-of-internet-users-worldwide/
- Winston & Strawn. (2017). Internet Privacy: An Overview of Federal Law. Lexology.
- Zavodny, M. (2017). Why does online privacy matter? Mercatus Center at George Mason University.

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Dr Jacklynne
Verified writer
- Expert in: Information Science and Technology Law, Crime & Punishment

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
5 pages / 2391 words
2 pages / 812 words
3 pages / 1579 words
2 pages / 985 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Internet
Valkenburg, P. M., & Peter, J. (2007). Online communication and adolescent well-being: Testing the stimulation versus the displacement hypothesis. Journal of Computer-Mediated Communication, 12(4), 1169-1182.
The excessive use of the internet has become a prevalent concern in today's digital age. The internet, once a revolutionary tool for communication and information, has now transformed into an integral part of our daily lives. [...]
Alton, L. (2017, May 15). Is Working From Home Making You Feel Miserable?. NBC news. Retrieved from https://www.inc.com/amy-morin/heres-why-internet-has-made-us-lonelier-than-ever.html
Hawkley, L., Cacioppo, J. (2010). Loneliness is a bodily function like hunger. AoBM.Anderson, W. A. (n.d.). The Impact of ICT on Loneliness in Elder Individuals. University of Alabama.Sharifpoor, E., Mohammadzadeh, M. J., & [...]
The internet is accessible to almost everyone from around the world. It can do many things, like helping people with things like fixing or building an item. The internet has many effects on people, but these effects are mostly [...]
Do you ever lose focus while reading? Find yourself constantly on your phone scrolling through emails, articles, and social feeds?The Shallows: What The Internet Is Doing To Our Brains by Nicholas Carr deeply examines the [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Digital privacy comes at a price. Here's how to protect it

Sharing personal data is an unavoidable part of digital connectivity. Image: rawpixel.com
.chakra .wef-1c7l3mo{-webkit-transition:all 0.15s ease-out;transition:all 0.15s ease-out;cursor:pointer;-webkit-text-decoration:none;text-decoration:none;outline:none;color:inherit;}.chakra .wef-1c7l3mo:hover,.chakra .wef-1c7l3mo[data-hover]{-webkit-text-decoration:underline;text-decoration:underline;}.chakra .wef-1c7l3mo:focus,.chakra .wef-1c7l3mo[data-focus]{box-shadow:0 0 0 3px rgba(168,203,251,0.5);} Robert Muggah

.chakra .wef-9dduvl{margin-top:16px;margin-bottom:16px;line-height:1.388;font-size:1.25rem;}@media screen and (min-width:56.5rem){.chakra .wef-9dduvl{font-size:1.125rem;}} Explore and monitor how .chakra .wef-15eoq1r{margin-top:16px;margin-bottom:16px;line-height:1.388;font-size:1.25rem;color:#F7DB5E;}@media screen and (min-width:56.5rem){.chakra .wef-15eoq1r{font-size:1.125rem;}} Cybersecurity is affecting economies, industries and global issues

.chakra .wef-1nk5u5d{margin-top:16px;margin-bottom:16px;line-height:1.388;color:#2846F8;font-size:1.25rem;}@media screen and (min-width:56.5rem){.chakra .wef-1nk5u5d{font-size:1.125rem;}} Get involved with our crowdsourced digital platform to deliver impact at scale
Stay up to date:, cybersecurity.
Listen to the article
- Data privacy exchanged for frictionless convenience is being compromised, stolen and leaked with disturbing regularity.
- People do not consciously put a price on their online privacy and most are unaware of how much data they are voluntarily sharing.
- We need a more coordinated approach across the public and private sector to tackle cyber security and enhance data protection.
The world is more wired than ever. Digital networks connect everything from office computers and bank accounts to baby monitors and pacemakers. Connectivity is blurring the lines between what is public and private. Privacies usually taken for granted – from web searches to heart-beats – are being steadily exploited in exchange for frictionless convenience. Meanwhile, personal data is being compromised, stolen and leaked with disturbing regularity. Promises made by cyber security companies of enhanced data privacy and protection ring hollow.
Have you read?
How to restore data privacy after the coronavirus pandemic, closing the trust gap: how responsible data use can accelerate a sustainable society, it's time to redefine how data is governed, controlled and shared. here's how.
Most people do not consciously put a price on their online privacy. But what if they did? A 2020 survey of Argentinians, Brazilians, Colombians, Mexicans, Germans and US citizens did precisely this. The Technology Policy Institute, a think tank, asked respondents how much a company would have to pay them each month to disclose various types of personal data. While the exact amounts varied across countries and categories – with Germans charging the most and US residents the least – the average came out to a surprisingly affordable $10, or $120 a year.
Yet most people are still unaware of just how much data they are voluntarily sharing, much less what is being syphoned from them involuntarily. But this is starting to change. The explosion of cyber attacks, especially ransomware, now makes the headlines. US companies are paying 400% more in ransom payouts in 2021 compared to 2019 . The average cost of a disclosed ransomware attack is a staggering $1.8 million , with companies forced to pay up or have millions of private records scattered across the internet. Predictably, cybersecurity insurance premiums are spiralling upward.
The pros and cons of a digitizing world
One reason people are sharing information is because it's an unavoidable part of joining the information superhighway. Today, there are over 4.6 billion active internet users, with billions more about to plug in. Social media platforms and search engines enlist billions of users a day who voluntarily part with their private information with the expectation it will “optimize” their experience.
All this digital onboarding has a dark side , including widening the exposure of governments, companies and citizens to an array of digital harms. There are signs that intrusive data harvesting and constant data theft is triggering a techlash. Sensing the shift in public mood, some tech companies are rolling-out new safeguards and reaping the benefits of surging demand for privacy.
Try as tech companies might to quell it, the popular push-back against surveillance capitalism is gathering pace. More and more people believe that their data is less secure than ever before. A 2019 survey of 24 countries found that 80% of respondents were concerned about online privacy, with one in four saying they did not trust the internet.
The World Economic Forum's Centre for Cybersecurity at the forefront of addressing global cybersecurity challenges and making the digital world safer for everyone.
Our goal is to enable secure and resilient digital and technological advancements for both individuals and organizations. As an independent and impartial platform, the Centre brings together a diverse range of experts from public and private sectors. We focus on elevating cybersecurity as a key strategic priority and drive collaborative initiatives worldwide to respond effectively to the most pressing security threats in the digital realm.
Learn more about our impact:
- Cybersecurity training: In collaboration with Salesforce, Fortinet and the Global Cyber Alliance, we are providing free training to the next generation of cybersecurity experts . To date, we have trained more than 122,000 people worldwide.
- Cyber resilience: Working with more than 170 partners, our centre is playing a pivotal role in enhancing cyber resilience across multiple industries: oil and gas , electricity , manufacturing and aviation .
Want to know more about our centre’s impact or get involved? Contact us .
Most Americans believe it is impossible to go through the day without having personal data harvested by governments or companies. Many are convinced that their online and offline lives are being tracked and monitored and that there is little they can do about it, which may help explain why they are so willing to part with it.
Mistrust of governments and companies also comes down to personal experience. The increase in cyber attacks and ransomware is undermining the binding glue of the internet: trust. According to one study , over 86% of all online consumers in 2020 were victims of some form of online fraud or data breach.
The relentless collection and reselling of personal data by private companies is hardly helping. Fewer people than ever believe they can safely and securely navigate online. This can lead to what researchers call “privacy self-defence” – withholding personal information, giving false biographical details or removing information from mailing lists altogether.
Building a more private and anonymous online experience
Forward-looking governments and companies are beginning to recognize that privacy has a price and some are developing solutions to protect it. They are responding to public calls to develop more stringent legislation, regulation and compliance to improve data protection and security. In democratic countries, at least, there is growing intolerance for intrusive harvesting and use of personal data, as the pushback against COVID-19-related contact tracing shows.
In most parts of the world, including more authoritarian corners, people value their anonymity and object to abuses of their privacy. More and more consumer groups , think tanks and universities are illuminating what governments and companies are doing with their data and how this contradicts data protection laws.

In a digitally-dependent world, securing data is more important than ever. A growing number of governments and companies recognize the importance of measuring and quantifying their data privacy and protection risks as evidenced by the European Union’s General Data Protection Regulation (GPPR), Brazil’s Marco Civil and California’s Consumer Privacy Act (CCPA), among others. Doing so can help avoid costly breaches, maintain a positive reputation and ensure compliance with basic laws and norms. Citizens too are starting to question whether the loss of privacy is worth the temporary convenience afforded by newly connected devices.
A privacy mindset is essential. One way to help mitigate exposure is through digital distancing . This includes using virtual private networks with no-log policies as well as Tor – free and open-source software that enables anonymous communication – in order to conceal user location and use from intrusive network surveillance. Encrypted emails are also essential, especially from providers and platforms that can neither read nor track user content. Regulating app permissions, installing ad blockers and avoiding social media altogether are well-known strategies to bolster online privacy and reduce one's digital footprint.
Preparedness is vital in a world of cascading digital threats . More than ever, governments, companies and international organizations – not just individuals – need to design-in digital defences while also managing their digital presence. Installing cyber security software is only the start. Privacy amplification and managed attribution technologies can help reinforce and strengthen data protection. At a time of persistent and omnipresent online surveillance and digital malfeasance, data security needs to be built at both the enterprise and the user levels. Minimizing exposure and maximizing privacy is a core value proposition.
Don't miss any update on this topic
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
Related topics:
The agenda .chakra .wef-n7bacu{margin-top:16px;margin-bottom:16px;line-height:1.388;font-weight:400;} weekly.
A weekly update of the most important issues driving the global agenda
.chakra .wef-1dtnjt5{display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;-webkit-flex-wrap:wrap;-ms-flex-wrap:wrap;flex-wrap:wrap;} More on Cybersecurity .chakra .wef-nr1rr4{display:-webkit-inline-box;display:-webkit-inline-flex;display:-ms-inline-flexbox;display:inline-flex;white-space:normal;vertical-align:middle;text-transform:uppercase;font-size:0.75rem;border-radius:0.25rem;font-weight:700;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;line-height:1.2;-webkit-letter-spacing:1.25px;-moz-letter-spacing:1.25px;-ms-letter-spacing:1.25px;letter-spacing:1.25px;background:none;padding:0px;color:#B3B3B3;-webkit-box-decoration-break:clone;box-decoration-break:clone;-webkit-box-decoration-break:clone;}@media screen and (min-width:37.5rem){.chakra .wef-nr1rr4{font-size:0.875rem;}}@media screen and (min-width:56.5rem){.chakra .wef-nr1rr4{font-size:1rem;}} See all

China outlines new plans for industrial cybersecurity - and other cybersecurity news to know this month
Akshay Joshi
March 21, 2024

3 trends set to drive cyberattacks and ransomware in 2024
Scott Sayce
February 22, 2024

'Operation Cronos' seizes major cybercrime group – and other cybersecurity news to know this month
February 21, 2024

LockBit: How an international operation seized control of ‘the world’s most harmful cybercrime group’
Kate Whiting

How to secure the modern cyber supply chain and surge in third-party risks amid AI automation
Anna Sarnek
February 19, 2024

What does 2024 have in store for the world of cybersecurity?
Aleksandr Yampolskiy
February 15, 2024

Essay on Internet Privacy
Students are often asked to write an essay on Internet Privacy in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Privacy
Understanding internet privacy.
Internet privacy is about protecting your personal data online. It’s important because when you use the internet, you share information that others could misuse.
Why is Internet Privacy Important?
Internet privacy is crucial to protect your identity and personal information. Without it, strangers could access your data, leading to potential harm.
How to Maintain Internet Privacy?
You can maintain internet privacy by using strong passwords, enabling privacy settings on social media, and avoiding sharing sensitive information online. Always remember, your online safety is in your hands.
250 Words Essay on Internet Privacy
Introduction to internet privacy.
Internet privacy, often synonymous with online privacy, is a subset of data privacy focusing on the protection of personal information in the digital realm. As the internet becomes increasingly integral to our daily lives, privacy issues have surged to the forefront of societal discourse.
The Importance of Internet Privacy
Internet privacy is crucial for numerous reasons. It safeguards personal data, prevents identity theft, and preserves freedom of speech. In the era of digitalization, a breach in privacy can lead to damaging consequences, ranging from financial loss to emotional distress.
Threats to Internet Privacy
Threats to internet privacy are manifold. They include cybercriminal activities, surveillance by government agencies, data mining by corporations, and even seemingly innocuous social media platforms that collect and utilize user data.
Internet Privacy: A Human Right?
Many argue that internet privacy is a fundamental human right. This perspective highlights the need for stringent laws and policies to protect individuals from intrusive surveillance and unauthorized data collection.
The Role of Individuals in Protecting Privacy
While legislation plays a vital role, individuals must also take proactive steps to safeguard their online privacy. This can include using encrypted communication, regularly updating software, and being mindful of the information shared online.
Internet privacy is a complex and critical issue in the digital age. The collective efforts of individuals, corporations, and governments are necessary to ensure the protection of personal information in the online sphere. As we continue to navigate this interconnected world, the importance of internet privacy will only increase.
500 Words Essay on Internet Privacy
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is crucial for numerous reasons. Primarily, it protects individuals’ identity and personal information from potential cybercriminals. With the rise of the digital economy, people are increasingly sharing their sensitive data online, making them vulnerable to identity theft, cyberstalking, and other forms of cybercrime. Internet privacy also ensures the freedom of speech and thought online, as it allows individuals to express their views without fear of being tracked or monitored.
Despite its importance, internet privacy is under constant threat. Cybercriminals often exploit security breaches to steal sensitive data. Also, many online platforms and services thrive on data collection, often without clear consent from users. Governments, too, may infringe upon internet privacy for surveillance and security purposes.
The Role of Legislation in Internet Privacy
Legislation plays a crucial role in protecting internet privacy. Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of attempts to regulate data collection and usage. However, enforcing these laws across borders is challenging, and loopholes often exist that allow for continued privacy infringements.
Individual Responsibility and Internet Privacy
While legislation is important, individual responsibility is equally critical in ensuring internet privacy. Users should be aware of the data they share online and the potential risks involved. They should also use privacy-enhancing tools, such as Virtual Private Networks (VPNs), secure browsers, and encryption, to protect their data.
Conclusion: The Future of Internet Privacy
The future of internet privacy is uncertain. On one hand, advancements in technology, such as blockchain and quantum computing, could potentially enhance data security. On the other hand, the increasing digitization of our lives threatens to erode privacy further. The challenge lies in finding a balance between the benefits of the digital age and the preservation of privacy. As we move forward, the discourse on internet privacy will remain a pivotal aspect of our digital lives.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Uses and Abuses of Internet
- Essay on These Days Exposure to Television and Internet
- Essay on Internet Influence on Kids
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Entertainment
- Environment
- Information Science and Technology
- Social Issues
Home Essay Samples Social Issues
Essay Samples on Internet Privacy
The issue of artificial intelligence and intrusion of privacy.
In an era driven by technological advancements, artificial intelligence (AI) has emerged as a powerful tool with far-reaching implications. While AI offers numerous benefits, including improved efficiency and enhanced decision-making, it also raises concerns about the intrusion of privacy. This essay delves into the complex...
- Artificial Intelligence
- Internet Privacy
Internet Privacy Nowadays: Challenges, Implications, and Measures to Safeguard
The modern era is marked by an unprecedented level of connectivity and information exchange, facilitated by the internet. However, as we revel in the benefits of this digital age, a crucial concern looms large – internet privacy. The rapid advancement of technology has brought forth...
Advantages and Disadvantages of Internet Censorship: Unveiling the Web
Introduction In this paper, I will be discussing the internet, the advantages and disadvantages of internet censorship, and how we can effectively control and censor the content on the web, in particular, the problems arising due to censorship. Definitely, Internet Censorship is a hot topic...
- Internet Censorship
The Dystopian Reality: How Technology is Turning Us into 1984
Technology has greatly impacted our lives and it has become a great resource for us. It is beneficial to our society, even though there are some effects we are not aware on how it's affecting us. George Orwell’s novel, 1984, describes the totalitarian government of...
- Disadvantages of Technology
Issue Of Internet Privacy And Open-Public Wifi
As everyone's been saying, the conventional wisdom is that open/public (o/p) WiFi is terribly dangerous and should be avoided at all costs because anyone can just intercept your packets and read them, whereas with WPA2, the packets are encrypted. For this reason, it is often...
Stressed out with your paper?
Consider using writing assistance:
- 100% unique papers
- 3 hrs deadline option
Privacy and the Dangerous of Insider Threats in the Public
You may know of a time when someone leaked personal information to the public. Have you ever thought that the information you were looking at was stolen or used against somebody? Well in fact events like this happen a lot and it could be happening...
- Computer Hacking
The Way How Google Single-handedly Makes Our Society Lazy, Both Physically And Mentally
In an era where all the world’s information is at our finger tips, it is very difficult to imagine life before the internet. Google can challenge your life for many reasons, it effects your brain, test scores, physical activities, jobs, mental health, and conveniences to...
Evolution of Social Networking Services and Their Privacy Intrusion
Since the dawn of civilization, social connections and networks have been a keystone of humanity. Social connections are a key part of success, from feudal alliances to modern day, who you know has proven to be just as, if not more important than what you...
- Network Security
- Social Networking
The Impact of Piracy on Business Profitability
What Does Piracy Mean? Piracy refers to the unauthorized or illegal reproduction of copyrighted content which is then sold at very low prices in the 'grey' market. Over the years, as the ease of access to technology increased, piracy has become more frequent. For instance,...
- Music Piracy
National Security Concern of Internet Privacy and the Onion Routing
Internet help connect people worldwide as a powerful communication and information sharing platform. However, as the internet “requires the collection of certain data from individuals who visit web sites—such as Internet address—in order for the site to operate properly”, every data the users provide may...
- National Security
Internet Privacy as the Serious Privacy Breach
In life, everyone has the secrets of personal life that they are unwilling to let others know. This secret is legally called privacy, such as personal privacy, diary, photographic album, living habits, communication secrets, physical defects, and the like. Their own secret is unwilling to...
- Cyber Crime
Dehumanisation of Human Privacy due to Loss of Internet Privacy
In today’s world, computers have essentially implemented themselves into almost every internet capable technological device, including but not limited to smart watches and virtual reality. These devices track the entity’s internet activity without their knowledge, thus invading their privacy. Due to this state of continual...
Easy Guide To Private Proxies
Although free proxies may not have a monthly subscription fee or a large one-time fee, they still are useful to their developers and owners. They generate value through consumer use. It is possible for free proxy providers to inject trackers into users’ computers once they...
The Significant Role Of Internet Privacy
Privacy is a facility for someone to secure themselves and personal information or any other things that one’s wanting to protect from people, and thereby express themselves all these things selectively. There are many things that we use for our need related to technology like...
Overview Of The Internet And Its Governing System
This research seeks to explain the Internet, its associated issues and threats and the governing bodies that are established to ensure that all procedures, accessibility and operation of the Internet successful. The Internet is “a global computer network providing a variety of information and communication...
Best topics on Internet Privacy
1. The Issue of Artificial Intelligence and Intrusion of Privacy
2. Internet Privacy Nowadays: Challenges, Implications, and Measures to Safeguard
3. Advantages and Disadvantages of Internet Censorship: Unveiling the Web
4. The Dystopian Reality: How Technology is Turning Us into 1984
5. Issue Of Internet Privacy And Open-Public Wifi
6. Privacy and the Dangerous of Insider Threats in the Public
7. The Way How Google Single-handedly Makes Our Society Lazy, Both Physically And Mentally
8. Evolution of Social Networking Services and Their Privacy Intrusion
9. The Impact of Piracy on Business Profitability
10. National Security Concern of Internet Privacy and the Onion Routing
11. Internet Privacy as the Serious Privacy Breach
12. Dehumanisation of Human Privacy due to Loss of Internet Privacy
13. Easy Guide To Private Proxies
14. The Significant Role Of Internet Privacy
15. Overview Of The Internet And Its Governing System
- Gender Inequality
- Discrimination
- Gender Equality
- Civil Rights
- Women's Rights
- Environmental Justice
- Transphobia
- Black Power Movement
- Sex Trafficking
Need writing help?
You can always rely on us no matter what type of paper you need
*No hidden charges
100% Unique Essays
Absolutely Confidential
Money Back Guarantee
By clicking “Send Essay”, you agree to our Terms of service and Privacy statement. We will occasionally send you account related emails
You can also get a UNIQUE essay on this or any other topic
Thank you! We’ll contact you as soon as possible.

Search form
A for and against essay about the internet.
Look at the essay and do the exercises to improve your writing skills.
Instructions
Do the preparation exercise first. Then read the text and do the other exercises.
Preparation

Check your writing: grouping - ideas
Check your writing: gap fill - useful phrases, worksheets and downloads.
What's your opinion? Do you think the internet is bad for young people?

Sign up to our newsletter for LearnEnglish Teens
We will process your data to send you our newsletter and updates based on your consent. You can unsubscribe at any time by clicking the "unsubscribe" link at the bottom of every email. Read our privacy policy for more information.

An official website of the United States government
Here’s how you know
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
Take action
- Report an antitrust violation
- File adjudicative documents
- Find banned debt collectors
- View competition guidance
- Competition Matters Blog
New HSR thresholds and filing fees for 2024
View all Competition Matters Blog posts
We work to advance government policies that protect consumers and promote competition.
View Policy
Search or browse the Legal Library
Find legal resources and guidance to understand your business responsibilities and comply with the law.
Browse legal resources
- Find policy statements
- Submit a public comment

Vision and Priorities
Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC.
Technology Blog
Best practices in building tech capacity in law enforcement agencies.
View all Technology Blog posts
Advice and Guidance
Learn more about your rights as a consumer and how to spot and avoid scams. Find the resources you need to understand how consumer protection law impacts your business.
- Report fraud
- Report identity theft
- Register for Do Not Call
- Sign up for consumer alerts
- Get Business Blog updates
- Get your free credit report
- Find refund cases
- Order bulk publications
- Consumer Advice
- Shopping and Donating
- Credit, Loans, and Debt
- Jobs and Making Money
- Unwanted Calls, Emails, and Texts
- Identity Theft and Online Security
- Business Guidance
- Advertising and Marketing
- Credit and Finance
- Privacy and Security
- By Industry
- For Small Businesses
- Browse Business Guidance Resources
- Business Blog
Servicemembers: Your tool for financial readiness
Visit militaryconsumer.gov
Get consumer protection basics, plain and simple
Visit consumer.gov
Learn how the FTC protects free enterprise and consumers
Visit Competition Counts
Looking for competition guidance?
- Competition Guidance
News and Events
Latest news, ftc announces impersonation rule goes into effect today.
View News and Events
Upcoming Event
Second scams against older adults advisory group meeting.
View more Events
Sign up for the latest news
Follow us on social media
--> --> --> --> -->

Playing it Safe: Explore the FTC's Top Video Game Cases
Learn about the FTC's notable video game cases and what our agency is doing to keep the public safe.
Latest Data Visualization
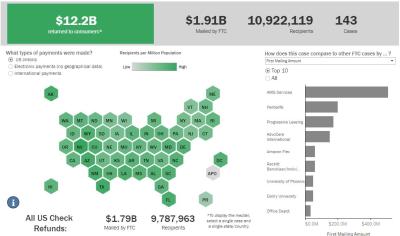
FTC Refunds to Consumers
Explore refund statistics including where refunds were sent and the dollar amounts refunded with this visualization.
About the FTC
Our mission is protecting consumers and competition by preventing anticompetitive, deceptive, and unfair business practices through law enforcement, advocacy, and education without unduly burdening legitimate business activity.
Learn more about the FTC

Meet the Chair
Lina M. Khan was sworn in as Chair of the Federal Trade Commission on June 15, 2021.
Chair Lina M. Khan
Looking for legal documents or records? Search the Legal Library instead.
- Cases and Proceedings
- Premerger Notification Program
- Merger Review
- Anticompetitive Practices
- Competition and Consumer Protection Guidance Documents
- Warning Letters
- Consumer Sentinel Network
- Criminal Liaison Unit
- FTC Refund Programs
- Notices of Penalty Offenses
- Advocacy and Research
- Advisory Opinions
- Cooperation Agreements
- Federal Register Notices
- Public Comments
- Policy Statements
- International
- Military Consumer
- Consumer.gov
- Bulk Publications
- Data and Visualizations
- Stay Connected
- Commissioners and Staff
- Bureaus and Offices
- Budget and Strategy
- Office of Inspector General
- Careers at the FTC
Privacy on the Internet: The Evolving Legal Landscape
* The views expressed here are those of the author, and not necessarily of the Federal Trade Commission or any Commissioner.
I. INTRODUCTION
The Internet has transformed from a communications link among defense researchers to a network providing millions of users easy access to a wealth of information, goods, and services. Currently, it is estimated that more than 120 million Americans have access to the Internet, and that foreign users recently surpassed U.S. ones in numbers. (1) In part, the exponential growth in the online consumer market has propelled the Internet's extraordinary growth. As the Federal Trade Commission (FTC) noted in its July 1999 report to Congress, online commerce tripled from approximately $3 billion in sales in 1997 to approximately $9 billion in 1998. (2) Annual consumer sales are projected to skyrocket from $15 billion in 1999 to $184 billion in 2004. (3)
The Net is transforming not just our economy but also our society and our notions of privacy. While the Internet provides a goldmine of information, products, and services to consumers, the Internet also is a rich source of information about consumers. Internet sites collect substantial amounts of personal information, both directly through registration pages, survey forms, order forms, and online contests, and indirectly through software products such as "cookies" and other types of tracking software. (4) By following consumers' online activities, Internet site owners and other data collectors gather significant information about visitors' personal interests and preferences. Such consumer data have proven to be extremely valuable to online companies -- they enable online marketers to target products and services tailored specifically to the interests of individual consumers and permit companies to boost their revenues by selling the data or selling advertising space on their Internet sites. (5) An entire industry has emerged to market a variety of software products designed to assist Internet sites in collecting and analyzing visitor data and in serving targeted advertising. (6)
Ultimately, the prevalence, ease, and relatively low cost of collecting, maintaining, and disseminating personal consumer information has a Janus-faced aspect. On the one hand, the ability to gather, process, and disseminate information on the Internet provides consumers with a wealth of benefits (e.g., Web sites can "remember" where a consumer has been and what type of products the consumer likes so that when the consumer returns to the site, s/he can be directed to additional products that are likely to interest him/her). On the other hand, darker voices are legitimately concerned that the manipulative use of information available on the Net may adversely affect privacy or citizenship. (7) Some uses of personal data can be intrusive, as when private information is widely circulated; or reckless, as when inaccurate information is widely shared with other people and companies; or predatory, as when the information is used to target victims for a scam or crime.
For over five years, the Federal Trade Commission has actively monitored developments in e-commerce, particularly those affecting consumer privacy. The FTC has supported industry self-regulation and taken enforcement actions as needed. The FTC also has endorsed certain legislative initiatives (e.g., the Children's Online Privacy Protection Act) to address specific online privacy concerns. As I will explain below, there is no simple choice between self-regulation or legislation as the anointed vehicle for protecting consumers' privacy. We already have both and will continue to need both in the future.
II. PRIVACY ON THE INTERNET -- THE EVOLVING LEGAL LANDSCAPE
In the United States, individual privacy, including online privacy, is protected through a combination of constitutional guarantees, federal and state statutes, regulations, and voluntary codes of conduct, all of which apply to the public and private sectors in different ways. Although the U.S. Constitution does not explicitly mention a right to privacy, the Supreme Court decades ago recognized a fundamental right to privacy or the right to be left alone. (8) It subsequently interpreted the Bill of Rights as creating, through a penumbra of various rights, "a right of personal privacy or a guarantee [that] certain zones of privacy [do] exist under the Constitution." (9) Viewed in hindsight, the federal courts have effectively acknowledged a right to privacy with respect to marital relations, procreation, contraception, family relationships, and child rearing and education. (10) In addition, a number of state constitutions specifically enumerate the right of citizens to be protected from privacy invasions. (11)
Aside from constitutional guarantees, the U.S. legislative approach to privacy has been traditionally sectoral, that is, privacy law has developed to address particular data types and users. (12) Historically, fear of the government's use of personal data was the primary concern. Certain statutes thus limit the use of personally identifiable data that the government maintains. (13) Other statutes limit the government's use of personal data maintained by industry. (14) And some statutes limit firms' use of personal data. (15) While no single law or regulation specifically recognizes a U.S. citizen's general right to informational privacy, certain laws as applied do afford a fair amount of such privacy to consumers.
Section 5 of the Federal Trade Commission Act (16) in particular can protect consumers' informational privacy whenever a company collects or disseminates personal data in an unfair or deceptive manner. For example, in August 1998, the Commission brought its first online privacy case against GeoCities. (17) In that case, the Commission was concerned that GeoCities, one of the Web's most frequently visited sites, (18) collected personal identifying information from its members, both adults and children, and misled them as to its use of that information. When visitors become members, they must fill out an online application that requires disclosure of certain personal identifying information and requests optional information regarding education level, income, marital status, occupation, and interests. Through the registration process, GeoCities created a database rich with target markets for advertisers. The Commission alleged in its complaint that GeoCities falsely represented that the mandatory information that members provided would not be released to third parties without permission. In addition, GeoCities collected personal identifying information from children, for whom it promotes a GeoKidz Club (19) that offers activities, contests, and games. The FTC charged that GeoCities misrepresented that it alone maintained this identifying information from children, when in fact a third party collected and maintained it.
Ultimately, GeoCities settled the case by agreeing to disclose prominently on its Web site just what information it is collecting, for what purpose, to whom it will be disclosed, and how consumers can inspect and, if desired, remove their personal information from the databases of third parties. The consent order also prohibits GeoCities from misrepresenting who is sponsoring the various activities offered on its Web site and who actually is collecting and maintaining personal information. Finally, to protect children, the order requires GeoCities to obtain parental consent before collecting information from those age 12 or younger, and to delete any such information already collected, unless GeoCities obtains affirmative parental consent to retain it.
The comprehensive GeoCities consent agreement helped establish some of the key elements of fair information practices that protect consumers' online privacy. Those elements include: 1) notice of the site's privacy practices; 2) consumer choice regarding the use of information collected; 3) consumer access to correct or remove personal information;
4) safeguarding the security of information; 5) parental control over the collection and use of information gathered from children and 6) an enforcement mechanism to ensure compliance. (20) These are precisely the types of protections that the Commission has been urging Web site operators to provide voluntarily through self-regulation. (21) These same principles also served as the foundation for the Children's Online Privacy Protection Act (COPPA) that was enacted in 1998 (see infra). (22)
Another recent case illustrating Section 5's ability to protect informational privacy is the Commission's action against ReverseAuction.com. (23) ReverseAuction is an online site that features "Declining Price" Auctions (that is, the initial, opening price of an item drops the longer the item remains up for auction) and "Wanted" Auctions (that is, buyers who are looking for a particular item or service indicate how much they are willing to pay for the item or service, and sellers then try to outbid each other by offering lower prices). The Commission charged that the firm violated consumers' privacy by harvesting consumers' personal information from a competitor's site and then sending deceptive spam to those consumers, soliciting their business.
In essence, what was alleged is that, in promoting its new site, ReverseAuction registered with eBay.com, a competitor auction site. ReverseAuction agreed to be bound by eBay's User Agreement and Privacy Policy, which protect consumers' privacy by prohibiting eBay users from gathering and using personal identifying information (such as names and email addresses) for unauthorized purposes such as spam. Notwithstanding that agreement, ReverseAuction harvested eBay's users' personal identifying information and used the data to send them spam promoting ReverseAuction's own web site. ReverseAuction indicated that the spam recipient's eBay user ID would expire soon when in fact it was in no danger of expiring. But by using this deceptive tactic, ReverseAuction lured eBay users to its web site where they could "re-register." The Commission also claimed that consumers believed that eBay had provided their eBay user IDs and other information to ReverseAuction, or at least had authorized these practices. In reality, eBay had no idea that ReverseAuction was engaging in these activities. At the end of the day, those who "re-registered" their eBay user IDs at ReverseAuction's site were simply registering with and becoming a member of ReverseAuction.com with their eBay IDs now also serving as their ReverseAuction IDs.
The proposed settlement bars ReverseAuction from making any misrepresentations about complying with another company's user agreement, privacy policy, or other provisions that govern the collection, use, or disclosure of consumers' personal identifying information. In addition, ReverseAuction will be barred from making any misrepresentations about the features, terms, conditions, business practices, or privacy policy of any other company. Furthermore, the proposed settlement requires ReverseAuction to send an e-mail message to all consumers to whom it had sent spam, explaining that ReverseAuction had not intended to suggest that consumers' eBay user IDs would expire and stating that eBay did not know about and had not authorized any of ReverseAuction's actions. The e-mail will inform consumers that their names and eBay user IDs can be purged from ReverseAuction's database and their registration canceled. Finally, the proposed settlement requires ReverseAuction to post its own privacy policy on its Internet web site and maintain certain records to enable the FTC to monitor compliance with the proposed settlement.
This case illustrates both Section 5's broad authority and the Commission's commitment to protecting consumers' privacy online whenever that privacy is threatened. Here, the FTC was able to ensure that the privacy protections assured to eBay's users were not compromised when the deceptive tactics of a competitor auction site thwarted eBay's self-regulatory efforts to protect consumers' privacy. Without actions such as this one, consumers will lose confidence about whether their privacy choices will be honored. And, with consumer confidence one of the biggest threats to e-commerce in general, cases such as this one are essential for fostering the continuing growth of e-trade.
In addition to the Federal Trade Commission Act, a few other federal statutes, such as the Fair Credit Reporting Act (FCRA) (24) and Title V of the Gramm-Leach-Bliley Act, (25) provide a certain amount of informational privacy protection. While these statutes, particularly the FCRA, may have been conceived for an off-line world, they function to protect the privacy of both on- and off-line consumers. Indeed, it is becoming increasingly difficult to meaningfully protect privacy without addressing concerns in both the real and virtual worlds. This will become even more true as companies begin to merge online and offline consumer data and profiles.
First enacted in the 1970s, the FCRA regulates consumer reporting agencies, also known as credit bureaus, and establishes important protections for consumers with respect to the privacy of their sensitive financial information that credit bureaus hold. The FCRA allows credit bureaus to disclose consumer credit reports only to entities with specified "permissible purposes" (such as evaluating individuals for credit, insurance, employment, or other, similar purposes). Moreover, these disclosures can only occur under specified conditions (such as certification of need from a prospective employer or insurer). In these ways, the FCRA generally limits the disclosure of consumer reports primarily to instances where a consumer initiates a transaction, such as a loan or employment application. Of course, these processes can now occur completely online.
There are certain caveats associated with the FCRA. First, in contrast to credit bureaus with their rich, accurate and up-to-date data collections, individual merchants, both on- and off-line, are free to distribute any information that they collect as part of their discrete transactions or experiences with consumers. (26) Second, the 1996 amendments to the FCRA include a provision that permits "affiliated" companies to share consumer reports, so long as consumers are notified and given the opportunity to prevent such sharing. (27) Sharing credit(?) information among affiliated companies may well raise special concerns in the electronic banking or electronic payments context, where detailed and sometimes sensitive information about consumers is gathered.
Congress recently enacted financial privacy provisions in Title V of the Gramm-Leach-Bliley Act, which add to the legal protections available for consumers' financial information. Under Title V, banking institutions may share personal confidential financial information with their affiliates, but not with third parties such as online marketers, unless consumers are first notified and given the option to require the banking institution to keep all information private. (28) Even with respect to affiliated entities, Title V requires financial institutions to disclose their privacy policies to their customers, including any intent to share nonpublic personal information.
Finally in the extremely sensitive area of medical records, the Department of Health and Human Services recently issued proposed regulations establishing the first-ever national standards to protect health information that is transmitted or maintained electronically. (29) Among other things, the proposal would require an individual's written consent to release medical information for purposes unrelated to treatment and payment. A notable loophole in the proposed rules is that the rules would not protect health information if it is transmitted or maintained solely via traditional, paper records.
Specific, federal protections for consumer privacy on the Internet are fairly limited. (30) Most notably, last year's Children's Online Privacy Protection Act (COPPA) requires that operators of Web sites directed to children under 13 or who knowingly collect personal information from children under 13 must: 1) provide parents notice of their information practices; 2) obtain prior, verifiable parental consent for the collection, use, and/or disclosure of personal information from children (with certain limited exceptions); 3) upon request, provide a parent with the ability to review the personal information collected from his/her child; 4) upon request, provide a parent with the opportunity to prevent the further use of personal information that has already been collected, or the future collection of personal information from that child;
5) limit collection of personal information for a child's online participation in a game, prize offer, or other activity to information that is reasonably necessary for the activity; and 6) establish and maintain reasonable procedures to protect the confidentiality, security, and integrity of the personal information collected. (31)
The Act directs the Commission to adopt regulations implementing these requirements and on November 3, 1999, the Commission published its final rule incorporating and explaining COPPA's privacy protections. (32) The Rule also provides a safe harbor for operators who follow Commission-approved self-regulatory guidelines. Moreover, the Commission retains its authority under Section 5 of the FTC Act to investigate and enforce against any child-related information practices that are deceptive or unfair. (33)
COPPA is a classic example of federal legislation aimed at protecting a particular privacy problem -- children's information privacy on the Internet. The lack of much additional federal legislation protecting Internet privacy stems from several sources. First, there is no consensus that one general approach solves all privacy problems. Some believe that firms should always seek consumers' consent before sharing their personal data (the opt-in advocates). Others believe that it is more efficient and beneficial for all involved if firms are allowed to share consumers' personal data so long as they notify consumers and enable them to prevent such sharing before it occurs (the opt-out advocates). Alternatively, it may prove most desirable to have opt-in (affirmative consent) rules for certain types of sensitive data sharing (e.g., medical information) and opt-out rules when less sensitive data is being shared or when there is a broad consensus that such sharing is useful for both consumers and firms.
Second, there is a general reluctance to create a plethora of national or state laws for an inherently global technological environment. There is a legitimate concern that an explosion of various sovereigns' laws regulating the Net would only create conflicts of laws rather than resolve issues of privacy invasion. In addition, there has been at least a tentative conclusion that existing laws such as Section 5 of the Federal Trade Commission Act, combined with self-regulation, may be adequate to protect personal informational privacy on the Net. But that tentative consensus may be falling apart, as businesses and consumers recognize the serious harm that hackers, fraud artists and sheer mistakes can wreak with personal financial and identifying information. Moreover, businesses are beginning to worry about the specter of fifty different state law standards as legislators attempt to respond to citizens' concerns about identity theft and privacy invasions. (34)
III. CURRENT FEDERAL POLICY ON INTERNET PRIVACY
The choice of either legislating privacy on the Net or fostering self-regulation is a false one. In fact, we already have both. However, there are legitimate reasons why federal policy regarding privacy on the Internet thus far has favored a self-regulating cyberspace marketplace.
Given the rapidly evolving nature of the Internet and computer technology, self-regulation is certainly the least intrusive and may be the most efficient means to ensure fair information practices. (35) Voluntary codes are by definition developed and adopted by those with the greatest expertise about and sensitivity to industry practices and conditions. And self-regulatory codes can be revised when necessary, more promptly than legislative codes. This allows firms to respond quickly to the rapid evolution of the Internet and computer technology and to employ emerging technologies to protect consumers' privacy. Moreover, when regulation is voluntarily-adopted, compliance tends to be broader, and enforcement more prompt than when a legislature or agency imposes its mandate. And self-regulation wholly avoids many of the First Amendment issues associated with governmental regulation. Finally, where an industry can regulate itself, the government need not devote as many of its limited resources to the task.
Self-regulatory efforts, of course, may fail -- they may not be rigorously implemented or enforced, or they may lapse into a vehicle for exclusionary or collusive conduct among rivals. Businesses may be reluctant to disclose to consumers what they do with personal data, simply to avoid having to compete for customers based on how firms protect personal data. Government vigilance is therefore appropriate and necessary, especially where business rivals, who have an incentive to restrain competition, are involved in the process.
The Commission's numerous activities to monitor industry efforts to protect consumers' privacy include public workshops, Commission Task Forces, creation of an Advisory Group, and surveys of web sites' privacy practices. The Commission's most recent workshop, jointly sponsored by the U.S. Department of Commerce, focused on online profiling. (36) This workshop, examined the use of "cookies" and other types of tracking software -- and even methods of combining this information with personal information collected directly from consumers or contained in other databases -- to create targeted, user-profile based advertising campaigns. Some maintain that no personally identifiable information is collected by this profiling -- at most the profile is of a browser with no knowable street or e-mail address or name. But consumer groups and privacy advocates have raised concerns about these practices, primarily because many consumers are unaware that software is used to create online profiles about them. Privacy advocates believe that consumers should at least be given notice that such profiling is occurring and given the choice of whether an online profile can be created, maintained, and used. I confess to having some sympathy with that position.
The Commission has also used Task Forces to grapple with various Internet privacy issues such as understanding the costs and benefits of implementing fair information practices online. The costs and benefits of granting consumer access to their online information and guaranteeing the security of personal information have been particularly contentious. Indeed, the benefits and costs are interrelated insofar as increased access to information, at least with today's technology, tends to undermine the security and integrity of the data.
To better address this dilemma, the Commission recently announced the establishment of the Advisory Committee on Online Access and Security. (37) The Advisory Committee is to examine what constitutes reasonable access to personal information, including whether the extent of access provided by Web sites should vary, depending upon the sensitivity of the personal information collected and/or the purpose for which such information is collected. It will consider whether consumers should be provided access to enhancements to personal information (e.g., inferences about their preferences or purchasing habits). Other issues are whether appropriate and feasible methods exist for verifying the identity of individuals seeking access and whether the difficulty and costs of retrieving consumers' data should be considered. Finally, should a reasonable fee be assessed for access and should limits be placed on the frequency of requests for access?
On the security side, the Committee will consider how to define appropriate standards for evaluating the measures taken by Web sites to protect the security of personal information. That is, what constitute reasonable steps to assure the integrity of this information and what measures should be undertaken to protect against its unauthorized use or disclosure? By May 2000, the Advisory Committee will prepare a written report presenting options for implementing these fair information practices along with the costs and benefits of each option.
Finally, the Commission continues to monitor through surveys the progress of firms' privacy efforts and to assess whether self-regulatory programs are in fact fulfilling their promise. The results of past surveys of commercial web sites suggest that online businesses are increasingly providing more notice of their information practices. The Commission's 1998 survey found that only 14% of the sites surveyed posted any disclosure regarding their information practices, and even fewer -- 2% -- posted a comprehensive privacy policy. The "most popular" web sites performed better -- 71% had posted an information disclosure practice or notice. (38) A year later, two other, independent surveys found that 66% of 361 busy web sites surveyed posted at least one disclosure about their information practices, while 93% of the 100 top web sites did. (39) Unfortunately, these same surveys found that very few sites (10 to 22%) posted disclosures covering all five of the fair information practice principles. (40) Thus, major challenges remain for effective self-regulation.
In March 2000, Commission staff will conduct a new Internet survey to assess the progress that commercial web sites have made in implementing all of the fair information practices (notice, choice, access, security, and enforcement) (41) and to try to get beneath the surface to determine whether online privacy practices are adequate for enabling consumers to exercise choice about how their personal information is collected and shared. (42) Commission staff will analyze what information a domain collects; whether a privacy policy is posted and what it covers; whether a recognized seal is posted; and whether third party advertisers attempt to place cookies on the site's visitors' computers. Staff hopes to issue its findings in a report by mid-summer.
If self-regulation is to succeed, another critical issue is how to create incentives to encourage the development of privacy-enhancing technologies that will give consumers more control over how and when their personal data is collected and used. One such technology is the Web's Consortium's Platform for Privacy Preferences (P3P). (43) The P3P platform would enable web sites to present their privacy policies in such a way that consumers' computers could automatically "read" the policies and automatically "release" information to sites that conform to consumers' pre-programmed choices on acceptable privacy policies. The P3P protocol, however, is still in the drafting stage.
IV. THE U.S. APPROACH TO PRIVACY VERSUS THE E.U. APPROACH
The U.S. approach to protecting consumer privacy online -- relying significantly on industry self-regulation with a minimum of legislative and administrative mandates -- differs from that of the European Union (E.U.), which relies more on legislative protections. In particular, the E.U. passed a Directive in 1995 that extensively regulates the buying and selling of personal data. (44) This Directive, which took effect on October 25, 1998, specifies common rules that firms must observe when collecting, holding, or transmitting personal data in their business or administrative activities. Most fundamental for firms is an obligation to collect data only for specified, legitimate purposes and to hold only data that are relevant, accurate, and up-to-date. European citizens, in turn, are guaranteed a bundle of rights -- a right of access to their personal data; a right to correct any data that are inaccurate; the right to refuse use of their data for activities such as direct marketing; and a right of recourse if unlawful processing occurs.
Significant for the U.S. is that the Directive prohibits the transfer of personal data to any country that does not provide "adequate" (meaning "comparable") protection. Each E.U. member country has been enacting its own laws to implement the Directive. It is still too early to know how stringent the various E.U. member states' laws and policies will be; how strictly they will be enforced; or how flexible their contemplated system of exemptions and special conditions for individual companies will be. Nevertheless, the Directive may impose substantial restrictions on U.S. subsidiaries who buy and sell personal data in the E.U., or on firms that acquire and transmit personal data to the United States.
The U.S. and the E.U. are currently in negotiations to determine how best to harmonize the different approaches taken to protect personal data. They have been working on developing "safe harbors" that establish a set of criteria which, if met, would allow U.S. companies to do business with European citizens or firms. (45) These "safe harbors" would require U.S. firms to provide: notice of their information practices; choice as to whether and how personal information may be disclosed to third parties; onward transfer of personal data to third parties, consistent with the notice and choice provided; security for personal data, whether at its creation, maintenance, use, or transmission; access by individuals to the information that a firm holds about them and the ability to correct, amend, or delete inaccurate information; and enforcement mechanisms to assure compliance with the foregoing principles and recourse for injured persons. Most recently, U.S. and E.U. delegates met in December to try and complete the negotiations on the safe harbors, but the December meeting ended without any definitive conclusions.
V. CONCLUSION
Like the ever-evolving Internet, the legal landscape that applies to the Internet is in motion and will be for years to come. One way to cope with such an ever-changing scene is to allow self-regulation to develop and change along with it. But industry self-regulation may only gradually develop effective enforcement mechanisms and may ultimately provide inadequate protection against highly motivated hackers or fraud artists. Another way is to empower citizens with technology that helps protect their privacy and permits them to assert control over how their personal data are used. But self-help requires considerable consumer education and sophistication and may well fail to protect consumers against surreptitious privacy invasions or identity theft. Finally, legislation may establish protection against specific fraudulent abuses, or for specific groups, such as children, or may even create useful minimum criteria. But the legislative process can be slow and cumbersome and may lag behind or interfere with technological developments. Thus, neither pure self-regulation, nor consumer education and technological empowerment, nor legislation alone can be the answer. All are needed to ensure meaningful privacy protection on the evolving Net.
1. Cass R. Sunstein, Code Comfort, The New Republic, Jan. 10, 2000, at 37; Nielsen Media Research and NetRatings, Inc., The Nielsen/Netratings Reporter (Jan. 13, 1999) (reported at http://www.nielsen-netratings.com/press_releases/pr_000113.html ).
2. FTC, Self-Regulation and Privacy Online: A Report to Congress 1 (July, 1999) [hereinafter FTC's July, 1999 Privacy Report]; FTC, The FTC's First Five Years: Protecting Consumers Online 3 (Dec. 1999) [hereinafter The FTC's First Five Years].
3. Actual sales for 1999 are not yet available, but the projected figures of $12 to $18 billion are probably fairly accurate, given estimated holiday sales of $7 billion. Online Holiday Sales Hit $7 Billion, Consumer Satisfaction Rising (Jan. 18, 2000). < http://jup.com/company/pressrelease.jsp?doc=pr000113>. See also Forrester Research, Inc., Online Retail to Reach $184 Billion by 2004 as Post-Web Retail Era Enfolds (Sept. 28, 1999) (reported at http://www.forrester.com/ER/Press/Release/0,1769,164FF.html).
4. John Markoff, Bitter Debate Divides Two Experts, (Dec. 30, 1999) < http://www.nytimes.com/library/tech/99/12/biztech/articles/30privacy.html >. Cookies technology allows a web site server to place information about a consumer's visits to the site on the consumer's computer in a text file readable only to that web site server. The cookie assigns each consumer's computer a unique identifier so that the consumer can be recognized in later visits to the site. Advertisers are now able to assign a cookie to the computers of users who visit sites in advertising networks and to follow those users from site to site by reading information stored in that cookie at each site.
5. FTC's July, 1999 Privacy Report at 2.
6. Id.; see also note 4, supra.
7. Glenn R. Simpson, E-Commerce Firms Start to Rethink Opposition to Privacy Regulation as Abuses, Anger Rise, Wall St. J., Jan. 6, 2000, at A-24; Cass R. Sunstein, Code Comfort, The New Republic, Jan. 10, 2000, at 37.
8. See Griswold v. Connecticut, 381 U.S. 479, 483-86 (1965).
9. Roe v. Wade, 410 U.S. 113, 152 (1973).
10. See, e.g., Loving v. Virginia, 388 U.S. 1, 12 (1967); Skinner v. Oklahoma, 316 U.S. 535 (1942); Eisenstadt v. Baird, 405 U.S. 438, 453-54 (1972); Prince v. Massachusetts, 321 U.S. 156, 166 (1944); Pierce v. Society of Sisters, 268 U.S. 510 (1925).
11. See, e.g., Cal. Const., art. I, § 1; Ariz Const., art. II, § 8; Ill. Const., art. I, § 6.
12. See, e.g., The Driver's Privacy Protection Act of 1994, 18 U.S.C. §§ 2721-2725 (1994 ed. and Supp. III). The DPPA regulates the disclosure and resale of personal information contained in records that state Departments of Motor Vehicles maintain. Recently, the state of South Carolina challenged the statute's constitutionality, arguing that it violated fundamental principles of federalism. The U.S. Supreme Court upheld the statute. Reno v. Condon, ---- U.S. ---- (2000), 2000 U.S. LEXIS 503 (Jan. 12, 2000).
13. For example, the Tax Reform Act of 1976, 26 U.S.C. § 6103 (1989 & Supp. 1996), protects the confidentiality of tax returns and return-related information and limits the dissemination of individual tax return data to other federal agencies. Another example is the Privacy Act of 1974, 5 U.S.C. § 552a (1994), which regulates the government's creation, collection, use, and dissemination of records which can identify an individual by name or other personal information.
14. See, e.g., the Electronic Communications Privacy Act, 18 U.S.C. §§ 2510-2522, § 2701 (1994), as amended, which limits the circumstances under which the federal and state governments may access oral, wire, and electronic communications.
15. Privacy statutes that regulate private industry include the Right to Financial Privacy Act, 12 U.S.C. §§ 3401-3422 (1994) (bank records); the Fair Credit Reporting Act, 15 U.S.C. §§ 1681-1681t (1994) (credit reports and credit bureaus); the Video Privacy Protection Act, 18 U.S.C. §§ 2710-2711 (1994) (barring video stores from disclosing customers' video choices); the Family Educational Rights and Privacy Act, 20 U.S.C. § 1232g (1994) (educational institutions' informational records); the Employee Polygraph Protection Act, 29 U.S.C.A. §§ 2001-2009 (West Supp. 1999) (limits employers' ability to use polygraphs); the Telemarketing Protections Act, 47 U.S.C. § 227 (1994) (limits on use of automatic dialing machines in telemarketing); and the Cable Communications Policy Act, 47 U.S.C. § 551(a) (1994) (cable television).
16. The Federal Trade Commission Act, 15 U.S.C. § 45(a) (1994 ed.).
17. GeoCities, Inc., Docket No. C-3849, 1999 FTC LEXIS 17 (FTC Feb. 5, 1999). Since the time of the settlement, GeoCities has become part of Yahoo.
18. GeoCities offers its members free and fee-based personal home pages, and links its members' home pages into a virtual community of themed neighborhoods.
19. The GeoKidz Club has been replaced by a kids' club called the Enchanted Forest.
20. These core information privacy principles have developed from studies, task forces, directives, and reports, including: U.S. Dep't of Health, Education, and Welfare, Records, Computers, and the Rights of Citizens (1973); The U.S. Privacy Protection Study Commission, Personal Privacy in an Information Society (1977); Organization for Economic Cooperation and Development, OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data (1980); U.S. Information Infrastructure Task Force, Information Policy Committee, Privacy Working Group, Privacy and the National Information Infrastructure: Principles for Providing and Using Personal Information (1995); U.S. Dep't of Commerce, Privacy and the NII: Safeguarding Telecommunications-Related Personal Information (1995); The European Union Directive on the Protection of Personal Data (1995); and the Canadian Standards Association, Model Code for the Protection of Personal Information: A National Standard of Canada (1996).
21. The FTC now recognizes five widely accepted principles essential for effective self-regulatory (or legislative programs) to protect privacy. These five principles are: Notice/Awareness is the most basic principle. All web sites should disclose to consumers the site's information use and privacy protection policies such as: 1) what information is being collected; 2) who is collecting it; 3) how it will be used; 4) who might have, or will be given access to the data; 5) what passive or non-obvious, data collection methods are used by the site; 6) whether providing the requested information is mandatory or voluntary; and 7) how the data will be protected. Choice/Consent embodies the principle that web sites should seek consumers' consent regarding any uses of the information beyond those necessary to achieve the basic purpose of the data request. Access/Participation establishes the principle that consumers should be able to access data about themselves and to challenge the data's accuracy or completeness. Timely and inexpensive access, a means for consumers to verify the information recorded in the site's database, and a method to correct information or add objections to the file, are essential for meaningful access. Integrity/Security reflects the principle that data collectors should ensure that the information they collect is secure and accurate. For example, the collector should use only reputable sources of data, should cross-check data where possible, and take steps to secure the data against loss or unauthorized access. Enforcement/Redress recognizes the principle that an enforcement mechanism is vital to ensure compliance with all the other fair information practices and to provide recourse for injured parties. A self-regulatory program that seeks to assure enforcement and redress might incorporate such features as periodic compliance audits, neutral investigation of consumer complaints, a dispute resolution mechanism, and correction of misinformation or compensation for injured parties.
22. Children's Online Privacy Protection Act, Pub. L. No. 105-277, Title XIII, 112 Stat. 2681, 2681-728 to 2681-735 (1998) (codified at 15 U.S.C. §§ 6501-6506).
23. ReverseAuction.com, File No. 002-3046 (Jan. 6, 2000) (available at /os/2000/01/reversecmp.html and /os/2000/01/reverseconsent.html
24. The Fair Credit Reporting Act (FCRA), 15 U.S.C. § 1681 et seq.
25. Gramm-Leach-Bliley Act, Pub. L. No. 106-102, Title V, Privacy, 113 Stat. 1338, 1436-1450 (1999) (to be codified at 15 U.S.C. §§ 6801-6809).
26. FCRA, 15 U.S.C. § 1681a(d) ("The term "consumer report" . . . does not include (A) any report containing information solely as to transactions or experiences between the consumer and the person making the report.").
27. 15 U.S.C. § 1681a(d)(2)(A)(iii). Note, moreover, that affiliates may freely share among themselves their individual transaction and experience data without providing any notice or opportunity to object to consumers. 15 U.S.C. § 1681a(d)(2)(A)(ii).
28. Gramm-Leach-Bliley Act, Pub. L. No. 106-102, 113 Stat. at 1437.
29. Dep't of Health & Human Servs., Standards for Privacy of Individually Identifiable Health Information, 64 Fed. Reg. 59,918 (Nov. 3, 1999) (proposed rule).
30. This situation may change during this Congressional session. The CQ Monitor News reported that "'the privacy dam may burst,'" because the argument that self-regulation is working to protect privacy just will not "'hold water anymore.'" Adam S. Marlin, Business Advocates Playing Catch-Up On Privacy Issues, CQ Monitor News, < http://onCongress1.cq.com/PSUser/psrecor...tternfiles/newsanalysis&NS_initial_frm=1 > (quoting Mark Rotenberg, director of the Electronic Privacy Information Center). Currently, there are two, nearly identical proposals to amend Title V of the Gramm-Leach-Bliley Act. They would require that customers opt-in (that is, give explicit permission beforehand) to the release of any of their confidential financial information. See H.R. 3320, 106th Cong. (1999) (sponsored by Rep. Markey); S. 1903, 106th Cong. (1999) (sponsored by Sen. Shelby). In addition, the White House states that it will push Congress this session to pass legislation to protect medical records. Two Virginia Congressmen (Boucher and Goodlatte) have offered legislation (H.R. 1685) that would require Internet sites to post how they use any information that they gather. A bill (S.809) sponsored by Senators Burns and Wyden would require all Web sites to post privacy information and give consumers the chance to limit disclosure of their personal information. The Burns-Wyden bill is closely modeled on the Children's Online Privacy Protection Act but would apply to adults.
31. Children's Online Privacy Protection Act, 15 U.S.C. §§ 6501-6506.
32. Children's Online Privacy Protection Rule, 64 Fed. Reg. 59,888 (Nov. 3, 1999) (to be codified at 16 C.F.R. Part 312). Notably, COPPA provides that "[a] violation of a regulation prescribed under subsection (a) [the FTC-promulgated rules] shall be treated as a violation of a rule defining an unfair or deceptive act or practice under section 18(a)(1)(B) of the Federal Trade Commission Act (15 U.S.C. § 57(a)(1)(B))." 15 U.S.C § 6502. By treating a COPPA rule violation as if it were a violation of a rule promulgated under section 18(a)(1)(B), the Commission can seek civil penalties immediately.
33. The FTC has done precisely this in Liberty Financial Cos., Docket No. C-3891 (Final Order Aug. 12, 1999), where it alleged, among other things, that the Young Investor web site falsely represented that personal information collected from children in a survey would be maintained anonymously when in fact it was not.
34. See Glenn R. Simpson, E-Commerce Firms Start to Rethink Opposition to Privacy Regulation as Abuses, Anger Rise, Wall St. J., Jan. 6, 2000, at A24.
35. FTC, Privacy Online: A Report to Congress (1998) < /reports/privacy3/index.html)>.
36. See Notice of Public Workshop on Online Profiling, Docket No. 990811219-9219-01 (Sept. 1999) < /os/1999/9909/FRN990915.html>.
37. Establishment of the Federal Trade Commission Advisory Committee on Online Access & Security and Request for Nominations, 64 Fed. Reg. 71,457 (Dec. 21, 1999).
38. See FTC's July, 1999 Privacy Report, at 8.
39. Prof. Mary Culnan, McDonough School of Business, Georgetown University, The Georgetown Internet Privacy Policy Survey Report (1999) (available at http://www.msb.edu/
faculty/culnanm/gippshome.html). See also Online Privacy Alliance, Privacy and the Top 100 Sites: A Report to the Federal Trade Commission (1999) (available at http://www.msb.edu/faculty/culnanm/gippshome.html ).
40. See FTC's July, 1999 Privacy Report, at 7-8.
41. See note 21 supra.
42. The survey will cover two data sets: 1) a random sample of 500 domains drawn from a list of the busiest U.S. ".com" sites having an audience of 39,000 unique visitors or more as compiled by Nielsen's Netratings from the month of January 2000; and 2) a review of the busiest 100 domains on the same Nielsen Netratings list.
43. The Consortium was created to develop common protocols that promote Web evolution and interoperability. It is an international group, jointly run by the MIT Laboratory for Computer Sciences (LCS) in the U.S., the National Institute for Research in Computer Science and Control in France, and Keio University in Japan. Currently, there are more than 260 members in the Consortium. W3C Publishes First Public Working Draft of P3P 1.0: Collaborative Efforts by Key Industry Players and Privacy Experts Promote Web Privacy and Commerce, < http://www.w3.org/Press/1998/P3P >.
44. Directive 95/46/EC of the European Parliament and of the Council of 24 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data (available at http://aspe.os.dhhs.gov/datacncl/eudirect.html). See also Guidelines on the Protection of Privacy and Transborder Flows of Personal Data (available at http://www.oecd.org//dsti/sti/it/secur/prod/PRIV-EN.html).
45. U.S. Dep't of Commerce, Draft, International Safe Harbor Privacy Principles (Nov. 15, 1999) (available at http://www.ita.doc.gov/td/ecom/Principles1199.html).
Sample details
- Information Technology
Internet Privacy
Related Topics
- Right to privacy

Privacy on the Internet Essay
Nowadays more and more individuals use the Internet for a wide variety of needs. From social media and shopping to the pursuit of an online degree or doing business, people are bettering their lives because of the Internet. It is a common belief that the Internet is a secure place and that personal information cannot be retrieved by anyone who knows how to do so, when in fact this is quite wrong. E-mails, passwords, banking, addresses, numbers can find their ways to hackers, terrorists or undesired marketers. Regardless of the reasons, every consumer has the right to have privacy as long as that right is used within the bounds of the law. This essay aims to emphasize the importance of Internet privacy. Furthermore, ways of harming privacy will be discussed, and possible measurements to increase one’s privacy will be suggested.
To begin with, in our day and age there are many different threats to a user’s privacy. The first potential privacy risk is phishing. This is an Internet hacking activity used to steal user data, including passwords, credit card numbers, bank account numbers and security PINs. Additionally, another risk is pharming, which is another hacking activity used to redirect a legitimate website visitor to a different IP address. In addition, another Internet threat is spyware, which is an offline application that obtains data without the user’s consent, when the computer is online. These examples illustrate the numerous ways in which nowadays Internet privacy can be harmed and collected data can be misused.
ready to help you now
Without paying upfront
Internet users should be concerned with not only the technological aspect of privacy attacks, such as corrupted files and damaged hardware but also with the potential risk of insufficient protection of user privacy on their personal lives. One example of a privacy risk is the possibility of identity theft. Although it is a common belief that usually companies and enterprises are the target of these crimes, rather than individuals, recent reports seem to show a trend opposing this belief. This could lead to considerable issues for people who have become victims of these attacks and is a pressing issue that Internet users should be aware of.
Privacy and anonymity are key factors in preventing personal data from being accessed by outside entities and used for malicious purposes. However, it is still a common misconception that privacy and anonymity are the same thing. While they may be related, the cases in which they have to be applied are quite different. According to Shirey (2007), the definition of anonymity is “the condition of an identity being unknown or concealed”, whereas the definition of privacy is “The right of individuals to control or influence what information related to them may be collected and stored and by whom and to whom that information may be disclosed.” There is a myriad of web-based services that appear to offer anonymity. However, few really do. Users are usually allowed to create a personal username that they use for accessing their accounts or sending messages. Unfortunately, through log-in and sign-up procedures, it is surprisingly simple to determine a user’s IP address, and even their true identity, when they use these services. This example shows us the potential threat hidden in something as simple as accessing a profile that people nowadays do daily. Therefore a deep understanding of data protection is crucial for all Internet users.
Fortunately, the risk of Internet privacy violation can be minimized. There are plentiful means available to protect one’s online privacy. Some of them are large and complex while others are extremely simple. One method to increase Internet security is to use preventative software applications, such as anti-virus and anti-spam. Another way to reduce the risk of Internet privacy violation is data minimization. “Data minimization refers to collecting, using, disclosing, and storing the minimal data necessary to perform a task. Reducing the amount of data exchanged reduces the amount of data that can be misused or leaked. Data minimization can be effectuated in a number of different ways, including by limiting collection, use, disclosure, retention, identifiability, sensitivity, and access to personal data.” as stated by Cooper et al. (2013) is the most straightforward method to minimize privacy risks. Moreover, another way to oppose Internet privacy threads is for the user to always use strong passwords and to choose different passwords for every application. As long as one is aware of the threats, there are myriad ways for protection.
In conclusion, Internet privacy should not be taken lightly. Most of the Internet users believe that the cyberspace is a secure place and are not fully aware of possible privacy violations such as phishing, pharming and spyware. There are plentiful methods available to protect one’s online privacy such as to use preventative software applications or data minimization among others. The first step of the process of minimizing Internet privacy violations is to understand the huge risk that Internet users are put at and the importance of online privacy.
Cite this page
https://graduateway.com/privacy-on-the-internet-essay/
You can get a custom paper by one of our expert writers
Check more samples on your topics
Problem of internet privacy essay.
Abstract The Internet is a resource that connects people from all over the world. In most parts of the world, the internet is free. With free internet, however, there comes a price. A lot of data from the internet is stored onto a local server, so it is vulnerable to hackers. Without proper knowledge and education,
Internet Privacy Pros And Cons
At home you have all of the privacy you need without someone looking over your shoulders at what you are doing. Also you will not have the problem of someone monitoring what you all looking at. But at work you will have someone who will monitor what you are watching and doing. Also you will
Dehumanization of Internet Privacy
In today’s world, computers have essentially implemented themselves into almost every internet capable technological device, including but not limited to smart watches and virtual reality. These devices track the entity’s internet activity without their knowledge, thus invading their privacy. Due to this state of continual surveillance, the users of this consumer society are forced to
Internet Technology Threats to Privacy
Abstract This research paper is all about Communication Systems and Internet Technology Threats to Privacy (ITTP). I will be telling you about all the legal issues related to computer and internet technology networks. Identify at least three of the social and ethical issues related to electronic technology systems. Introduction Communication Systems and Internet Technology Threats to Privacy are
Importance of Internet Privacy
The rise of internet invades people's privacy is an issue to people today. Privacy has several meanings. It states the quality or state of being apart from a company or observation. Another definition is it states the freedom to unauthorized intrusion, One's right to privacy. Privacy is something that shouldn't be taken away, Privacy can
Internet User Privacy Protection Policy Analysis
While the advent of Internet has drastically advanced our life in a gradually globalized and networked modern world, the growing influence of Internet and technologies draws public’s concern on cybersecurity and overflow of personal data on the Internet. The two largest issues with Internet user privacy are the abuse of user data for financial value
Celebrities deserve privacy Argumentative Essay
Celebrities are constantly In the media for their outrageous or strange antics. Nowadays It doesn't take a lot to be known as a 'Caleb'. The Influence of the 'Celebrity world' has led to extreme effects, especially amongst youths, as most magazines are full of tabloids and attention seeking articles which speak little truth. Not only
Teen Privacy Debate Argumentative Essay
Search and seizure
Contrary to what some may believe, the teens actually had a high level of privacy awareness," (Ackerman). This quote Is referring to a study done on twenty adolescents and their privacy when it comes to electronics, parents, and school. Most adults tend to think their child does not think before they text, tweet, post, or
Issue of Students’ Privacy Rights Argumentative Essay
Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the government for a redress of grievances. The right of the people to be secure in their

Hi, my name is Amy 👋
In case you can't find a relevant example, our professional writers are ready to help you write a unique paper. Just talk to our smart assistant Amy and she'll connect you with the best match.

25,000+ students realised their study abroad dream with us. Take the first step today
Here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

Essay on Internet
- Updated on
- Oct 1, 2021

With throat-cutting competition, the difficulty level of various competitive exams has increased. Apart from domain-specific knowledge, questions framed in various exams evaluate critical thinking and decision-making ability, reading and writing skills, and Logical and Analytical Reasoning . It thus has become important to focus on all the components equally. Just like the aforementioned topics, Essay writing is another crucial element of a wide range of entrance tests like IELTS , TOEFL , UPSC exams , etc. The topics for essays can range from Digital India and Economic issues to the role of Education and Women Empowerment . In this blog, we will share some samples of essays on the internet with you!
Uses of Internet Essay
Essay on advantages and disadvantages of internet, tips to write an essay on the internet .
Here are some of the tips which you can follow in order to write an impressive essay on the internet.
- Your essay on the internet should be clear and concise with appropriate information.
- Research meticulously before you start writing an essay on the internet.
- Add both, advantages and disadvantages of using it.
- Write the content in paragraphs.
- Avoid the use of jargons and slangs.
- Keep the tone formal.
- You can also add statistical data.
The internet is a worldwide network of computer networks that connects millions of people in over 150 countries. Using the internet, you can send emails, chat with people, and obtain information on different variety of subjects.
Internet can be used for multiple purposes including finding information, communicate with people, shop online, manage your finances, etc.
The first workable prototype of internet came in the late 1960s with creation of ARPANET or the Advanced Research Projects Agency Network. ARPANET used packet switching to allow multiple computers to communicate on a single network.
In order to complete your application process for studying abroad, apart from the basic documents, you also need to submit a personal essay / statement of purpose as it elucidates your motive to take admission in a particular course and university and also shed light on your career goals. It thus needs to be impressive! Take the assistance from the experts at Leverage Edu who will help you write an SOP that will highlight your achievements, purpose and future goals in a very lucid yet impeccable way!
Team Leverage Edu
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Leaving already?
8 Universities with higher ROI than IITs and IIMs
Grab this one-time opportunity to download this ebook
Connect With Us
25,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
September 2024
January 2025
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.

COMMENTS
Although every individual has the right to accuse the government and internet service providing companies over their failure to protect their customers' privacy, individuals should recognize, they have a crucial duty to play as far […]
But there are pros and cons to this convenience. While consumer suggestions and reminders can be helpful, the same aggregations of personal data can be used to cause harmful discrimination in education, employment, housing and law enforcement. When surveyed about the importance of privacy in the abstract, most of us rate privacy highly.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
Ultimately, the importance of internet privacy extends beyond individual convenience; it is a fundamental right that underpins our freedom, security, and individuality in the digital age. By recognizing the significance of internet privacy and taking meaningful steps to protect it, we can ensure that the digital landscape remains a place where individuals can freely express themselves ...
Most people do not consciously put a price on their online privacy. But what if they did? A 2020 survey of Argentinians, Brazilians, Colombians, Mexicans, Germans and US citizens did precisely this. The Technology Policy Institute, a think tank, asked respondents how much a company would have to pay them each month to disclose various types of personal data.
725 Words3 Pages. "While the Internet-based economy provides many benefits, it also raises new concerns for maintaining the privacy of information. “Internet privacy is the privacy and security level of personal data published via the Internet. It is a broad term that refers to a variety of factors, techniques and technologies used to ...
1309 Words. 6 Pages. Open Document. Now, the Internet is not only a way people access information, but also the net that connects them. People use it to communicate with friends and family, keep current events and shop online. The using of Internet sometimes involves personal data, triggers fraud and abuse. These are the reason people have laws ...
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Advantages and Disadvantages of Internet Censorship: Unveiling the Web. Introduction In this paper, I will be discussing the internet, the advantages and disadvantages of internet censorship, and how we can effectively control and censor the content on the web, in particular, the problems arising due to censorship.
Instructions. Preparation. Reading. Check your writing: grouping - ideas. Check your writing: gap fill - useful phrases. Worksheets and downloads. A for and against essay about the internet - exercises 592.59 KB. A for and against essay about the internet - answers 136.91 KB. A for and against essay about the internet - essay 511.93 KB.
President Trump had recently signed a congressional resolution in the repeal for internet privacy and the protection of peoples' information. This policy was created during the Obama era by the Federal Communications Commission to protect and hide information from certain company providers from using the subscriber's information.
The study is to prove the intermediary effect of privacy concerns, explore the attitude toward online privacy on social media, and summarize the privacy protection strategies adopted by college ...
Currently, it is estimated that more than 120 million Americans have access to the Internet, and that foreign users recently surpassed U.S. ones in numbers. (1) In part, the exponential growth in the online consumer market has propelled the Internet's extraordinary growth. As the Federal Trade Commission (FTC) noted in its July 1999 report to ...
When the internet first made its appearance to the public in the early 90s, people are more interested in doing things manually. It was like any other technology that was first introduced to the world: it would take a few months, maybe years, before the people gets to try and incorporate them in their everyday
Using this technology can also lead to a feeling of fear and of all ways being watched - the so-called panopticon phenomenon. The pros of using electronic eyes are preventing crimes, identifying criminals and monitoring important places. The interception and reading of emails and messages.
Argumentative Essay On Patriot Act 413 Words | 2 Pages. Tragedy is the great unifier, but it is also a great opportunity for manipulation. In attempting to create a sense of peace and togetherness Obama has unwittingly planted the seeds for censorship and social stagnation in America.
Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices.
Recently, many people were divided in terms of their strong views about the importance of privacy and the exchange "between security needs and personal privacy" (Rainie & Maniam, 2016) as millions of Americans were also affected by online threats and privacy breaches and at the same time concerned with our security.
This essay aims to emphasize the importance of Internet privacy. Furthermore, ways of harming privacy will be discussed, and possible measurements to increase one's privacy will be suggested. To begin with, in our day and age there are many different threats to a user's privacy. The first potential privacy risk is phishing.
Hire writer. 14). The use of unique passwords is therefore the first step in online privacy protection. The second step involves ignoring suspicious emails and links. Phishing is a general threat to people's online privacy. Phishing is mostly done through rogue links sent in emails and messages.
Identity theft, hacking, viruses, and cheating are also the main disadvantages of the internet. There are advantages and disadvantages to every new invention, however, with proper precautions like practicing safe browsing, staying vigilant with the data you share, changing passwords frequently, updating privacy settings, and not sharing your ...